“Wisdom does not consist in trying to wrest the good from the evil but in learning to “ride them as a cork adapts itself to the crests and troughs of the waves.”
-Bruce Lee
Standing behind a curtain you hear murmuring voices in a darkened auditorium. From the podium in a meeting you hear every voice, see every gesture and notice every sigh, nod or tap of a finger. Confronting a spouse. Coming to terms with a medical diagnosis. Waiting for a text message. Soldiers on the battlefield of life, poised and ready to react, sometimes fearful, sometimes thrilled – a time always comes when you will need to attack or retreat. Back away from a disagreement. Fight an injustice. Protect your children, your parents, your friends. Protect yourself. Situations that require response are everywhere – and we choose how, however unconsciously, to respond. Response is a diverse array of chemical reaction, muscle memory, clear and muddled thinking, racing hearts or steady hands.
“Our brains are wired emotionally,” says Dr. Arthur Cassidy, celebrity psychologist. “We all have a repertoire of emotional strategies that we draw on to deal with anger, joy and other situations. But normally we don’t go searching for confrontation, so we haven’t always built a form of strategy to overcome and deal with it.”
Here in the APAC region, the response to stressors is as unique as the array of cultures. Angry voices aren’t often raised in public. A laugh could indicate an uncomfortable moment. A downward glace is often humility. Respect is important and trust is earned. This may not lend itself readily to the concept of a full-frontal, proactive assault on cyber security threats. When asking if a log has been analysed, who clicked on a phishing email attachment, who shared the Wi-Fi password or who opened the door for the cyber-thief are not topics easily addressed or mistakes easily rectified, how do we proactively protect our work environment from cyber-threat?
We educate ourselves on all potential threats and our arsenal of responses (however extensive or meagre), we define our ideal response scenario, and we equip ourselves with the technology and knowledge to respond effectively.
"CIOs can't protect their organizations from everything, so they need to create a sustainable set of controls that balances their need to protect their businesses with their need to run them. Taking a risk-based approach is imperative to set a target level of cybersecurity readiness. Raising budget alone does not create an improved risk posture. CIOs must prioritize security investments by business outcomes to ensure that the right amount of budget is being spent on the right things. Attacks and compromise are inevitable, and, by 2020, 60% of security budgets will be in support of detection and response capabilities." writes Paul Proctor, Gartner vice president and distinguished analyst.
Global consulting firm, A.T. Kearney, suggests the following 4-point strategy, their “Regional Cybersecurity Defence Playbook,” when focusing on cyber-security in the ASEAN region.
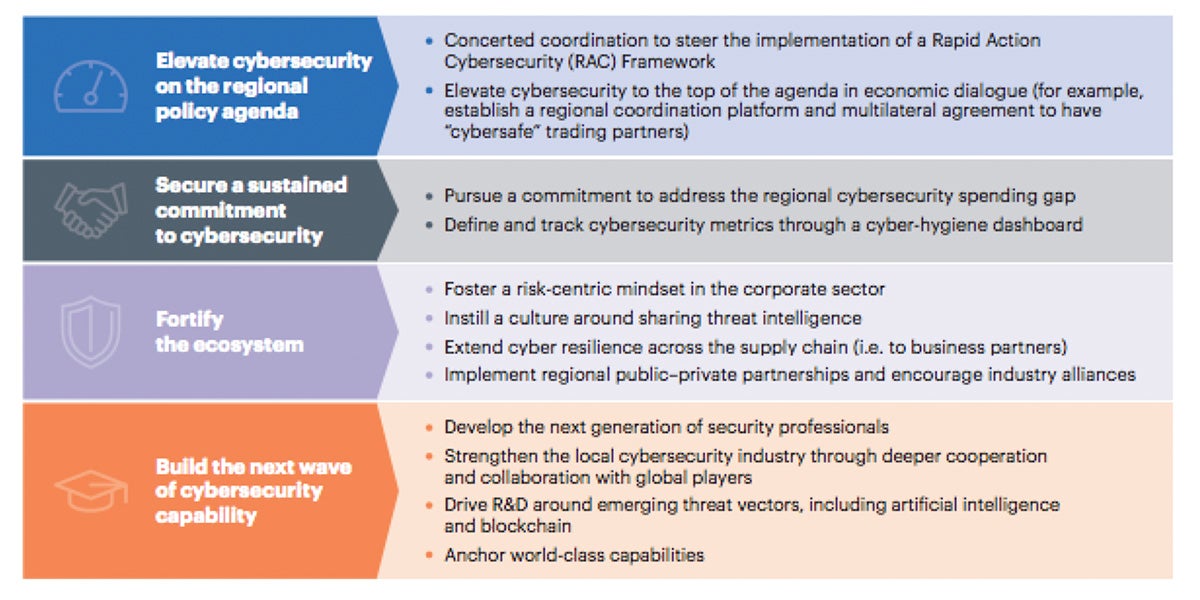 Source: A.T. Kearney analysis
Source: A.T. Kearney analysis
Why Sangfor?
Some of the easiest ways to secure the buy-in necessary for these types of changes, is implementation of a clear and concise method of reporting, showing cyber risk your company is currently facing daily. Deployment of an endpoint protection platform like Sangfor’s Endpoint Secure, capable of intelligent detection, quick response and comprehensive protection is the first step toward total security. It’s ability to correlate with next-generation firewall like NGAF, malware detection engines like Engine Zero, threat intelligence and analytics platforms like Neural-X, and SWG’s like Sangfor’s IAM, makes Endpoint Secure the APAC and global one-stop-shop for network security.
Join us for our next and final series instalment, Part 5, discussing changing our mindset to be as adaptive and flexible as possible when considering cyber-security and our response to it. The opportunities for growth have never been closer. Sangfor will take you there.
Founded in 2000 and a publicly traded company as of 2018 (SANGFOR STOCK CODE: 300454 (CH)), Sangfor Technologies is an APAC-based, global leading vendor of IT infrastructure solutions specializing in Network Security and Cloud Computing. Visit us at www.sangfor.com to learn more about your internet security options, benefits and functions, and make your IT simpler, more secure and more valuable.





