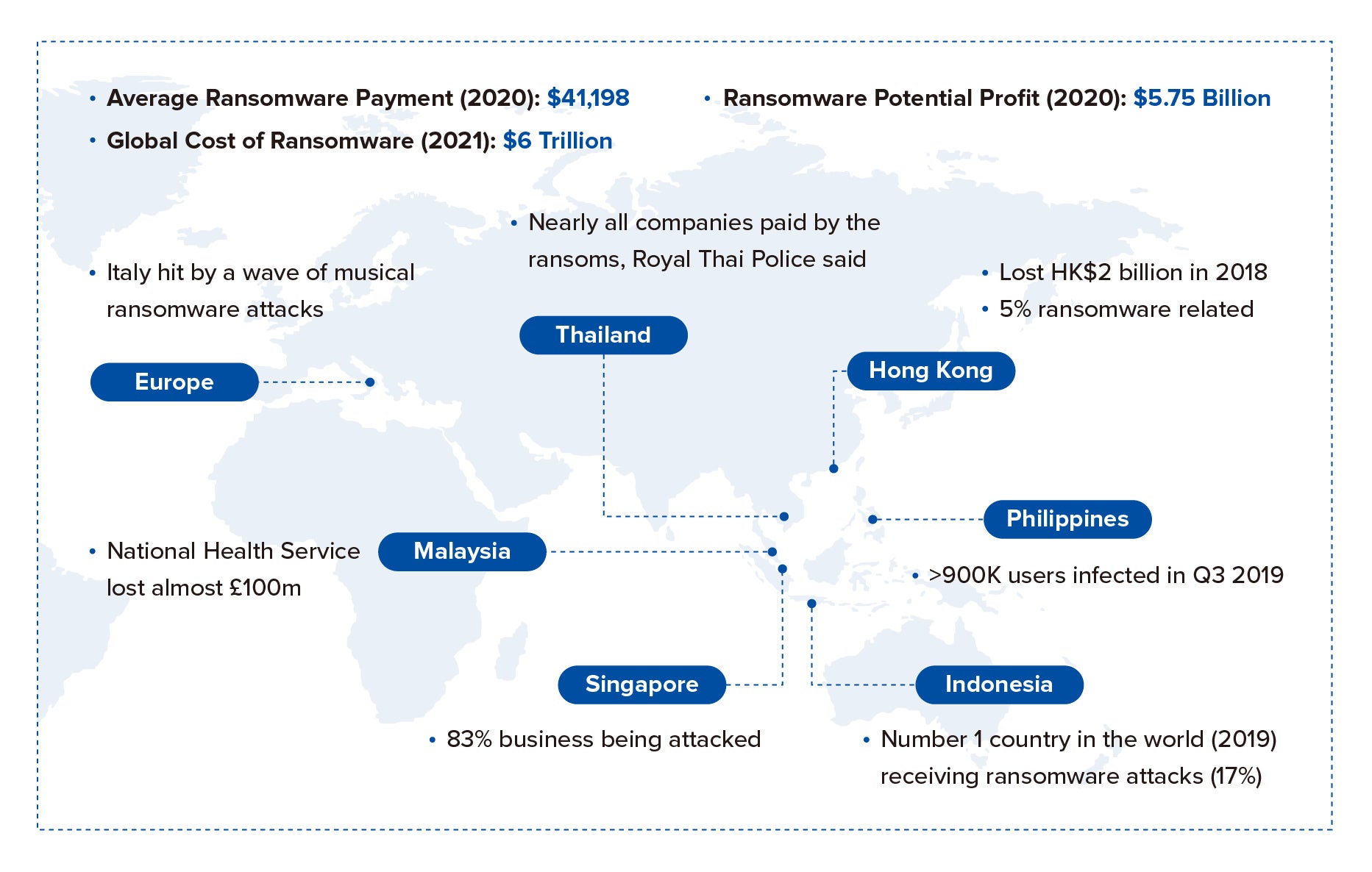
Ransomware is the fastest growing cyberthreat today. Where national governments and large enterprises were once the primary targets, now local governments and smaller organizations have become victims, with operations shutdown days or weeks unless the exorbitant ransom is paid. On average, the cost of downtime starts at US$100K/hour.
Ransomware is a type of malware that uses a specific sequence of steps call a “Kill Chain” to infect and spread.
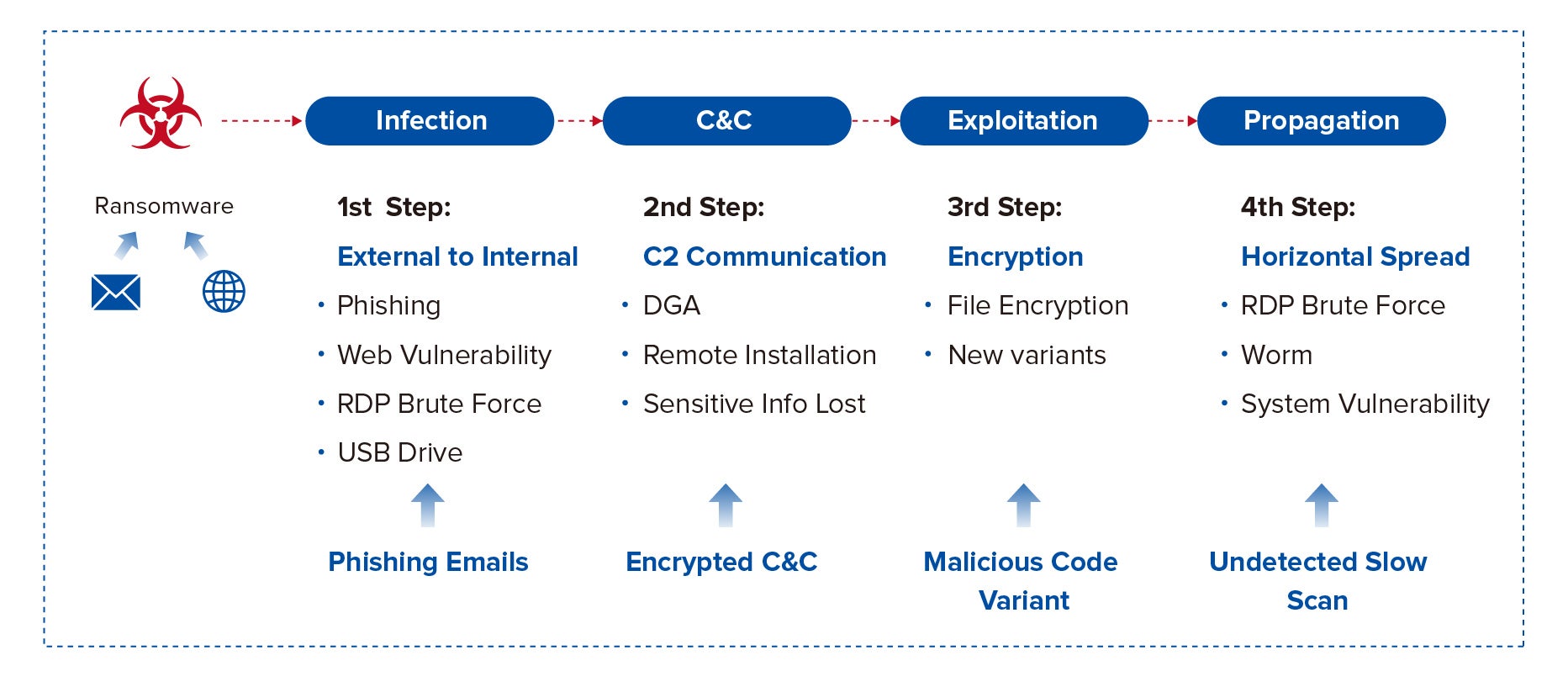
Traditional security point products alone have not effectively stopped these steps in the Kill Chain. Organizations may be protected with next-generation firewalls (NGFW), email gateways, and next-generation anti-virus/malware solutions (NGAV), but WannaCry proved them ineffective by infecting 200,000 systems across 150 countries in only 4 days. Let us examine these steps to understand why.
Infection
Infection occurs when an attachment is opened, or a link clicked from a phishing email. Same for clicking on links at malicious websites. This is the step that anti-virus/anti-malware products typically combat; they scan files being downloaded or saved to the endpoint looking for malware/viruses. Once found the files are deleted or quarantined. The problem is 3rd party testing shows that NGAV is 99.95% effective at detection. That may seem quite high. But, AVTest receives over 350K new malware samples daily. Blocking 350K new malware samples at 99.95% effectiveness would potentially allow 1750 samples through. In other words, NGAF cannot block everything and something WILL get through. But NGAV does not really do well after malware installs.
C&C Communications
NGAV cannot directly identify malware C&C communications. Firewalls can track communications to potential C&C servers, but they cannot verify if the communications are valid or malicious. Most NGAV and NGFW do not share information to identify that an infected endpoint is communication with C&C servers.
Exploitation
The most difficult step to stop is exploitation where encryption of files occurs. Ransomware does a great job of not only hiding which running system process is controlling the encryption but the application that initiated the process as well.
Propagation
Malware will spread to other vulnerable systems quickly, sometimes within only a few minutes. In many cases, it may be possible to isolate a system from the network to prevent propagation. However, an infected system may need to be operational for business requirements and cannot be isolated. That system would then look for other systems to infect throughout the organization.
A Holistic Solution
Sangfor’s Security Solution for Ransomware provides a holistic solution to stop ransomware attacks in real-time. The solution is robust enough to block every step in the ransomware Kill Chain but modular enough to be tailored to any organization. For more information on how to protect your organization against Ransomware, please click here to contact us.






