Ransomware attacks have been plaguing the digital landscape for years. In 2023, organizations around the world detected around 317.59 million ransomware attempts. While the main goal of ransomware attacks is financial gain, the consequences for most companies can stretch further into operational disruptions and reputational damage. Threat actors are finding more innovative ways to carry out ransomware attacks across different sectors. In particular, the healthcare sector has been in the firing range of most cyber-attacks due to the industry's vulnerability.
Recently, the healthcare sector cyber threat made headlines again with the Black Basta ransomware attack on Ascension Healthcare IT systems. In this blog article, we explore the details of the Ascension Healthcare ransomware attack and the fallout from the incident. We also look further into the Black Basta ransomware group – focusing on who they are, how they work, and where they target. Then we delve into other Black Basta victims and try to understand Black Basta and other ransomware prevention protocols. Now, let’s start by understanding the Ascension Healthcare ransomware attack.
Black Basta Ransomware Attack on Ascension IT Systems
Ascension Healthcare is a non-profit Catholic healthcare network based in Washington. The US provider supports over 140 hospitals in 19 states. On the 8th of May, Ascension Healthcare “detected unusual activity on select technology network systems,” which the company admitted to being a cyber security event in a release the next day. The incident was later confirmed to be a ransomware attack and disrupted many Ascension Healthcare systems and services.
Phone systems and “various systems utilized to order certain tests, procedures, and medications,” were affected by the ransomware attack according to another statement by Ascension. Five days after the attack was publicized, the healthcare provider further alerted its patients that its pharmacies would no longer be able to take credit cards – forcing them to depend on “manual and paper-based systems” while dealing with the incident.

How Ascension Responded to patients at the time of cyber attack?
A doctor compared the conditions to working in the 1980s, according to The Detroit Free Press. “We have to write everything on paper,” he said, while still acknowledging that Ascension has trained their staff for events like this. While scheduled visits were proceeding as planned, patients were asked to write down their symptoms, medications, and other health information for their appointments. Retail pharmacies were able to fill prescriptions but also asked that patients “bring their prescription bottles from a previous fill.”
Several Ascension hospitals were also forced to divert “emergency medical services in order to ensure emergency cases are triaged immediately.” This alone could have had devastating effects on patient mortality rates and critical procedures. In another update, Ascension noted that its MyChart system, which allows patients to view their medical records and communicate with their providers, was also unavailable.
Ascension Healthcare advised its business partners to disconnect from its systems immediately after the incident due to the ongoing disruptions and "out of an abundance of caution." The company also temporarily paused many non-emergent elective procedures, tests, and appointments while working to bring its systems back online.
What actions has Ascension taken for this Ransomware Attack
The healthcare organization reassured its patients that despite the challenges posed by the ransomware incident, patient safety would continue to be its utmost priority and that it was working on remediation efforts. Ascension further confirmed that was in “close contact” with the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) to try to resolve and learn from the incident. The organization said it is yet to determine if any sensitive patient information was accessed and will soon notify the impacted individuals.
While Ascension itself has yet to confirm the threat actor behind the ransomware attack, four sources briefed on the investigation told CNN that the type of ransomware used in the hack is known as Black Basta - which has been used repeatedly against the healthcare sector in recent years. Now, let’s look further into the Black Basta ransomware.
Who Is Black Basta?
The Black Basta ransomware group surfaced in April of 2022. After the Conti ransomware group was taken down in June 2022, it’s believed that the cybercrime syndicate broke into multiple groups. Black Basta is likely one of the split groups due to similarities in their approach to malware development, leak sites, and communications for negotiation, payment, and data recovery. The Ransomware-as-a-Service group quickly gained traction by targeting 19 prominent companies and more than 100 confirmed victims in its first few months of operation.
Black Basta uses double extortion tactics - encrypting victims’ data and then threatening to leak sensitive information on its public leak site on Tor, Basta News. When first observed in 2022, Black Basta was using QakBot as an initial vector. Now, Black Basta’s malware – which is written in C++ - targets both Windows and Linux systems. It encrypts data using ChaCha20 and RSA-4096 and attempts to delete shadow copies and backups.
Federal authorities have linked Black Basta ransomware to the exploitation of critical vulnerabilities in ConnectWise ScreenConnect since February. The ransomware group has also been linked to the FIN7 threat actor through similarities in their custom Endpoint Detection and Response (EDR) evasion modules and overlapping use of IP addresses for command and control (C2) operations.
The Department of Health and Human Services security team said in a March 2023 report that the threat group's prolific targeting of at least 20 victims in its first two weeks of operation indicates that it is experienced in ransomware and has a steady source of initial access. Bleeping Computer also reported that the Russia-linked Black Basta ransomware gang has made up to US$ 100 million in ransom payments from more than 90 victims since it first surfaced. All this, and the most recent Ascension Healthcare attack, have prompted the US to make statements warning companies about the Black Basta ransomware group.
US Warns of Black Basta Ransomware Gang
On the 10th of May, the FBI and Cybersecurity and Infrastructure Security Agency CISA issued a joint advisory with the Department of Health and Human Services and MS-ISAC to warn about the Black Basta ransomware. The advisory states that the group has impacted a wide range of businesses and critical infrastructure in North America, Europe, and Australia. It further went on to confirm that, as of May 2024, Black Basta affiliates have impacted over 500 organizations globally.
The Health-Information Sharing and Analysis Center then also issued a threat bulletin warning that the Black Basta ransomware gang "has recently accelerated attacks against the healthcare sector." The bulletin describes the Black Basta ransomware group as financially motivated and a significant threat to the healthcare sector. The Health-ISAC advised that members should keep an eye on the threat actor and their Tactics, Techniques, and Procedures (TTPs).
While the federal agencies haven’t said what exactly prompted the warning issued about the Black Basta ransomware, it can be deduced that it was partly the result of the attack on Ascension Healthcare. Now that we know the dangers of the Black Basta ransomware, let’s explore how a Black Basta attack works.
How Does a Black Basta Attack Work?
As mentioned before, Black Basta uses the double extortion method to get its ransom – first encrypting data and then exfiltrating data and threatening to publish it if not paid. Black Basta campaigns use targeted spear-phishing attacks and exploit known vulnerabilities as an attack vector to gain initial access. In 2022, the group shared its intentions of buying corporate network access and sharing the profits with its affiliated Initial Access Brokers (IAB). Black Basta typically deploys a range of second-stage tactics to acquire Windows Domain credentials and penetrate a target’s network laterally after access is gained - stealing sensitive data and deploying ransomware.
While ransom notes do not generally include an initial ransom demand or payment instructions, they do provide Black Basta victims with a unique code and instruct them to contact the ransomware group via a .onion URL through the Tor browser. Black Basta ransom notes usually give victims between 10 and 12 days to pay the ransom before the ransomware group publishes their data.
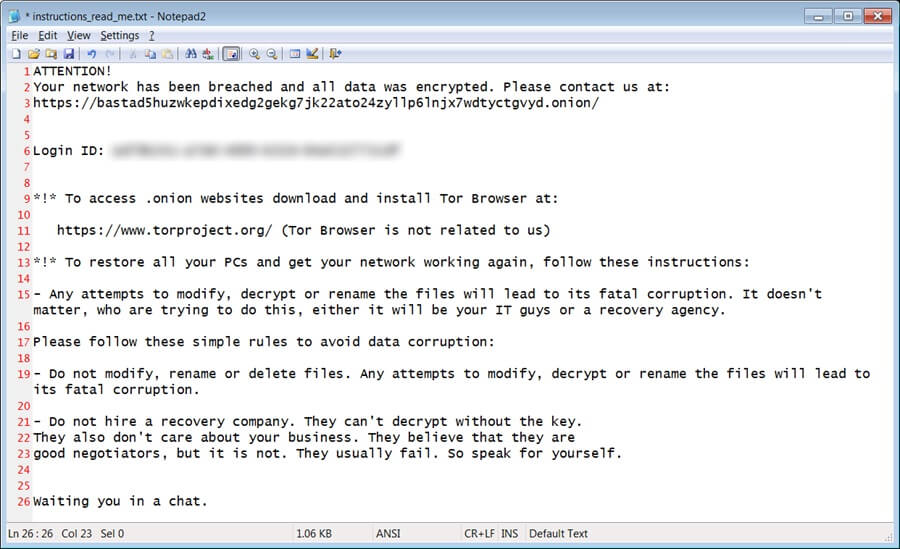
A Black Basta ransom note (BleepingComputer)
Black Basta then uses a diverse set of tactics to access adjacent network endpoints with extracted credentials through Powershell and PsExec commands. This includes the use of QakBot stealer, MimiKatz, and the exploitation of the native Windows Management Instrumentation (WMI) API for credential harvesting. The Black Basta ransomware can also exploit the ZeroLogon, NoPac, and PrintNightmare vulnerabilities for local and Windows Active Domain privilege escalation. For C2 remote control of infected systems, Black Basta installs Cobalt Strike Beacons, uses SystemBC for C2 proxy, and the Rclone tool for data exfiltration.
The encryption stage of a Black Basta attack starts by disabling antivirus products, executing an encryption payload remotely via PowerShell, and deleting system shadow copies using the vssadmin.exe program. After that, Black Basta executes a custom ransomware payload that has been through at least one significant version change since it was first observed. The first version of Black Basta’s encryption module was similar to Conti ransomware, however, the improved second version uses heavy obfuscation and randomized filenames to evade EDR products and has replaced its use of the GNU Multiple Precision Arithmetic Library (GMP) algorithms with the Crypto++ encryption library.
The Black Basta 2.0 encryption module uses the XChaCha20 algorithm for symmetric encryption, a unique Elliptic Curve Cryptography (ECC) key pair to encrypt and prepend the symmetric key along with the ECC public key to decrypt it and with a nonce to the encrypted file data. Black Basta also disables the compromised system’s DNS services to complicate the recovery process by preventing it from accessing the internet and deploying a ransomware variant that targets Linux-based VMware ESXi virtual machines (VMs). After knowing how these attacks take place, we can now learn more about who the Black Basta ransomware group targets the most.
Who Does Black Basta Ransomware Target?
According to CISA, healthcare organizations are attractive targets for cybercrime actors due to their size, technological dependence, access to personal health information, and unique impacts from patient care disruptions. The Black Basta ransomware group has taken advantage of this crisis and has mostly targeted healthcare and other critical infrastructure providers. The RaaS group has hit organizations in the US, Japan, Canada, the United Kingdom, Australia, and New Zealand in highly specific attacks.
The group has also targeted 12 of the 16 government-designated critical infrastructure sectors. So far, Black Basta victims have spanned several industries – including healthcare, manufacturing, construction, food and beverage, and transportation. Ransomware in healthcare has been an issue for decades where threat actors find it easier to squeeze money out of the already-overwhelmed and critical infrastructure that needs operations to continue for the sake of life-saving services.
Unfortunately, examples of ransomware attacks in critical infrastructure are not a new feat. In March 2023, Managed Care of North America Dental Insurance Company was the victim of a ransomware attack that affected 8.9 million patients. The LockBit ransomware group took responsibility and published all of the stolen files after the company refused to pay a US$ 10 million ransom demand. Later on in April, the Harvard Pilgrim Health Care (HPHC) organization was also targeted by a ransomware attack that compromised the data of 2,550,922 people.
Black Basta is only the latest ransomware group targeting critical infrastructure in a long line of opportunistic threat actors. We’ll now run through some of the Black Basta attacks that have made headlines in the past.
Black Basta Ransomware Attack Victims
The Black Basta ransomware group has already made a name for itself over the last three years. The RaaS threat actor has targeted several sectors – extorting money and stealing data. These are some of the Black Basta victims that have made headlines recently:
ABB Black Basta Ransomware Attack
In May 2023, global industrial automation company ABB confirmed that its data had been stolen in an attack attributed to the Black Basta ransomware group. The company’s Windows Active Directory was targeted in the cyber-attack and disrupted hundreds of devices. ABB assured customers that it had no evidence that its customers’ systems had been directly impacted or that the security of its products had been compromised.
Cybersecurity researcher, Kevin Beaumont, commented that the attack was “a standard Black Basta playbook attack.” Beaumont further stated that in the ABB Black Basta attack, initial entry into the company’s systems was gained using malicious weblink techniques such as SEO poisoning and fake browser updates to install Qakbot trojan malware – a tactic the group regularly uses.
Capita Black Basta Ransomware Attack
The U.K. outsourcing firm, Capita, confirmed in April 2023 that it had been hit by a major cyber incident that prevented access to internal applications and disrupted some services. The Black Basta ransomware group listed Capita on its leak website and shared some files as proof that they had exfiltrated data from its systems. The breached data included personal and financial information that was being auctioned off rather than being used as leverage for a ransom. The company expected to incur exceptional costs of up to US$ 25 million due to the attack.
Rheinmetall Black Basta Ransomware Attack
The German automotive and arms producer, Rheinmetall, was hit by a ransomware attack in April of 2023 as well. While only the company’s civilian business was disrupted by the incident, it still cost the firm US$ 10 million in recovery expenses. The breach, which Black Basta took credit for, led to the disclosure of confidential data such as copies of passports, non-disclosure agreements, and purchase orders. While the attack is seemingly opportunistic, some believe that Black Basta targeted the weapons manufacturer due to its support for Ukraine amid the conflict.
Knauf Black Basta Ransomware Attack
In June 2022, global building supply manufacturer Knauf suffered a cyber-attack. Operations were shut down to isolate the attack and took weeks to resume regularly. Black Basta took responsibility for the attack on its extortion site in July and published 20% of the files they allegedly exfiltrated.
Sobeys Black Basta Ransomware Attack
In November of 2022, Canadian food retailer, Sorbeys, admitted to being a victim of an IT incident. While the stores remained open, some in-store functions were delayed or disrupted by the attack. Employee reports, however, noted that all computers were locked out in affected Sobeys stores, with point-of-sale (POS) and payment processing systems still online and working since they're set up to work on a separate network. Based on ransom notes and negotiation chats seen by BleepingComputer, the attackers deployed Black Basta ransomware payloads to encrypt systems on Sobeys' network.
The Black Basta ransomware group has been behind multiple ransomware attacks and shows no sign of slowing down as it evolves. This is why it's important to know how to protect your organization from Black Basta ransomware in the future.
Black Basta Ransomware Prevention
To ensure the ideal ransomware protection against a threat like Black Basta, your organization needs to be equipped with the right tools and practices to prevent, detect, and recover from a ransomware attack. Let’s go over some of the ways you can keep your business safe during ransomware attack season:
- Installing and configuring advanced Endpoint Security products that monitor endpoints for suspicious activity.
- Regularly updating software, operating systems, and firmware to ensure the latest features and patches while updating any Known Exploited Vulnerabilities.
- Using Multi-Factor Authentication for all user accounts to prevent phishing. This can be done through authenticator apps or the use of physical tokens and smart cards.
- Enhancing access management tools and software by using the principle of zero-trust to regularly enforce strict access control to authorized personnel.
- Educate and train workforces to be wary of opening links or attachments and to look out for Black Basta’s known TTP, IoC, and file signatures.
- Implementing reliable backup strategies and disaster recovery options to protect data and reduce downtime in the event of a security incident.
- Use strong and unique passwords. Threat actors are unlikely to breach the network when you use stronger passwords.
- Using cybersecurity solutions such as Sangfor’s Anti-Ransomware to seamlessly identify and prevent all aspects of the ransomware kill chain to give your organization a secure and reliable platform to mitigate the risk of ransomware in the future.
Sangfor Technologies provides superior cybersecurity and cloud computing infrastructure that will protect you from ransomware attacks – offering you elite detection, mitigation, and recovery options. Sangfor has all the tools you need to stay secure. Contact Sangfor Technologies today to see how we can help you be prepared for anything.





