In today's digital landscape, where cyber threats are increasingly sophisticated, strong passwords serve as the first line of defense against unauthorized access. Despite advancements in authentication technologies, passwords remain a primary target for cybercriminals employing brute-force attacks, credential stuffing, and other malicious methods. As highlighted during Cybersecurity Awareness Month (CSAM) 2024, understanding the importance of robust password practices is crucial for safeguarding personal and organizational data.
This article shows the significance of strong passwords in cybersecurity, examines the risks associated with weak password practices, and provides actionable strategies to enhance password security.

The Importance of Using Strong Passwords for Cybersecurity
Using strong passwords is crucial for maintaining cybersecurity and protecting sensitive information, as they serve as the first line of defense against unauthorized access. Here are key reasons to prioritize strong passwords:
- Strong passwords help protect against threatening access to personal accounts, financial information, emails, and sensitive business data. A strong password creates a strong barrier, making it harder for any attackers to breach accounts. Be it through brute force or other misplaced password-cracking methods.
- Data breaches often occur when attackers gain access to weak passwords. Once a password is compromised, attackers can infiltrate systems, extract data, or lock users out of their accounts. Strong passwords can help mitigate the possibility of a breach and minimize potential damage.
- Identity theft is a growing cybercrime in which attackers use stolen passwords to access personal accounts. A strong password makes it incredibly difficult for hackers to impersonate you or misuse your identity for fraud activities.
- For businesses, strong passwords protect confidential information like financial data, intellectual property, and customer data from being stolen or misused. Weak passwords jeopardize the security of internal networks, cloud accounts, and databases.
- Many industries have strict regulatory requirements for data protection. Strong passwords are often mandated as part of compliance with cybersecurity regulations such as the GDPR.
Consequences of Weak Passwords
Weak passwords can lead to a variety of serious consequences for organizations. Here are some of the key risks associated with weak passwords:
- Data Breaches: Compromised passwords are a leading cause of data breaches. When hackers gain access to an organization’s network, they can steal vast amounts of important data. This can lead to financial losses, legal consequences, and reputational damage.
- Account Hijacking: Cybercriminals often use weak passwords to take over social media, email, and other personal accounts. They may impersonate you, send phishing messages to your contacts, or lock you out of your own accounts.
- Identity Theft: Weak passwords make it easier for hackers to gain unauthorized access to accounts to steal sensitive personal information. This can lead to identity theft, where criminals use your identity to commit fraud, or open credit accounts.
- Financial Losses: Weak passwords can result in unauthorized access to banking and financial accounts. Once inside, attackers can transfer funds, or make purchases, leading to severe financial losses.
- Phishing and Ransomware Attacks: Weak passwords may also allow hackers to deploy phishing schemes or install ransomware on your devices. Then they hold your data hostage until a ransom is paid.
Statistics and Examples on Password-Related Security Breaches
- The average cost of a data breach is $4.88 million in 2024, with many caused by weak passwords (IBM, 2024).
- 74% of data breaches involve human error, like weak or stolen passwords (2023 Verizon Report).
- 193 billion accounts were affected by credential stuffing attacks in 2022 (Akamai).
- Ransomware attacks increased by 93% in 2023, often using weak passwords.
Here are some notable real-world examples of security breaches caused by weak passwords:
Yahoo Data Breach (2013-2014)
The Yahoo data breach, occurring between 2013 and 2014, is one of the largest data breaches in history, affecting approximately 3 billion user accounts. This massive compromise was primarily due to inadequate security practices, including the reliance on weak and frequently reused passwords, which made it easier for attackers to infiltrate the system. Additionally, Yahoo’s failure to implement robust encryption methods and its delayed detection of the breach allowed cybercriminals to access sensitive information, including names, email addresses, and security questions. The incident serves as a critical reminder of the importance of strong cybersecurity measures and the need for users to adopt better password hygiene to protect their personal data.
Facebook Breach (2019)
In 2019, Facebook experienced a significant security lapse when it was revealed that millions of user passwords were stored in plain text due to a misconfiguration in their internal storage system, which allowed unauthorized access to sensitive data by employees. This oversight meant that the passwords were not encrypted or hashed, making them easily retrievable and posing a serious risk to user accounts. The incident underscored the critical need for robust security practices, including the implementation of strong password hashing algorithms, stringent access controls to limit employee access to sensitive information, and regular security audits to identify and mitigate vulnerabilities. As a result, Facebook faced scrutiny over its data protection measures and the importance of safeguarding user information in an increasingly digital world.
Colonial Pipeline Ransomware Attack (2021)
In 2021, the Colonial Pipeline experienced a significant ransomware attack that disrupted fuel supplies across the Eastern United States. The breach was traced back to a single compromised password, underscoring the severe risks associated with weak password management practices. This incident not only led to fuel shortages but also emphasized the importance of implementing strong cybersecurity measures, including multi-factor authentication and regular password updates, to protect critical infrastructure from similar threats in the future.
Tips for Creating Strong Passwords
Understanding the significance of strong passwords and the dangers of weak ones, here are effective strategies for creating robust passwords:
- Use a Passphrase: Create a long password using a phrase or sentence that’s easy to remember but difficult to guess.
- Mix Characters: Combine uppercase letters, lowercase letters, numbers, and symbols.
- Avoid Personal Information: Do not use personal details such as your name, birthdate, or pet’s name. These are often easy for attackers to guess.
- Randomize It: Make your password as random as possible. Use a password generator tool to create a completely unpredictable password if you struggle to come up with one.
- Use a Password Manager: A password manager can generate and store passwords for all your accounts including bank accounts.
- Don’t Reuse Passwords: Always use unique passwords for each account. Reusing or using old passwords increases vulnerability.
- Unique for Each Account: A strong password should not be reused across different online accounts. Using a unique password for each login minimizes the risk of a security breach spreading to other accounts.
Tools for Managing Passwords
Several tools are available to simplify password management, making it easier to store and retrieve passwords. Here are some popular options:
- Password Managers: Password managers are software applications designed to store and manage your passwords securely. They encrypt your credentials and provide an easy way to access them.
- Built-in Browser Password Managers: Modern web browsers including Google Chrome, Apple iCloud Keychain and Mozilla Firefox come with their own password managers. Using these, one can store your passwords and autofill them on websites
- Two-Factor Authentication (2FA) Tools: Tools like Microsoft Authenticator, Google Authenticator and Authy enhance account security by requiring a second form of verification. Some password managers also support two-factor authentication (2FA) for added security.
- Password Generators: Most password managers include built-in password generators. But you can also use standalone online tools or software that create strong, random passwords.
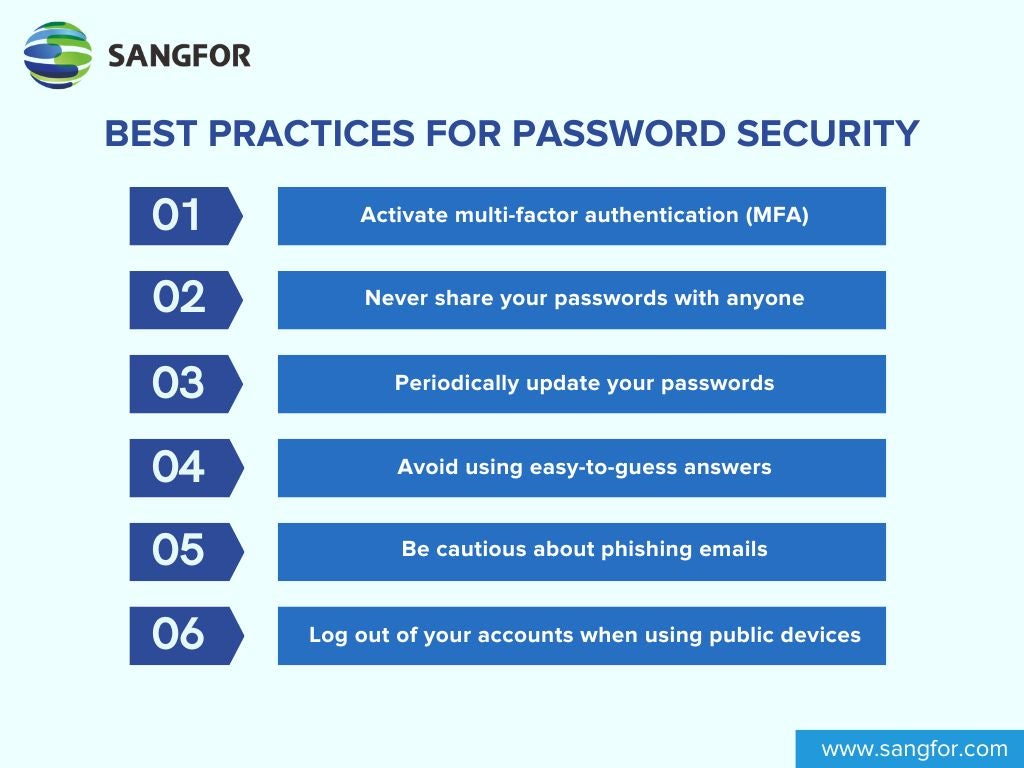
Best Practices for Password Security
There are simple ways to enhance their security, helping to protect your accounts from hackers and safeguard your personal information and finances.
- Activate two-factor authentication (2FA) or multi-factor authentication (MFA) wherever possible to add an extra layer of security. Enable biometric authentication, such as fingerprints, on devices that support it.
- Never share your passwords with anyone, even with the trustiest ones.
- Periodically update your passwords, especially for critical accounts like email, banking, and social media.
- Avoid using easy-to-guess answers for security questions and make up answers that aren't easily discoverable.
- Be cautious about phishing emails or messages asking for your password or personal information.
- Always log out of your accounts when using shared or public devices. Use the “private” or “incognito” mode in browsers if you're on a public computer.
Sangfor For Your Security
Strong passwords are an important defense against cyberattacks; however, it is also advisable to invest in a robust, innovative, and intuitive cybersecurity vendor like Sangfor Technologies to ensure your organization’s cybersecurity. At Sangfor, we provide a cutting-edge suite of security solutions designed to keep your organization protected in a rapidly evolving cyber landscape. Our latest innovations include Security GPT, which leverages AI to enhance threat detection and Zero Trust frameworks for secure access management. Additionally, Omni-Command (XDR) delivers unparalleled threat visibility and control, while our Access Secure (SASE) solutions provide seamless, secure access across your networks. Moreover, Sangfor ensures your business is safeguarded against sophisticated cyber threats with advanced firewalls and endpoint security.
Contact Sangfor today for more information on enhancing cloud infrastructure and cybersecurity.





