About Cyber Security Awareness Month
CSAM is short for Cyber Security Awareness Month, observed in October of every year since 2004, about 20 years ago. Observing CSAM aims to raise awareness between the public and private sectors about the importance of cybersecurity.
The United States initially initiated the event, which is now observed globally due to its grave importance. This October marks the 21st Cybersecurity Awareness Month. The month-long initiative emphasizes the importance of cybersecurity risks for individuals, communities, and organizations. It empowers them to adopt safe online practices and improve their overall digital security.
To sum up, the CSAM emphasizes the shared responsibility for cybersecurity threats among all stakeholders.
Theme and Message for the 21st CSAM
This year’s Cybersecurity Awareness Month’s theme is “Secure Our World”. A simple call to action that invites you to protect yourself and your business from cybersecurity threats and dangers online.

Image source: https://www.cisa.gov/cybersecurity-awareness-month
The campaign shares the following four simple steps to enhance your security and stay safe online:
- Use Strong Passwords: Implementing strong passwords and using password managers are simple ways to enhance your security and safeguard your accounts from unauthorized access attempts that may aim to steal your sensitive information or money.
- Turn on Multifactor Authentication (MFA): Multifactor Authentication means adding another layer of verification on top of your password. With MFA, you might be asked to enter a temporary text-based code or use a biometric or a time-based code from authentication apps. This approach significantly safeguards your accounts in case your password is compromised.
- Recognize and Report Phishing Attempts: Phishing attacks are increasing more than ever. Always double-check before sharing any sensitive information because unsolicited messages and emails may look like they were sent from a legitimate person or organization. Ensure that you report the phishing attempt and block them away for good.
- Update Software: In today’s digital age, updating your devices with the latest software and security patches is important. Regularly check for updates and ensure automatic updates are enabled to keep your devices safe from attacks and threats.
Facts & Figures around Cybersecurity Threat
The following are some of the eye-opening facts and figures around cyber security threats that are gathered for the current and past year 2023-2024:
- According to Forbes, global cybercrime damage is expected to grow by 15% in the coming two years, reaching a staggering 10.5 trillion USD by 2025.
- Per the report by IBM, the global average cost of a data breach in 2024 is USD 4.88 million, a 10% increase over the last year and recorded the highest total ever.
- Norton Antivirus shared that around 75% of the cyberattacks started with emails in 2024, making phishing a primary entry point for cybercrimes.
- Deloitte reported that ransomware affected 66% of the organization in 2023 alone.
- According to Veeam, cyber-attacks are reported as the number one cause of outages across organizations for the fourth year in a row.
Top Cybersecurity Threats in 2024
The following are some of the top cyber security trends occurring in the current year 2024:
- Ransomware
- Artificial Intelligence Threats
- Insider Threats
- Social Engineering Attacks
Ransomware
Ransomware is a type of malicious software that cybercriminals use to hold victims' sensitive data or their devices hostage. They further threaten victims to keep the data locked until the victim pays a ransom amount to the attacker.
Ransomware attacks have evolved massively since their inception. Recent ransomware attacks have evolved to include double-extortion and triple-extortion tactics that even greatly induce risks for people or organizations that maintain regular data backups. Double extortion attacks increase the threat of stealing a victim’s sensitive data and leaking it online. Triple extortion ransomware attacks further heighten the risk of using stolen data to target the victim’s customers and business partners.
Ransomware attacks can be categorized into several types, including Crypto Ransomware, Locker Ransomware, Scareware, Doxware, and Ransomware-as-a-Service (RaaS).
Real-Life Example of Ransomware Attacks: Attack on Toyota Supplier
According to Reuters, Toyota’s supplier of plastic parts and electronic components was hit with a significant ransomware attack in 2022 that forced Toyota to suspend its operation in 14 plants across Japan. This forced suspension accounted for the closure of 28 production lines, and one-third of Toyota's global production was halted. It was estimated that this attack caused a loss of output for about 13,000 vehicles, which is a very large number considering the vehicle manufacturing industry.
Artificial Intelligence
Artificial intelligence, shortened as AI, is a technology that enables computer systems and machines to simulate human-like behavior by learning, problem-solving, comprehension, decision-making, and creativity. AI is becoming the backbone of innovation and modern computing, helping individuals and companies unlock value that was previously deemed impossible. AI’s implementation rapidly encompasses almost all disciplines, including computer science, data analysis, medicine, linguistics, neuroscience, psychology, and others.
The evolution of artificial intelligence over the past 70 years can be summarized as follows:
- In the 1950s, AI primarily involved machines mimicking human intelligence.
- By the 1980s, AI systems began to learn from historical data, a process known as machine learning.
- During the 2010s, machine learning models advanced significantly and started replicating the human brain's functions, a field known as deep learning.
- In the 2020s, deep learning models have developed into foundation models that can generate original content, a capability referred to as Generative AI or Gen AI.
Real-Life Threat Example from AI: Uber’s Self-Driving Incident
AI’s rapid development has resulted in some unforeseen legal and life-threatening issues. The complexity of AI algorithms and sole reliance on them blurs the line of responsibility between the company and its use of AI.
BBC shared news about Uber’s self-driving car being involved in a fatal accident. Self-driving cars rely highly on AI to make decisions while on the road. The vehicle hit and killed a 49-year-old individual while he was wheeling a bicycle across the road. This incident was first on record, and afterward, many fatal incidents happened due to the use of AI. Tesla’s autopilot features, which heavily rely on AI, have so far been involved in up to 13 fatal accidents.
Insider Threats
As the name suggests, insider threats are cybersecurity threats that originate from within the organization. An insider is any person who has or had legitimate access or knowledge of an organization’s proprietary resources, facilities, equipment, network, and systems. The person in the subject could be a business partner, former employee, or contractor affiliated with the organization.
These threats come in many forms and shapes that serve different purposes. Some of them are:
- Espionage
- Terrorism
- Information leaking
- Negligent or unintentional employee
- Corruption and organized crime
- Sabotage
- Workplace violence
- Foreign government targeting
Real-Life Threat Examples from Insider Threats
Example 1: Former Tesla Employees Leaked 75,000 Employee Data
In 2023, two former Tesla employees leaked personally identifiable information (PII) of approximately 75,000 current and former employees. The leaked information contained the employees' names, addresses, employment history, contact numbers, and social security numbers. Upon further investigation, it was also observed that this insider breach exposed production secrets, customer bank details, and some classified complaints concerning Telsa's self-driving features.
While legal actions were taken against the employees, and they were apprehended, but the stain on the brand’s security reputation remains irreversible.
Example 2: A Reddit Employee Falling into a Fraudulent Landing Page
In 2023, Reddit admitted that it had suffered a security breach, where an active Reddit employee was lured into a deceptive landing page, posing as a legitimate internal site. The attackers captured the authorized access credentials and compromised the company’s secure database containing the user credentials, email addresses, and logs dating back to 2007. The attackers were able to gain access to the encrypted data.
Reddit advised its affected customers to update their passwords and use multi-factor authentication to secure their accounts better. The breach marks the vulnerability and insider threat risks even for a well-established cyber company.
Example 3: Disney’s Internal Communications Exposed: Sensitive Information Revealed
In 2024, the hacktivist group NullBulge claimed to have accessed and leaked thousands of Disney’s internal Slack channels, revealing sensitive information about unreleased projects, internal communications, and employee details. Initially reported by the Wall Street Journal, the breach appears to date back to 2019 and includes a significant amount of data, estimated to be around 1.2 terabytes, much larger than the initial 2.6GB estimate. The group stated that they gained access through a user with Slack credentials and linked their actions to a previous breach involving Club Penguin fans. NullBulge asserts that their intentions are not malicious, aiming to protect artists and promote a fair ecosystem in light of AI’s impact on the industry.
Social Engineering
Social Engineering is also considered one of the top cybersecurity threats of 2024. Social engineering attacks manipulate people by divulging them to give information that they should not share in the first place. It also extends to making people download software, visit websites, send money, share company proprietary secrets, and make other mistakes they should not do under normal circumstances.
Social Engineering attacks are conducted with different psychological tactics, some of which are:
- Phishing people by using fraudulent emails or messages.
- Baiting and luring victims by giving them tempting offers.
- Tailgating authorized people into areas containing sensitive information.
- Pretexting creates a fake situation for the victim and acts as the right person to resolve the situation.
- Scareware uses fear to manipulate victims into sharing confidential information.
Real-Life Threat Examples from Social Engineering
Example 1: Social Engineering Attack on Uber
A threat actor named “TeaPot” utilized Uber’s Slack platform, which was used internally by employees, to impersonate an employee and gain access to the company's internal network. The threat actor was able to escalate the privileges and view sensitive information. After his apprehension, he admitted that he used social engineering tactics to fool an employee into giving their confidential login credentials.
The lesson here is that no application or platform should be taken for granted when the company’s employees use it for discussion purposes. Moreover, organizations should strictly consider implementing multifactor authentication for their internal platforms and the use of their third-party applications.
Example 2: $100K Twitter Bitcoin Scam
A major social engineering attack using the Twitter platform resulted in obtaining ~$100K in Bitcoin from victims. This attack underscored that not even giant social media platforms are protected from sophisticatedly designed cyber breaches.
The attack was carried out by a verified user who tweeted a "Double Your Bitcoin" offer, claiming followers could double their bitcoins by clicking a link. Victims included notable celebrities and influencers, allowing the attackers to gather contributions quickly. According to BBC reports, they received up to $100,000 in donations.
How to Prevent Cyber Security Threats
The following are some practical tips curated to prevent cyber security threats for you and your organization:
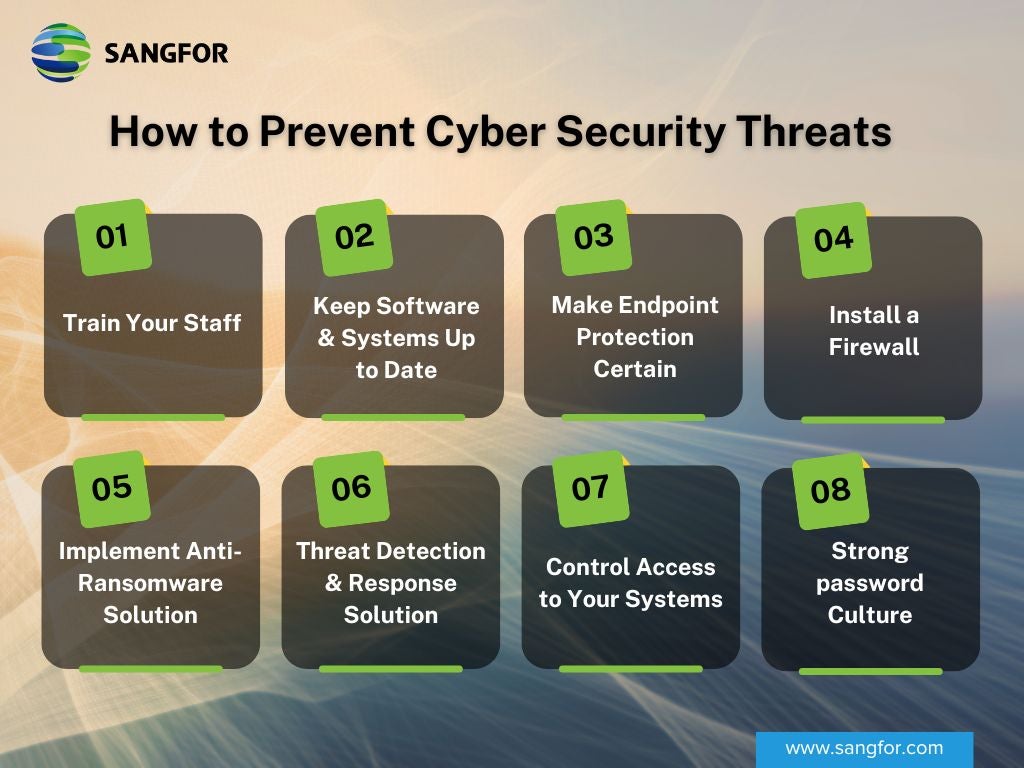
- Train Your Staff: This tip goes a long way. Educated employees are your first line of defense. They are knowledgeable about distinguishing between a legitimate email and a phishing email. They are intellectually sound in spotting social engineering tactics if employed by an insider or outsider. They are sure not to share personal or company proprietary information either offline or online anywhere. Click here to learn more about cybersecurity training.
- Keep Software & Systems Up to Date: Most cyber-attacks happen because attackers take advantage of exposed loopholes and vulnerabilities in the software. These loopholes and vulnerabilities rarely sometimes extend to hardware, but that is quite unlikely. All the software and hardware of your organization must be up to date so the commonly found vulnerabilities are patched and fixed before they are used to hijack your company’s systems. Click here to learn more about the importance of software updates.
- Make Endpoint Protection Certain: Endpoint protection safeguards the network and devices connected over the enterprise network. Mobile devices, laptops, and tablets that are connected over the corporate network can give access to security threats. It is essential to implement endpoint protection in the company-wide paradigm. Sangfor’s Endpoint Secure is an advanced solution that safeguards endpoint devices from evolving threats and breaches. It can block malware, viruses, ransomware, and malicious worms using advanced technologies.
- Install a Firewall: Cyber-attacks and data breaches are evolving, with new ones surfacing daily. An organization must secure its network behind a firewall. Firewalls are among the most effective ways to defend your organization from cyberattacks. Sangfor’s Network Secure Firewall comes with all-in-one solution-based hardware to protect your organization from all attack verticals. Network Secure offers malware detection, threat intelligence, cloud deception, web application firewall, SoC Lite, and anti-ransomware capabilities. Network Secure is the world’s first AI-enabled next-generation firewall that has the power to eliminate 99% of external threats at the network perimeter.
- Implement Anti-Ransomware Solution: Ransomware is among the top cybersecurity threats that individuals and companies face in today's digital age. Companies should not take anti-ransomware lightly. Investing in ransomware solutions ensures your data is not taken hostage for hefty ransom amounts, and even after payouts, it may be leaked online. Governing bodies and law enforcement agencies like GDPR may slap additional hefty fines due to data leakage. Sangfor offers unique Anti-Ransomware solutions that work with the synergies of Sangfor Network Secure and Endpoint Secure to kill the ransomware in a mere 3 seconds, yes, in just 3 seconds.
- Threat Detection & Response Solution: Implementing advanced Network Detection and Response (NDR) solutions can improve your organization's overall security footprint while eliminating potential cybersecurity threats. Investing in Sangfor Cyber Command NDR solutions can aid the organization in superior threat detection and remedial capabilities by constantly monitoring internal network traffic. It can also correlate critical events with global threat intelligence and AI to minimize and uncover hidden threats within the network.
- Control Access to Your Systems: Sangfor’s Access Secure is a comprehensive SASE (Secure Access Service Edge) solution that offers advanced SD-WAN capabilities and ZTNA (Zero Trust Network Access) security. With this advanced solution, your organization can provide exceptional user experience, empowering your business to operate securely and seamlessly from all locations of the company’s presence points. This solution consolidates multiple network functions into one device to reduce the total cost of ownership.
- Strong password Culture: Organizations should enforce strong password policies coupled with multifactor authentication techniques to promote a culture of safety among employees. Policies like password rotation every quarter are essential to protect the company’s network and secure resources from unauthorized or stolen legitimate users' credentials. Click here to learn more about best practices of password security.
Conclusion
Cybersecurity Awareness is a crucial reminder for individuals and organizations to remain vigilant and prepared. The cybersecurity threats mentioned for this year underscore the need for continuous learning, improving, and adopting defense strategies. Organizations must invest in the right solution to protect their overall security safety from evolving cyberattacks and threats. The solutions mentioned in this article serve as a cornerstone and foundation for having foolproof security against today's sophisticated threats.





