Log4j Component Introduction
Log4j is a open-source project of Apache By using Log4j, the destination of log transfer can be controlled as console, file, GUI component, and even socket server, NT event logger, UNIX Syslog daemon, etc. The output format of each log can also be controlled. By defining the level of each log, log generation process can be controlled in a more detailed way.
Vulnerability CVE-2019-17571 Introduction
Log4j has a remote code execution vulnerability. The cause of this vulnerability is thatSocketServerclass does not perform effective security verification on the data obtained by eavesdropping, but directly deserializes it. Attackers can pass in malicious serialized data to exploit the vulnerability and launch remote code execution attack against the server.
Vulnerability Reproduction
Establish environment of Log4j 1.2.17 and use nc to send malicious serialized data to Log4j open port, as shown below:
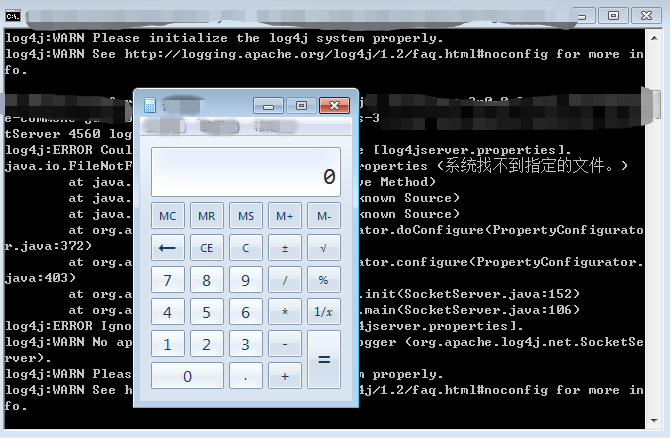
Impacts
Affectd Log4j versions:
Impacts: Apache Log4j 1.2.4 - 1.2.17
Timestamp
On Dec 20, 2019, NVD disclosed this vulnerability
On Jan 2, 2020, Sangfor Security Team conducted in-depth analysis on it and release early warning articles and solutions.
Solution
Remediation
- Update Apache Log4j 2 to the latest version
- Prohibit exposing socket ports opened by the SocketServer class to the Internet
Sangfor Solution
- Sangfor NGAF has updated corresponding security protection feature. Simply turn it on.
- Sangfor Cloud WAF has updated database immediately in the cloud. Users can be protected from high risk easily and rapidly without performing any operation.
- Sangfor Cyber Command can detect attacks exploiting this vulnerability and perform real-time alert. It can also correlate with Sangfor NGAF to block IP address of attackers.





