Threat Overview
Last month, Avast Threat Labs reported on the newly discovered Parrot Traffic Direction System (TDS), which was found to have compromised tens of thousands of websites.
As the name suggests, traffic direction systems are leveraged as Internet landing pages by cybercriminals to filter users according to various criteria to determine whether they are desired targets for malware distribution.
As of March 2022, Parrot TDS, using malicious JavaScript code, infected more than 16,500 websites, including personal, university, adult, and local government sites. The infected web servers share one particular commonality in that many hosted poorly secured content management systems (CMS), primarily WordPress, with weak login credentials. It is suspected that attackers picked their targets based on their level of security as opposed to other factors.
Unlike previous malicious DTS such as Prometheus, Parrot has much greater reach. Based on analysis and investigation conducted by Avast, Parrot TDS is believed to have been in operation since October 2021, with heightened levels of activity observed in February and March 2022. Targeted users are spread across the world; the Avast report reveals most targeted users were in Brazil, India, the U.S, Singapore, Indonesia, Thailand, the Philippines, Argentina, Mexico, France, Pakistan, and Russia.

Chain of Infection
Websites infected with Parrot DTS are manipulated by FakeUpdate (also known as SocGholish) to initiate a drive-by-download attack. The JavaScript code displays a fraudulent yet authentic-looking software update page, such as that of Google Chrome, to trick users into clicking the malicious link. Once clicked, Parrot DTS, via a malicious PHP script compiled into the compromised web server, filters users based on various criteria, such as IP address, user agreement, referrer, and cookies. The requests of users who are deemed to be of interest are then forwarded to the command and control (C2) server under the adversary’s control. What is more, the malicious PHP script allows attackers to perform arbitrary code execution on the compromised server creating a backdoor for more convenient access.

Example of fake software update page
The C2 server responds by first, loading JavaScript code onto the victim’s machine which further capture information about the logged-on user and client, including the name of the PC, username, domain name, installed antivirus and antispyware products, MAC address, list of processes, etc. Next, the C2 delivers the final payload, a NetSupport Client remote access tool (RAT) that gives the attacker full access to the client machine for further exploitation.
The RAT is commonly downloaded to the "AppData\Roaming" folder and masquerades as ctfmon.exe, the same name as a common, legitimate Microsoft process, and thus could easily go unnoticed. The RAT runs automatically after the client machine is switched on, and with chat functions disabled and the silent option turned on, it can operate stealthily in the background and be difficult to detect.

NetSupport RAT disguised as ctfmon.exe
Remediations
Indicators of Compromise (IoC) & Sangfor Protection
Avast Threat Labs provides in its report a list of IoCs for Parrot TDS, FakeUpdate, and NetSupport RAT.
Sangfor Network Secure (Next-Generation Firewall, previously known as NGAF) and Endpoint Secure (endpoint protection) using threat intelligence from Sangfor Neural-X are proven to detect, alert, and kill the malicious activity in each step of the attack kill chain, keeping users safe from intrusion. The following are examples of Sangfor Neural-X’s detection of key Parrot TDS IoCs (Screenshots taken from Sangfor Neural-X Threat Intelligence Platform).
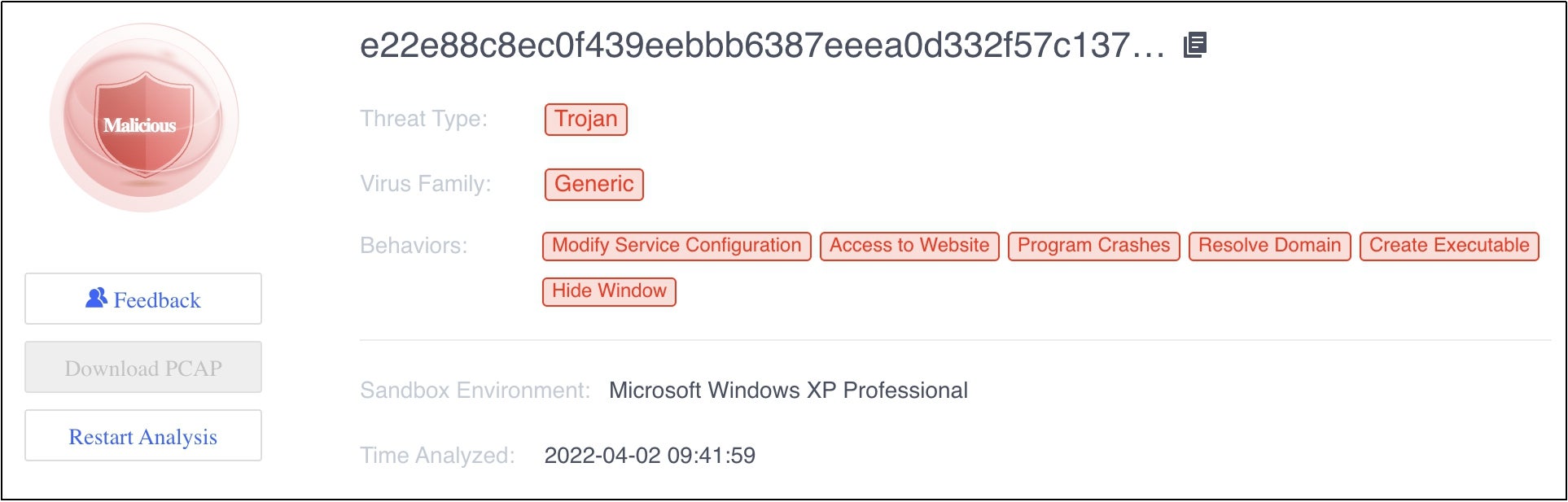
Sangfor Neural-X detects SHA256 of Parrot TDS (direct version JavaScript)

Sangfor Neural-X detects SHA256 of FakeUpdate JavaScript

Sangfor Neural-X detects SHA256 of NetSupport RAT
Other Workarounds
Sangfor suggests the following recommendations for developers to prevent servers from being compromised.
- Scan all files on the web server with antivirus. Sangfor recommends using Endpoint Secure for the least amount of impact to a system when scanning.
- Use the latest CMS version.
- Use the latest versions of installed plugins.
- Inspect all JavaScript and PHP files on the web server and replace with original ones if any appear to have been tampered with.
- Check for automatically running tasks on the web server (for example, cron jobs).
- Check and set up secure credentials. Make sure to always use unique credentials for every service.
- Check the administrator accounts on the server. Make sure each of them belongs to you and have strong passwords.
- When applicable, set up 2FA for all the web server admin accounts.
- Use some of the available security plugins (WordPress, Joomla).
About Sangfor Technologies
Sangfor Technologies is an APAC-based, global leading vendor of Cyber Security, Cloud Computing, and Network Infrastructure solutions. To find out more about Sangfor’s full range of offerings, please visit us at www.sangfor.com, and let Sangfor make your digital transformation simpler and secure.





