Cyber-attacks in the modern age are becoming increasingly complex. As threat actors choose more sophisticated methods, the use of newer malware is growing. Malware is any type of software used to harm a computer or network. By disguising themselves as harmless, malware files will push users to open suspicious files which then infect the network. Malware attacks have been on the rise these last few years. In 2022, Statista reported that global malware attacks reached 5.5 billion. The escalating issue is something to take note of. Lately, the QakBot malware has been making more headlines – however, this time for a good reason.
FBI Take Down QakBot
The FBI recently dismantled the QakBot malware’s infrastructure and identified more than 700,000 infected computers worldwide - including more than 200,000 in the United States. Many countries, including the US, France, Germany, the Netherlands, the United Kingdom, Romania, and Latvia, worked together to stop the "qbot" malware. This malware caused ransomware attacks and resulted in billions of dollars in damage.
The Department assured the public in its release that the QakBot malicious code was being deleted from victim computers - preventing it from doing any more harm. It also announced the seizure of more than US$ 8.6 million in cryptocurrency in illicit profits. The agency redirected QakBot botnet traffic to and through FBI servers which infected the affected computers and prompted them to download a new file. This file would then uninstall the QakBot malware and “untether” the victim’s computer from the QakBot botnet. Martin Estrada, a US Attorney, said that the operation also led to the seizure of almost 9 million dollars in cryptocurrency from the QakBot cybercriminal organization, which would be made available to victims.
The operation – named Duck Hunt – is also the largest US-led financial and technical disruption of a botnet infrastructure leveraged by cybercriminals to commit ransomware, financial fraud, and other cyber-enabled criminal activity.
What Is QakBot Malware?
QakBot – also known as “qbot” or “Pinkslipbot” – was discovered in 2008. As one of the largest and longest-running botnets to date, it has made quite a name for itself.
Qbot is a Windows malware that started as a banking trojan. It later evolved into a malware dropper. The malware has been used to target financial institutions, critical infrastructure contractors, and medical device manufacturers on the West Coast. QakBot steals sensitive information to self-propagate to other systems on the network. The malware has been used globally by several ransomware organizations - including Black Basta, Egregor, and Prolock.
The Cybersecurity and Infrastructure Security Agency (CISA) named QakBot as one of the top malware strains of 2021. The agency also released a report classifying the malware strain as a banking trojan that steals financial data, browser information or hooks, keystrokes, and credentials. According to another 2020 State of Malware report, QakBot was also named 9th on the list of “Top 10 Threats to Private Companies” and saw a 465% increase from 2019.
How Does QakBot Work?
QakBot is a second-stage malware, which means it needs to be introduced into the system by a first-stage downloader malware. The initial access can be gained through various techniques – such as malspam, phishing, vulnerability exploitation, or insider attacks. Once inside the system, the qbot malware steals credentials and spreads to other hosts on the network using Microsoft’s PowerShell and the Mimikatz exploit kit.
The multiple modules of the QakBot malware also allow qbot to use several methods to steal credentials, including:
- Keyboard stroke monitoring.
- Search browser caches for stored passwords.
- Enumerating system files to find password hashes.
The qbot malware allows threat actors to perform manual attacks through remote code execution (RCE). Once infected, qbot can also send additional malware onto the computer, such as ransomware. The malware has been updated and has been adapted many times to help hackers by performing reconnaissance and lateral movement, gathering and exfiltrating data, or delivering other payloads on affected devices. Victim computers then become part of the botnet. A botnet is a network of compromised computers that the hackers control. The users are often unaware of this infection until it's too late.
QakBot Malware Infrastructure
QakBot uses a command-and-control infrastructure to carry out attacks globally, according to FBI Director, Christopher Wray. In a joint advisory by CISA and the FBI, QakBot’s modular structure was found to be responsible for many malicious features. These have included process and web injection, victim network enumeration and credential stealing, and the delivery of follow-on payloads such as Cobalt Strike, Brute Ratel, and other malware. QakBot’s infrastructure relied heavily on using hosting providers for its own infrastructure and malicious activity. The advisory also revealed that at any given time, thousands of victim computers running Microsoft Windows were infected with QakBot as the botnet was controlled through three tiers of C2 servers.
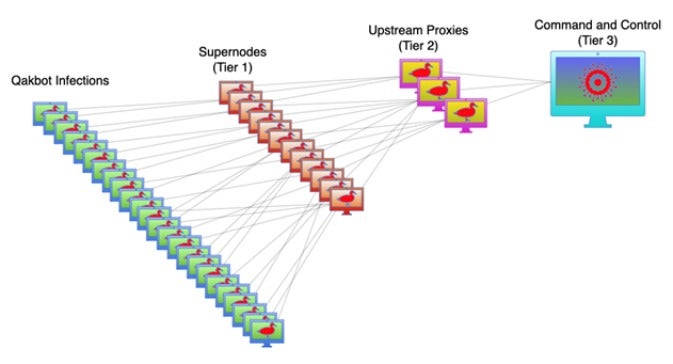
Figure 1: QakBot’s Tiered C2 Servers Infrastructure, Sourced from CISA
The advisory further noted that the first tier of C2 servers in the QakBot infrastructure included a subset of thousands of bots selected by the malware’s administrators. These were promoted to Tier 1 “supernodes” by downloading an additional software module.
These supernodes then communicate with the victim computers to relay commands and communications between the upstream C2 servers and the infected computers. CISA stated that as of mid-June 2023, 853 supernodes have been identified in 63 countries - which were all active that same month. The supernodes also frequently change which helps the malware avoid detection by network protection systems. Every bot has been seen communicating with a set of Tier 1 supernodes to relay messages to the Tier 2 C2 servers - serving as proxies to conceal the main C2 server. The 3rd tier server controls all of the bots.
Microsoft has also taken a swing at breaking down the infrastructure of the QakBot malware. From its research, the company noted that the qbot might present itself differently on different devices. QakBot was also noted to have three email delivery methods - malicious links, malicious attachments, or embedded images. However, according to Microsoft, the qbot infrastructure seemed to always have the same basic “building blocks” in each campaign that can be rearranged or replaced according to the device shown in Figure 2.
These included:
- The Delivery Blocks – Attachment, Hyperlink, or Embedded Image
- Macros
- QakBot Payload
- Process Injection
- Credential Theft
- Scheduled Task
- Email Exfiltration
- Lateral Movement
- Cobalt Strike
- Ransomware
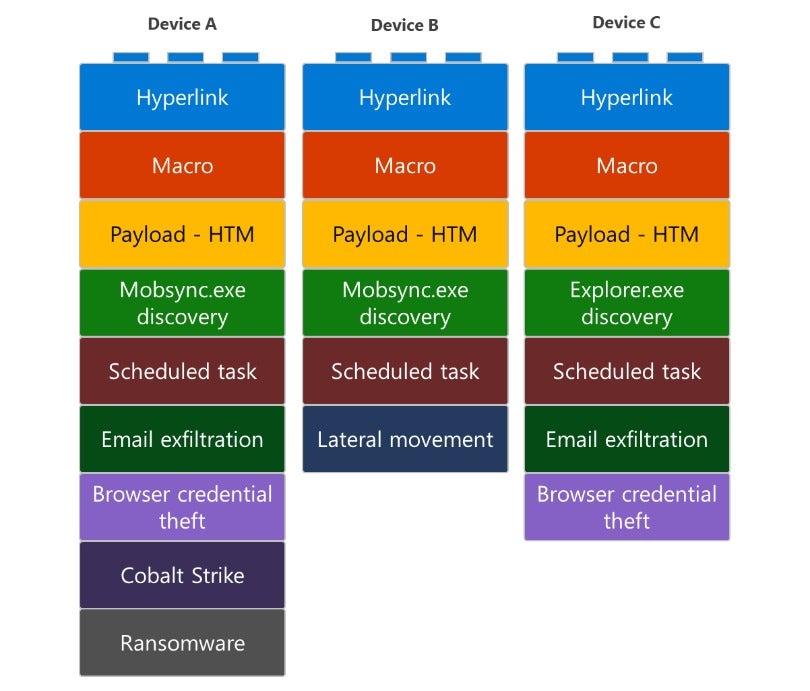
Figure 2. Sample differences among devices affected by a single QakBot campaign. Sourced from Microsoft
The QakBot emails sent would all contain hyperlinks with missing the HTTP or HTTPS protocols – which allowed the links to avoid sandboxing but also meant the user had to manually copy and paste the link in the search bar to open the file.
Between September and November 2023, Microsoft observed some of the following attachment naming patterns:
- CMPL-[digits]-[month]-[day].zip
- Compensation_Reject-[digits]-[mmddyyyy].zip
- Document_[digits]-[mmddyyyy].zip
- Document_[digits]-Copy.zip
- PRMS-[digits].zip
- Rebate-[digits]-[mmddyyyy].zip
- REF-[digits]-[month]-[day].zip
- TXN-[digits].zip
Despite varying delivery methods, the QakBot campaigns all use malicious macros in Office documents - specifically Excel 4.0 macros. Once enabled, the macros connect to a predefined set of IP addresses or domains to download the malicious files.
The QakBot NoteOne Attacks
In January of this year, Microsoft’s OneNote service was used to deliver the QakBot malware. As mentioned before, QakBot campaigns would use Microsoft Office attachments to spread. However, the company began rolling out versions of Office that could block XL4 and VBA macros by default in early 2022. Threat actors then began using HTML attachments.
In May 2022, the Follina vulnerability (CVE-2022-30190) in Microsoft’s Support Diagnostic Tool (MSDT) became the ideal opportunity for qbot hackers to deliver the QakBot payload.
In December 2022, the Qakbot threat actors turned their attention to OneNote due to its ability to embed executable file types - such as HTA files, CMD files, and BAT files. Since then, OneNote has been used to deliver a variety of malware strains, including Formbook, AsynRAT, and Emotet.
The malware campaign – dubbed QakNote – was inspected by cybersecurity specialists who noted two parallel spam campaigns distributing malicious Microsoft OneNote attachments embedded with an HTML application – or HTA file.
- In one, the hackers would send impersonal malspams with an embedded link to the weaponized “.one file”.
- On the other, the hackers would use the thread injection method to hijack existing email threads and send a reply-to-all message to its participants with an attached malicious OneNote notebook.
However, the subject matter within the messages would be different. Most attachments used in the QakNote campaign would be named either:
- ApplicationReject_#####(Jan31)[.]one
- ComplaintCopy_#####(Feb01)[.]one.
A fake button then prompts the user to double-click to download the attachment. The hackers can then run the embedded HTA attachment file that further retrieves the QakBot payload.
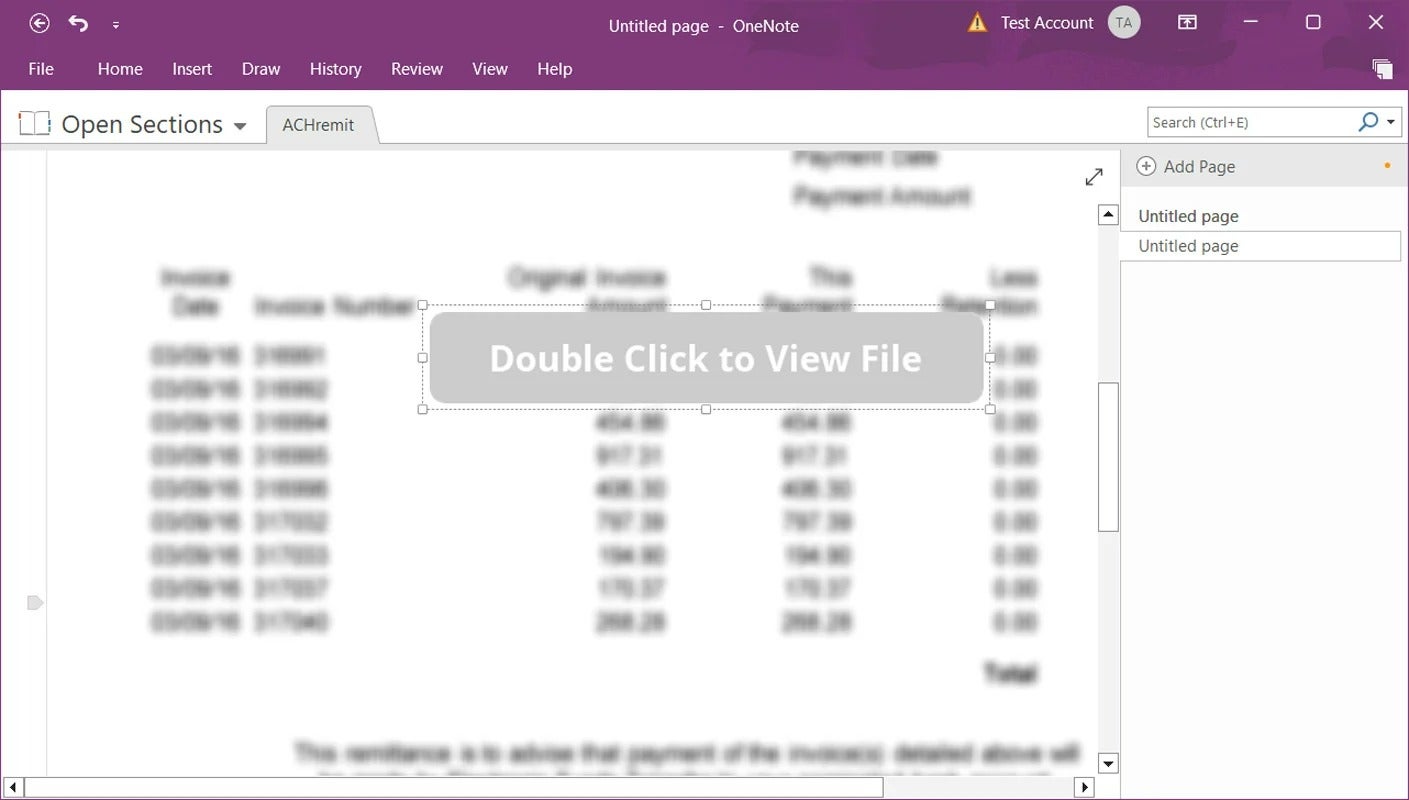
Example of a malicious Microsoft OneNote attachment. Sourced from BleepingComputer
After being launched, those attachments execute commands on the device to download and install QBot. Most of the .hta files contain identical scripting language and instructions for the rest of the attack to follow. The HTA file script uses the legitimate curl.exe application to download a QBot payload to the C:\ProgramData folder and is then executed using Rundll32[.]exe. The QakBot payload then injects itself into the Windows Assistive Technology manager (AtBroker.exe) to conceal its presence and evade detection from AV tools running on the device.
About Sangfor
Sangfor Technologies is a world-class cybersecurity and cloud computing company that offers intensive and advanced Anti-Ransomware prevention and state-of-the-art IT infrastructure. Protect your data and network from malware using the Sangfor Next-Generation Firewall (NGFW) integrated with Endpoint Security to identify malicious files at both the network level and endpoints and so much more. For more information on Sangfor’s cybersecurity and cloud computing solutions, please visit www.sangfor.com.
Frequently Asked Questions
QakBot is a malware that was initially a banking trojan used to steal financial credentials. Its modular design helps it deliver and install malicious software on computers in several ways. QakBot attacks create a large botnet of the infected computers under the hacker’s control.
QakBot malware spreads laterally through the use of emails with malicious links or attachments. These infected emails were sent through breached accounts and looked legitimate. This would fool the receiver into trusting them and clicking on the infected attachments.
QakBot is very good at hiding its tracks. The QakBot payload is not executed in areas with virtualization, Windows Registry keys, or specific cybersecurity products. This allows it to stay concealed. Seeing an unauthorized run key in the Windows Registry is one of the ways you could point out a Qakbot compromise. These run keys automatically execute a program when a user logs on and the Qakbot malware needs to create an entry to auto-start itself.
According to CISA, QakBot will set up persistence through these keys:
- Qbot will delete this key when running and set it back up before the computer restarts: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<random_string>
- QakBot will also write its binary back to disk to maintain persistence in the following folder: C:\Users\<user>\AppData\Roaming\Microsoft\<random_string>\
- QakBot will write an encrypted registry configuration detailing information about the bot to the following registry key: HKEY_CURRENT_USER\Software\Microsoft\<random_string>
The agency also has a list of IP addresses that have obtained access to victim computers. Organizations are encouraged to review any connections with these IP addresses.
Safeguarding yourself from the QakBot malware – or any malware – requires a set of cyber hygiene practices to ensure the best cybersecurity for your network. These can include:
- Changing and updating passwords to any breached accounts.
- Using strong passwords that are regularly changed and kept secure.
- Having an incident response plan to backup data and sensitive files.
- Never click on downloads or attachments that are suspicious.
- Use multi-factor Authentication on all your accounts.
- Keeping all software and systems updated.
- Using logging tools for network traffic.
- Auditing user accounts for access privileges.
- Disabling hyperlinks in received emails.





