Sangfor Botnet Detection
Background
No savvy hacker launches attacks from their personal IP address unless they want to be caught. To maximise the effect and longevity of attacks, hackers command an army of botnets to carry out their malicious activities like DDoS, ransomware infection or network scanning to detect valuable assets and vulnerabilities.
Command and Control is the primary communication vehicle employed to control these botnets. While these C&C networks once operated from static IP addresses, hackers have recently responded to increasingly sophisticated security advances by transforming Domain Generating Algorithms (DGA) into C&C servers. Botnets communicate with C&C servers by sending out a dynamic domain name, predefined by an algorithm only known to the hackers. These DNS requests change quickly and often and are extremely difficult to detect using the traditional firewall and threat intelligence.
* Picture on the top is sourced from virustotal.com (March 2018)
Botnet Detection Innovation Overview
How does Sangfor scan for and detect Botnets in your network?Sangfor's Neural-X uses a set of advanced deep learning, visual calculation and flow analysis technologies to enable more effective Botnet Detection and scanning.
Deep Learning:
Deep learning is a complex element of machine learning inspired by the function of interconnecting neurons in the human brain. Evolution of Machine Learning and an element of AI, it teaches itself to make more accurate and faster predictions by observing, processing and analysing massive amounts of data.
Sangfor uses Deep Learning to break down cryptic domain names into vectors. Unlike other natural language processing techniques which primarily focuses on determining benign or malicious malware, Sangfor’s Deep Learning models take the malware family into account. Through a process of vector association, we are able to detect domain names used by similar malware families. Over time, Deep Learning teaches itself every time it is executed, resulting in the identification of many previously undetected malicious domain names.
Visual Calculation:
Families of malware return to their original families or relative domain names for C&C communications. By creating an association map of the domain names, Sangfor is able to detect similar domain names used by malware families.
Flow Analysis:
Malware typically generates abnormal data traffic when communicating with C&C servers. Sangfor’s ZSand analyses, observes and captures these activities to determine if a system is under attack from a controlled botnet, which would display very different behaviour compared to a human user. The evidence collected is then processed by the flow analysis engine to discover malicious behaviour patterns. Confirmed evidence of IOC of IP, URL and DNS are then shared through the Sangfor Threat Intelligence system for the benefit of all customers.
Botnet Detection Results
A combination of the above techniques uncovers significantly more malicious domain names compared to other popular Botnet Scanning services. Sangfor’s Botnet Detection tool has already uncovered several new malicious domain names, as illustrated below in a comparison between malicious domain names discovered by Sangfor and VirusTotal.
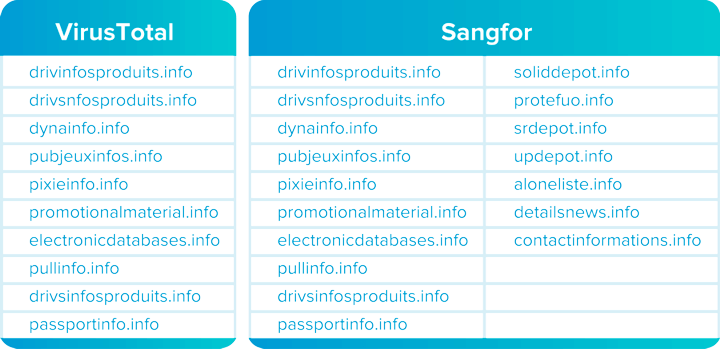
Our Advantages
Neural-X Botnet Detection has uncovered over 1 million malicious domain names, with additional discoveries daily.

