1. Overview of Cactus Ransomware
| Malware Family |
Cactus |
|---|---|
| Threat Type |
Ransomware |
|
Description |
The Cactus ransomware gains initial access through a known vulnerability in Fortinet VPN devices. What sets it apart from other ransomware is that the attackers utilize a batch script to execute the ransomware sample using 7-Zip. Additionally, it encrypts itself to evade detection. |
2. Analysis of Cactus Ransomware
2.1 Introduction of Cactus Ransomware
Sangfor FarSight Labs recently captured and analyzed a sample of the Cactus ransomware family, which has been active since at least March of 2023. Attackers gain initial access through a known vulnerability in Fortinet VPN devices. The attack chain in one of the incidents is as follows:
- Gain initial access by exploiting a vulnerability in a Fortinet VPN device, then immediately create an SSH backdoor for persistence using a scheduled task.
- Identify hosts in the entire environment using SoftPerfect Network Scanner and ping them to check for their availability.
- Query the IP addresses, user information, and security event logs of computers in the domain using PowerShell commands, saving the results in separate files.
- Gain access to the target computer using Splashtop or AnyDesk.
- Manage and monitor multiple target computers using SuperOps RMM software.
- Simulate attacks and test the security of the target system using Cobalt Strike.
- Establish an encrypted communication channel using Chisel.
- Exfiltrate credentials from the user's web browser and LSASS memory dump.
- Send sensitive data from file sharing servers in the environment to MEGA (cloud storage) servers using Rclone.
- Deploy the ransomware to all accessible hosts using PsExec.
2.2 Analysis
2.2.1 MITRE ATT&CK
| Tactic | Technique | Sub-Technique | Operation |
|---|---|---|---|
| Initial Access (TA0001) | Exploit Public-Facing Application (T1190) | N/A | Exploit a vulnerability in Fortinet VPN devices to gain initial access |
| Execution (TA0002) | Command and Scripting Interpreter (T1059) | Windows Command Shell (T1059.003) | Use a series of Windows commands, e.g., ping |
| Power Shell (T1059.001) | Collect internal network information using PowerShell | ||
| Scheduled Task/Job (T1053) | Scheduled Task (T1053.005) | Execute the ransomware using a scheduled task | |
| Native API (T1106) | N/A | Execute functions using multiple system API functions, e.g., GetLogicalDriveStringsW | |
| Persistence (TA0003) | Create Account (T1136) | Local Account (T1136.001) | Create an administrator account using a batch script |
| Defense Evasion (TA0005) | Impair Defenses (T1562) | Disable or Modify System Firewall (T1562.004) | Disable or turn off the system firewall |
| Disable or Modify Tools (T1562.001) | Terminate antivirus software, e.g., Bitdefender | ||
| Obfuscated Files or Information (T1027) | Software Packing (T1027.002) | Pack the ransomware using UPX 4.02 | |
| Indicator Removal (T1070) | File Deletion (T1070.004) | Delete relevant files after the ransomware is executed | |
| Credential Access (TA0006) | Credentials from Password Stores (T1555) | Credentials from Web Browsers (T1555.003) | Dump credentials from the user's web browser |
| OS Credential Dumping (T1003) | LSASS Memory (T1003.001) | Obtain credentials through LSASS memory dump | |
| Discovery (TA0007) |
System Network Connections Discovery (T1049) | N/A | Enumerate all connected drives |
| Remote System Discovery (T1018) | N/A | Search for domain controllers and remote services in the target environment using various scans and queries | |
| Process Delivery (T1057) | N/A | Enumerate whitelisted processes | |
| File and Directory Discovery (T1083) | N/A | Query specified files, folders, and file extensions | |
| Lateral Movement (TA0008) | Software Deployment Tools (T1072) | N/A | Use remote management tools like SuperOps RMM and AnyDesk |
| Lateral Tool Transfer (T1570) | N/A | Deploy the ransomware to other machines using PsExec | |
| Collection (TA0009) | Automated Collection (T1119) | N/A | Collect internal network information using a batch script |
| Exfiltration (TA0010) | Exfiltration Over Web Service (T1567) | Exfiltration to Cloud Storage (T1567.002) | Exfiltrate files and sensitive data to MEGA cloud storage using Rclone |
| Command and Control (TA0011) | Remote Access Software (T1219) | N/A | Gain access to the target computer using Splashtop or AnyDesk |
| Proxy (T1090) | N/A | Create a SOCK5 proxy between infected hosts using the Chisel tool | |
| Impact (TA0040) | Data Encrypted for Impact (T1486) | N/A | Encrypt files on the computer |
2.2.2 Analysis of Techniques
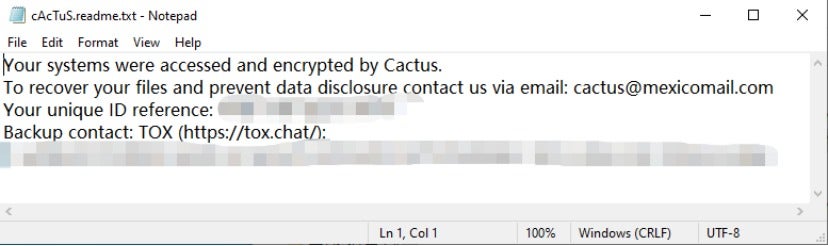
After the sample is launched, it encrypts files in the system and releases a ransom note file. The names of files to be encrypted are appended with the extension ".cts0". After encryption, the extension changes from ".cts0" to ".cts1". The ransom note file is named "cAcTuS.readme.txt". The ransom note prompts the victim to communicate with the attacker via email or TOX with their unique ID to recover their files and prevent data disclosure. However, it does not specify the ransom amount or payment method.
The content of the cAcTuS.readme.txt ransom note is as follows:
Parameters
The sample can accept the following parameters listed here with their respective meanings:
| Parameter | Description |
|---|---|
| -r | C:\ProgramData\ntuser.dat (configuration file) |
| -i | AES key for decrypting the RSA public key (optional) |
| -s | Copy itself to the C:\ProgramData\ directory |
| -t | Number of threads for encryption |
| -d | Path for encryption |
| -f | Encrypt a single file |
| -e | Set the maximum file size for encryption |
Drive Enumeration
The following functions are used to enumerate the logical drives on the computer. First, the GetLogicalDriveStringsW function is used to retrieve a list of logical drives. Then, the GetDriveTypeW function is used to check the type of each drive, excluding CD/DVD drives from encryption.

Create the Ransom Note File
The following function creates the ransom note file.

Persistence
The following function creates a scheduled task named "Updates Check Task" that runs every 5 minutes. This task is used to run the ransomware as SYSTEM.

File Path Normalization
The purpose of this function is to convert file paths into a standardized format for subsequent operations. Specifically, this function checks if the file path begins with "\\?\" or "\", and if so, no further action is taken. Otherwise, it adds "\\?\" or "\\?\UNC\" to the beginning of the file path to support long paths and paths of network shared folders.

Encryption Mode
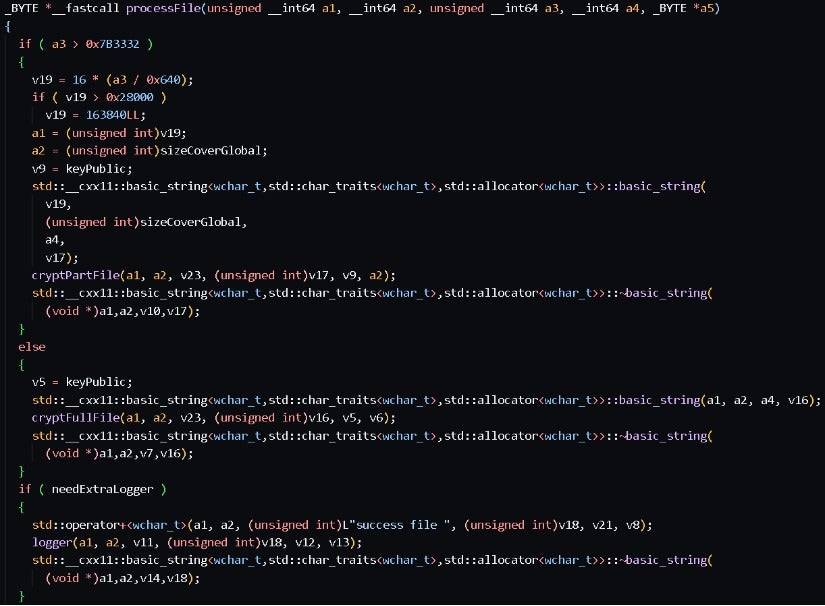
The function shown in the figure below first checks if the file size is larger than 0x7B3332 (approximately 125MB). If it is, the file is divided into several chunks for encryption. Otherwise, the entire file is encrypted. When the chunk size exceeds 0x28000 (approximately 26.8MB), each chunk is set to a size of 0x28000. Finally, the function concatenates "success file" with the filename of the encrypted file and logs it.
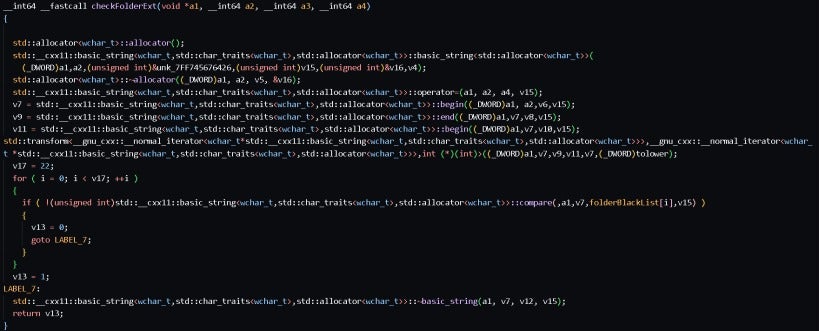
The following function checks if a folder name is on the blacklist. The ransomware program avoids encrypting files in folders on the blacklist.
The following folders and files are excluded from encryption:
1.$recycle.bin
2.system volume information
3.windows
4.tmp
5.temp
6.thumb
7.winnt
8.windows.~bt
9.windows.old
10.perflog
11.perflogs
12.boot
13.programdata
14.packages
15.efi
16.windowsapps
17.microsoft
18.windows defender
19.microsoft shared
20.internet explorer
21.tor browser
22.Ctslck
23.CaCtUs.ReAdMe.txt
24.desktop.ini
25.update.log
26.ntuser.dat
The following function checks if the file extension of a traversed file matches any extension on the blacklist. The ransomware program avoids encrypting files with file extensions on the blacklist.

Files with the following extensions are excluded from encryption:
1.exe
2.dll
3.lnk
4.sys
5.msi
6.bat
7.cts0
8.cts1
The following function utilizes the Windows API functions RmStartSession, RmRegisterResources, RmGetList, RmShutdown, and RmEndSession to terminate processes that are occupying specific files.
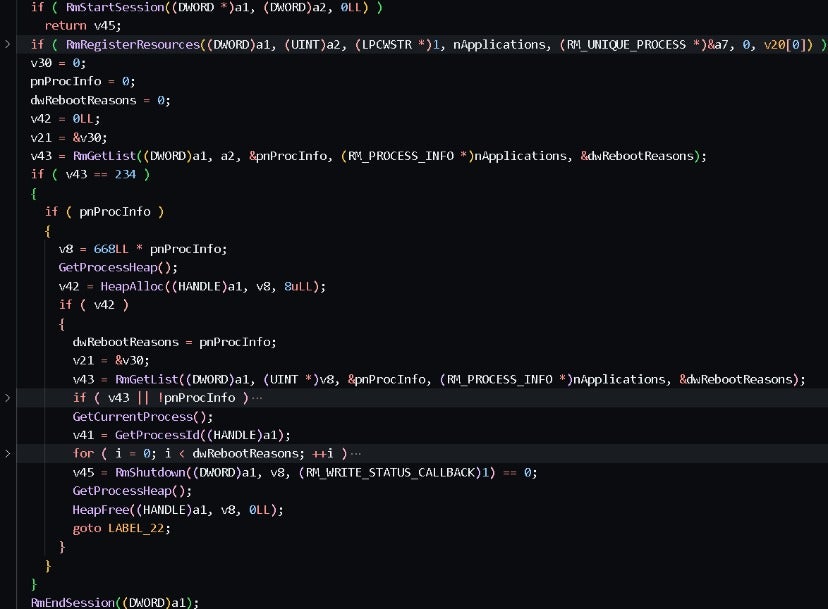
Files occupied by the following processes are excluded from encryption:
1.spoolsv.exe
2.explorer.exe
3.sihost.exe
4.fontdrvhost.exe
5.cmd.exe
6.dwm.exe
7.LogonUI.exe
8.SearchUI.exe
9.lsass.exe
10.csrss.exe
11.smss.exe
12.winlogon.exe
13.services.exe
14.conhost.exe
Encryption Algorithm
Cactus ransomware uses the AES-256-GCM algorithm to decrypt the input AES key (value for -i parameter). The decrypted value serves as the RSA key. The RSA key is then copied to a specified memory address to check its validity. If the key is valid, the public portion of the RSA key is returned.

The encryption process of the Cactus ransomware is as follows:
- Create a ransom note in each traversed directory that is not on the blacklist.
- Convert long paths into standardized paths.
- Check if a file belongs to a directory excluded from encryption, if it is an excluded file, or if it has an excluded file extension. If any of these conditions are true, skip the file and proceed to the next file. If none of the conditions are true, encrypt the file with the following steps.
- Append the extension ".cts0" to the ename of the file to be encrypted.
- Encrypt the file using the AES-256-CBC encryption algorithm, and the key is encrypted using the RSA-4096 encryption algorithm.
- Replace the original source file with the encrypted version, changing the file extension from ".cts0" to "cts1".
2.3 Indicators of Compromise (IOCs)
MD5
1.5737cb3a9a6d22e957cf747986eeb1b3
2.e28db6a65da2ebcf304873c9a5ed086d
3.949d9523269604db26065f002feef9ae
4.eba1596272ff695a1219b1380468293a
5.1add9766eb649496bc2fa516902a5965
6.2611833c12aa97d3b14d2ed541df06b2
7.de6ce47e28337d28b6d29ff61980b2e9
2.4 Sangfor Solution
The following Sangfor products and services provide protection against Cactus Ransomware:
- Sangfor Endpoint Secure
About Sangfor FarSight Labs
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





