1. Summary
| Vulnerability Name | Alibaba Fastjson Remote Code Execution Vulnerability (CVE-2022-25845) |
|---|---|
| Release Time | August 29, 2022 |
| Component Name | Alibaba Fastjson |
| Affected Versions | Before Fastjson 1.2.83 |
| Vulnerability Type | Remote Code Execution |
| Exploit Condition | User Authentication: Not required. Precondition: Default. Trigger Mode: Remote. |
| Description | Exploit Difficulty: Low. Severity: Critical. Attackers can perform remote code execution. CVSS Score: 9.8 (NVD) |
2. About CVE-2022-25845
2.1 Introduction
Fastjson is Alibaba's open-source JSON parsing library. It parses strings in JSON format, supports serialization of Java Beans into JSON strings, and deserializes from JSON strings to JavaBeans.
2.2 Summary
On May 23, 2022, Sangfor FarSight Labs received a notice about the Alibaba Fastjson Remote Code Execution Vulnerability (CVE-2022-25845), classified as critical with a CVSS score of 9.8 (NVD). Versions of the package com.alibaba:fastjson before 1.2.83 are vulnerable to Deserialization of Untrusted Data by bypassing the default autoType shutdown restrictions, which is possible under certain conditions. Exploiting this vulnerability allows attacking remote servers.
3. Affected Versions
Before Alibaba Fastjson 1.2.83
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
Option 1
If it is a Maven project, check whether the dependencies used in the project pom.xml file contain the following content, and if so, check whether the version used is affected.
<dependency>
com.alibaba
fastjson
1.2.xx
</dependency>
Option 2
Search the files in the current project directory for the fastjson-x.x.xx.jar package and check whether the version is affected.
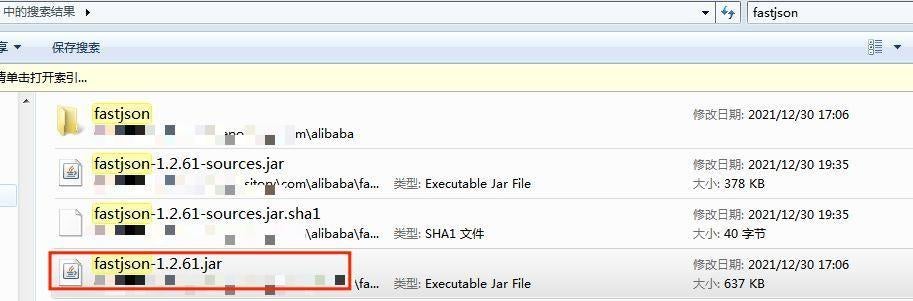
For Linux systems, execute find ./ -name "fastjson*.jar" in the current project and check whether the version is affected.
4.1.2 Fastjson Solution
Users can update their affected products to the latest version to fix the vulnerability at https://github.com/alibaba/fastjson/releases
4.1.3 Workaround
If upgrading is not possible, users can enable safeMode. When safeMode is turned on, AutoType is disabled.
Enable safeMode using one of the three following options:
Option 1: Configure in Code
ParserConfig.getGlobalInstance().setSafeMode(true);
Option 2: Use JVM startup parameters
-Dfastjson.parser.safeMode=true
Note: If there are multiple package name prefixes, separate them with commas.
Option 3: Configure through the fastjson.properties file
fastjson.parser.safeMode=true
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Alibaba Fastjson Remote Code Execution vulnerability (CVE-2022-25845):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services perform real-time monitoring of assets affected by the Alibaba Fastjson Remote Code Execution vulnerability (CVE-2022-25845):
5. Timeline
On May 23, 2022, Sangfor FarSight Labs received a notice about the Alibaba Fastjson Remote Code Execution vulnerability (CVE-2022-25845).
On May 23, 2022, Sangfor FarSight Labs released a vulnerability alert.
On August 29, 2022, Sangfor FarSight Labs released an updated vulnerability alert.
6. Reference
https://nvd.nist.gov/vuln/detail/CVE-2022-25845
https://cve.report/CVE-2022-25845
https://github.com/alibaba/fastjson/wiki/security_update_20220523
https://github.com/alibaba/fastjson/wiki/fastjson_safemode_en





