1. Summary
| Vulnerability Name | Apache Commons Text Remote Code Execution Vulnerability (CVE-2022-42889) “Text4Shell” |
|---|---|
| Release Time | October 14, 2022 |
| Component Name | Apache Commons Text |
| Affected Versions | 1.5 ≤ Apache Commons Text ≤ 1.9 |
| Vulnerability Type | Remote Code Execution |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: None User Interaction: None |
| Impact | Severity: CVSS v3 Base Score 9.8 (Critical) Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-42889
2.1 Introduction
Apache Commons Text is a popular open-source Java library with an "interpolation system" that allows developers to modify, decode, generate, and escape strings based on inputted string lookups.
2.2 Summary
On October 14, 2022, Sangfor FarSight Labs received a notice about an Apache Commons Text remote code execution vulnerability (CVE-2022-42889), dubbed “Text4Shell” and classified as critical with a CVSS Score of 9.8.
Apache Commons Text performs variable interpolation, allowing properties to be dynamically evaluated and expanded. The standard format for interpolation is "${prefix:name}", where "prefix" is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation. In vulnerable versions of Apache Commons Text, (versions 1.5 through 1.9), the set of default Lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers. These lookups are:
- "script" - execute expressions using the JVM script execution engine (javax.script)
- "dns" - resolve DNS records
- "url" - load values from URLs, including from remote servers.
Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution when processing malicious input.
2.3 Exploits of CVE-2022-42889 “Text4Shell”
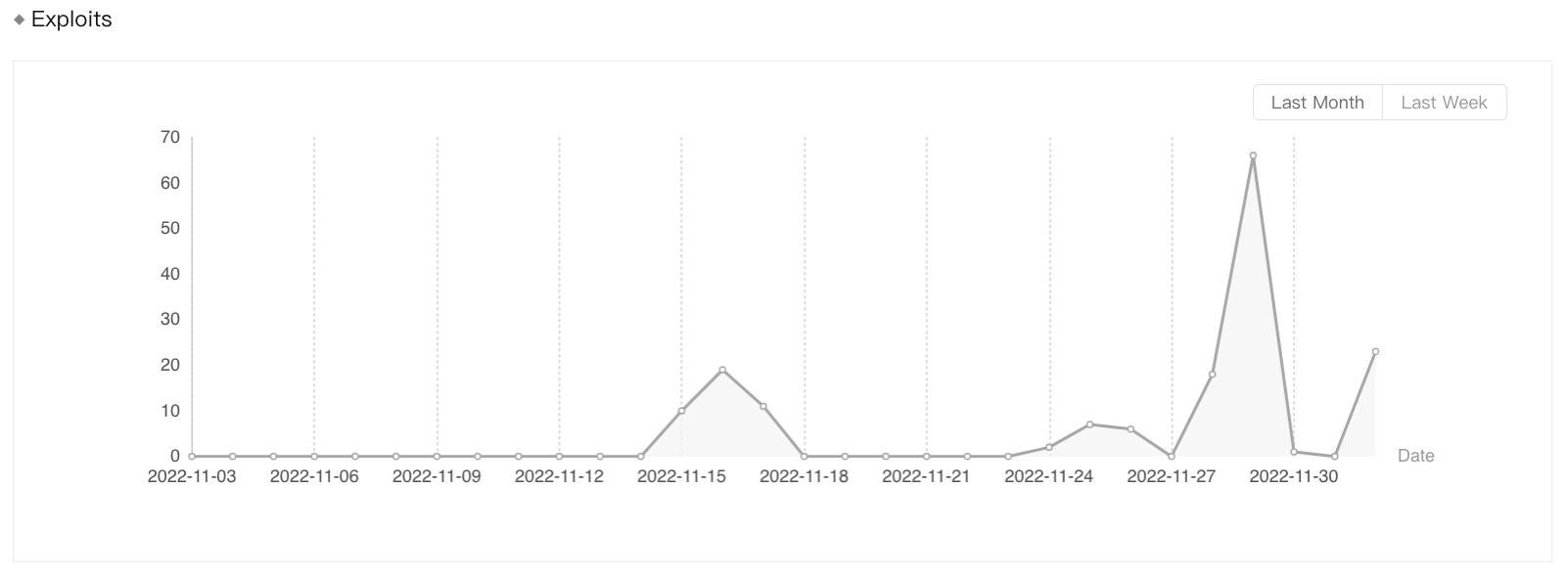
Figure 1. Exploits of CVE-2022-42889 “Text4Shell” detected by Sangfor from November 3 to December 2, 2022.
For the most up-to-day exploit statistics, please visit the following page (registration required).
3. Affected Versions
1.5 ≤ Apache Commons Text ≤ 1.9
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
Option 1
Do a global search for commons-text. If commons-text-{version}.jar exists and the version is below 1.10.0, then users may be affected by this vulnerability.
Option 2
If the project is compiled by Maven, pom.xml should be in the root directory of the project.
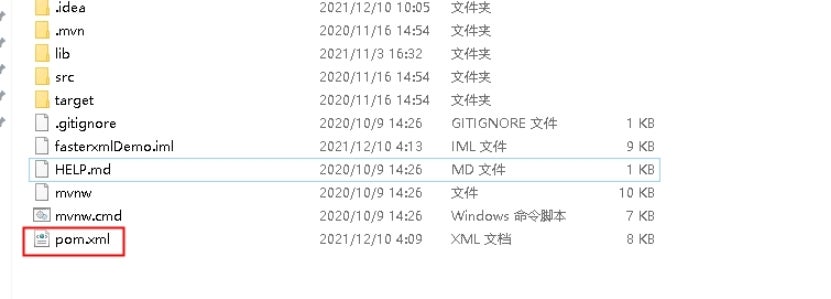
Open the pom.xml file, and search for commons-text in this file. If it is found, and the string inside the <version> tag is below 1.10.0, then users may be affected by this vulnerability. (The Commons Text version in the figure below is 1.10.0, which is not affected by the vulnerability.)
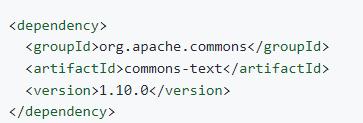
4.1.2 Remediation Solutions
Apache has released Commons Text version 1.10 to fix this vulnerability. Users can download the latest version from the following link: https://commons.apache.org/proper/commons-text/download_text.cgi
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the remote code execution vulnerability in Apache Commons Text (CVE-2022-42889):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services provide protection against the remote code execution vulnerability in Apache Commons Text (CVE-2022-42889):
- Sangfor Next Generation Application Firewall (NGAF)
- Sangfor Cyber Guardian (Managed Detection and Response)
5. Timeline
On Oct 14, 2022, Sangfor FarSight Labs received a notice about the remote code execution vulnerability in Apache Commons Text (CVE-2022-42889).
On Oct 14, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://nvd.nist.gov/vuln/detail/CVE-2022-42889
https://commons.apache.org/proper/commons-text/download_text.cgi
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





