Overview of the LockBit 3.0 Ransomware Attack
In early July 2023, a Sangfor customer in Italy experienced a ransomware attack carried out by the LockBit ransomware group. The education sector customer was using Sangfor’s endpoint detection and response (EDR) product, Endpoint Secure. The attack resulted in the encryption of over 50 computers by the LockBit 3.0 variant, also known as LockBit Black. The victim received a ransom note demanding payment in exchange for their data, as shown below.
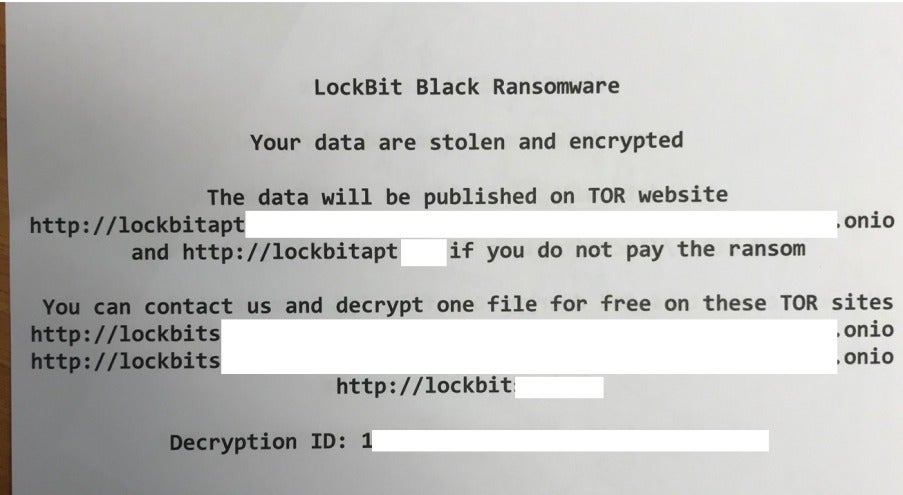
Investigation into the LockBit 3.0 Ransomware Attack
The Sangfor Cyber Guardian Incident Response (IR) team was swiftly deployed to investigate the incident and assist the customer in restoring their operations.
During the investigation, it was discovered that the TDSSKiller tool was loaded onto the compromised machines prior to ransomware infection and encryption. TDSSKiller is a free tool developed by the cybersecurity firm Kaspersky for detecting and removing rootkits. It is also capable of disabling stubborn malicious processes via command prompt execution, as shown below.

Source: https://support.kaspersky.com/common/disinfection/5350#block1
During incident response, the Sangfor Cyber Guardian IR team first identifies the ransomware family to understand its common tactics, techniques, and procedures (TTPs). This allows the IR team to determine the root cause and trace the chain of events that led to the ransomware compromise.
The article "Dark Web Profile: LockBit 3.0 Ransomware" on SoCRadar outlines the tools and propagation techniques used by LockBit 3.0, including TDSSKiller. However, there are currently no resources available that provide a detailed explanation of how TDSSKiller is specifically abused in LockBit attacks. This information was absent to the general public on ANY.RUN (an interactive malware execution virtual platform), Joe Sandbox, and other websites that typically publish such details as of 14 July 2023. The closest mention of LockBit 3.0 leveraging the TDSSKiller tool was found in the above-mentioned SoCRadar article and on the Cybersecurity and Infrastructure Security Agency (CISA) website.
The lack of published detailed information on its misuse prevents security experts and end users from understanding how TDSSKiller is exploited for malicious purposes. This is significant given that TDSSKiller is a legitimate portable scanner used to detect and remove rootkits released by Kaspersky and available on their website.
However, further exploration by Sangfor revealed that the Kaspersky TDSSKiller tool is capable of terminating antivirus and EDR software through a command line script or batch file. The figure below demonstrates the removal of Microsoft Defender by executing the command "tdsskiller.exe -dcsvc windefend".
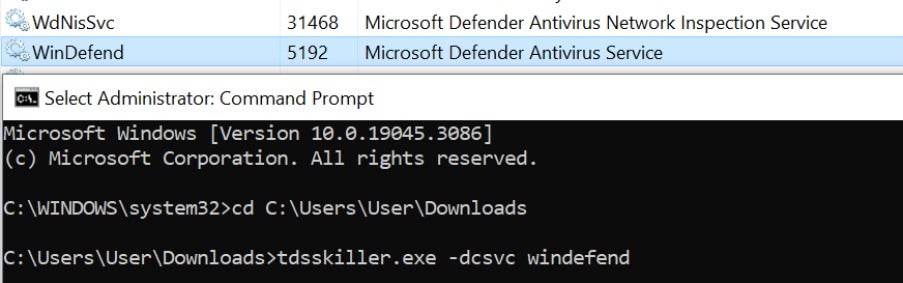
The "-dcsvc <service_name>" command deletes the specified service, removing the registry keys and executables associated with the service and software, as shown in the test conducted on Windows Defender Antimalware Client Version: 4.18.23050.5.

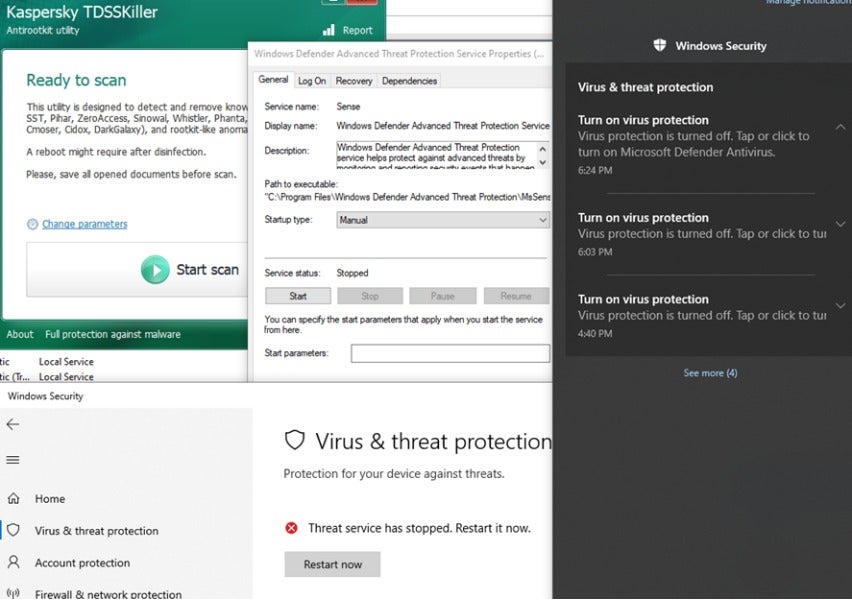
After rebooting, Windows Defender was no longer working, as shown below by system alerts and service status.
From our incident response investigation, the following screenshot illustrates that TDSSKiller.exe was loaded onto a compromised machine before the LBB.exe LockBit payload file was executed to start the ransomware infection. System logs confirm that the EDR software on this host was disabled prior to the start of the LockBit 3.0 ransomware infection and encryption. This is evidence that TDSSKiller terminated the endpoint security software, enabling the unobstructed deployment of ransomware.
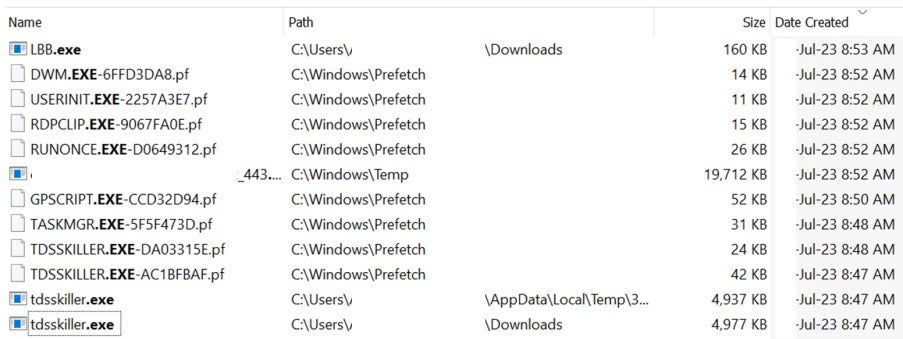
Figure 1 - tdsskiller.exe tool was loaded onto compromised computer first before LBB.exe was later imported to launch the attack.

Figure 2 - LBB.exe associated to LockBit ransomware execution file
The TDSSKiller tool was also tested against third-party endpoint security software, proving to be effective in successfully disabling it, as shown below. The termination of this security software is not feasible using Process Hacker or a simple "end task" or "end process tree" in the Windows Task Manager, which further demonstrates the capabilities of TDSSKiller.

Figure 3 - Failed to terminate a tested third-party security software process through Task Manager

Figure 4 - Successfully removed the third-party security software with TDSSKiller
With LockBit 3.0 actively in the wild on top of other ransomware families still exploiting the MOVEit vulnerability, it is a matter of time before more APT groups and ransomware families adopt TDSSKiller or similar tools to bypass endpoint security.
Remediation Recommendations
The following recommendations are provided as part of immediate remediation or risk reduction measures:
- Ensure your endpoint security can detect, identify, and alert you upon finding these files in your network. The file hashes are shared below.
- Set up alert notifications in your endpoint security manager to alert when endpoint security agents go offline and/or computers shut down on a random basis.
- Use Sangfor Cyber Guardian MDR service, employing industry threat response best practices, to monitor your critical assets and Endpoint Secure agents around the clock.
- Employ other security controls in the network such as network detection response (NDR) tools like Sangfor’s Cyber Command for a defense-in-depth approach to detect and respond quickly upon detection of common ransomware TTPs.
- Sangfor Endpoint Secure customers should do the following immediately:
- Enable alerts within the Endpoint Secure Manager to notify if any agent is disabled or disconnected from the network.
- Set up a policy to auto restart a terminated agent after a computer reboot.
- Run daily scans for the detection of the malicious files listed below in item #7.
- Enable auto update on the virus engine program to immediately receive the latest bugfix.
- If the malicious files below were found on your systems, immediately request Incident Response (IR) service from the Sangfor Cyber Guardian team to identify the compromised entry point, patient zero, and steps to fix security gaps observed from the attack.
- Below are the IOCs for the TDSSKiller tools and LockBit execution file seen in the attack:
LockBit 3.0 IOCs
| Filename |
tdsskiller.exe |
|---|---|
| MITRE ID |
T1562.001 - Impair Defenses: Disable or Modify Tools |
| MD5 Hash |
d76bfd6f8119251cbd940f66c42a1eef |
| SHA256 Hash |
545037aa05c3462adca4f84aebf7cb5780abb18dcd69e6e3acc453921ec7d18c |
| Filename |
TDSSKiller.exe |
| MITRE ID |
T1562.001 - Impair Defenses: Disable or Modify Tools |
| MD5 Hash |
ff1eff0e0f1f2eabe1199ae71194e560 |
| SHA256 Hash |
2d823c8b6076e932d696e8cb8a2c5c5df6d392526cba8e39b64c43635f683009 |
| Filename |
LBB.exe |
| MITRE ID |
T1027.002 - Obfuscated Files or Information: Software Packing |
| MD5 Hash |
a6c5d33c27d11af892793586788ec7e4 |
| SHA256 Hash |
2a8a116da4235a2cb0d7471b697e2eadb858c86c4458a33bbed8247af7ea699a |
Reach out to your local Sangfor office and explore how Sangfor Cyber Guardian can protect you from this and other ransomware or APT threats.





