Investigation Overview
A higher education institution in Pakistan reported a Medusa ransomware attack to Sangfor Cyber Guardian Incident Response (IR) team. The attack infected multiple hosts and essential systems in their network environment.
Before Sangfor’s engagement, another security company attempted to investigate the incident using a paid third-party Digital Forensics (DFIR) Tool Specialized For Incident Response software. However, they were unsuccessful in finding useful information due to missing critical log files from the ransomware infection date. As a result, the D:\ drive on one of the infected servers (SERVER_16) was formatted and restored from backup as the third-party software did not find anything useful and the D:\ drive was required for business usage thereafter.
The screenshot below shows a sample of encrypted files before reformatting and restoration. No Medusa-infected files were left on the server when the Sangfor Cyber Guardian Incident Response (IR) team was engaged to investigate on March 12, 2023, as SERVER_16 had already been restored from backups.
The customer informed the Sangfor IR team that only SERVER_16 was available for the incident response investigation for Sangfor to identify potential leads and evidence associated with the Medusa ransomware attack.
Detailed Observations from Analysis on SERVER_16
On March 12, 2023, it was observed that host SERVER_16 was infected with Medusa ransomware. The customer provided the screenshot below showing that files on the D:\ drive were encrypted and appended with the “.MEDUSA” extension. The screenshot was captured before the drive was restored from backup.
When Sangfor IR team was deployed on March 12, 2023, the affected D:\ drive had been restored from backup, and no other traces of Medusa-encrypted files were found on the remaining drives (C:\ and F:\).
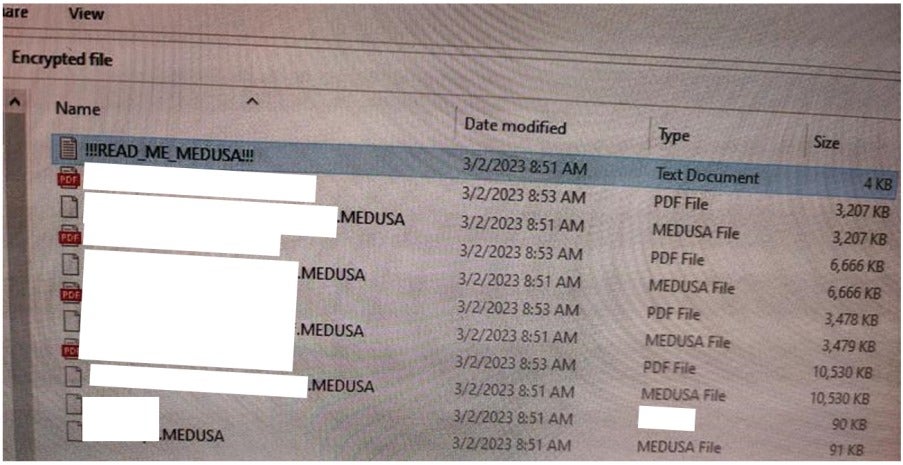
Based on the screenshot, the earliest encryption time occurred on March 2, 2023, at 08:51 GMT+5. This information served as a starting point for identifying the attack vector and tracing malicious activity in the infected host’s system logs.
Windows Security Event Logs: These logs had been overwritten by newer logs due to small event log storage. As of March 12, 2023, the earliest log dated back to March 8, 2023.
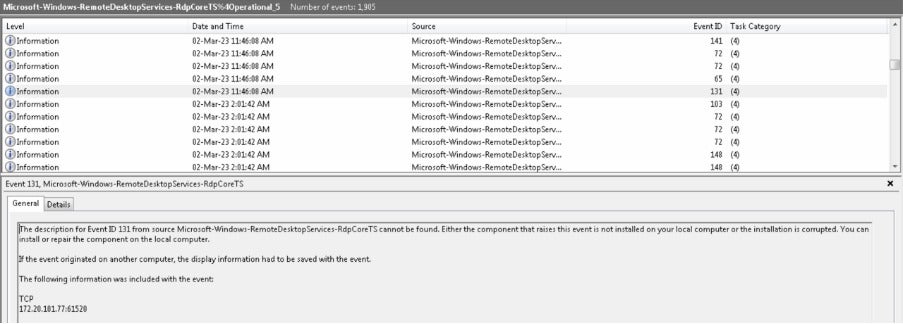
Remote Desktop Protocol (RDP) Logs: RDP logs revealed a remote login from the IP address 172.20.101.77 to the infected host on March 2, 2023, at 08:46 GMT+5 (11:46 GMT+8). The customer’s staff confirmed on March 15, 2023, that this IP address was unknown to them, including who and which workstation it was assigned to.
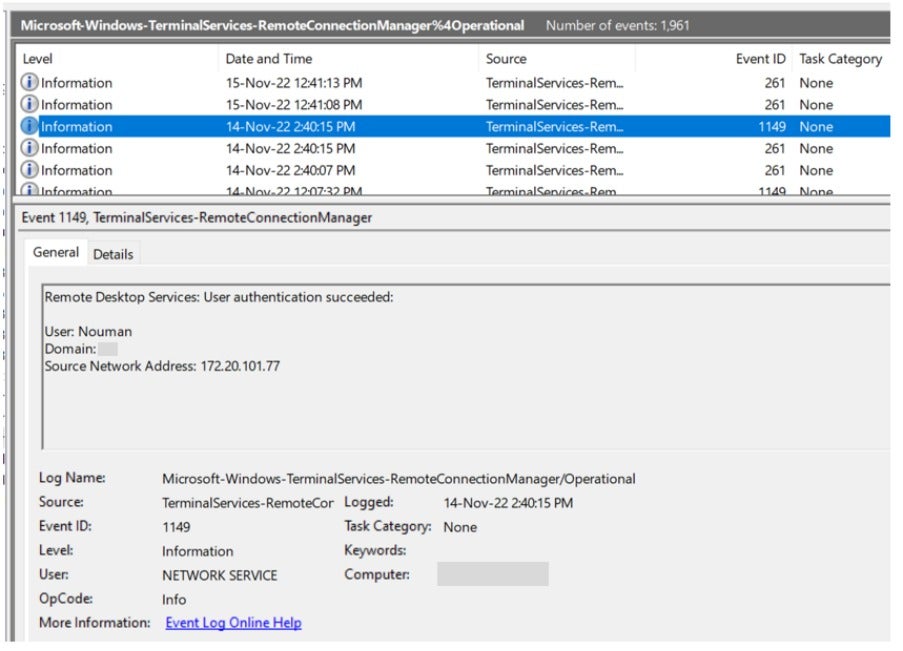
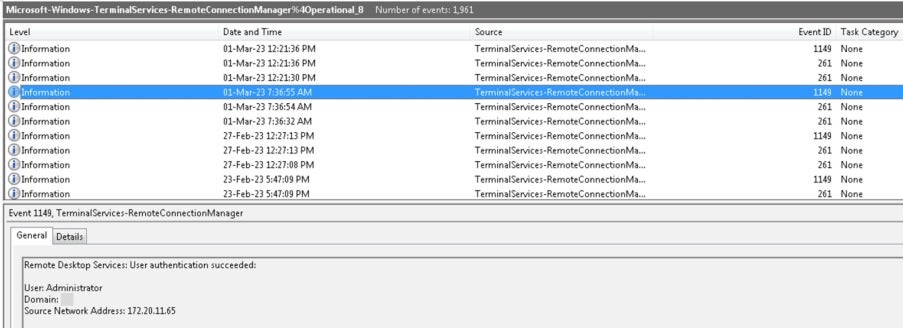
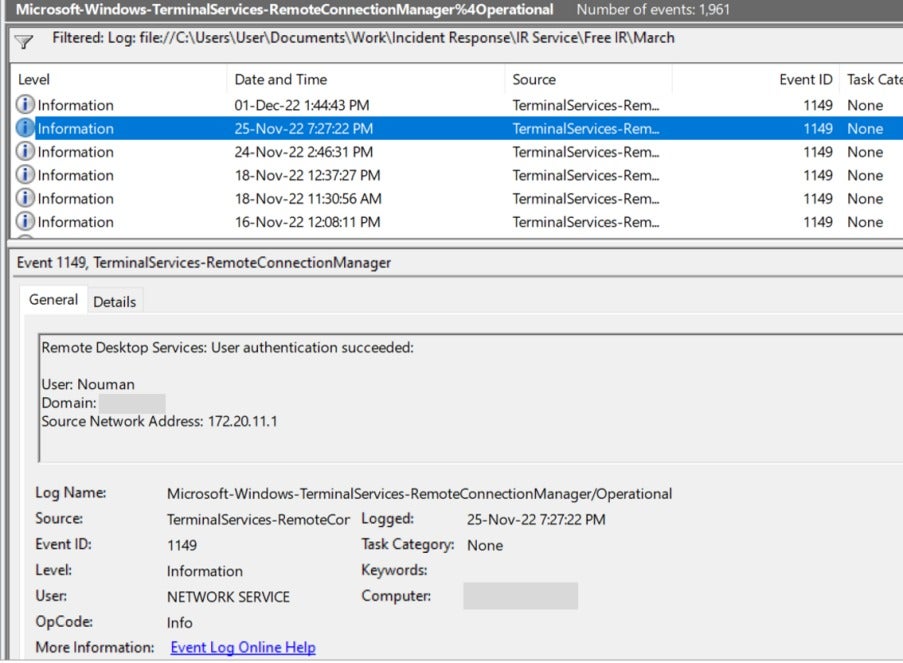
Microsoft-Windows-TerminalServices-RemoteConnectionManager: The earliest record of remote access from 172.20.101.77 was dated November 14, 2022, by the user “Nouman.
We also observed another suspicious login during non-business hours on March 1, 2023, at 04:36 GMT+5 (07:36 GMT+8) from 172.20.11.65 with the account "Administrator." This activity warrants the customer’s internal verification to determine who and where the login originated from and if it was legitimate access by an authorized user or vendor(s).
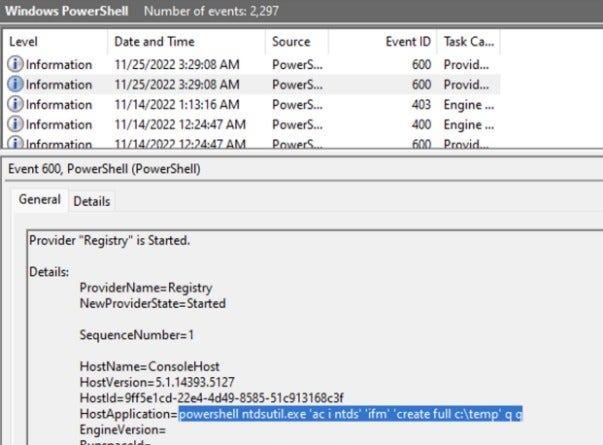
PowerShell Logs: PowerShell logs revealed a series of suspicious historical commands that required further verification by the customer to determine if they were executed with the proper authorization of the company.
On November 25, 2022, a command-line tool called ntdsutil.exe was executed with a series of arguments to create an IFM (Install from Media) backup of the Active Directory database on a domain controller.
Our analysis reveals the following commands executed through ntdsutil.exe:
- "ac i ntds" - This command connects to the Active Directory Domain Services Instance.
- "ifm" - This command switches to the IFM (Install from Media) mode.
- "create full c:\temp" - This command creates a full backup of the Active Directory database and saves it to the C:\temp directory.
- "q" - This command exits the IFM mode and returns to the AD DS Instance context.
- "q" - This command exits ntdsutil.exe.
These commands indicate an attempt to create a full backup of the Active Directory database and save it to the C:\temp directory on the local computer. Note that these commands must be executed on a domain controller, for which administrative privileges are required.
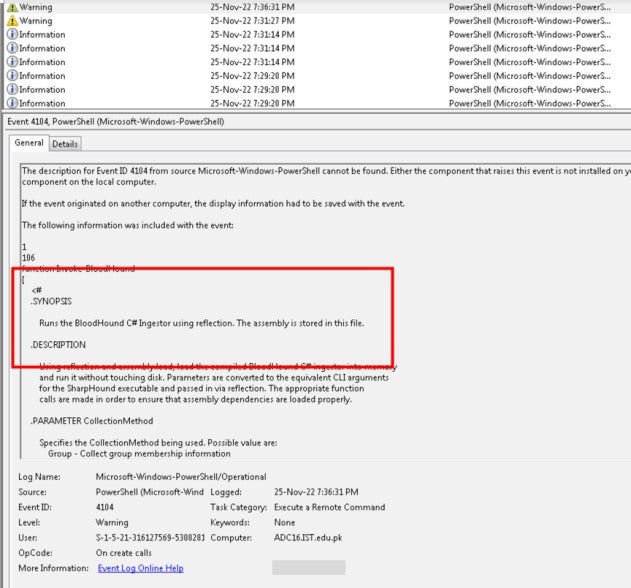
BloodHound Tool: A tool called BloodHound was also discovered running on the infected host on November 25, 2022, based on PowerShell activity logs. Bloodhound is a tool that analyzes Windows Active Directory (AD) environments to identify potential attack paths, commonly abused to compromise high-privileged domain accounts such as domain admins, schema, and enterprise administrator domain accounts.
It does this by visualizing the relationships between various objects in the AD environment and identifying paths that attackers could use to move laterally through the network. The BloodHound C# Ingestor is a component of BloodHound that collects data from AD for analysis.
The Bloodhound script is publicly accessible here: https://github.com/BloodHoundAD/BloodHound
Several related scripts were attempted to be executed from the same directory as the Bloodhound tool on November 25, 2022.
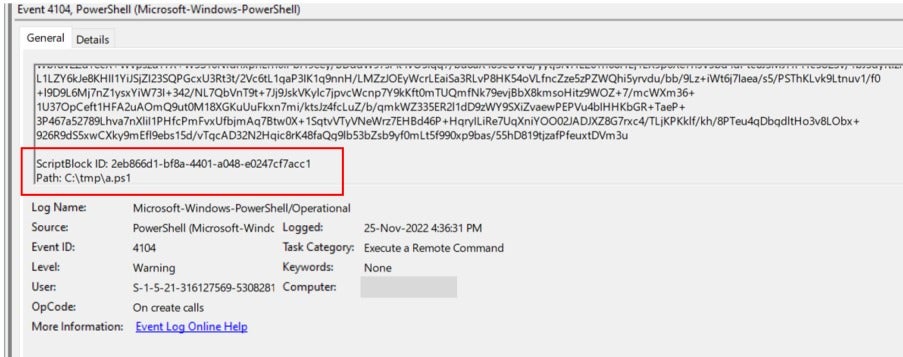
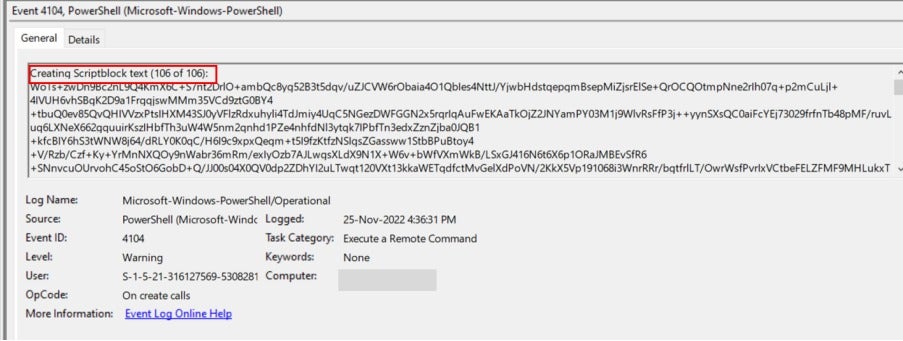
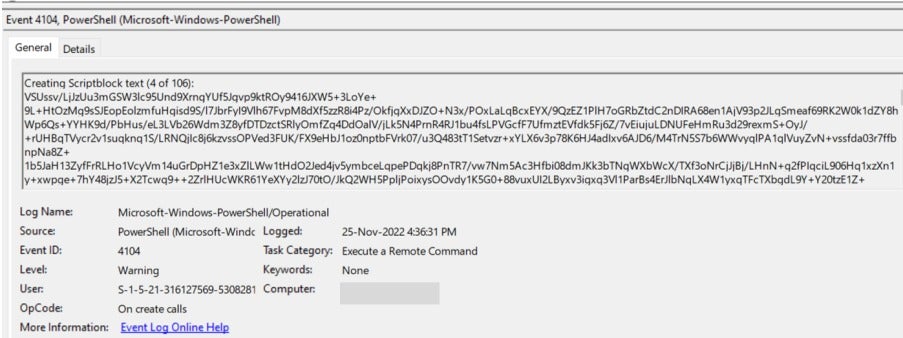
Before the Bloodhound tool execution, there was remote access from the firewall segment (172.20.11.1) on November 25, 2022, at 16:27 GMT+5 (19:27 GMT+8) by the user account named “Nouman,” similar to the RDP event on November 14, 2022.
Analysis Conclusion
Based on the available system logs and the restoration of the infected host prior to investigation by the Sangfor IR team, the following observations were made:
The Medusa Ransomware started encryption before the start of the customer’s working hours in early March 2023.
There were multiple suspicious remote logins from an IP address unknown to the customer due to the DHCP setup. The IP address and host first appeared on November 14, 2022, using a user account with local administrator privileges.
Several suspiciously obfuscated PowerShell scripts were executed from November 2022 to the day of the attack in March 2023, which suggests a period of reconnaissance before executing the attack.
One of the suspicious scripts allowed the attacker to map the entire domain network setup, commonly abused to compromise powerful domain accounts such as domain admin, schema admin, and enterprise admin accounts.
The customer then took over the investigation to first locate the host of the unknown IP address within the network. Other malicious files and tools used in the attack could not be determined because the infected host had been reformatted and restored from backup.
Nevertheless, the customer was provided with recommendations to improve their security controls against commonly abused security gaps based on the Sangfor Cyber Guardian IR team’s experience in various ransomware cases. Our recommendations included, but was limited, to the following:
- Implement endpoint security with multiple anti-ransomware controls. Sangfor Endpoint Secure has various detection, prevention, and containment features against ransomware attacks and suspicious files, such as honeypot sandboxing, anti-brute force, fileless execution protection, and micro-segmentation for detected ransomware-infected files or executables.
- Ensure the log storage size is expanded to fit at least 6-12 months of system logs, preferably in a segmented environment.
- Change administrator-privileged accounts on a periodic basis with a complex password policy.
- Employ continuous threat monitoring or leverage on Sangfor Cyber Guardian MDR service, employing industry threat response best practices, to monitor your critical assets and Endpoint Secure agents around the clock.
- Employ other security controls in the network, such as network detection response (NDR) tools like Sangfor Cyber Command for a defense-in-depth approach to detect and respond quickly upon the detection of common ransomware TTPs.
- Immediately contact the Sangfor Cyber Guardian team for Incident Response (IR) service once any Medusa or ransomware attack is identified to uncover the attack entry point, patient zero, and steps to fix security gaps observed from the attack.





