About the Vulnerability
Introduction
WebLogic is an Application Server produced by Oracle Corporation in the United States. More precisely, it is a middleware based on the Java EE architecture. WebLogic is a Java application server used for the development, integration, deployment, and management of large-scale distributed web applications, network applications, and database applications.
WebLogic introduces the dynamic capabilities of Java and the security standards of the Java Enterprise into the development, integration, deployment, and management of large-scale network applications. It is one of the main Java (J2EE) application server software (Application Server) in the commercial market and is the world's first successfully commercialized J2EE application server. It has the advantages of scalability, rapid development, flexibility, and reliability.
Summary
Recently, Sangfor FarSight Labs received notification that Oracle WebLogic Server has released security patches, fixing a total of 5 security vulnerabilities, including 1 critical vulnerability and 4 high-risk vulnerabilities.
| Number | Vulnerability Name | Affected Version | Risk Level |
|---|---|---|---|
| 1 | Oracle WebLogic Server Remote Code Execution Vulnerability (CVE-2024-21216) |
12.2.1.4.0 14.1.1.0.0 |
Critical |
| 2 | Oracle WebLogic Server Unauthorized Information Disclosure Vulnerability (CVE-2024-21234) |
12.2.1.4.0 14.1.1.0.0 |
High |
| 3 | Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21274) |
12.2.1.4.0 14.1.1.0.0 |
High |
| 4 | Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21215) |
12.2.1.4.0 14.1.1.0.0 |
High |
| 5 | Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21260) |
12.2.1.4.0 14.1.1.0.0 |
High |
Description
Oracle WebLogic Server Remote Code Execution Vulnerability (CVE-2024-21216)
Oracle WebLogic Server contains a remote code execution vulnerability, unauthorized attackers can execute malicious code on the server through T3/IIOP protocol, resulting in server subsidence.
Oracle WebLogic Server Unauthorized Information Disclosure Vulnerability (CVE-2024-21234)
Oracle WebLogic Server contains an unauthorized access vulnerability that allows unauthenticated attackers to obtain sensitive information.
Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21274)
Oracle WebLogic Server contains an unauthorized denial of service vulnerability, which can be exploited by unauthenticated attackers to crash the server.
Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21215)
Oracle WebLogic Server contains an unauthorized access vulnerability, which can be exploited by unauthenticated attackers to crash the server.
Oracle WebLogic Server Unauthorized Denial of Service Vulnerability (CVE-2024-21260)
Oracle WebLogic Server There is an unauthorized access vulnerability, which can be exploited by unauthenticated attackers to crash the server.
Affected Versions
WebLogic is a Java application server used for the development, integration, deployment, and management of large-scale distributed web applications, network applications, and database applications, and it is widely used globally. Assets potentially affected by vulnerabilities are extensively distributed worldwide. The vulnerabilities disclosed this year involve a large number of affected users, resulting in significant impact from the vulnerabilities.
Solutions
Remediation Solutions
Check the System Version
1. Check the WebLogic version
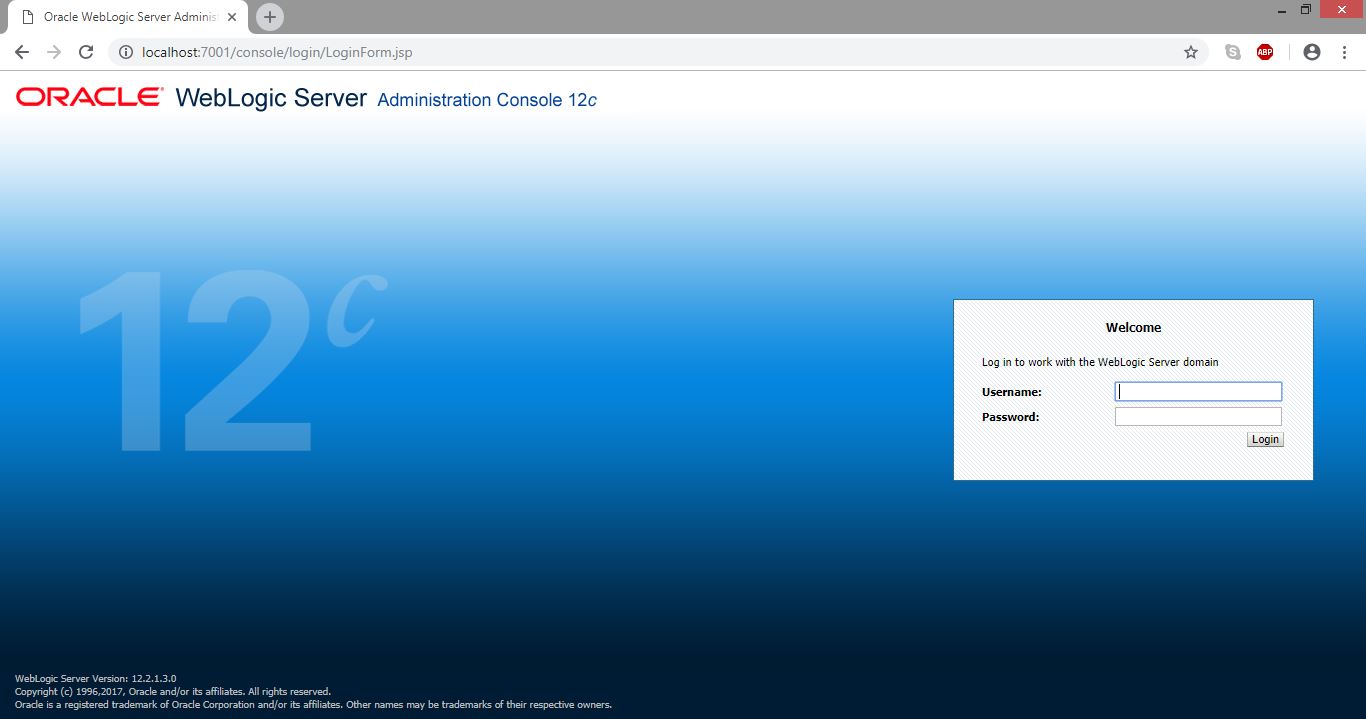
You can check the version by accessing the WebLogic Administration Console page.
2. Check the WebLogic patch version
Users can enter the WebLogic and install the OPatch directory under the home directory to open the command line by entering .\opatch lspatches command for device
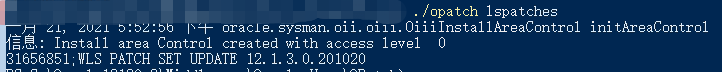
As shown above, the testing device’s patch number is 31656851.
Patching/Updating Method
Affected users are strongly advised to update the GitLab to the latest version(17.4.2, 17.3.5, 17.2.9 or versions above).
Example:Version 12.2.1.3
Step 1 Update the Opatch Patch-upgrading tool
Enter the C:\oracle\Middleware\Oracle_Home\OPatch directory and execute the following command:
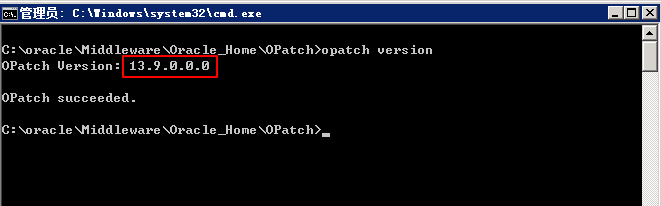
C:\oracle\Middleware\Oracle_Home\OPatch > opatch version
As shown here, if the version is not 13.9.4.0.0, you need to upgrade the Opatch version first, otherwise you can go directly for step 2
Opatch Upgrading method:
Remove the old version of the Opatch
Enter the C:\oracle\Middleware\Oracle_Home directory,
Rename the four directories: OPatch, oracle_common, oui, and inventory
Download and decompress the installation package
Download link:
Since WebLogic is constantly being updated, please download the latest patch from the official website (https://support.oracle.com). You can refer to the following link for specific download methods:
http://blog.itpub.net/31394774/viewspace-2699573
Install the Opatch
Execute the following commands:
java -jar opatch_generic.jar -silent oracle_home=C:\oracle\Middleware\Oracle_Home
Check the installation results
Four directories of OPatch, oracle_common, oui, inventory have been regenerated,
Execute the command again:
C:\oracle\Middleware\Oracle_Home\OPatch > opatch version
Opatch Version was changed to 13.9.4
Step 2 Download and decompress the patch package
The downloaded patch links for this document are as follows:
Since WebLogic is constantly being updated, please download the latest patch from the official website (https://support.oracle.com). You can refer to the following link for specific download methods:
http://blog.itpub.net/31394774/viewspace-2699573
Decompress it to any directory after download.
Step 3 It is recommended to read the README document before patching
Step 4 Stop the WebLogic service
Step 5 Install the patch
Enter the patch pack decompression directory and execute the following command:
C:\oracle\Middleware\Oracle_Home\OPatch\opatch apply
Step 6 Restart the WebLogic service
Restart the WebLogic services and verify whether the business can be in normal use.
Note: If the patch causes a business exception, roll back by the following command:
C:\oracle \Middleware\Oracle_Home\OPatch\opatch rollback-id <Patch ID>
Other versions
Other versions must be upgraded to version above 12.2.1.3 before patching. Since WebLogic is a paid service, please contact the official technical support for the upgrade method.
Temporary Solution
The temporary repair contains some risks; it is suggested that users can prudently choose the temporary repair scheme according to the characteristics of the business system:
1. This vulnerability can be temporarily defended by closing the IIOP protocol. The operation is as follows:
In the WebLogic Console, select the Service-> AdminServer-> Protocol, and uncheck IIOP Enable. And restart the WebLogic project so that the configuration takes effect.
2. Control of the T3 services
Methods to control the T3 service:
Select the Security-Filter in the WebLogic interface above, find the "Connect Filter" in the interface below, and enter:
security.net.ConnectionFilterImpl
Then enter the following commands in the Connection Filter rule
127.0.0.1 * * allow t3 t3s,0.0.0.0/0 * * deny t3 t3s
Finally, save and restart the server.
Official Solution
Currently, the official patch of the affected version has been released, affected users are advised to update the official security patch in time. The link is as follows:
https://www.oracle.com/security-alerts/cpuoct2024.html
Sangfor Solutions
Risky Assets Detection
Support is provided for the proactive detection of Oracle WebLogic Server; and it is capable of batch identifying the affected asset conditions of this event in business scenarios. Related products are as follows:
[Sangfor CWPP] has released a detection scheme.
[Sangfor Host Security] has released a detection scheme.
Vulnerability Proactive Detection
Support is provided for proactive detection of CVE-2024-21274, CVE-2024-21215, CVE-2024-21234, CVE-2024-21260, CVE-2024-21216; and it is capable of quickly batch identifying whether there are vulnerability risks in business scenarios. Related products are as follows:
[Sangfor Host Security] is expected to release a detection scheme on October 20, 2024, with Code: SF-0005-21021 to SF-0005-21025.
[Sangfor Cyber Guardian MDR] is expected to release a detection scheme on October 17, 2024, with Code: SF-0005-21021 to SF-0005-21025.
[Sangfor Omni-Command] is expected to release a detection scheme on October 20, 2024(requiring Host Security component capabilities), with Code: SF-0005-21021 to SF-0005-21025.
Timeline
On October 16, 2024, Sangfor FarSight Labs received notification that Oracle has released security patches.
On October 16, 2024, Sangfor FarSight Labs released a vulnerability alert.





