On June 20, 2024, the Indonesian National Data Center suffered a major ransomware attack that disrupted airport immigration checks and various government services. The attackers demanded a ransom of 8 million USD (approximately 131 billion Indonesian Rupiah).
The attack affected over 200 government institutions, including digital services for immigration, visas, passports, and residence permits. This led to long lines and delays at airports. In response, the Indonesian government refused to pay the ransom and has been working to mitigate the impact. They have migrated critical data to Amazon Web Services to restore functionality and continue to investigate the attack.
The ransomware used in the attack, identified as Brain Cipher, closely resembles ransomware generated by the leaked LockBit 3.0 builder, suggesting it was created using this builder. Analysis of the attacker’s infrastructure indicates that the group is still in its early stages and lacks a fully developed setup.
Sangfor Endpoint Secure has been verified to offer protection against Brain Cipher ransomware. See the Sangfor Solutions section for more details.
What We Know About Brain Cipher
Brain Cipher is a new ransomware group that recently made headlines by breaching Indonesia’s National Data Center. They demanded a ransom of 8 million USD. The ransomware they used closely resembles those produced by the leaked LockBit 3.0 builder, suggesting that they likely used this builder to create their malware.
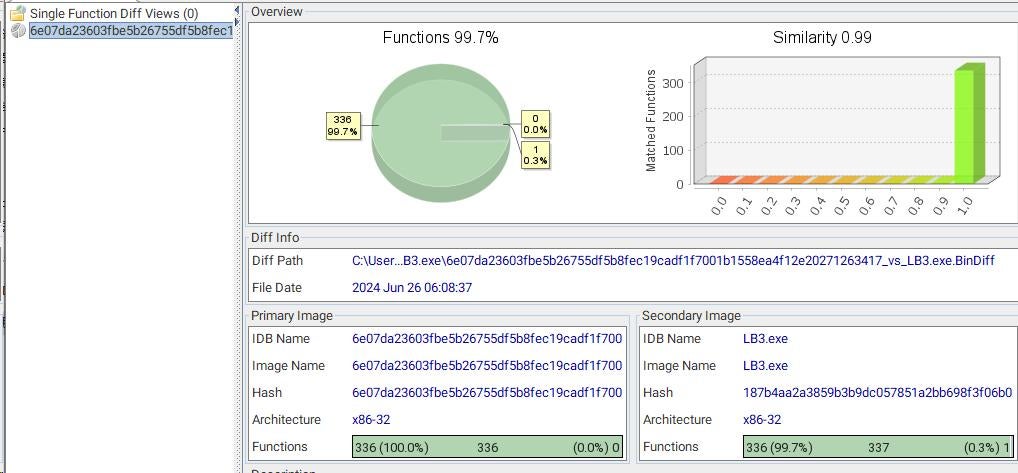
Figure 1: High Similarity between Brain Cipher Encryptor and LockBit 3.0
Unlike other ransomware groups, Brain Cipher did not include the ransom amount or wallet address in the ransom note. Instead, they directed victims to a Tor-based communication page for these details. Brain Cipher also operates a data leak site, but it appears to be incomplete, only listing the ransom demands for current victims.
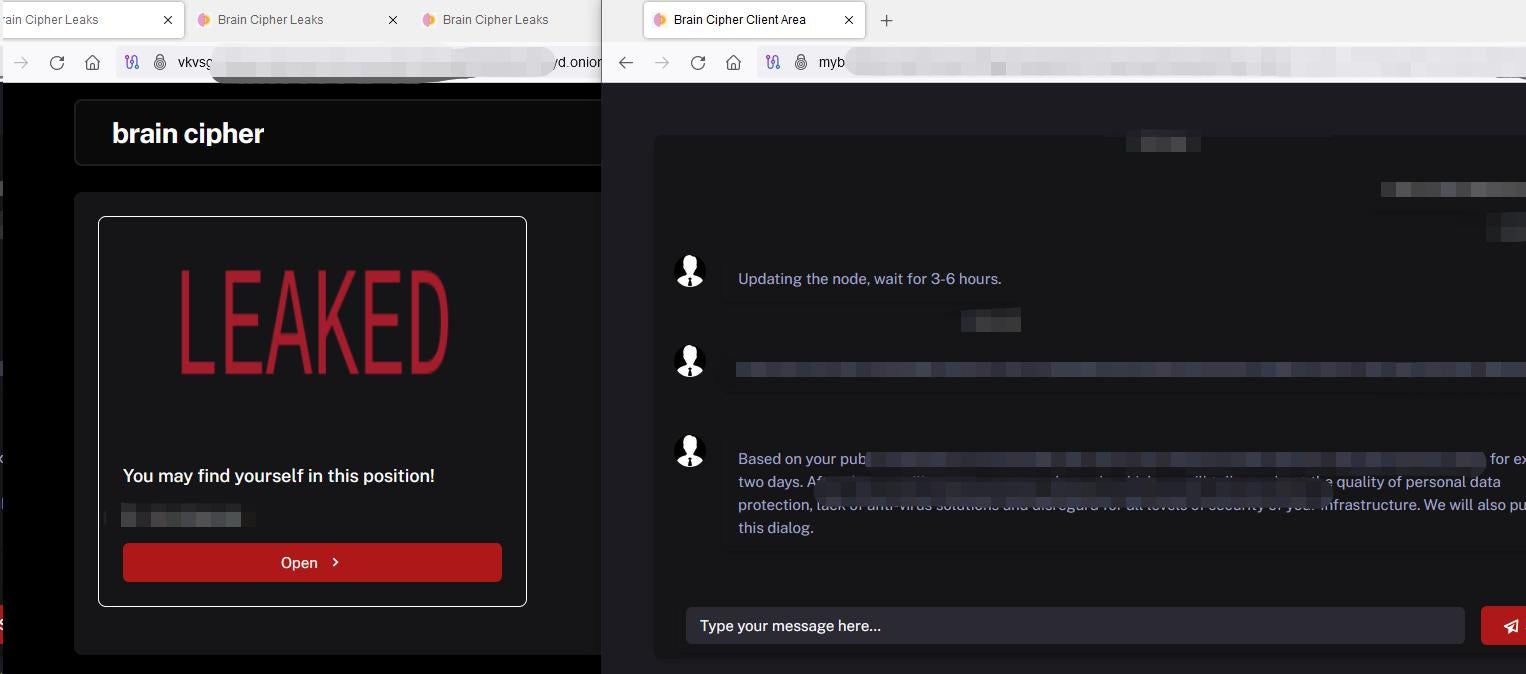
Figure 2: Brain Cipher’s Incomplete Leak Site and Communication Page
Sample Analysis
The analysis of the captured sample reveals that this variant has minimal code changes compared to those created by the leaked LockBit 3.0 builder. The main differences are slight modifications in the Portable Executable (PE) header structure, mainly in the data section based on custom parameters.
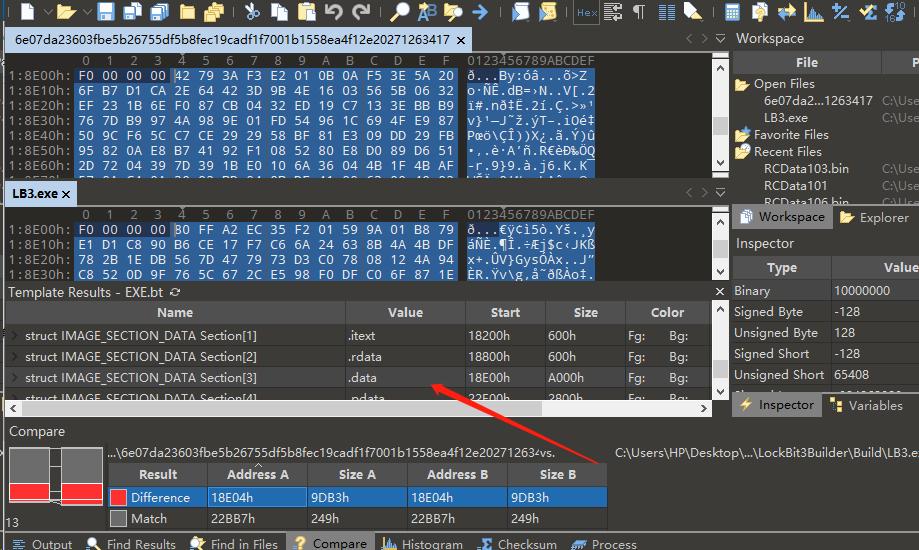
Figure 3: Comparison of Brain Cipher and a Sample Created by the LockBit 3.0 Builder
Similar to samples created by the LockBit 3.0 builder, Brain Cipher supports the following optional configurations:
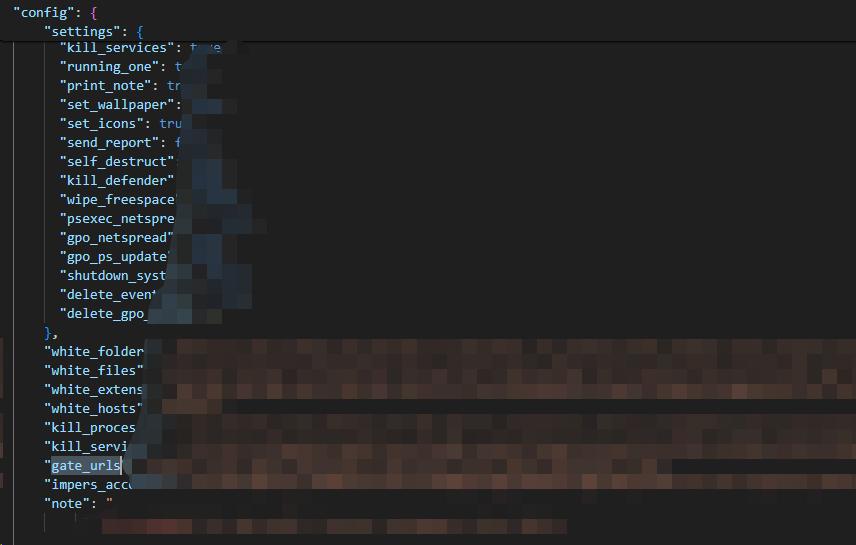
Figure 4: Brain Cipher Optional Configurations
Two types of ransom notes have been identified for this ransomware family.
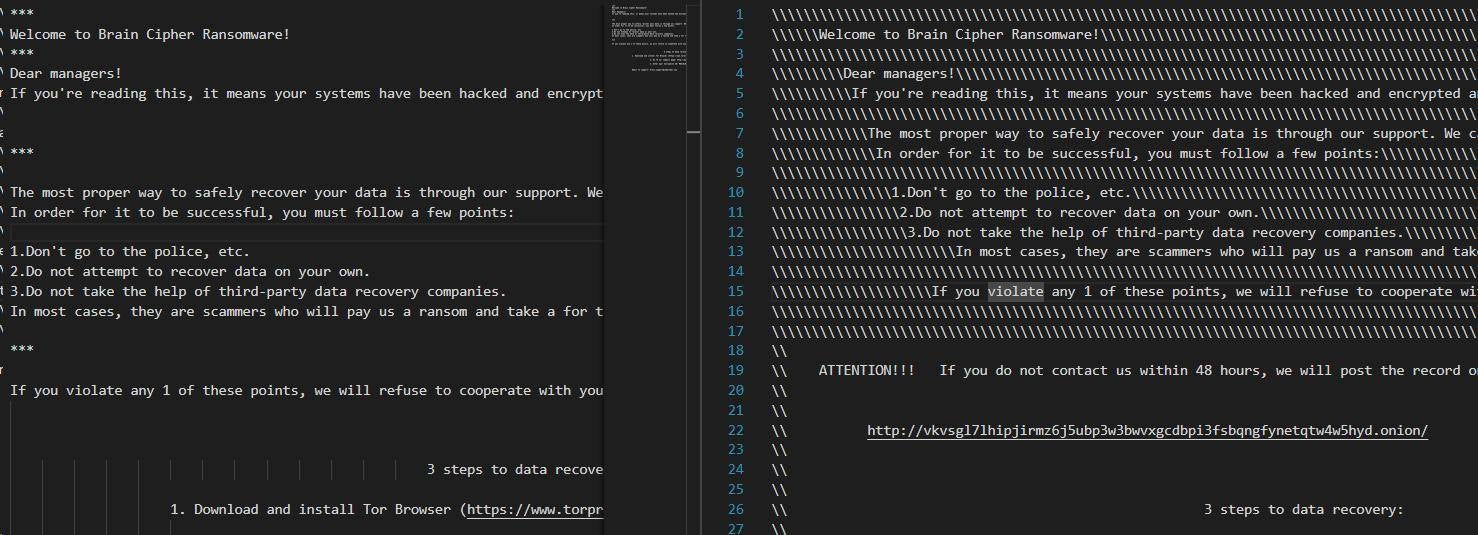
Figure 5: Brain Cipher Ransom notes
Conclusion
The similarities between Brain Cipher ransomware and LockBit 3.0 suggest that the new variant is derived from the leaked LockBit 3.0 builder, with specific customizations in the data segment. This analysis helps in understanding the ransomware’s development and assists in creating targeted defense mechanisms.
Indicators of Compromise
| Hashes | 9c5698924d4d1881efaf88651a304cb3 |
| URL | http://vkvsgl7lhipjirmz6j5ubp3w3bwvxgcdbpi3fsbqngfynetqtw4w5hyd[.]onion/ |
| Email address | brain.support@cyberfear.com |
Sangfor Solutions
Sangfor Endpoint Secure
Sangfor Endpoint Secure supports the detection and blocking of Brain Cipher ransomware with its AI-driven static and dynamic ransomware detection engines. The static engine blocks ransomware files upon landing on endpoints, while the dynamic engine defends against ransomware payload execution. This combination enables Endpoint Secure to “Kill Ransomware in 3 Seconds,” achieving 100% detection accuracy for known ransomware and 99.83% for unknown ransomware. Additionally, Endpoint Secure offers dynamic backup and recovery capabilities. Upon detecting suspected ransomware behavior, it backs up files in real time to ensure their recovery if encryption occurs.
Protection is provided without updates, but updating to the latest version is recommended for enhanced security.
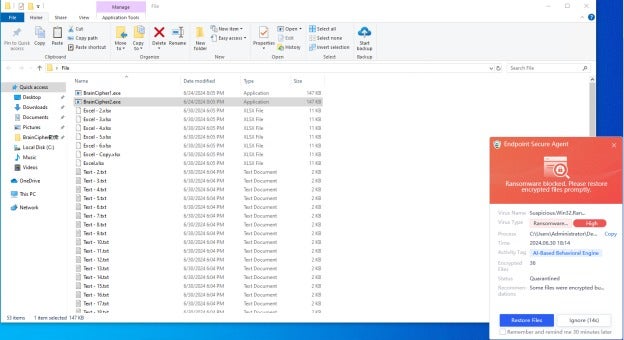
Figure 6: Sangfor Endpoint Secure blocks ransomware encryption by Brain Cipher and provides the option to restore encrypted files
Watch Endpoint Secure Kill Ransomware in 3 Seconds
Sangfor Cyber Guardian Incident Response (IR) and Managed Detection Response (MDR)
Sangfor Cyber Guardian offers incident response (IR) services for victims of ransomware and other cyberattacks. Cyber Guardian IR provides both on-site and remote response assistance, including threat containment to stop the spread of the attack and in-depth threat hunting to eliminate threats from the environment. Cyber Guardian IR also conducts a thorough incident investigation to identify the root cause and offers hardening recommendations to prevent future incidents.
Alternatively, Sangfor Cyber Guardian Managed Detection and Response (MDR) provides 24/7 monitoring, response, and protection by a team of security experts to keep you safe at all times. The Cyber Guardian team uses their experience in offensive and defensive security to accurately verify and report only true positives – reducing your workload and preventing important security alerts from being overlooked. The team implements fixes using a range of Sangfor technology, allowing you to focus on building your business instead of micromanaging threats.
Ransomware Prevention Best Practices
- Perform regular vulnerability scans and security assessments and promptly update systems and applications to fix known vulnerabilities.
- Do not open suspicious or unexpected emails, especially the links and attachments in them If you must open unknown files, scan them first with antivirus software.
- Install reputable antivirus software, perform regular full system scans, and remove detected threats. Ensure timely updates and patches.
- Download products via official and verified channels. Activate and update products using tools/features provided by legitimate developers. Avoid illegal activation tools and third-party downloaders, as they often distribute malicious content.





