Network firewalls are security tools primarily focused on monitoring, inspecting, and restricting traffic going into and coming out of a network. However, they differ from web application firewalls, which protect applications and primarily deal with HTTP/S security threats. In today’s highly digitalized world, businesses and organizations need to use network firewalls as part of their network firewall security system.
In this article, we will give a brief overview of network firewalls, including their history, capabilities, and why they are essential as security solutions for organizations and enterprises to counter newer and more advanced cyber threats.

What Are Network Firewalls?
Network firewalls are vital components in network security systems, acting as a barrier between your internal network and external threats. They monitor and control incoming and outgoing network traffic, defend against unauthorized access and cyber attacks, and protect your system from vulnerabilities using packet filtering, proxy service, stateful inspection, and other security methods.
By analyzing data packets, firewalls evaluate their validity based on predetermined security rules. They enforce network policies, protecting against hacking attempts and data breaches. With granular control, firewalls safeguard against threats like DDoS attacks and generate alerts for prompt action. Overall, firewalls play a crucial role in network security, protecting your network and sensitive information from potential threats. and generate alerts for prompt action.
Common Features of Network Firewalls
Network firewalls encompass a wide range of features to build a robust security framework against various cyber threats while ensuring compliance with security policies. These core features include:
- Traffic Filtering: Network firewalls screen and control traffic flow based on various criteria, such as source and destination IP addresses, protocols, and port numbers, to prevent unauthorized access and block malicious traffic from entering the network.
- Access Control: This feature enforces access policies by allowing or blocking specific types of traffic. They typically start with a "deny all" approach, permitting only explicitly allowed traffic.
- Web Filtering: Firewalls can screen web content based on preset categories or specific domain names to bar access to harmful or inappropriate websites, reducing the risk of users visiting potentially hazardous sites.
- Logging and Monitoring: Users can utilize the logging capabilities to track network events like blocked connections or policy breaches for trend analysis, vulnerability identification, and potential attack detection.
- Intrusion Prevention and Detection: Modern firewalls integrate intrusion prevention systems (IPS) and intrusion detection systems (IDS) to scrutinize traffic for suspicious activities and known threat signatures, bolstering security defenses against advanced threats.
- Virtual Private Network (VPN) Support: This helps encrypt data exchanged between remote users and internal users, facilitating secure remote access through VPNs and safeguarding sensitive information accessed by off-site employees.
- Malware Protection: Many firewalls are equipped with features to scan incoming data for malware, ensuring that links, attachments, and files are safe before users download or open them.
- Bandwidth Control: This functionality enables administrators to regulate bandwidth usage among various applications or users, optimizing network performance by prioritizing critical applications over less essential traffic.
- High Availability: To maintain uninterrupted operation, many network firewalls support high availability configurations, where multiple firewalls work in sync. In case of failure, one firewall seamlessly takes over to prevent service disruptions.
- Application Awareness: Advanced firewalls can recognize applications operating on the network and enforce specific security policies tailored to each application, granting greater control over application behavior within the network.
- Deep Packet Inspection (DPI): Next-generation firewalls (NGFWs) employ deep packet inspection to analyze data packet contents beyond header information. This enables the detection and prevention of sophisticated application-layer attacks that traditional firewalls might overlook.
These features enhance both firewalls and network security, ensuring real-time protection, flexibility, and scalability.
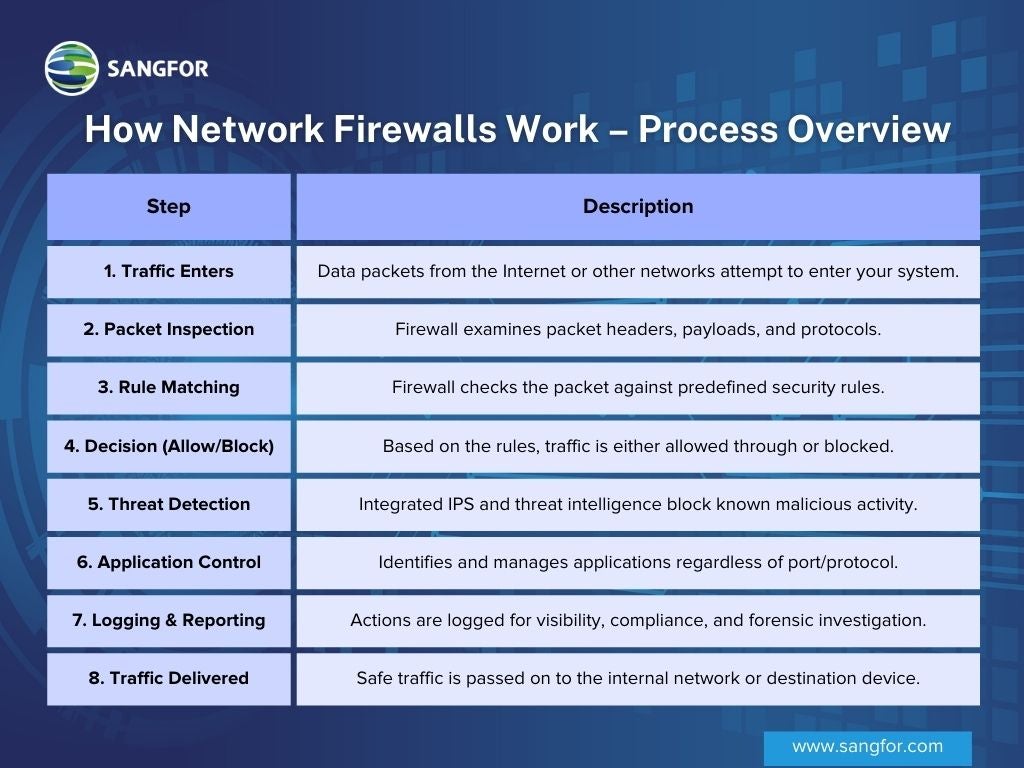
How Network Firewalls Work – Process Overview
What Is the History of Firewalls?
Network firewalls were developed by a major American company called Digital Equipment Corporation (DEC) in 1988. The first type of firewall is often known as the Packet Filter. It inspects and restricts suspicious packets of information transferred between different computers on a network.
Fast forward three decades, and cyber threats have become much more advanced than they were when network firewalls were first made, as they are now highly evasive, multi-vectored, and increasingly difficult to defend against. Traditional network security firewalls struggle to deal with these, and businesses globally lose billions of dollars each year due to cyberattacks. Newer types of network firewalls then emerged, providing improvements from their predecessor and feature cloud capability to leverage scalable resources and threat intelligence updates, enabling adaptive and dynamic protection against evolving cyber threats.
Types of Firewalls
Network firewalls try to keep your network safe, but different types of firewalls have different capabilities. The main types include:
- Packet-Filtering Firewalls: These firewalls look at incoming and outgoing traffic and allow access to the network based on specific criteria, like port numbers, allowed IP addresses, packet types, and more. Also known as stateless firewalls, they do not fully inspect the packets and use the source and destination details of the data packets to figure out if it is a threat. Their primary function revolves around an established set of rules, and they operate at a relatively faster rate because of their basic filtering methods. This makes these firewalls more vulnerable to IP spoofing or attacks on TCP.
- Circuit-Level Firewalls: This firewall will monitor the system once a UDP or TCP connection is made. Understanding the communication session's attributes can validate the legitimacy of the interaction, offering an additional layer of protection. Their primary focus is not on the data itself but on the nature of the TCP handshake between packets, ensuring valid and consistent communication. This allows it to secure the exchange of data packets directly between hosts without the need for more filtering.
- Stateful Firewalls: Also known as third-generation technology, these stateful inspection firewalls look at data packets and track any connections made as part of an established network session. This dynamic tracking system helps in assessing the context of traffic, providing a balance between performance and security. With the ability to remember previous communications, they can make more informed decisions on subsequent packets, reducing the chance of malicious content slipping through. Any deviations from the expected pattern are blocked. This type of firewall is easier to use; it increases access control granularity. It is helpful in the prevention of Distributed Denial of Service (DDoS) attacks.
- Application Firewalls: This type of firewall filters and inspects network traffic based on its intended purpose. It monitors the network on the application layer, defining rules for HTTP connections and finding outliers to established patterns. Application firewalls are useful for identifying and preventing DoS attacks, buffer overflow attacks, and malware. Given the rise of application-specific attacks, this firewall type becomes crucial in deciphering intricate data flows and ensuring only legitimate traffic gets through.
- Proxy Server Firewalls: These firewalls check all incoming and outgoing messages in a network and then hide the real network addresses from any external inspection. Acting as intermediaries, they decide if a connection request is valid based on predefined policies before forwarding it, adding a layer of security. Moreover, by caching frequent requests, they can enhance the overall network performance, providing a blend of security and efficiency.
- Next-Generation Firewalls: These firewalls offer a combination of packet inspection, stateful inspection, deep packet inspection, and many more security features. Armed with the capability of understanding the applications generating traffic, they're more adept at identifying and blocking malicious activity. Integrated with threat intelligence features, they can adapt and evolve based on emerging threats, ensuring a robust defense mechanism. They filter traffic inside the network by inspecting applications, traffic types, and assigned ports. Next-generation firewalls are a more holistic and self-sufficient approach to securing your network.
While each of these firewalls has its benefits, try to understand what your network looks like before choosing the right one.
What Are the Benefits of Network Firewalls?
Regardless of the specific types, network firewalls, in general, offer many benefits that enhance network firewall security and enable greater control of the overall infrastructure, such as:
- Granular Control: Network firewalls offer precise control over network traffic by enabling administrators to set specific rules for different types of traffic based on criteria like IP addresses, port numbers, and protocols. This capability allows organizations to authorize or block access to particular applications or services, ensuring that only authorized traffic moves through the network. For example, firewalls can be configured to grant access to sensitive data to specific users while restricting it for others, thereby enhancing security through customized access policies.
- Centralized Control Management: Their centralized control management capability simplifies the administration of security policies across multiple devices and locations. This approach empowers IT teams to apply consistent security measures and oversee network activity from a unified interface. It reduces the complexity associated with managing diverse security systems and ensures that all network segments comply with uniform security standards.
- Threat Prevention: Organizations can prevent threats by scrutinizing incoming and outgoing traffic for malicious activities through network firewalls. They employ techniques such as deep packet inspection and intrusion prevention systems (IPS) to detect and block potential threats before they infiltrate the network. Advanced functionalities of NGFWs, like application awareness and machine learning, can enhance their ability to identify sophisticated attacks.
- Data and Privacy Protection: With strict access controls and a "deny by default" policy that only permits authorized users to access, firewalls significantly reduce the risk of data breaches. Additionally, techniques like deep packet inspection can analyze data packets for potential threats while maintaining user privacy.
- Network Performance Optimization: By segmenting networks into different zones (e.g., internal, external, DMZ), network firewalls reduce exposure to potential threats and ensure that critical resources are isolated from less secure areas. Furthermore, compliance with regulatory mandates such as GDPR or HIPAA often necessitates the use of firewalls to safeguard personal data, making them indispensable for organizations handling sensitive information.
- Risk Mitigation: Actions such as establishing predefined traffic management rules and monitoring for abnormal behavior help organizations shrink their attack surface and minimize the potential impact of security breaches. However, a robust firewall strategy is also needed for a comprehensive risk management framework, allowing organizations to effectively counter emerging threats while ensuring business continuity.
- Enhanced Compliance Adherence: Network firewalls bolster compliance adherence by aiding organizations in fulfilling regulatory mandates like GDPR, HIPAA, and PCI DSS. These firewalls enforce security protocols that safeguard sensitive data and offer robust logging and reporting functionalities essential for audits and showcasing compliance.
These benefits reinforce how critical firewalls and network security are in today’s threat landscape.
Why Do Organizations and Enterprises Need Network Firewalls?
In an era of increasing digital dependency, cybersecurity measures and solutions have become essential for organizations and enterprises. Businesses, in particular, need protection over sensitive data to ensure business continuity and maintain customer trust. Firewalls serve as the first line of defense, preventing unauthorized access and shielding networks from attacks like Distributed Denial of Service (DDoS) and ransomware.
Regulatory compliance is another major area of concern. With firewalls, organizations can easily meet standards, such as GDPR or HIPAA, to help avoid legal penalties and reputational damage. They also enable businesses to segment networks, ensuring critical data is isolated from less secure areas and smooth operations can continue even during cyber incidents.
Use Cases of Network Firewalls
Network firewalls are employed across diverse scenarios to meet the unique needs of organizations. Some of the most common use cases include:
- Securing Remote Workforces: With remote work becoming the norm, firewalls enable secure connections through Virtual Private Networks (VPNs), ensuring employees can access internal resources without exposing the network to vulnerabilities.
- Protecting E-commerce Platforms: Network firewalls safeguard online stores by blocking unauthorized access, preventing data breaches, and mitigating risks from cyber threats like phishing and malware.
- Regulating Guest Access: Enterprises offering guest Wi-Fi can use firewalls to segregate visitor networks from internal systems, protecting sensitive resources while allowing seamless guest connectivity.
- Defending Industrial Systems: In manufacturing or energy sectors, firewalls protect Operational Technology (OT) systems from external threats, ensuring uninterrupted industrial processes.
- Optimizing Cloud Environments: Firewalls for cloud infrastructures manage traffic between on-premises systems and cloud-based resources, ensuring secure and efficient communication.
What Are the Best Practices for Network Firewalls?
To maximize the effectiveness of network firewalls, organizations should follow these best practices:
- Regular Updates and Patching: Ensure firewalls are updated with the latest firmware to protect against newly identified vulnerabilities and threats.
- Network Segmentation: Divide the network into distinct zones (e.g., internal, external, and DMZ) to isolate sensitive data and reduce potential exposure to attacks.
- Implementing Access Control Lists (ACLs): Define granular rules to regulate network traffic, allowing only authorized users and services access to critical resources.
- Enforcing Strong Authentication: Use multi-factor authentication (MFA) to prevent unauthorized access and enhance the overall security posture.
- Periodic Security Audits: Conduct regular reviews of firewall configurations to ensure they align with current security policies and address emerging threats.
- Employee Training: Educate staff on the importance of network security and safe practices to minimize human errors that could bypass firewall defenses.
Choose Sangfor Network Secure as your complete firewall solution
Sangfor Network Secure, is more than just a traditional firewall—it’s a next-generation firewall (NGFW) that integrates critical security features such as web application firewall (WAF) capabilities, application control, AI-powered threat intelligence, and advanced intrusion prevention into a single, easy-to-manage solution.
For organizations seeking a broader security strategy, Sangfor Network Secure works seamlessly with Sangfor Cyber Command, an advanced Network Detection and Response (NDR) platform designed to detect and respond to threats that bypass conventional defenses. Cyber Command uses AI-driven analytics and network-wide visibility to identify anomalous behavior and lateral threat movements in real-time, strengthening your cybersecurity posture beyond perimeter protection.
This integrated approach is especially beneficial for small to medium-sized businesses, offering a scalable solution that combines NGFW, NDR, and endpoint protection to defend against both known and unknown threats. With features like centralized management and role-based access control, Sangfor makes cybersecurity easier to deploy and manage across your entire infrastructure.
By implementing Sangfor Network Secure alongside Sangfor Cyber Command, businesses can achieve enhanced threat detection, faster incident response, and a more efficient IT environment overall.
Visit the Sangfor Network Secure product page to learn how it can protect your business from 99% of cybersecurity threats.
Frequently Asked Questions
In this day and age, it is hard to imagine any business or organization that can get away with not using a network firewall for protection and not run into trouble. Cyber threats are everywhere, and they are evolving faster than you think. For large enterprises, failure to protect confidential business information could lead to huge consequences. Small and medium businesses have also become easy targets for hackers and cyberattacks, and often must pay expensive ransoms to get their systems back to normal.
Regardless of what industry you work in, network firewalls have become an essential cyber security tool. Businesses should consider whether to stick with a cheaper or free-to-use firewall that only provides basic protection or upgrade to an enterprise-grade firewall for all-round coverage.
Network firewalls should be placed at your network’s front line and between any network that has a connection to the Internet in order to achieve full-spectrum security. Since most network setups involve a trio of switches, firewalls, and routers, the router would typically be the first part of a LAN system, followed by the network firewall and, ultimately, the switch.
VPNs are widely advertised today as an essential layer of cybersecurity tools when surfing the internet. However, it is extremely important to understand that they are neither designed to replace network firewalls nor capable of replacing them. The two cybersecurity tools perform very different functions and are designed to achieve very different goals.
Simply put, VPNs can encrypt your connection, hide your real IP address, and enhance your privacy and security on the internet, but they cannot protect you against the various types of threats that network firewalls are designed to restrict. VPNs offer just one layer of protection when you browse the internet, whereas a firewall is designed to protect you from a wide range of cyber threats. Using a VPN along with your firewall would further enhance your cybersecurity, but replacing your firewall with just a VPN would leave you exposed to all kinds of different threats.





