What is the CIA Triad (Confidentiality, Integrity and Availability)?
The CIA triad is a fundamental model in information security that consists of three core components: Confidentiality, Integrity, and Availability. These principles are crucial in maintaining the security posture of an organization and can be practically applied in various ways, such as through access controls, encryption, and auditing. The components of the CIA Triad work together to guide an organization's security procedures and policies, ensuring the protection of data, networks, and devices.

History of the CIA Triad
The concept of the CIA triad has its roots in various sources, including a 1976 paper for the U.S. Air Force and a paper on the difference between commercial and military computer systems. It is widely accepted and used by information security professionals to evaluate incident response plans and identify vulnerabilities in an organization's systems.
Over time, the CIA triad has evolved to include additional elements such as authenticity, non-repudiation, and accountability. As these elements further enhance the overall security of information systems, it has also been adopted by various regulatory bodies and standards, such as the ISO 27001 and NIST Cybersecurity Framework, as a means to ensure the protection of sensitive data.
What are the components of the CIA triad?
The CIA triad is a fundamental concept in information security and is essential in maintaining the confidentiality, integrity, and availability of sensitive information. It is often used as a guideline for organizations to assess and improve their overall security posture. By implementing strong measures for each component of the triad, organizations can better protect their data and systems from cyber threats.
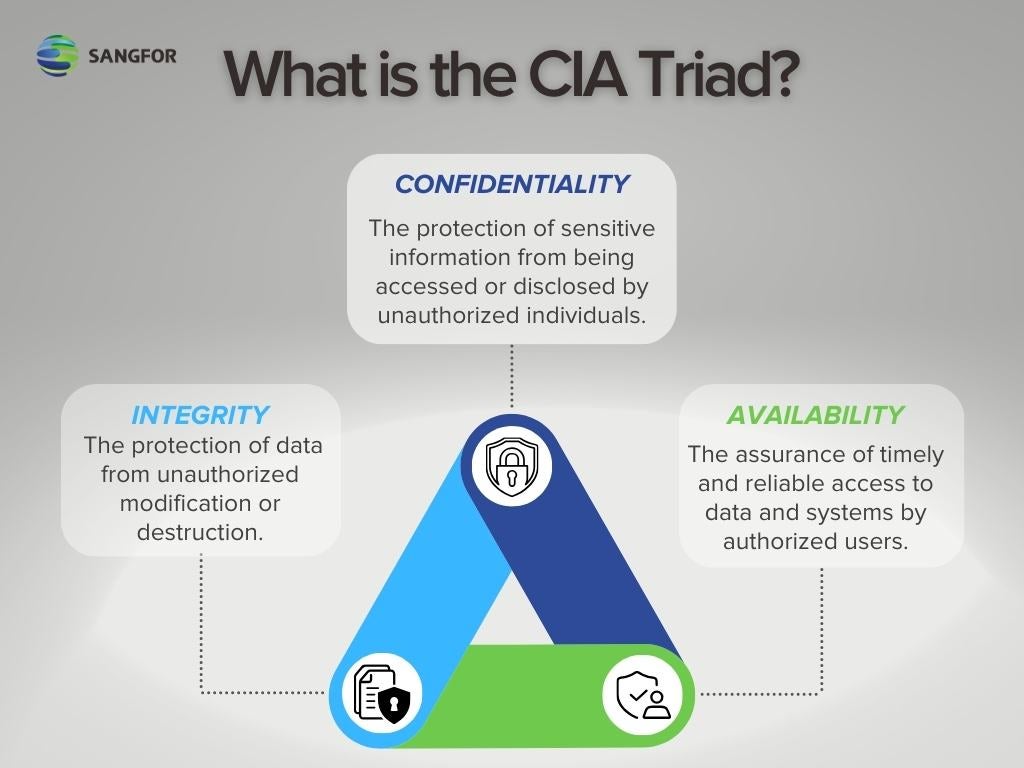
Confidentiality
Confidentiality refers to the protection of sensitive information from being accessed or disclosed by unauthorized individuals. The concept of confidentiality is an essential aspect of information security, as it ensures that only authorized individuals have access to sensitive information. This can include personal data, financial information, or trade secrets. Confidentiality is achieved by implementing security measures such as access controls, encryption, and data masking.
In addition, confidentiality also plays a major role in protecting against data breaches, which can lead to financial and reputational damage for organizations. By implementing strong confidentiality measures, organizations can mitigate the risk of data breaches and protect their sensitive information.
Integrity
This aspect of the CIA triad model refers to the protection of data from unauthorized modification or destruction. It ensures that information remains accurate and trustworthy by preventing any unauthorized changes or tampering. For example, a company's financial records must have integrity to ensure that the numbers have not been altered by anyone without proper authorization. This can be achieved through measures such as access controls, encryption, and data backups.
One way to ensure integrity is through data backups, which can help restore information in case of accidental or malicious changes. Additionally, access controls can limit the ability of unauthorized individuals to modify or delete data. Encryption is another important measure for maintaining data integrity. This involves encoding data to make it unreadable without the proper decryption key. This can prevent hackers from accessing and altering sensitive information.
Availability
Availability refers to the assurance of timely and reliable access to data and systems by authorized users. It is a crucial aspect of the triad as it ensures that information is accessible when needed and that systems are functioning properly. The availability of data and systems is essential for organizations to operate smoothly and efficiently. Without proper availability, employees may not be able to perform their tasks, which can result in loss of productivity and revenue. This is why it is important for organizations to prioritize the availability of their data and systems, along with confidentiality and integrity, in order to maintain a strong overall security posture.
The concept of availability also extends to disaster recovery and business continuity planning. Organizations must have measures in place to ensure that in the event of a disaster or system failure, data and systems can be quickly restored to minimize downtime and maintain business operations. This is especially important for organizations that handle sensitive information, such as healthcare providers and financial institutions.
Examples of CIA Triad Best Practices
There are examples of cybersecurity strategies that you can implement to ensure that your organization is secure and your information remains compliant with the CIA triad.
- Confidentiality: One example is the use of encryption to protect sensitive data. Encryption scrambles the data, making it unreadable to anyone without the proper key. This ensures that even if data is intercepted, it cannot be understood without the key, thus maintaining confidentiality. Examples include 2-factor authentication and security tokens when working with sensitive data.
- Integrity: One example is using digital signatures to provide effective non-repudiation measures, ensuring that evidence of logins, messages, and document viewing cannot be denied. Other examples include using file permissions and user access controls, implementing version control to prevent erroneous changes, and regularly backing up data to prevent loss or corruption.
- Availability: Best practices in terms of availability according to the CIA triad model include implementing redundancy in systems, regularly testing and updating backup and recovery processes, and having a disaster recovery plan in place. For example, a company may have multiple servers for its website to ensure it stays up and running even if one server fails. They may also have a process in place to regularly back up and test their data in case of a system failure. Another best practice for availability is having a response plan for cyber attacks or disasters so that systems and resources can be quickly restored to minimize downtime.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.
CIA Triad: Frequently Asked Questions
Some of the challenges for implementing CIA triad practices include balancing the level of security with usability, ensuring proper training and education for employees, keeping up with constantly evolving threats and technologies, and maintaining the integrity and availability of systems and data while also protecting their confidentiality. There may also be financial constraints and limited resources for implementing and maintaining strong security measures.
Additionally, there may be conflicts between different aspects of the CIA triad, such as the need for strong encryption to protect confidentiality but also the need for timely access to data to maintain availability. Organizations also need to consider the potential impact of insider threats and how to prevent or mitigate them. Finally, compliance with regulations and industry standards may add another layer of complexity to implementing CIA triad practices.
The CIA triad is important because it helps organizations prioritize their security efforts, identify vulnerabilities, and respond to cyber attacks more effectively. It also serves as a framework for incident response, allowing organizations to evaluate what went wrong and how to prevent future attacks. By implementing measures to protect confidentiality, integrity, and availability, organizations can improve their overall security posture and protect their data from unauthorized access or tampering.
The CIA triad is also important for compliance and regulatory purposes. Many industries and government agencies have specific regulations and standards that require organizations to protect the confidentiality, integrity, and availability of their data. By following the principles of the CIA triad, organizations can ensure that they are meeting these requirements and avoiding potential penalties or fines.
Additionally, the CIA triad is a constantly evolving concept as technology and cyber threats continue to advance. As new technologies and threats emerge, organizations must re-evaluate their security strategies and ensure that they are still effectively protecting the confidentiality, integrity, and availability of their data. Overall, the CIA triad is a crucial framework that helps organizations maintain the security and privacy of their data in an increasingly interconnected and digital world.





