Session hijacking, also known as session hijack, is a cybersecurity attack where a malicious actor takes over a user's web session by acquiring the session ID. This allows the attacker to hijack a session and gain unauthorized access to the user's data and actions within that session. Understanding what session hijacking is and how it works is crucial for both users and developers to protect sensitive information and maintain secure online interactions.

How Session Hijacking Works: Understanding the Basics
In web applications, a session is a series of interactions between a user and the server. When a user logs in, the server assigns a session ID to identify and maintain the state of the user's session. This session ID is typically stored in cookies, URLs, or hidden form fields.
Common Methods Used to Hijack a Session
Attackers use various techniques to obtain session IDs and hijack a session:
- Packet Sniffing: Intercepting network traffic to capture session IDs transmitted over unsecured connections.
- Cross-site Scripting (XSS): Injecting malicious scripts into web pages to steal session IDs from users' browsers.
- Malware-Based Attacks: Using malware to infect a user's device and extract session information.
- Session Fixation: Forcing a user to use a known session ID, allowing the attacker to hijack the session after the user logs in.
- Session Side Jacking: Utilizing tools to intercept communication between the user and server, often over unsecured Wi-Fi networks.
- Cross-site Request Forgery (CSRF): Exploiting authenticated users to perform unauthorized actions on a web application.
- Man-in-the-Middle Attacks: Intercepting communication between two parties to steal session information.
Types of Session Hijacking Attacks
Understanding the different types of session hijacking can help in recognizing the specific threats posed by attackers. These types are typically categorized as active or passive:
- Active Attacks: The attacker takes over the session and interacts with the web application as the user.
- Passive Attacks: The attacker monitors the session to gather information without interfering.
Session Hijacking vs. Session Spoofing vs. Session Fixation
Understanding the distinctions between session hijacking, session spoofing, and session fixation is essential for effectively securing web applications. Each attack method differs in how the attacker gains access to a session, and recognizing these differences can help in applying the right protective measures.
- Session Hijacking: Stealing an existing session ID to impersonate a user.
- Session Spoofing: Creating a fake session to deceive the server.
- Session Fixation: Forcing a user to log in with a predetermined session ID.
Understanding these differences helps in implementing appropriate security measures.
What Do Attackers Gain from Session Hijacking?
Session hijacking isn't just about gaining access to a user's session—attackers seek to exploit this access for various malicious purposes. Here are some of the key gains for attackers:
- Access to Sensitive Information: Personal data, financial information, and confidential communications.
- Unauthorized Transactions: Performing actions such as transferring money or making purchases.
- Identity Theft: Using the victim's credentials to impersonate them.
- Spreading Malware: Propagating malicious software to other users.
- Compromising Business Systems: Gaining access to corporate networks and resources.
Impact of Session Hijacking
Risks and Consequences
1. Unauthorized Access to Sensitive Data
Attackers gain access to personal, financial, and confidential information by taking over user sessions. This can include:
- Personal Data: Usernames, passwords, contact details, and browsing history.
- Financial Information: Credit card details, bank account credentials, and payment histories.
- Corporate Data: Trade secrets, intellectual property, and sensitive business communications.
Once accessed, this information can be exploited for fraud, identity theft, or sold on the dark web.
2. Financial Loss
For individuals, session hijacking may lead to:
- Unauthorized Transactions: Attackers can make purchases, withdraw funds, or transfer money.
- Stolen Cryptocurrency: Cryptocurrency wallets accessed through hijacked sessions can result in significant financial losses.
For organizations, the financial impact can be catastrophic:
- Operational Disruption: Interruptions in service caused by session hijacking attacks can lead to revenue loss.
- Regulatory Penalties: Failing to protect sensitive data may result in hefty fines under regulations such as GDPR, HIPAA, or PCI DSS.
- Incident Response Costs: Investigating and mitigating the breach often requires expensive technical resources.
3. Damage to Reputation
Organizations targeted by session hijacking may suffer a loss of customer trust due to:
- Data Breaches: Publicized incidents can tarnish a company’s image.
- Loss of Clients: Customers may abandon services they perceive as insecure.
- Brand Devaluation: Negative press surrounding a session hijacking incident can harm long-term market credibility.
Even individuals can experience reputational damage if attackers misuse their accounts for inappropriate actions, such as posting offensive content or conducting fraudulent activities.
4. Legal Liabilities
Victims of session hijacking may face legal repercussions if:
- Fraudulent Actions: Attackers commit crimes using hijacked accounts, leading to investigations implicating the victim.
- Non-Compliance Penalties: Organizations failing to implement robust cybersecurity measures could face lawsuits from affected clients or customers.
Legal consequences can extend to class-action lawsuits from customers or shareholders, further compounding the financial and reputational impact.
How to Detect Session Hijacking
Detecting session hijacking can be challenging, but with the right tools and vigilance, suspicious activity can be identified before significant damage occurs. Below are signs that indicate a compromised session, as well as some tools and techniques that can aid in detecting hijacking attempts:
Signs of a Compromised Session
Detecting suspicious activity early can prevent further damage. Watch for the following indicators of a compromised session:
- Unexpected account activity
- Automatic logouts or session terminations
- Notifications of login from unfamiliar locations or devices
Monitoring Tools and Techniques
To detect session hijacking, organizations need to implement monitoring systems that can identify unusual activity. Here are some tools and techniques used to monitor and analyze potential threats:
- Implementing Intrusion Detection Systems (IDS)
- Analyzing server logs for anomalies
- Utilizing Security Information and Event Management (SIEM) tools
- Employing machine learning algorithms to detect unusual patterns
Advanced Detection Techniques
Organizations are employing Artificial Intelligence (AI) and Machine Learning (ML) to analyze vast amounts of data and detect anomalies indicative of session hijacking. These technologies can identify patterns and respond in real-time to potential threats.
How to Prevent Session Hijacking
The key to protecting yourself from session hijacking lies in both user practices and developer strategies. Below are measures that can be taken on both sides to prevent session hijacking:
For Users
As an end user, there are several important steps you can take to protect your sessions from hijacking attempts:
- Secure Communication Protocols (HTTPS): Ensure websites use HTTPS to encrypt data transmission.
- Use of VPNs: Protect network traffic on unsecured networks.
- Avoid Suspicious Links and Downloads: Be cautious with unknown emails and websites.
- Browser Settings and Security Plugins: Use plugins like HTTPS Everywhere and keep browsers updated.
- Be Wary on Public Wi-Fi: Avoid accessing sensitive information on unsecured public networks.
For Developers
Developers play a crucial role in securing web applications and preventing session hijacking attacks. Below are key security measures that developers should implement:
- Secure Coding Practices: Validate and sanitize user inputs to prevent XSS and CSRF attacks.
- Session ID Management and Security:
- Use long, random session IDs
- Regenerate session IDs after login
- Set secure and HttpOnly flags on cookies
- Implementing HTTP Security Headers: Utilize headers like Content Security Policy (CSP) and Strict-Transport-Security (HSTS).
- Use of Multi-Factor Authentication (MFA): Add an extra layer of security beyond passwords.
- Enforcing SSL/TLS Encryption: Ensure all data between the client and server is encrypted using SSL/TLS protocols.
- Regular Security Audits: Conduct code reviews and penetration testing to identify vulnerabilities.
Response and Recovery After an Attack
In the event of a session hijacking attack, quick response and recovery are crucial. The quicker the response, the lower the potential damage. Here are immediate actions and long-term strategies to consider after an attack:
Immediate Actions
After discovering a session hijacking attack, it's important to take immediate steps to limit further damage. These actions include:
- Terminate Active Sessions: Log out of all devices to invalidate session IDs.
- Change Passwords: Update credentials to prevent further unauthorized access.
- Notify Relevant Parties: Inform your organization or service provider about the breach.
Long-Term Strategies
In addition to responding quickly, it’s essential to have strategies in place to prevent future attacks. Here are key steps to take after an attack:
- Conduct a Security Audit: Identify vulnerabilities that allowed the attack.
- Update Security Measures: Implement stronger authentication and encryption.
- User Education: Increase awareness about security best practices.
Visualizing Session Hijacking
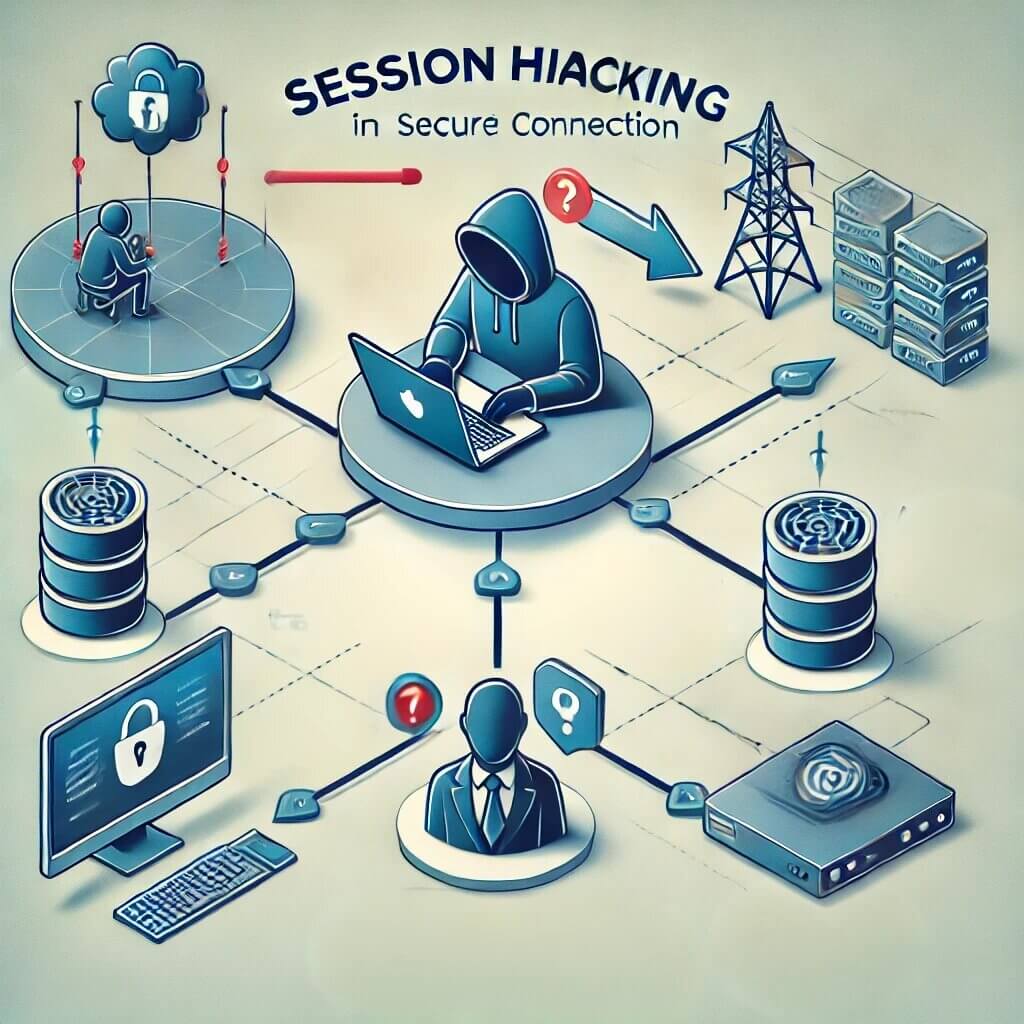
The image above provides a conceptual illustration of session hijacking in a secure connection. It visually breaks down how attackers can intercept and exploit active web sessions, even within seemingly secure environments. Here's a detailed explanation of the components in the diagram:
1. Hacker Intercepting a Session:
- The central figure in the image depicts a malicious actor using a laptop to infiltrate a web session.
- This highlights the role of hackers who leverage various techniques like packet sniffing or man-in-the-middle attacks to steal session IDs.
2. Targeted User on a Secured Connection:
- The image shows a user connected to what they assume to be a secure system, often indicated by HTTPS or a secure Wi-Fi connection.
- Despite this, vulnerabilities such as weak encryption or poor session management can allow an attacker to compromise the session.
3. Data Flow and Network Components:
- The interconnected lines represent the flow of information between the user, servers, and other devices on the network.
- It emphasizes how session IDs travel through various nodes, including routers, servers, and endpoints, any of which could be intercepted.
4. Critical Security Points:
- Elements like the locked padlock icon signify encrypted communication, which is crucial for secure sessions.
- However, the diagram warns of areas where security can fail, leading to session hijacking.
5. Outcomes of a Successful Attack:
- The question marks and warning symbols in the image indicate the uncertainties and risks once a session has been hijacked.
- Attackers may gain access to sensitive data, execute unauthorized actions, or impersonate the user entirely.
How This Relates to Session Hijacking Prevention
This illustration reinforces the importance of using secure protocols, such as SSL/TLS encryption, and adopting robust session management practices. It also underscores the need for vigilance, especially when connected to public networks, as attackers often exploit weak links in communication.
By understanding the pathways and vulnerabilities depicted in this diagram, both users and developers can take proactive steps to detect, prevent, and respond to session hijacking threats effectively.
Conclusion
Session hijacking poses significant risks in today's interconnected world. By understanding what session hijacking is, how attackers hijack a session, and implementing effective session hijacking prevention strategies, both users and developers can enhance security and protect sensitive information.
Frequently Asked Questions
Session hijacking is a cyber attack where an attacker takes over a user's web session by stealing or manipulating the session ID.
Attackers hijack a session by obtaining the session ID through methods like packet sniffing, XSS attacks, malware, or man-in-the-middle attacks.
Detection involves monitoring for unusual activity, while prevention includes using HTTPS, secure coding practices, session management techniques, and client-side precautions.
They gain unauthorized access to sensitive information, the ability to perform fraudulent transactions, and the potential to spread malware.
Immediately terminate sessions, change passwords, notify relevant parties, and assess security measures to prevent future attacks.
Yes, SSL/TLS encryption secures data transmission, making it difficult for attackers to intercept session IDs.
Mobile devices can be vulnerable due to unsecured apps and networks; proper security measures are needed to protect mobile sessions.
Risks include unauthorized access to personal data, financial loss, and damage to reputation.
In cybersecurity, session hijacking is the exploitation of a valid computer session to gain unauthorized access to information or services.





