Smishing Definition
Smishing, also known as SMS phishing, is a form of social engineering attack that targets individuals through fraudulent text messages sent to their mobile devices. It combines the terms "SMS" (short message service) and "phishing" to describe this specific method of cybercrime. Smishing attacks aim to deceive recipients into taking certain actions, such as clicking on malicious links, downloading malware-infected files, disclosing sensitive information, or making financial transactions.

Why Smishing is Becoming Increasingly Prevalent
Smishing Has become increasingly popular in the last several years due to a variety of reasons. Whether it is the changes in technology or human behavior, criminals are opting to use smishing to illegally acquire sensitive data due to its efficiency compared to other methods.
- Increased Vulnerability: Smishing attacks have gained popularity because cyber criminals have recognized that people are more likely to click on text messages compared to other forms of communication like emails or phone calls. As a result, they exploit this vulnerability to target individuals through SMS messages.
- Advancements in Spam Filters: The effectiveness of spam filters in detecting and blocking phishing emails has improved over time. This has led cybercriminals to explore alternative avenues for their attacks, such as smishing. SMS messages can bypass traditional email filters, making it easier for scammers to reach their targets.
- Higher Click Rates: Research has shown that people are more prone to clicking links in text messages compared to email links. This is due to factors such as the immediacy and perceived authenticity of SMS messages. Smishing attacks capitalize on this behavior to trick individuals into interacting with malicious links or sharing sensitive information.
- Mobile Device Usage: The rise of bring-your-own-device (BYOD) policies and remote work arrangements has resulted in an increased reliance on mobile devices for work-related activities. This trend has expanded the attack surface for cybercriminals, as they can exploit vulnerabilities in mobile devices to gain unauthorized access to company networks or steal sensitive information.
- Social Engineering Techniques: Smishing attacks leverage social engineering techniques to manipulate victims' emotions and deceive them into taking a desired action. By impersonating trusted entities like financial institutions, government agencies, or well-known brands, scammers create a sense of urgency or legitimacy, increasing the likelihood of victims falling for the scams.
- Evolving Attack Tactics: Smishers continually adapt their tactics to evade security measures and exploit technological advancements. They employ techniques such as spoofing phone numbers, utilizing burner phones, or sending texts via email to mask the origins of their smishing messages. Additionally, scammers leverage shortened URLs and the familiarity of receiving text messages from banks or brands to deceive victims.
How SMS Phishing Attacks Work
In a smishing attack, the attacker typically poses as a legitimate entity, such as a bank, government agency, or well-known company, to gain the victim's trust. They send a text message to the victim's mobile phone, often containing urgent or enticing content to prompt an immediate response. The message may claim that there is a problem with the victim's account, offer a prize or discount, or request personal information.
The text message will often include a link or phone number for the victim to interact with. Clicking on the link or calling the provided number can lead to various malicious activities. Here's how smishing attacks work at different stages:
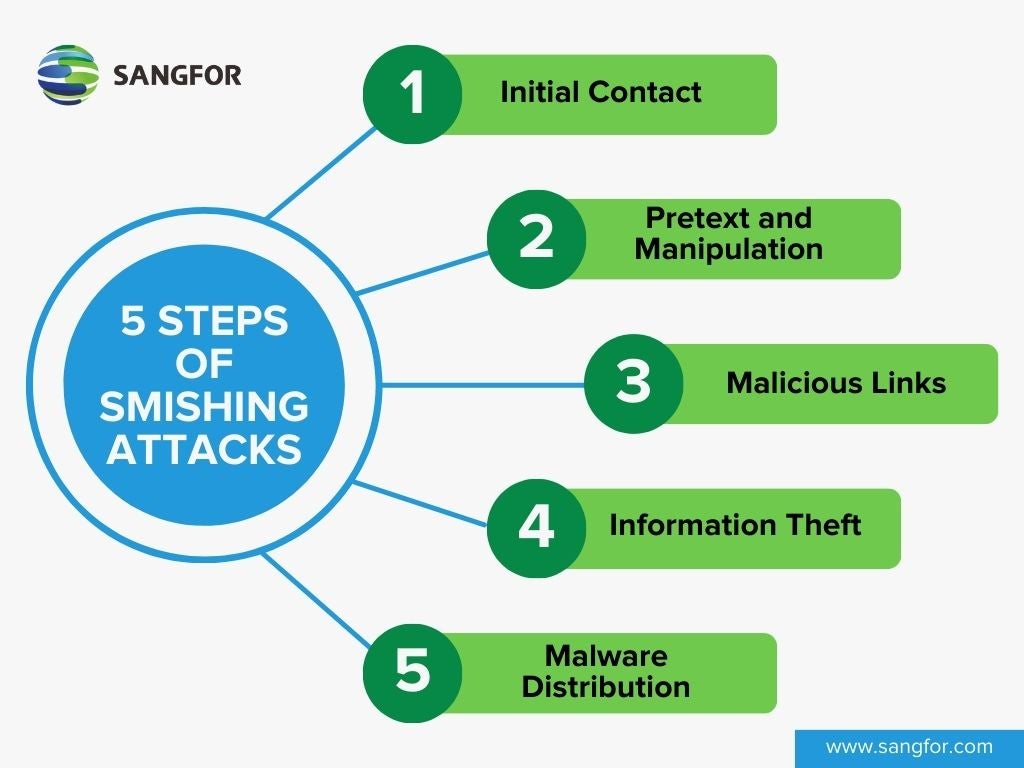
Step 1 - Initial Contact
The attacker initiates the attack by sending a text message to the target's mobile device. The message may appear to come from a legitimate source, such as a financial institution, government agency, or well-known brand.
Step 2 - Pretext and Manipulation
The smishing message often uses pretexting, which involves crafting a fake story or urgent scenario to manipulate the victim's emotions and prompt immediate action. Examples of smishing scams include pretending to be a financial institution, government agency, customer support, a shipper, a boss or colleague, texting the wrong number, offering free apps, or attempting multifactor authentication fraud. These tactics aim to deceive individuals into sharing sensitive information, downloading malware-infected apps, or sending money to the attackers.
Step 3 - Malicious Links
The smishing message may contain a link that appears legitimate but redirects the recipient to a fake website designed to collect sensitive information or deliver malware. These links can lead to phishing websites that mimic legitimate ones, where victims are tricked into entering their login credentials, financial details, or personal information.
Step 4 - Information Theft
If the victim interacts with the malicious link or provides sensitive information, the attacker can use it for various fraudulent purposes. This can include identity theft, unauthorized financial transactions, or gaining unauthorized access to the victim's online accounts.
Step 5 - Malware Distribution
In some cases, smishing messages may contain attachments or links that, when clicked, download malware onto the victim's mobile device. This malware can enable the attacker to gain control over the device, steal data, or spy on the victim's activities.
How Does Smishing Spread?
Smishing primarily occurs using the two following methods listed below.
- Fake Mobile Texts: Smishing attacks rely on fake mobile text messages to trick people into downloading malware, sharing sensitive information, or sending money to cybercriminals. Smishers take advantage of the fact that individuals are more likely to click on text messages compared to other forms of communication like emails or phone calls. Smishing attacks have become more prevalent due to the increasing use of mobile devices and the difficulty of detecting dangerous links on smartphones.
- Messenger Apps: In addition to mobile texts, cybercriminals are also using messaging apps as a medium to conduct cybercrimes. Attackers prefer smishing over other types of phishing attacks because people are more prone to clicking links in text messages. The click-through rates for SMS messages are significantly higher compared to emails. Scammers can also mask the origins of smishing messages by spoofing phone numbers or utilizing software to send texts via email.
Tips to Prevent Smishing Attacks
Although damage caused by smishing Can be devastating to both companies and individuals, there are ways to identify these attacks. To avoid smishing attacks, Keep these points in mind when responding to any messages over text or instant messaging platforms.
- Be cautious of unsolicited messages: Be wary of text messages that come from unknown or suspicious sources. Avoid interacting with unsolicited messages, especially those requesting personal information or financial transactions.
- Verify requests independently: If you receive a text message claiming to be from a trusted organization or individual, independently verify the information through official channels. Use contact information obtained from a reliable source, such as the organization's official website or a phone number from a trusted source, to confirm the legitimacy of the request.
- Avoid clicking on links: cyber criminals have used clickjacking technique for years. Refrain from clicking on links in text messages, especially those from unknown or suspicious senders. These links may lead to malicious websites designed to steal personal information or deliver malware to your device.
- Don't share sensitive information: Avoid sharing sensitive information, such as passwords, PINs, or financial details, through text messages. Legitimate organizations will not request such information via SMS.
- Be cautious of urgency and offers: Exercise caution when text messages create a sense of urgency or offer enticing rewards. Scammers often use these tactics to manipulate victims into taking immediate action without thinking critically.
- Install mobile security software: Utilize reputable mobile security software that can detect and block smishing attempts. These applications can provide an additional layer of protection against malicious text messages.
- Keep your devices updated: Regularly update your mobile device's operating system, applications, and security software. Updates often include security patches that address vulnerabilities and protect against new threats, including smishing attacks.
- Trust your instincts: If something feels suspicious or too good to be true, trust your instincts and exercise caution. If you have doubts about the authenticity of a text message, it's better to err on the side of caution and avoid interacting with it.
Comparison - Smishing vs Phishing
Both smishing and phishing attacks rely on social engineering techniques to exploit human psychology, manipulate trust, and deceive individuals into taking actions that benefit the attackers. The difference lies in the medium used for the attack.
Phishing refers to a cyber attack where scammers use fraudulent emails, instant messages, or deceptive websites to trick individuals into revealing sensitive information, such as usernames, passwords, or financial details. Phishing attacks typically occur through email or other electronic communication platforms.
Smishing, on the other hand, is a form of phishing that specifically targets individuals through SMS or text messages sent to their mobile devices. Deceiving recipients into divulging personal information is what smishing aims to do, along with downloading malware-infected files, or taking other actions that benefit the attackers.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.
Smishing Attacks: Frequently Asked Questions
As the name implies, SMS phishing primarily targets mobile devices. As long as a device has SMS functionalities, they are at risk of smishing attacks.
- Mobile Phones: Smishing attacks are prevalent on mobile phones, including smartphones and feature phones. Mobile phones are widely used for text messaging, making them an attractive target for smishing campaigns.
- Tablets: Tablets with SMS functionality or receiving text messages are also potential targets for smishing attacks. Although tablets may not have phone capabilities, they can still receive SMS messages if connected to a cellular network.
- Wearable Devices: Certain wearable devices, such as smartwatches or fitness trackers, may have SMS capabilities. If these devices can receive text messages, they can also be targeted by smishing attacks.
Smishing attacks often involve false promises of free services or products, fraudulent account issues, or fake order confirmations. Some of the examples of smishing attacks include
- COVID-19 Smishing: Scammers would pose as government officials, asking for sensitive health information.
- Financial Services Smishing: The attacker would pose as a bank representative and ask the recipient to verify suspicious activity, and request to unlock their account.
- Gift Smishing: A link would be sent to the recipient under the premise of free services or products, often using limited-time offers to entice the recipient to access the link as soon as possible.
- Invoice / Order Confirmation Smishing: Using a false confirmation of a recent purchase or billing invoice, recipients would likely use the link provided to prevent unwanted charges.





