The Definition of Smurf Attack
A smurf attack is a type of Distributed Denial of Service (DDoS) attack that exploits Internet Control Message Protocol (ICMP) packets. The attacker sends ICMP echo requests (pings) to a network's broadcast address with a spoofed source IP address (the victim's IP). This causes all devices on the network to respond to the victim, overwhelming it with traffic and potentially causing a denial of service. This type of attack is particularly effective because it leverages the network's own devices to amplify the attack, making it difficult to trace back to the original attacker.

History of Smurf Attacks
The smurf attack was first identified in the late 1990s. It was named after the "smurf.c" program, which was used to execute the attack. During this period, many networks were not configured to handle such attacks, making them highly effective. The attack gained notoriety because it was simple to execute and could cause significant disruption with minimal effort. Over time, as awareness grew, network administrators implemented measures to mitigate these attacks, but they remain a relevant threat in cybersecurity. The evolution of network security practices has reduced the prevalence of smurf attacks, but they serve as a reminder of the importance of robust network configuration and monitoring.
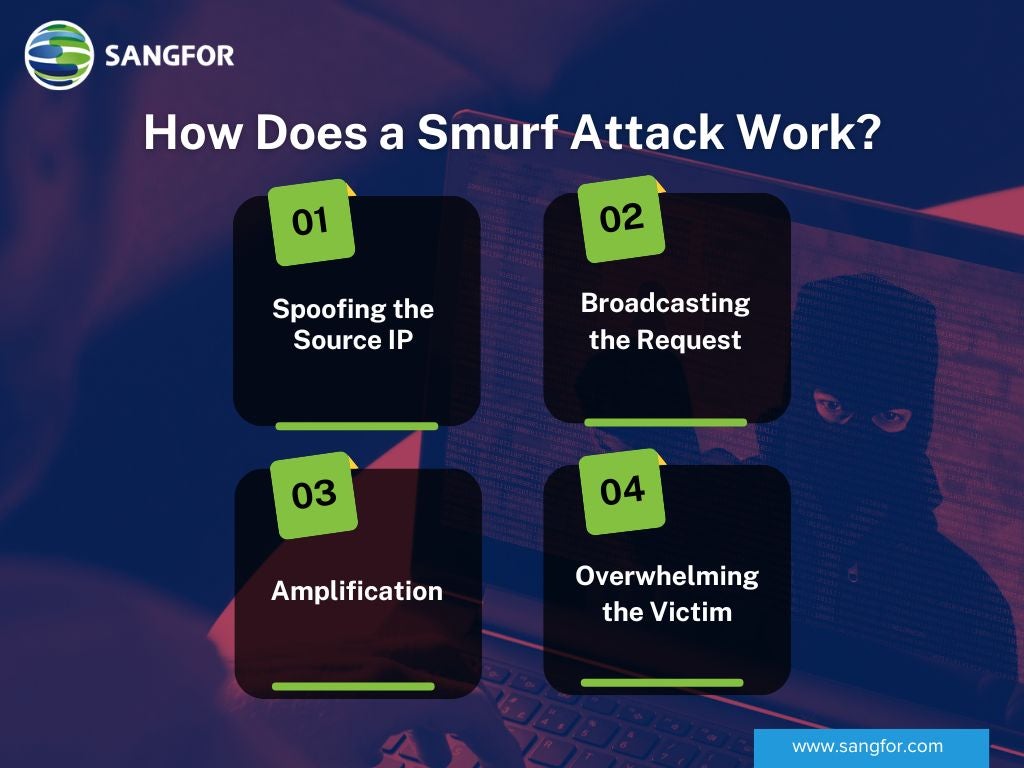
How Does a Smurf Attack Work?
A smurf attack works by exploiting the ICMP protocol. Here’s a step-by-step breakdown:
- Spoofing the Source IP: The attacker sends ICMP echo request packets with the source IP address set to the victim's IP. This makes it appear as though the victim is requesting information from the network.
- Broadcasting the Request: These packets are sent to the broadcast address of a network, causing all devices on that network to receive the request. The broadcast address ensures that every device on the network receives the packet.
- Amplification: Each device on the network responds to the echo request, sending a reply to the spoofed IP address (the victim). This significantly amplifies the amount of traffic directed at the victim.
- Overwhelming the Victim: The victim's network is flooded with ICMP replies, leading to a denial of service. The sheer volume of responses can overwhelm the victim's network resources, causing legitimate traffic to be dropped.
Types of Smurf Attacks
Smurf attacks can vary based on the scale and method of execution:
- Basic Smurf Attack: Involves sending ICMP echo requests to a single network's broadcast address. This type of attack is relatively straightforward but can still cause significant disruption.
- Advanced Smurf Attack: Utilizes multiple networks to amplify the attack, increasing the volume of traffic directed at the victim. By leveraging multiple networks, the attacker can create a more powerful and harder-to-mitigate attack.
Characteristics of a Smurf Attack
Key characteristics of a smurf attack include:
- Amplification: The attack leverages the responses from multiple devices to amplify the traffic directed at the victim. This makes the attack more effective and harder to defend against.
- Spoofing: The attacker uses a spoofed IP address to hide their identity and direct the attack towards the victim. This makes it difficult to trace the attack back to its source.
- ICMP Exploitation: The attack exploits the ICMP protocol, specifically echo requests and replies. This protocol is commonly used for network diagnostics, making it a convenient target for attackers.
Impact of Smurf Attacks on a Business
Smurf attacks can have significant impacts on businesses, including:
- Service Disruption: The primary goal of a smurf attack is to disrupt services, making websites or online services unavailable. This can lead to lost revenue and frustrated customers.
- Financial Loss: Downtime can lead to lost revenue, especially for businesses that rely on online transactions. The cost of mitigating the attack and restoring services can also be significant.
- Reputation Damage: Frequent or prolonged attacks can damage a business's reputation, leading to loss of customer trust. Customers may perceive the business as unreliable or insecure.
- Resource Drain: Mitigating and recovering from attacks can consume significant IT resources and time. This can divert resources away from other important projects and initiatives.
How to Prevent and Mitigate Smurf Attacks
Preventing and mitigating smurf attacks involves several strategies:
- Disable IP Broadcasts: Configure network devices to ignore broadcast requests. This prevents the network from responding to broadcasted ICMP requests.
- Filter ICMP Traffic: Use firewalls to filter out unnecessary ICMP traffic. This can help reduce the risk of an attack reaching the network.
- Rate Limiting: Implement rate limiting to control the flow of ICMP packets. This can help prevent the network from being overwhelmed by a large volume of traffic.
- Network Monitoring: Continuously monitor network traffic for unusual patterns that may indicate an attack. Early detection can help mitigate the impact of an attack.
Recovering from Smurf Attacks
Recovery steps include:
- Identify the Attack: Use network monitoring tools to identify the source and nature of the attack. Understanding the attack can help inform the response.
- Isolate the Attack: Implement measures to isolate the affected network segments. This can help prevent the attack from spreading and causing further disruption.
- Restore Services: Gradually restore services while ensuring the attack has been mitigated. This can help minimize the impact on users and customers.
- Review and Improve: Analyze the attack to improve future defenses and update security protocols. Learning from the attack can help prevent future incidents.
Conclusion
Smurf attacks, though less common today due to improved network security practices, remain a potent reminder of the vulnerabilities inherent in network protocols. Understanding the mechanics, impact, and mitigation strategies for smurf attacks is crucial for maintaining robust cybersecurity defenses. By staying vigilant and continuously updating security measures, businesses can protect themselves from these and other evolving threats.





