Recently, Sangfor Technologies was made aware that several servers of organizations in the construction industry had been infiltrated and encrypted by an unknown strain of ransomware. Careful tracking and analysis of the virus sample supplied by customers confirmed that the virus is a variant of the CrySiS ransom virus.
Targeted attacks on the construction industry are often launched via social engineering and RDP brute-force attacks. As many customers in the construction industry are closely interconnected, Sangfor encourages vigilance and security preparedness in the face of this new virus strain.
CrySiS has been largely dormant since its master key was released in May 2017, until it reemerged in 2018. 2019 has seen a resurgence of CrySiS on a large scale, targeting industrial industries. This variant changes the suffix of encrypted files to .jack and uses both AES and RSA encryption algorithms, making decryption impossible currently.
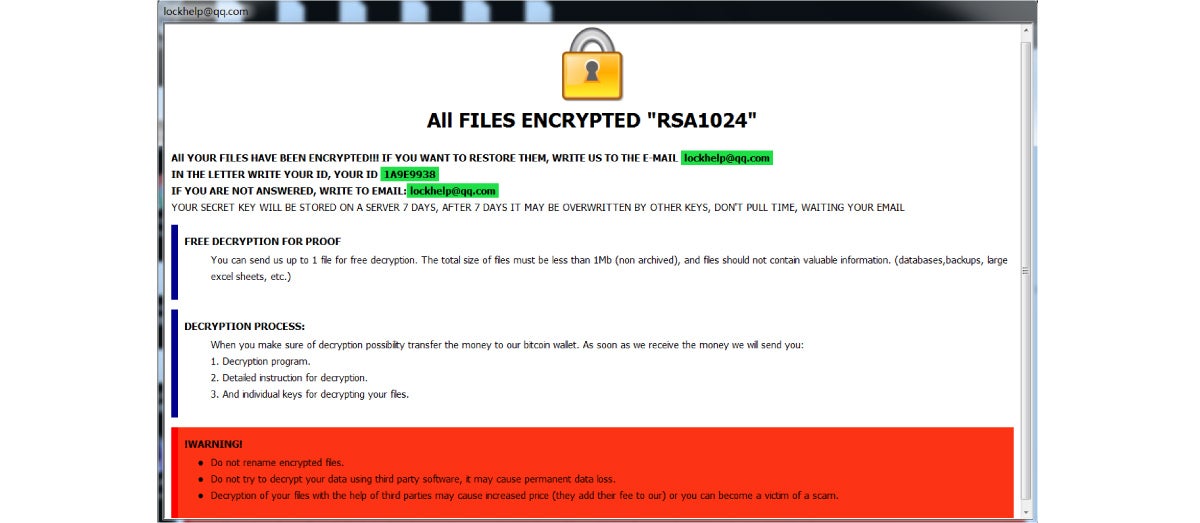
The hacker organization responsible left his own email address (as shown below) and ransom note reads, “ALL FILES ENCRYPTED ‘RSA1024’” (a powerful asymmetric encryption algorithm), as shown below:
Sample Analysis
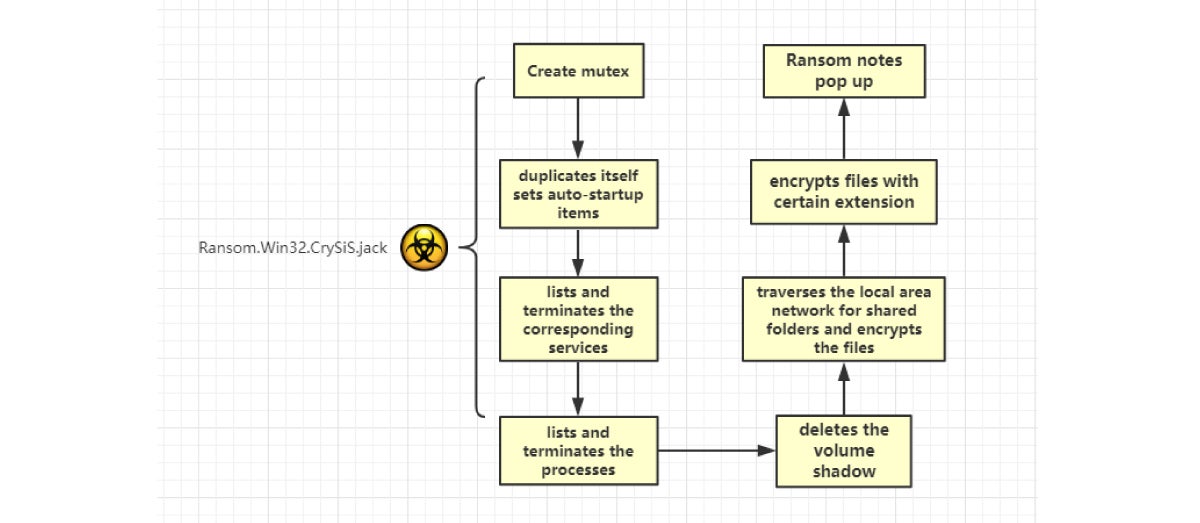
1. The whole attack process of CrySiS is as shown in the following diagram:
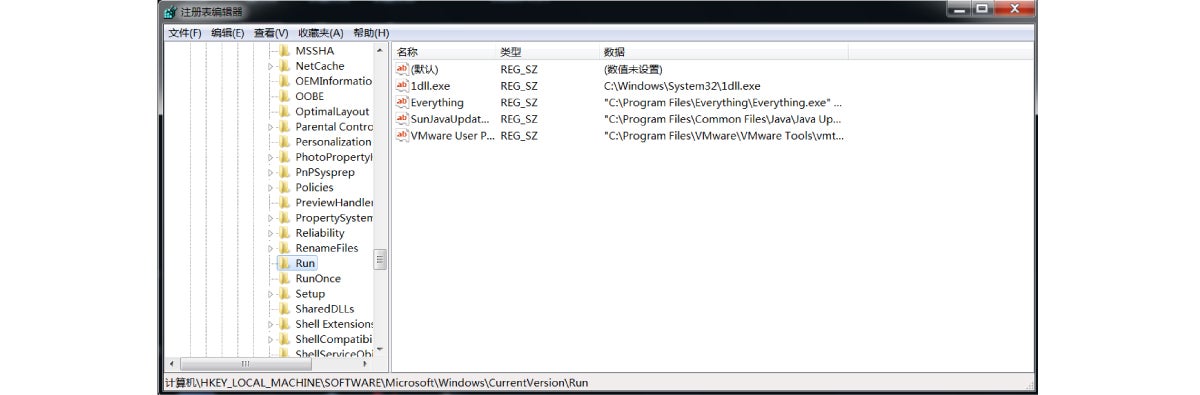
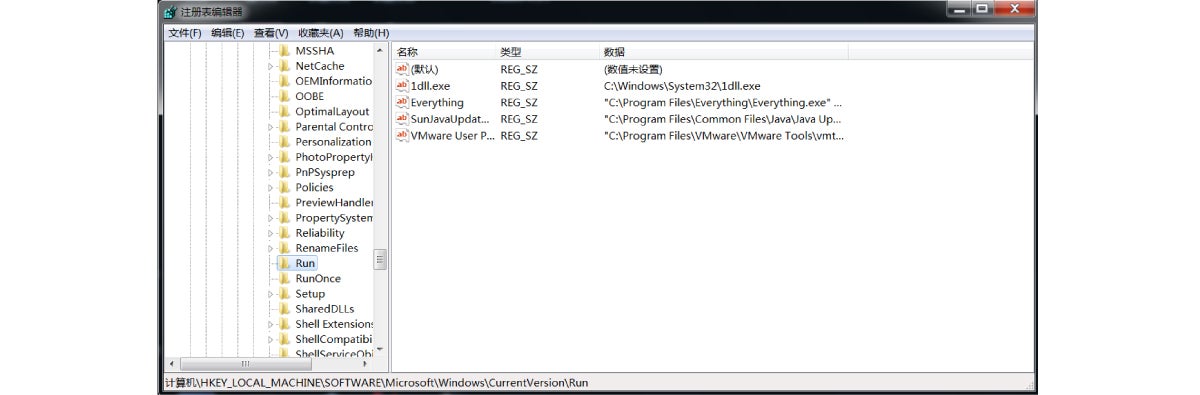
2. It duplicates itself and installs auto-startup items, as shown below:
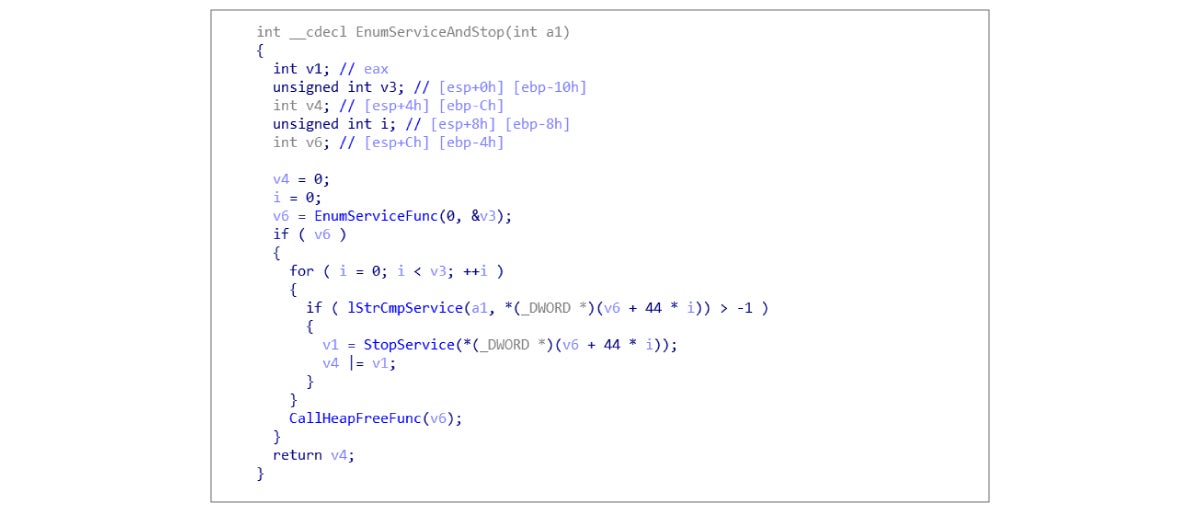
3. It then lists and terminates the corresponding services, as shown below:
The terminated services are:
• Windows Driver Foundation
• User mode Driver Framework
• wudfsvc
• Windows Update
• wuauserv
• Security Center
• wscsvc
• Windows Management
• Instrumentation
• Winmgmt
• Diagnostic Service Host
• WdiServiceHost
• VMWare Tools
• VMTools.Desktop
• Window Manager Session Manager
The disassembly code is as shown below:
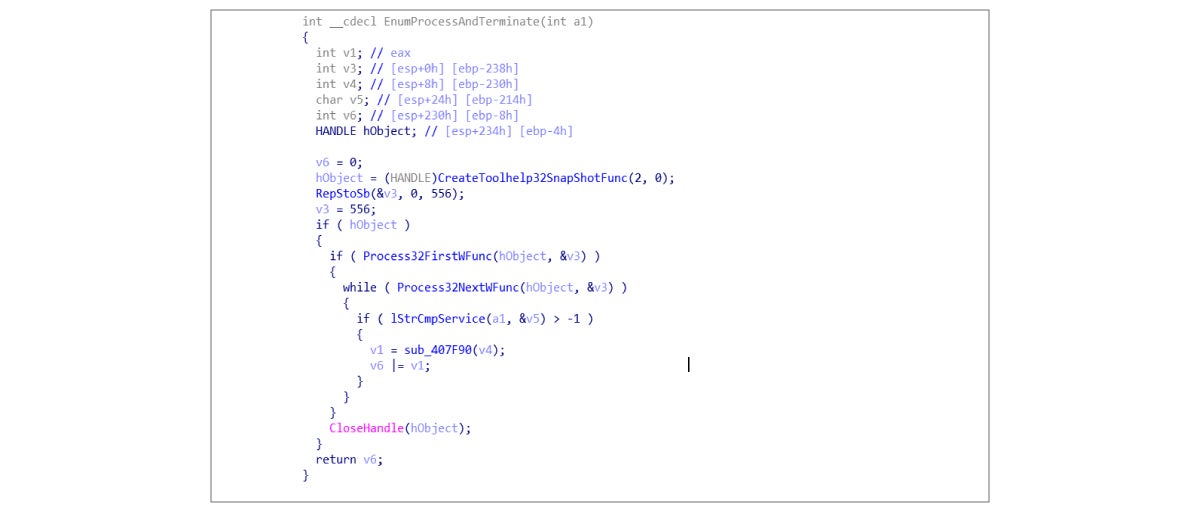
4. It then lists and terminates the processes, as shown below:
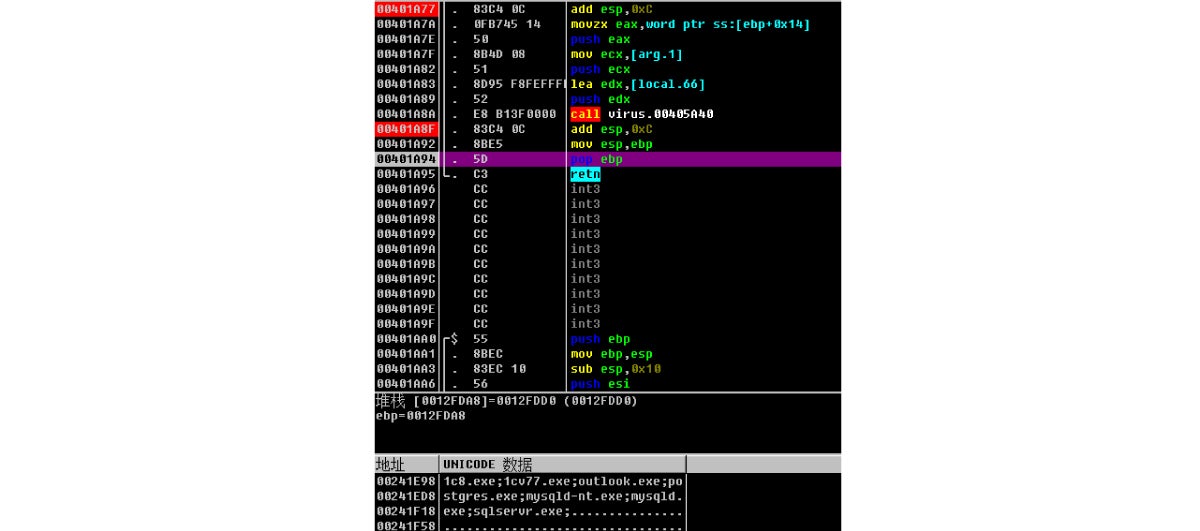
The processes are:
• 1c8.exe
• 1cv77.exe
• outlook.exe
• postgres.exe
• mysqld-nt.exe
• mysqld.exe
• sqlserver.exe
From the list above, we see that the ransomware is tasked with terminating corresponding database programs, making file encryption impossible. The disassembly code is as shown below:
5. It then deletes the volume shadow to stop data from being restored.
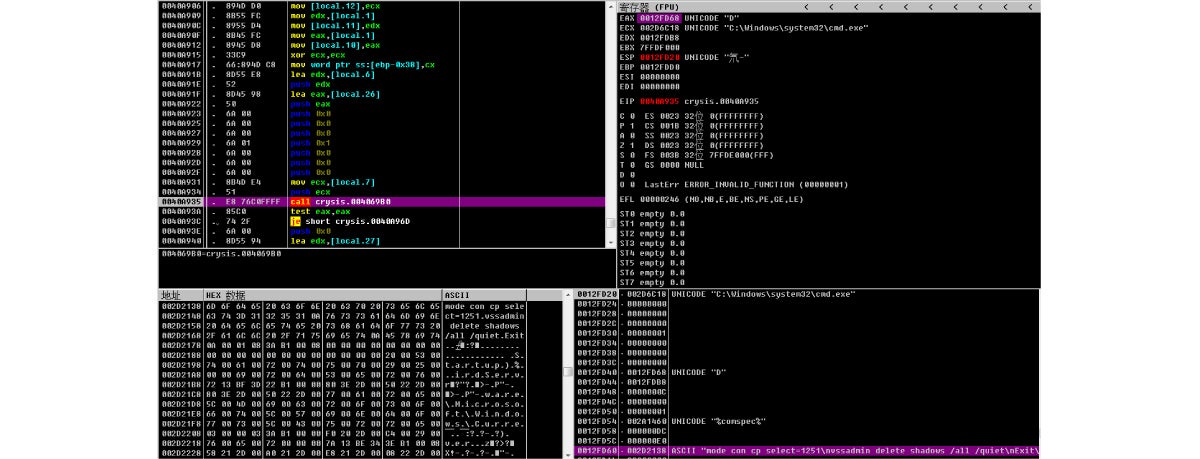
6. It traverses the local area network searching for shared folders and encrypting files.
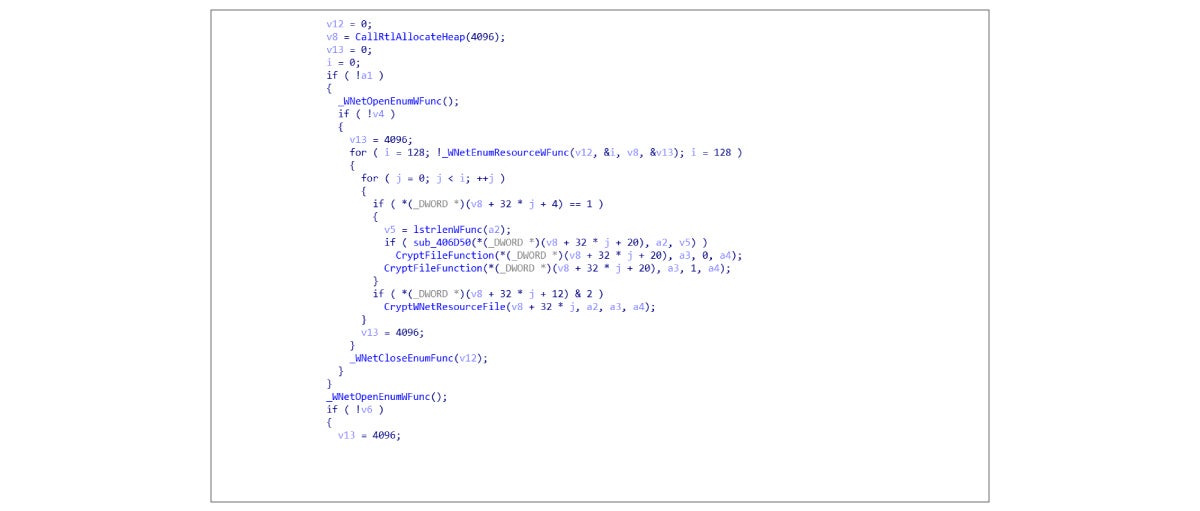
7. It continues on to encrypt files with a certain extension, as shown below:
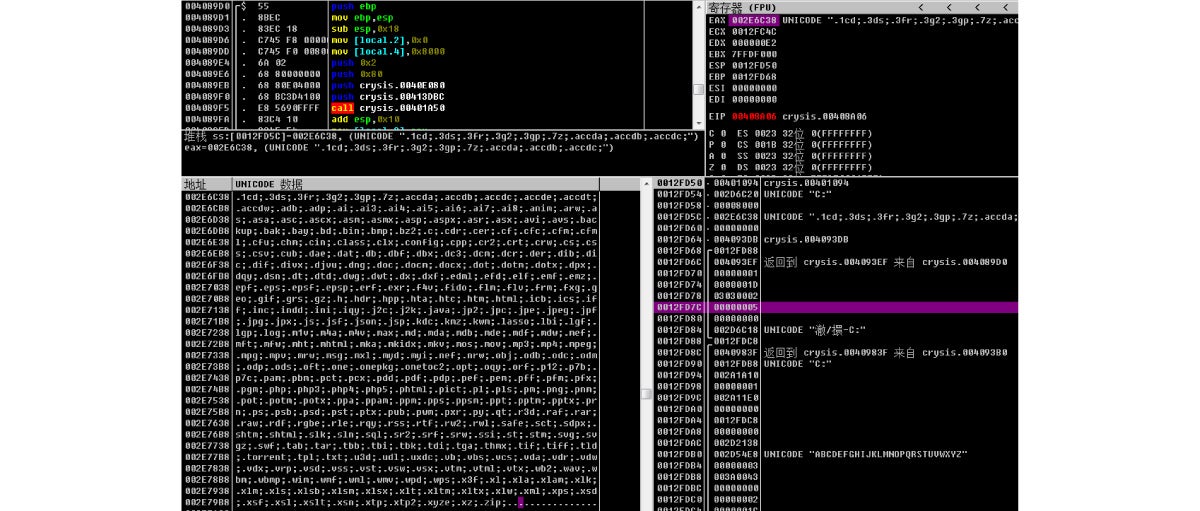
The types of files shown above are to be encrypted. The disassembly code is as shown below:
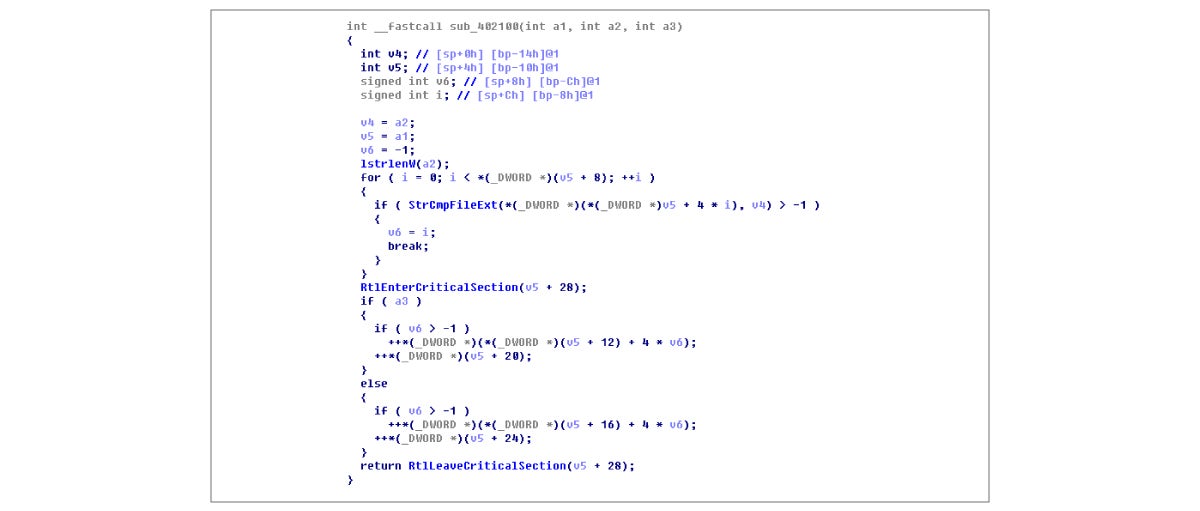
The file name is appended .jack, as shown below:
8. A ransom notes pops up and is set to auto-start through registry.
Solutions
Solutions
Currently there is no decryption tool for those victims. To minimize damage, you should isolate infected hosts and disconnect them from network. We recommend you to perform a virus scan and removal as soon as possible.
Ransomware Detection
1. Sangfor EDR and NGAF products are capable of detecting this ransom virus.
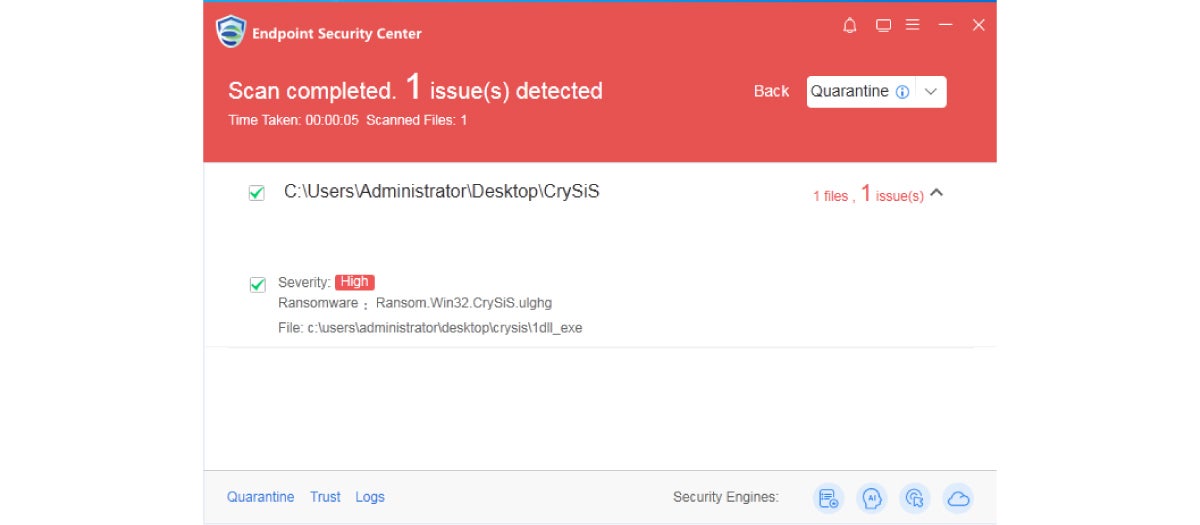
2. Sangfor offers customers and users a free anti-malware software to scan for and remove the ransomware virus.
Protection
The Sangfor Security Team recommends you take steps to prevent infection, as there is no known decryption method currently – as is the case for many viruses.
1. Fix the vulnerability quickly by installing the corresponding patch on the host.
2. Back up critical data files regularly to other hosts or storage devices.
3. Do not click on any email attachment from unknown sources and do not download any software from untrusted websites.
4. Disable unnecessary file sharing.
5. Strengthen your computer password and do not use the same passwords for multiple computers to avoid compromising a series of computers.
6. Disable RDP if it is unnecessary for your business. When computers are attacked, use Sangfor NGAF or EDR to block port 3389 and stop the virus from spreading.
7. Sangfor NGAF can prevent brute-force attacks. Turn on brute-force attack prevention on NGAF and enable Rules 11080051, 11080027 and 11080016. Turn on brute-force attack prevention on Sangfor EDR.
8. For Sangfor NGAF customers, update NGAF to version 8.0.5 and enable AI-based Sangfor Engine Zero to achieve the most comprehensive protection.
9. Deploy Sangfor security products and connect to cloud-based Sangfor Neural-X to detect new threats.
10. Perform a security scan and virus removal on the entire network to enhance network security. We recommend Sangfor NGAF and EDR to detect, prevent and protect your internal network.





