Introduction

Why you need continuous threat detection
350,000 new malware strains everyday Your existing security controls can only block 99.5% of them. That means 1750 new malware attacks every day can bypass your security devices New malware and virus variants are produced every day. According to AV-TEST Institute, there are over 350,000 new malware samples registered every day. So, you can imagine that if your existing security controls can block 99.5% of the new malware every day, there are still more than 1,750 malware threats that can bypass your security controls and get into your network. Even worse, studies show most threat detection services organizations' have in place are unable to prevent 50% of the new malwares. This is an alarming figure and should serve as a wake-up call for companies to take appropriate action when it comes to advanced threat detection, implementing network traffic analysis tools, and getting the latest and best threat hunting and detection software available.
Security Teams Need to Shift Mindset
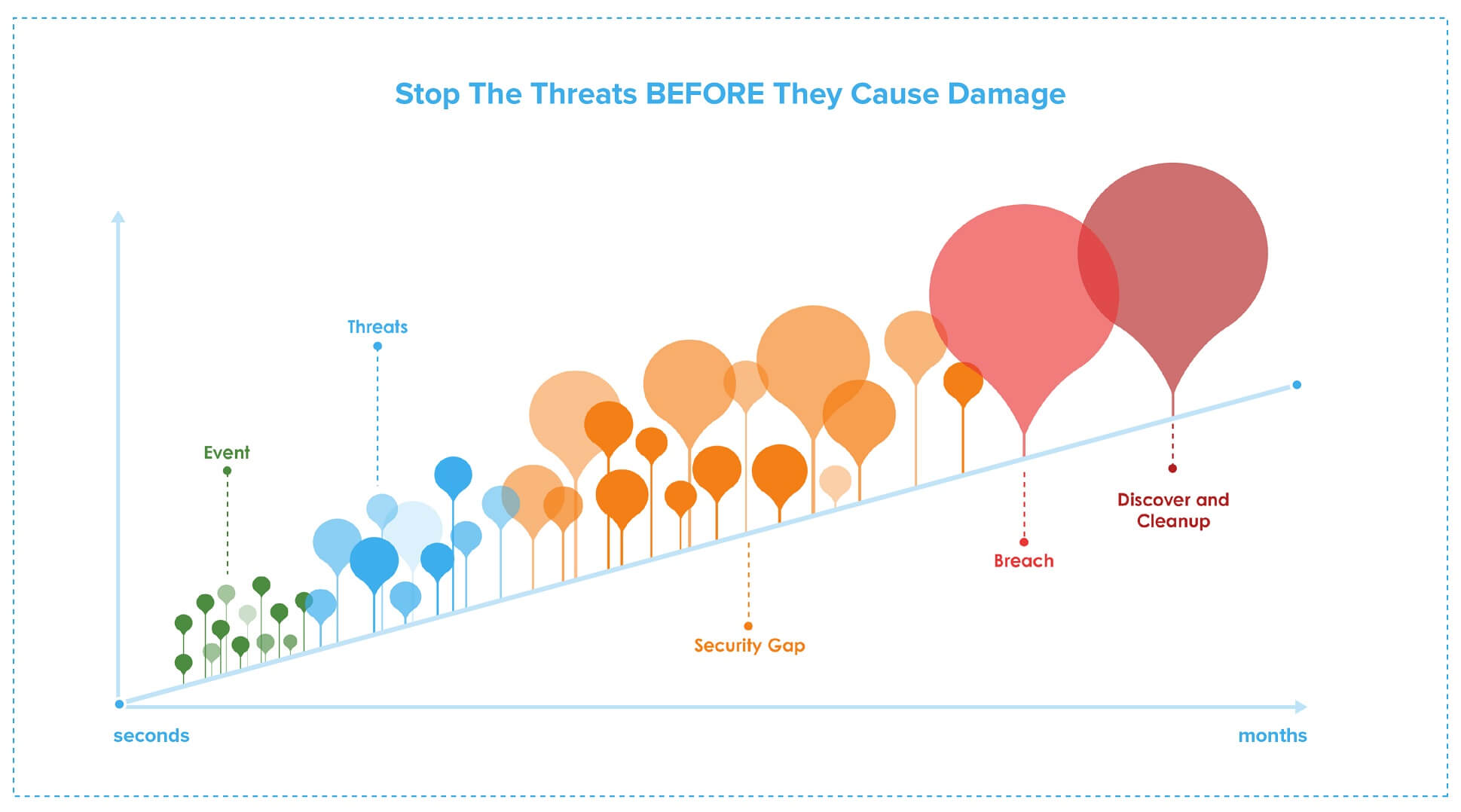
Prevention alone cannot stop attacks. Security teams must recognize that new threats require new paradigms and threat detection services to defend against them. Changing their mindset from keeping all attackers out of their network to assuming the hackers are already in their network will help develop more robust strategies to identify and stop attacks before they cause damage. Understanding mean-time-to-identify (MTTI) and mean-time-to-Response (MTTR) is important. Security events can become breaches if they have months to spread throughout a network. Security teams need to find and fix any security gaps through threat hunting and detection to reduce MTTI and MTTR; the faster they can find and respond, the less damage a breach will incur.
Work from Anywhere Scenario Solutions
All it takes is One Breach
XDDR puts emphasis on the coordinated response, ready to contain and mitigate that one breach WHEN it happens.
Recent News and Press Releases
Find out more about Sangfor’s achievements, including industry recognition, awards, and accreditation from the world’s leading analyst firms and test institutes.
Sangfor Technologies Named Winner of Coveted Global InfoSec Awards at RSAC 2025
07 May, 2025Sangfor Leads 2024 Cybersecurity Hardware Market in China
21 Apr, 2025"AI + Cloud Adoption": Sangfor Charts a New Path in Cybersecurity with Network Secure, IAG, and VPN Leading the Market
31 Mar, 2025Frequently Asked Question
With so many different malware programs out there, finding the right one can be tricky. With threat detection services and software still being in high demand, Sangfor Continuous Threat Detection is one of the leading solutions when it comes to threat hunting, threat detection, and network traffic analysis.
Malware has evolved significantly lately to evade all the threat detection software out there. Some of the ways it does this includes stalling delays, intelligent suspension, and fragmentation. With many more ways to avoid detection, the need for threat detection services and network traffic analysis tools has never been higher.


