As cyber threats evolve, hackers are becoming better at breaching networks, encrypting data, and extorting victims. In this article, we look at three of the most recent data cyber-attacks to make headlines: the Dell data breach, the Boeing cyber-attack, and the Hatari Electric hack. We then try to understand how you can protect your organization from cyber threats. First, let’s focus on the Dell cyber attack.
Dell Data Breach Affects 49 Million Customers
Technological giant, Dell, started sending out emails to its users on the 9th of May to notify them that a security incident took place that may have compromised customer names, addresses, and Dell hardware and order information. The email further stressed that no financial or sensitive data was breached. Dell noted that there was not any significant risk to customers after the Dell cyber attack given the type of information involved – severely downplaying the impact of the breach on most users.
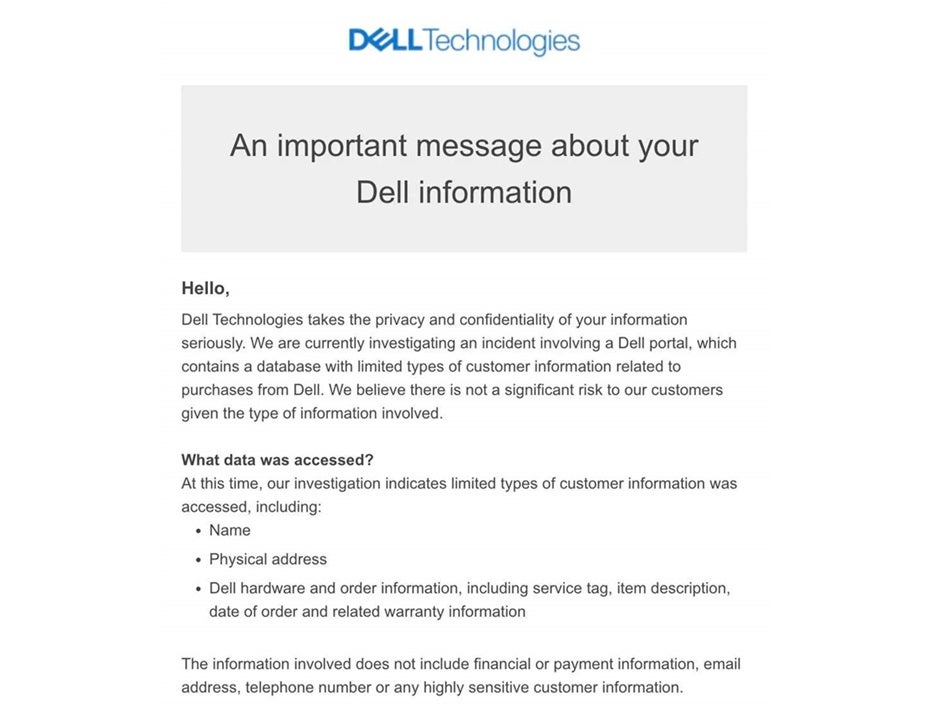
The Dell customer database hack confirmation email. Sourced from Forbes
Threat Actor Tries to Sell Dell Hack Data
In April, the Daily Dark Web reported that a threat actor claimed to have access to 49 million customer records from Dell. The declaration was put on a hacking forum and offered to sell the data to a single customer. The hacker claimed that the stolen data included information on Dell systems that were purchased between 2017 and 2024. It was also said to contain up-to-date information registered at Dell servers. This includes sensitive personal and company information such as full names, addresses, cities, provinces, postal codes, countries, unique 7-digit service tags of systems, system shipment dates (warranty start), warranty plans, serial numbers (for monitors), Dell customer numbers, and Dell order numbers.
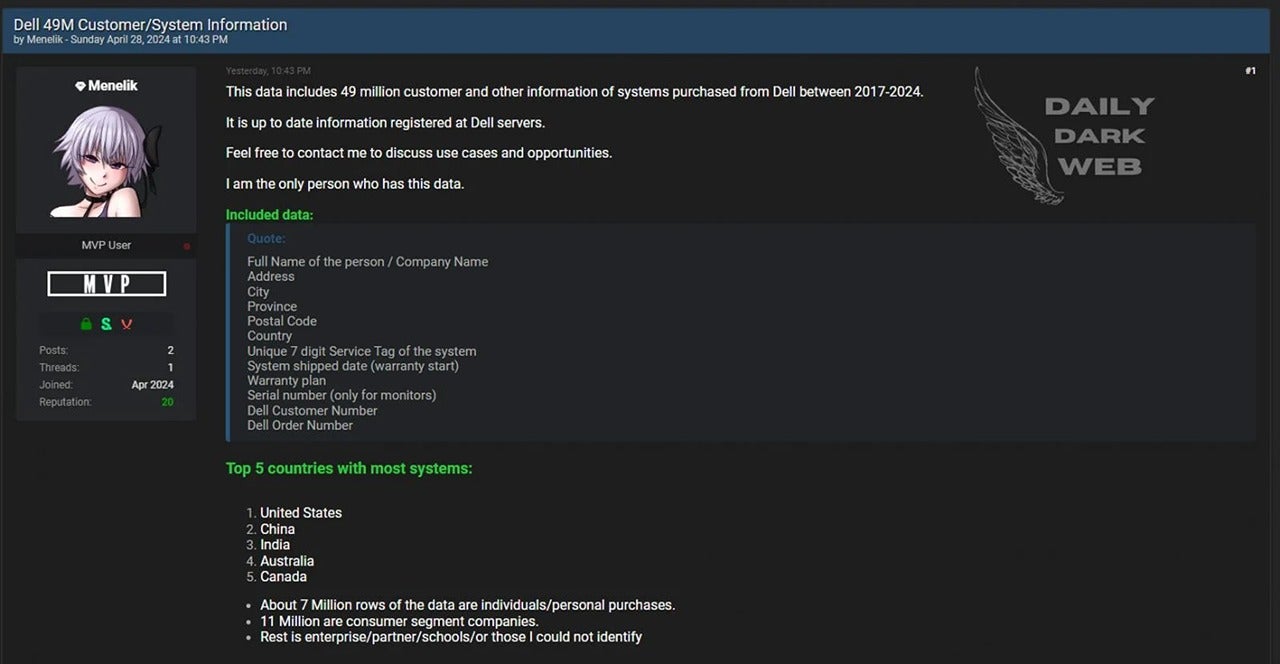
Dell customer data being sold on Breach Forums. Sourced from BleepingComputer
Around 7 million rows of the stolen Dell data are related to personal purchases while 11 million belong to consumer segment companies. The remaining data pertains to enterprises, partners, schools, or unidentified entities. The hacker also highlighted the top five countries with the most systems represented in the database. These included the United States, China, India, Australia, and Canada.
A Dell spokesperson told Forbes that the company has a cybersecurity program designed to limit risk to environments, including those used by customers and partners. They went on to state that they had “recently identified an incident involving a Dell portal with access to a database containing limited types of customer information including name, physical address, and certain Dell hardware and order information.” The Dell spokesperson further stressed that as far as numbers go, the company will not be disclosing that specific information from the ongoing investigation.
Weak API Access Controls Led to Dell Hack
The hacker shared with TechCrunch that he had brute-forced an online company portal and scraped customer data directly from Dell’s servers during the Dell data breach. The threat actor, going by the name Menelik, said he had registered with several different names on a particular Dell portal as a “partner” - these are companies that usually resell Dell products or services. After Dell had approved his partner accounts, Menelik said he brute-forced customer service tags made of seven digits of only numbers and consonants. He further stated that “any kind of partner” could access the portal he was granted access to.
Menelik told the publication that he had sent more than 5000 requests per minute to a page containing sensitive information. He continued doing this for almost 3 weeks without Dell noticing. He shared screenshots with TechCrunch as well and stated, “After I thought I got enough data, I sent multiple emails to Dell and notified the vulnerability. It took them nearly a week to patch it all up.” Dell confirmed that they had received the emails from the threat actor. The company also stated that before receiving the threat actor's email, Dell was already aware of and investigating the incident. The Dell data breach is just one of the many causing waves recently. Let’s now look at the Boeing cyber attack in more detail.
LockBit Hackers Demanded $200 Million After Boeing Cyber Attack
In 2023, airline conglomerate, Boeing, suffered from a data breach. The threat actors behind the Boeing hack used the LockBit Ransomware to target the company in 2023 and demanded a US$ 200 million ransom. The Boeing ransomware attack affected only the company’s parts and distribution business – not compromising flight safety in any way. Around 43 gigabytes of data were posted onto the LockBit website in November following the Boeing cyber attack, however, the company did not pay the ransom demanded.
Boeing Named in LockBit Indictment
Recently, the US Department of Justice unsealed an indictment against Dmitry Yuryevich Khoroshev, a man accused of being the one to develop and maintain the LockBit ransomware. In the document, an unnamed multinational aeronautical and defence corporation was named as one of the victims who were asked to pay US$ 200 million as a ransom. Boeing confirmed to CyberScoop that their company was the one referenced in the document and declined to comment further.
LockBit Gives Boeing a Deadline
In October, LockBit posted Boeing on their site and gave the company a November 2nd deadline to contact them and engage in negotiations. At the time, the hackers said that they had stolen “a tremendous amount of sensitive data” and were ready to publish it.
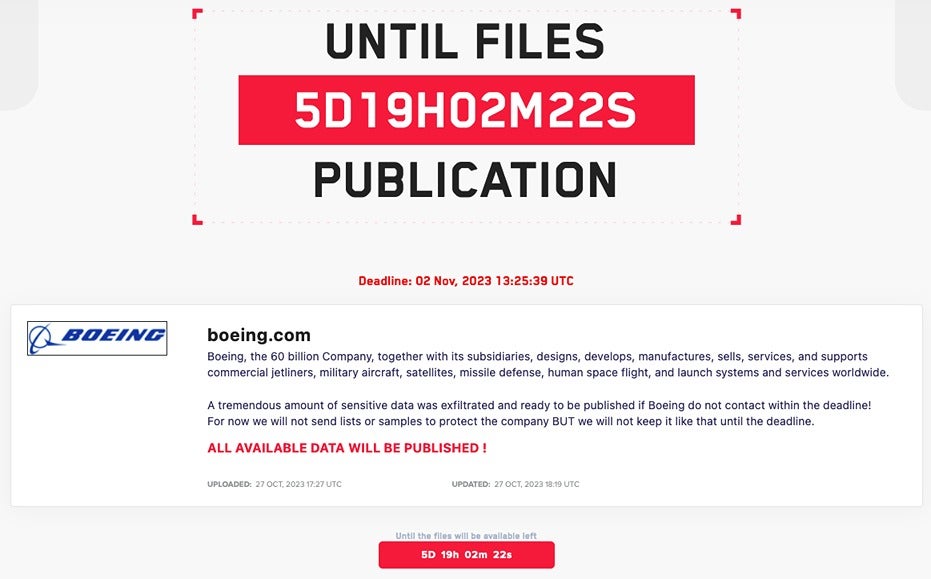
Boeing page on LockBit data leak site. Sourced from BleepingComputer
For a while, Boeing disappeared from LockBit’s list of victims but was later listed again when the hackers stated that their warnings had been ignored. The hacking group then decided to publish 4GB of sample data and threatened to release more if Boeing did not cooperate. A few days later, the group released all the Boeing hack data it had onto its website – including configuration backups for IT management software, and logs for monitoring and auditing tools. Backups from Citrix appliances were also listed - sparking speculation about LockBit ransomware using the recently disclosed Citrix Bleed vulnerability (CVE-2023-4966). Unfortunately, the Boeing ransomware attack was not the end for big corporations. Now, we’ll look at the Hatari Electric cyber attack as well.
Hatari Electric Hack by GHOSTR Exposes 617.3GB of Data
Hatari Electric Co. Ltd. is Thailand’s largest electrical appliances company. In March of 2024, the company became the victim of a data breach carried out by the threat actor known as GHOSTR. The hacker claimed that an alarming 617.3 gigabytes of data from across 18 databases were compromised during the breach. The stolen data is said to include critical corporate records, accounting information, human resources files, employee details, sales data, supplier listings, as well as partner and customer information. Joon Wanavit, the founder of Hatari Electric and one of Thailand’s wealthiest individuals, has also been affected by the cyber attack.
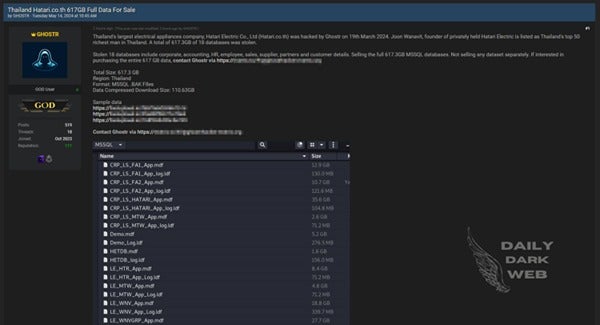
Sourced from Daily Dark Web
The threat actor, GHOSTR, has further threatened to sell the complete set of stolen MSSQL databases while also stating that individual datasets will not be for sale. The breached databases are said to be in an MSSQL.BAK file format and compressed to a download size of 110.63 GB.
When large companies fall victim to cyber-attacks, it can be daunting for other businesses that might not have the same resources and security at hand. The Dell hack, Boeing cyber attack, and Hatari Electrics breach show that all organizations can become victims of cyber attacks. The AT&T Data Breach is another example of a huge company being breached that we can take lessons from. And recently, Black Basta ransomware hacked Ascension Healthcare's systems. Now, let’s focus on how to maintain your organization's data integrity.
How To Protect Against Cyber Threats
With cyber threats quickly gaining traction against all types of companies across sectors, it’s important to prepare your organization as best as possible. These are some tips to ensure that your data is protected:
- Be wary of links and attachments. Most ransomware attacks gain access through phishing attacks directed at employee email accounts. Always check for the validity of emails, texts, and messages.
- Train and educate your workforce about maintaining proper cyber hygiene practices such as using stronger passwords, scanning for anomalies, and being cautious when using the company network.
- Embrace the system of zero-trust to ensure secure access management. This will provide access to only authorized personnel and limit risk.
- Keep software and systems updated. This will prevent the risk of vulnerabilities being exploited and ensure that your business is running off the most efficient infrastructure.
- Build up your company’s cyber resilience by implementing effective disaster recovery and cybersecurity. This will ensure that your organization will survive and recover from a cyber-attack with minimum damage or downtime.
- Install effective antivirus software and next-generation firewalls to prevent suspicious files or malware from entering the network.
- Run regular penetration tests to check on the integrity of your cybersecurity posture.
- Use network segmentation to isolate the access and attack surface for malware to spread.
- Use Extended Detection and Response (XDR) solutions such as Sangfor Omni-Command, which provides a unified, intelligent, and proactive approach to threat detection and response.
The Dell data breach, Hatari Electric breach and Boeing cyber attacks are proof that companies, whether big or small, will always be at risk of cyber threats. That’s why organizations should always stay prepared. Contact us to learn more about cyber security solutions by Sangfor.





