On February 20, 2024, the US Department of Justice (DOJ) announced that LockBit, the notorious ransomware operation that attacked more than 2,000 victims globally and extorted $120 million in ransom payments, had been finally taken down. From 2020 to 2022, LockBit was responsible for 16% of the attacks in the US, making it one of the most prominent ransomware families.
An international operation involving the FBI and law enforcement agencies of several countries, including Canada, Australia, France, and Germany, disrupted the group and took over control of their websites and servers. Two perpetrators have been taken into custody, and the encrypted files will be soon decrypted and returned to their victims.
However, in an unexpected turn of events, the ransomware group resurfaced on the dark web days after the US and UK enforcers’ announcement of its takedown. The actors behind LockBit now operate a new data leak portal on the TOR network. They have investigated their takedown and have attributed it to the exploitation of a critical PHP flaw tracked as CVE-2023-3824, facilitated by their personal negligence and failure to update PHP.
Their message also made menacing promises about providing maximum protection to every locker build and only allowing manual decryption, aiming to complicate the FBI’s next attempt to take down the group.
Sangfor has tracked the LockBit ransomware family since it appeared in 2019. We have thoroughly analyzed the tactics and hacking methods utilized by the ransomware over time. Sangfor’s experts have also been actively involved in this research for a considerable period. Let’s take a minute to review the rise of LockBit, its sophisticated techniques, and Sangfor’s protection against this formidable ransomware adversary.
LockBit Ransomware Family Background
Here is a brief overview of how LockBit developed into one of the most notorious ransomware families:
- September 2019 - LockBit attacks began in 2019. Dubbed "ABCD Ransomware" at first, it was later renamed “LockBit”.
- June 2021 - LockBit 2.0 appeared in June 2021. It introduced the double extortion technique and automatic encryption of devices across Windows domains.
- October 2021 - LockBit began infiltrating Linux servers, targeting ESXi servers. The LockBit ransomware group also introduced StealBit - a malware tool used for data exfiltration.
- June 2022 - LockBit 3.0 - also known as LockBit Black - was discovered in June 2022. It introduced the first ransomware bug bounty program and leaked new extortion tactics and Zcash cryptocurrency payment options. LockBit 3.0's code is remarkably similar to that of the famed BlackMatter and DarkSide ransomware.
- September 2022 - In September 2022, an allegedly disgruntled developer leaked the builder for LockBit 3.0's encryptor on Twitter. This was a blow to the ransomware group as the builder data allows anyone to start their ransomware kit with an encryptor, decryptor, and the specialized tools to launch the decryptor in certain ways. Based on the leaked builder, the Bl00dy ransomware gang has developed encryptors and has used them in an attack on the Ukrainian entity in September 2022.
- January 2023 - The LockBit ransomware gang released LockBit Green based on the leaked source code of the Conti ransomware.
TTPs of the LockBit Ransomware Family
The LockBit ransomware team is a large and highly sophisticated group. They possess various tactics, tools, and vulnerabilities that enable the widespread distribution of their LockBit ransomware.
For instance, LockBit ransomware can use the Mimikatz hacker tool to dump credentials.
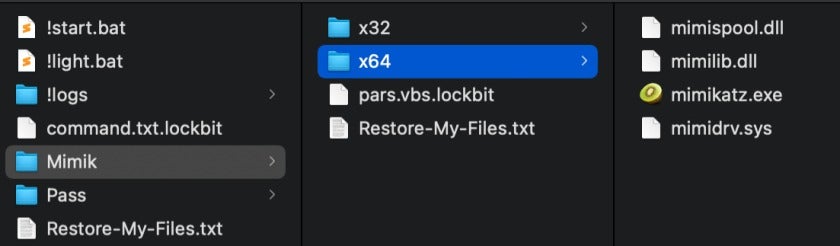
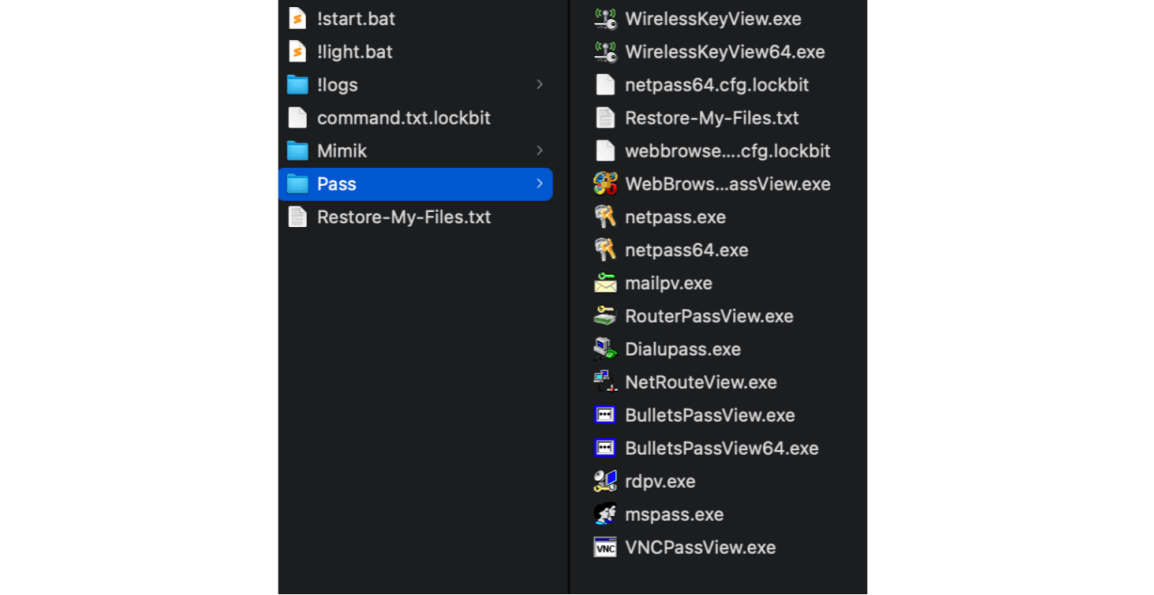
It also uses multiple third-party applications or hacker tools to steal credentials and passwords. These include Wi-Fi, web browsers, and even email passwords.
LockBit ransomware also exploits vulnerabilities to breach the target system. Sangfor has found that the group often uses vulnerabilities in Microsoft Exchange servers - namely CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. Recently, Sangfor also found LockBit 3.0 Ransomware Silently Disables EDR Using TDSSKiller as explained in this article.
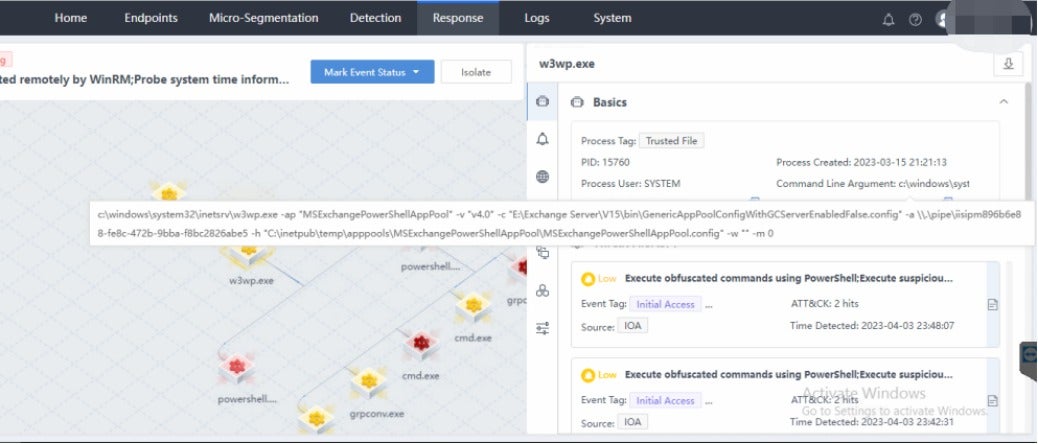
The graph above is from a real LockBit incident response plan. It involved hackers exploiting vulnerabilities that were detected by Sangfor’s Endpoint Secure platform with visual root cause analysis.
Additionally, the LockBit ransomware uses remote password spraying, brute force attacks, and pass-the-hash techniques - which can all trigger traffic alerts.
How Does Sangfor Protect Against LockBit Ransomware?
To protect against LockBit ransomware, you need a strong, multi-layered defense strategy. This includes protection at an endpoint, network, and gateway level. Sangfor’s Endpoint Secure offers direct detection and blocking of ransomware files at the endpoint level.
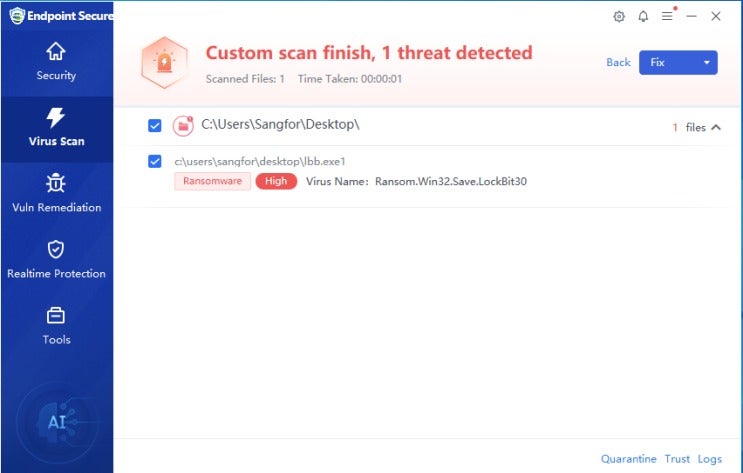
If the LockBit hacker attempts to bypass the file engines, Sangfor can still employ ransomware behavioral detection engines to block the ransomware at runtime.
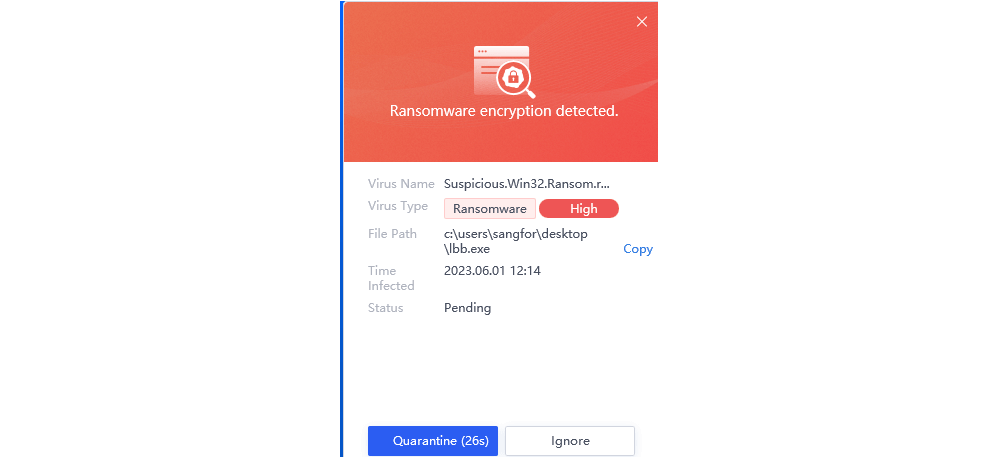
Sangfor also makes use of various AI techniques to detect and prevent ransomware attacks.

An example of this is in the ability to use Natural Language Processing to interpret a ransomware release note.

Sangfor’s Machine Learning Engine is trained using ransomware file properties that encompass thousands of dimensions and elements.

If you want to identify an early breach from a LockBit ransomware attack, it's better to detect vulnerability exploitation, lateral movement, and other forms of remote traffic attacks.
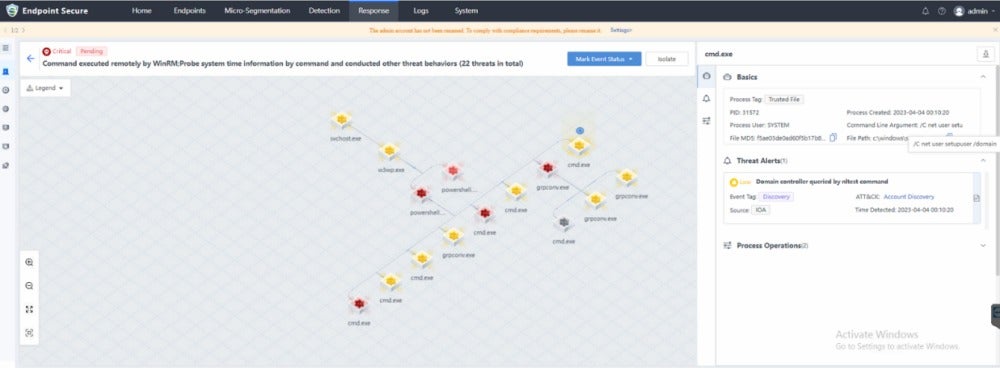
An Example of the LockBit Ransomware
The LockBit hacker in this example used commands through w3wp.exe to exploit multiple vulnerabilities in Microsoft Exchange servers (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065). This triggered the first step of the LockBit ransomware attack and the activity was immediately detected by Sangfor’s Endpoint Secure platform.
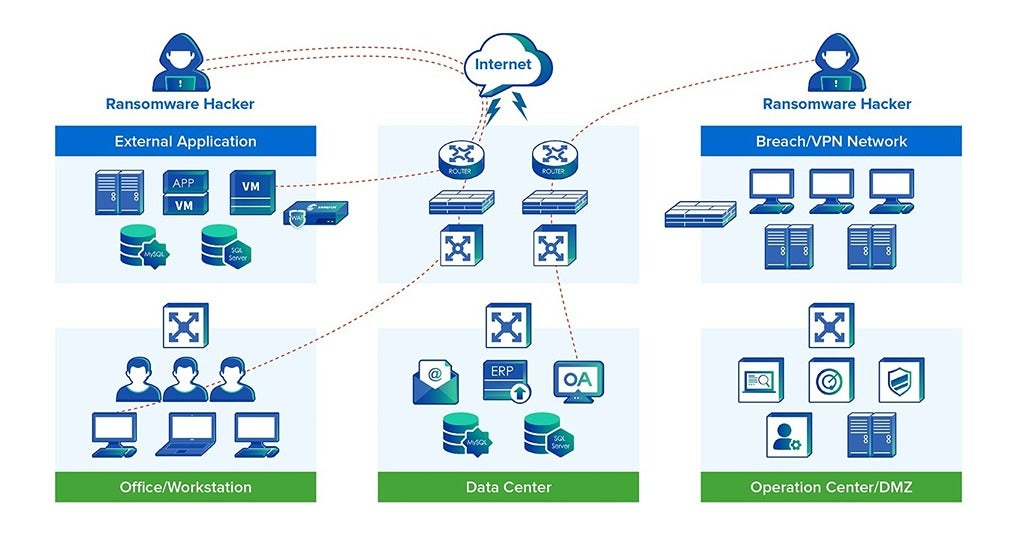
During a ransomware attack, things can become quite complex. Hackers can breach the system from various entry points – including a breach/VPN network, external applications, workstations, or data centers.
To complicate matters further, all of these hacking activities can be routed through firewalls, web application firewalls, routers, switches, or NDRs. As such, it would be a lot easier if all these devices had an integrated response during a ransomware attack.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





