As the year 2025 kicks off, it’s important to remember the mistakes and achievements that shaped the previous year. This helps us pave the way to a brighter future where we learn from our errors and actively choose to be better. This concept rings true in terms of cybersecurity awareness as well. By looking back at major cyber incidents, we can better prepare for the future. In this blog article, we explore some of the top ransomware attacks 2024 threw at us and try to understand how we can improve cybersecurity across all sectors to prevent these threats in the coming years.
Ransomware is an elusive, lucrative, and popular attack method for most hackers today. With advanced technologies like Artificial Intelligence (AI), cryptocurrencies, and Ransomware-as-a-Service platforms becoming more widespread, ransomware has become more accessible to the common man – making it all the more dangerous. To fully understand the scope of the ransomware attacks of 2024, let’s first dive in with some statistics from last year.
Ransomware Statistics for 2024
Last year was a big year for cybersecurity, with several high-profile cyber-attacks and incidents taking place. These are some of the 2024 ransomware statistics to help you get an understanding of the landscape:
- In 2024, roughly 65% of financial organizations worldwide reported experiencing a ransomware attack. (Statista)
- There has been a 56% increase in active ransomware groups in the first half of 2024. (Searchlight Cyber)
- The annual average cost of cybercrime is predicted to hit more than $23 trillion in 2027. (US Department of State)
- A 2024 survey of cybersecurity professionals of organizations worldwide revealed that 32% of the organizations suffered ransomware attacks because of exploited vulnerabilities. (Statista)
- Over 30,000 new vulnerabilities were disclosed in the past year. (TechTarget)
- On average, 59% of organizations worldwide were victims of a ransomware attack between January and February of 2024 alone. (Statista)
- Ransomware victims permanently lose 43% of the data affected by an attack on average. (SCWorld)
- Credential compromise was the second-most common cause of successful ransomware attacks, while malicious email ranked third. (Statista)
Now that we have a grasp on how dire the situation has been through last year, let’s focus on the main ransomware attacks of 2024.
List of Top Ransomware Attacks in 2024
Moving forward into 2025 allows us to look back at where we faltered along the line. Now, we’ll go over some of the top ransomware attacks from 2024 to see what we can learn from them.
Lurie Children's Hospital Ransomware Attack
In January of 2024, the Chicago Lurie Children's Hospital took its systems offline and delayed patient care after a ransomware attack. Rhysida, a popular Ransomware-as-a-Service group, demanded a US$ 3.7 million ransom in exchange for 600GB of stolen data. After Lurie refused to meet the price, the data was leaked online. The breach caused by this ransomware attack impacted around 791,000 people.
Change Healthcare Ransomware Attack
In February of 2024, Change Healthcare was hit by a ransomware attack – forcing it to shut down for several weeks. The organization invoked its security protocols and shut down its entire network to isolate an intrusion in its system. The ALPHV/BlackCat gang took credit for the attack, claiming to have stolen millions of Americans’ sensitive health and patient information. The company paid a US$ 22 million ransom. Andrew Witty, the chief executive of UnitedHealth Group (UHG) – who owns Change Healthcare - later admitted that the hackers broke into Change Healthcare’s systems using a single set password on a user account not protected with multi-factor authentication. After more details emerged about the hack, the state of Nebraska filed a lawsuit against Change Healthcare in December in which it accuses the health tech giant of security failings that led to the massive breach of at least 100 million people in America.
VNDirect Securities Ransomware Attack
In March of 2024, the third-largest stockbroker in Vietnam by capital base, VNDirect Securities became the victim of a ransomware attack as well. Nguyen Vu Long, the CEO of VNDirect, stated that the company was attacked by a group of professional hackers who encrypted the company’s data. Several customers complained that they were having difficulty accessing the company’s trading systems, making account inquiries, and placing orders. VNDirect then successfully decrypted the blocked data and began restoring the system. The following day, the Hanoi Stock Exchange (HNX) announced it would temporarily disconnect the remote trading and online trading of derivative securities transactions, debt instrument transactions, and individual corporate bond transactions of VNDirect Securities until the problem was resolved. On the 1st of April – a week after the attack - Ho Chi Minh and Hanoi stock exchanges allowed the company to resume trading. However, the company suffered an 18% year-on-year decrease in net profit primarily due to the fallout from the ransomware attack.
Ascension Health Ransomware Attack
The Ascension Healthcare ransomware attack rocked the healthcare sector in 2024. On the 8th of May, the US-based, non-profit healthcare organization was hit by a cyber-attack that severely disrupted operations across its 120 hospitals. Later confirmed as a ransomware attack, the incident encrypted thousands of computer systems - rendering electronic health records inaccessible and affecting key diagnostic services, including MRIs and CT scans. Nurses and doctors were forced to rely on printed scans during surgeries. Sources confirmed that Black Basta was the ransomware used in the attack. Ascension spent about US$ 130 million on its response to the attack – losing a net of approximately US$ 01.1 billion in operating revenue by the end of the 2024 fiscal year.
Indonesia National Data Center Ransomware Attack
In June last year, the Indonesia National Data Center fell into a ransomware attack – disrupting government services over the whole weekend. The company uncovered the attack after receiving a notification about “attempts to shut down Windows Defender” – the pre-installed security software that identifies viruses, spyware, and other malware. Several airports and ferries were affected and passport systems were brought to a halt. The attack further disrupted services at 210 state institutions nationwide. Fortunately, the Surabaya data center that was attacked in the incident was only a temporary facility being used while new data centers were being built to integrate data from government bodies at the central and regional levels. The threat actors behind the attack seemed to have been affiliates of the LockBit ransomware group and demanded a US$ 8 million ransom. However, the Communications and Informatics minister, Budi Arie Setiadi, assured that the Indonesian government would never pay the ransom. The Brain Cipher ransomware is believed to have been used in the attack.
CDK Global Ransomware Attack
June of 2024 saw a massive ransomware attack on CDK Global – a software company providing systems for car dealerships around North America and Canada. The CDK Global outage led to widespread disruptions across multiple automotive dealership systems – including tracking and ordering car parts, conducting new sales, and financing. The company chose to shut down its systems proactively – forcing employees to manually record transactions on paper. The BlackSuit ransomware group took credit for the attack and demanded 387 Bitcoin – which is roughly US$ 25 million - as a ransom. The third-party data and personally identifying information (PII) that were stolen by the group then allowed threat actors to orchestrate a secondary attack campaign on CDK customers. On June 21, SC Media reported that CDK “posted a voicemail advising that threat actors are contacting CDK customers and business partners posing as members or affiliates of CDK.”
NHS England Ransomware Attack
Also in June of 2024, The UK's National Health Service (NHS) confirmed that the patient data managed by pathology testing organization, Synnovis, was stolen in a ransomware attack. More than 3000 hospital and GP appointments were affected by the attack orchestrated by Russian hacking group, Qilin. The group went on to share almost 400GB of confidential data on their darknet site after threatening Synnovis in the ransomware attack. The data included requests for appointments and pathology and histology tests. Synnovis obtained a preliminary injunction from the English High Court against the ransomware group ordering them not to access Synnovis’ IT systems. While it might seem moot to do so, it forces platforms such as Telegram as well as ISPs to demand the removal of the hacked data. Following this injunction, the Telegram channel used by Qilin to distribute the data no longer appeared to be active.
OneBlood Ransomware Attack
In July of 2024, the healthcare sector took another hit when OneBlood, a non-profit blood donation service, became the victim of a ransomware attack that affected its critical software systems. The incident affected the company’s ability to ship blood products to hospitals in Florida and OneBlood had to resort to manual labeling of blood products. The organization also had to ask more than 250 hospitals under their service to activate their critical blood shortage protocols and remain in that status for as long as needed.
Casio Ransomware Attack
In October of 2024, Casio suffered a ransomware attack that compromised the personal data of almost 8,500 people. The massive Japanese electronics company had more than 200 gigabytes of data stolen by the Underground ransomware group. After investigating, Casio revealed that the breach had impacted the data of almost 6,500 employees – revealing information such as names, employee numbers, email addresses, gender information, dates of birth, ID card data, family data, and taxpayer ID numbers. The attack also compromised the personal information of more than 1,900 Casio business partners and 91 customers. The company revealed later that the attackers used phishing techniques to get in, due to “some deficiencies in the company’s measures against phishing emails.”
Schneider Electric Ransomware Attack
In November, the French multinational company, Schneider Electric, became the victim of a ransomware attack. The Hellcat ransomware group took credit for the attack and taunted the company online asking for the absurd ransom of US$ 125,000 in "Baguettes" to prevent the data from being leaked.
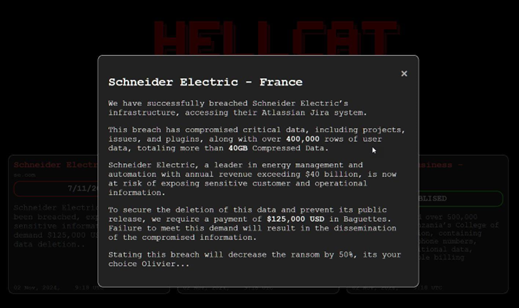
Source: BleepingComputer
The group claimed to have stolen 40GB of compressed data. Later it was found that the group actually wanted US$ 125,000 in Monero cryptocurrency and overplayed the baguette aspect to gain traction in the news.
Deloitte UK Ransomware Attack
In December of 2024, a ransomware group called Brain Cipher claimed to have hit Deloitte UK with a ransomware attack. The group stated that they breached the organization’s systems and stole 1 terabyte (TB) of compressed data. The group provided a deadline for Deloitte to respond and threatened to disclose how "the 'elementary points' of information security are not observed" by the firm. The group further criticized large corporations for not adequately securing their systems - implying that Deloitte's cybersecurity practices were insufficient. Deloitte issued a statement denying that the breach had impacted any of its systems – stating that “the allegations relate to a single client’s system which sits outside of the Deloitte network.”
These are only a few of the top ransomware attacks to make headlines last year. Now, let’s take a look at some of the more popular ransomware groups in 2024.
Ransomware Groups Who Made Waves in 2024
Ransomware groups are often emboldened by anonymity; however, many thrive in popularity as well. This is especially true for Ransomware-as-a-Service groups who use their notoriety to attract customers. These are some of the main ransomware groups that took the spotlight in 2024:
Akira
The ransomware group emerged in 2023 as a breakoff group from the Conti Ransomware – most likely one that has more ties with Conti’s infrastructure than any other group. According to an advisory from CISA, as of the 1st of January 2024, the ransomware group has impacted over 250 organizations and claimed approximately US$ 42 million in ransomware proceeds. Statista showed that in the third quarter of 2024, the Akira ransomware accounted for 13% of the market share of ransomware attacks, making it the most prevalent variant in the United States.
Play or PlayCrypt
The Play Ransomware emerged in 2022 and focused on exploiting supply chain vulnerabilities in common security software used by popular organizations, such as Fortinet, Citrix, and VMWare’s ESXi. A July 2024 report by Trend Micro revealed a connection between Play and Prolific Puma – another ransomware group known for generating domains using random algorithms and offering link-shortening services to cybercriminals to evade detection. In 2024, Play ransomware claimed 362 victims.
LockBit
Despite a global law enforcement operation taking down key LockBit infrastructure in February of 2024, the gargantuan ransomware group seems to still be around. The resurgence of LockBit 3.0 came back with a vengeance - becoming the most prominent ransomware actor in May of 2024. In May alone, the group launched 176 ransomware attacks, 37% of the total number for the month. This represents an enormous 665% month-on-month increase for the ransomware-as-a-service (RaaS) gang.
RansomHub
In February of 2024, RansomHub emerged as a Ransomware-as-a-Service (RaaS) group and gained notoriety during the Change Healthcare attack. While the group was not directly involved in the attack, it allegedly acquired the stolen data and issued a ransomware demand to Change Healthcare to prevent its release. Since February of 2024, RansomHub has conducted at least 210 attacks. The group is allegedly behind attacks on Rite Aid, American Clinical Solutions, the Neurological Spine Institute of Savannah, and the Florida Department of Health. CISA and the FBI issued a joint cybersecurity advisory about the RansomHub ransomware group in August.
Black Basta
Surfacing in 2022, the Black Basta Ransomware-as-a-Service group quickly gained traction by targeting 19 prominent companies and having more than 100 confirmed victims in its first few months of operation. Black Basta uses double extortion tactics - encrypting victims’ data and then threatening to leak sensitive information on its public leak site on Tor, Basta News. The group has hit organizations in the US, Japan, Canada, the United Kingdom, Australia, and New Zealand in highly specific attacks. In 2024, Black Basta took credit for the attack on Ascension Healthcare.
Brain Cipher
A relatively new ransomware, Brain Cipher was first identified in mid-2024 and gained recognition after a high-profile attack on Indonesia's National Data Center in June - disrupting essential public services and immigration processes. The group uses multi-pronged extortion strategies and a TOR-based data leak site to pressure victims into compliance. Brain Cipher also took responsibility for the ransomware attack on Deloitte UK in 2024.
DarkVault
While it emerged in 2023, DarkVault only became a proper threat in 2024. The new ransomware group came out with strong similarities to the LockBit ransomware – leading many to believe that it was a copycat. The group specializes in ransomware attacks, bomb threats, swatting, doxing, website defacing, malware creation, scams, spam, and various forms of fraud. DarkVault's most recent activity includes the publication of 19 victims' data on its leak site in April while its notable victims include the UK-based charity Tommy Club and a data breach at Sandip University in Nashik, India.
These ransomware groups emerge – and then reemerge – throughout the years to cause havoc and open up a wider attack surface on organizations. However, if we can learn from the past and invest in essential cybersecurity technologies and practices, we can ensure a better and safer future.
How to Stay Prepared and Protected Against Ransomware in 2025
To ensure effective ransomware protection in 2025, organizations can follow these few best practices:
- Regularly update software, operating systems, and firmware to ensure the latest features and patches.
- Use strong passwords that are regularly changed and efficiently managed.
- Raise cybersecurity awareness across your workforce with campaigns, events, and regular educational workshops.
- Use Multi-Factor Authentication (MFA) for all user accounts to prevent phishing.
- Adopt a zero-trust policy across your organization to ensure watertight access control.
- Invest in robust Endpoint Security products that monitor endpoints for suspicious activity.
Sangfor’s Anti-Ransomware solution seamlessly identifies and prevents all aspects of the ransomware kill chain to give your organization a secure and reliable platform to mitigate the risk of ransomware in the future. Sangfor Technologies also provides versatile and integrated superior cybersecurity and cloud computing infrastructure that ensures ransomware protection.
As we look back at the top ransomware attacks 2024 had in store, it’s important to learn from these headlines and invest in the technologies and infrastructure to prevent them. Proactive, innovative, and enhanced cybersecurity solutions are essential in combating the spread of ransomware in 2025. Contact Sangfor Technologies today or visit www.sangfor.com for more information.





