The digital landscape in Asia has witnessed numerous cyber-attacks, making it one of the fastest-growing regions in terms of such incidents. From the data breach for Shangri-La Hotels in Asia to the recent Jolibee data breach in the Philippines, service sectors are increasingly burdened with cyber threats in Southeast Asia. The Southeast Asian country of Indonesia is no stranger to cyber-attacks. According to the Global Data Breach statistics, Indonesia has recorded the highest number of breached accounts in Southeast Asia, totaling 144 million. As of the first quarter of 2023, the number of data breaches in Indonesia reached approximately 89.11 thousand records. In this blog article, we take a closer look at the recent Indonesia Ransomware Breach. This incident has urged organizations to strengthen their data security regulations and parameters to maintain client trust. Additionally, we will explore strategies for businesses to prevent future cyber threats. First, let’s provide a brief overview of the data breaches that have impacted Indonesia Immigration and other government services.

Indonesia Ransomware Breach Disrupted Government Services
On the 20th of June, the Indonesia National Data Center was hit by a ransomware attack that disrupted government services over the entire weekend. Most ferries and airports in the country were affected by the attack and passport verification systems were brought down. The hackers demanded a ransom of US$ 8 million and seem to be affiliates of the LockBit ransomware group. Security experts believe that a 2023 build of the LockBit 3.0 ransomware that was leaked is now being deployed by another threat actor making use of the Phorpiex botnet. This version that was used to attack Indonesia’s national data center is called Brain Cipher ransomware and is the latest version of LockBit 3.0 under the group’s control. (read this article to learn more about the Brain Cipher)
While services have been gradually getting back online, it’s still unclear if any personal data was compromised in the attack. The Surabaya data center that was attacked was a temporary facility being used while new data centers are being built to integrate data from government bodies at the central and regional levels. Semuel Abrijani Pangerapan, a Communications ministry official, has said that the Indonesia national data center attack is still being investigated and that a digital forensics team has been brought in.
The head of the National Cyber and Crypto Agency (BSSN), Hinsa Siburian, shared with the public that digital forensic investigators found the usage of the new variant of the existing malicious software Lockbit 3.0.
Communications and Informatics minister, Budi Arie Setiadi, has assured that the Indonesian government will never pay the ransom demanded and his department confirmed that the cyber-attack had disrupted services at 210 state institutions nationwide.
The spokesman for the National Cyber and Crypto Agency - or BSSN - Ariandi Putra, revealed in a statement that the cyber-attack was first detected on the 17th of June when the agency received a notification about “attempts to shut down Windows Defender” – a pre-installed security software that helps to identify viruses, spyware, and other malware.
According to The Register, Indonesia’s president Joko Widodo, has now ordered an audit of government data centers after it was revealed that most of the data they store is not backed up. This news comes after the Indonesia ransomware breach on the Temporary National Data Center. On the floor of Parliament, the head of the National Cyber and Encryption Agency (BSSN), Hinsa Siburian admitted that no backup was made for 98% of the data stored in one of the two compromised data centers.
Budi assured that while backup capacity is available to government agencies at the data centers, the use of it was optional due to budget constraints -however, in the future, it will now become mandatory. The Chair of the First Commission of the People's Representative Council, Meutya Hafid, responded to the issue by stating that this was not a governance issue, but a “stupidity issue” to have national data without a single backup. Now, let’s try to unravel the effects of the Indonesia cyber attack that turned it into an immigration ransomware breach.
Effects of the Indonesia Ransomware Breach
Following the Indonesia ransomware breach, many travelers were forced to queue in long lines to have their passports manually checked. Usually, passengers moving through customers and immigration will use automated passport-checking kiosks at Indonesian airports, however, the attack disrupted all those systems. Ferries also saw lines lasting for hours as booking systems were down and employees were forced to use pen and paper to manually record transactions and trips.
With such a massive impact on the immigration process, the attack has sparked outrage from the public who took to social media to complain about the service and demanded accountability.
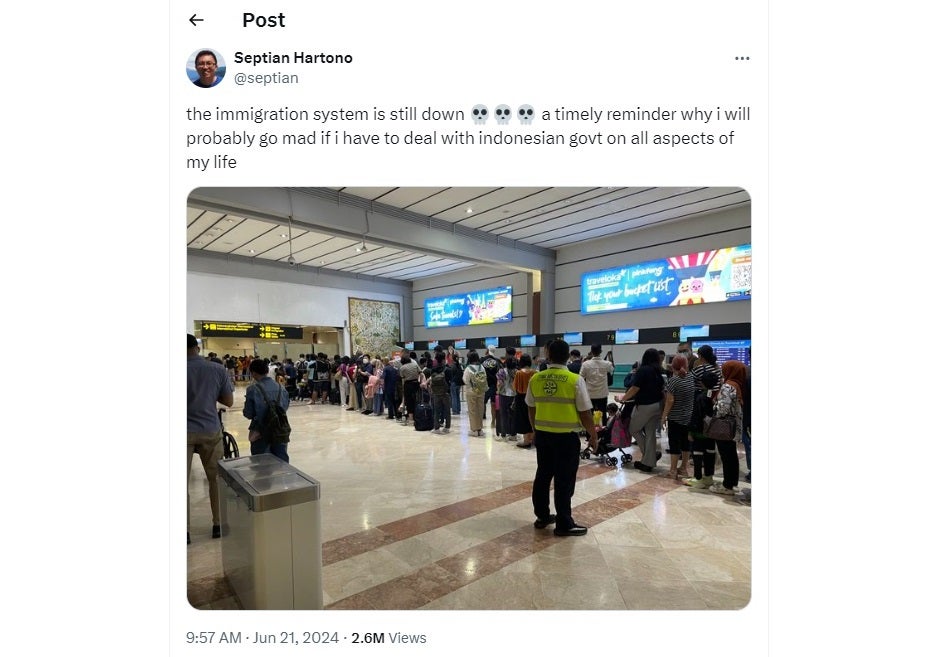
Sourced from X
While the travel sector took a major hit, other services like financial licensing and student registration, may be out for a longer as the national data center appears to be bringing systems back online without the use of a decryption key or cooperation from the hackers.
BSSN spokesman Hinsa also confirmed that the Indonesia Automatic Fingerprint Identification System used by the police was also accessed during the attack. The biometric data has been offered for sale on a data leak site since June 22nd for US$ 1,000, however, Hinsa maintains that the information being sold “was old data”.
Wahyudi Djafar, the executive director at the Jakarta-based Institute for Policy Research and Advocacy, said the incident had highlighted “the state’s failure to protect citizens’ personal data” He goes on to state that public trust in the government’s plans for digital transformation of government services will decrease drastically and that there is a possibility that the public will be afraid if their personal data is collected by state institutions. Governments have a responsibility to secure data – especially when trying to figure out how much a data breach will cost you in the long run.
Laws and Regulations for Data Breaches in Indonesia
Indonesia has an alarming number of cyber-attacks; however, the country also has stringent laws and regulations to protect private data in the hands of organizations and governments. Data protection in Indonesia is mainly regulated by Law No. 27 of 2022 on Personal Data Protection – or the PDP Law. This is Indonesia's first overarching regulation on data protection applicable to various sectors. The PDP Law has 76 articles across 16 chapters that extensively cover data ownership rights, prohibitions on data use, and regulations regarding the collection, storage, processing, and transfer of personal data of Indonesian users.
In the event of a data breach, the law demands the controller notify both the affected personal data subjects and the PDP Agency. More serious breaches which would disturb public services and/or significantly affect the public interest, need to be made public.
Now, let’s focus on some preventative measures that could have been used during the Indonesia ransomware breach.
Security Measures That Could Have Prevented the Indonesia Ransomware Breach
While the government of Indonesia may have dropped the ball when it came to preventative measures for data security, it’s important to realize that cyber-attacks on such a large scale are often complex, evolved, and very difficult to avoid. Organizations need to ensure that they can avoid the next ransomware breach by being prepared and having backups to maintain crucial services. Some preventative measures of note here include:
- Installing an effective Ransomware Protection Solution to protect your data from within the system and detect anomalies.
- Regularly updating software and patches to stay protected from vulnerabilities.
- Using strong passwords and Multi-Factor Authentication.
- Educating staff and government officials alike on cybersecurity practices to avoid social engineering attacks or mismanagement.
- Sticking to regulations around data privacy and security.
- Maintaining transparency about security incidents.
Sangfor Solutions
Sangfor Endpoint Secure: Sangfor Endpoint Secure supports the detection and blocking of Brain Cipher ransomware with its AI-driven static and dynamic ransomware detection engines. The static engine blocks ransomware files upon landing on endpoints, while the dynamic engine defends against ransomware payload execution. This combination enables Endpoint Secure to “Kill Ransomware in 3 Seconds,” achieving 100% detection accuracy for known ransomware and 99.83% for unknown ransomware.
Sangfor Cyber Guardian Incident Response (IR) and Managed Detection Response (MDR): Sangfor Cyber Guardian offers incident response (IR) services for victims of ransomware and other cyberattacks. Cyber Guardian IR provides both on-site and remote response assistance, including threat containment to stop the spread of the attack and in-depth threat hunting to eliminate threats from the environment. Alternatively, Sangfor Cyber Guardian Managed Detection and Response (MDR) provides 24/7 monitoring, response, and protection by a team of security experts to keep you safe at all times. The Cyber Guardian team uses their experience in offensive and defensive security to accurately verify and report only true positives.
While our data is constantly being collected, processed, and stored in multiple different ways each day – companies are still fully liable for the misuse and unlawful access to that data under any circumstance. This is why cybersecurity tools and practices need to be a mandatory part of every organization's resources. Allow the Indonesia ransomware breach to be a reminder that your company’s data is vulnerable in any industry and demands the right protection. For more information on cloud infrastructure and cybersecurity, visit www.sangfor.com today.
Frequently Asked Questions
The data breach notification law in Indonesia states that a personal data breach be notified by the controller to both the affected personal data subjects and the PDP Agency. More serious breaches which would disturb public services and/or significantly affect the public interest, need to also be notified to the public.
To protect your company from ransomware, you should:
- Use an effective Ransomware Protection Solution
- Regularly update software and patches
- Using strong passwords
- Enable Multi-Factor Authentication
- Ensure cybersecurity awareness and training





