
Colonial Oil Pipeline Hack Confirmed to be DarkSide
The FBI confirmed on 10 May 2021 that the oil pipeline ransomware attack on 8 May 2021 against Colonial Pipeline was conducted by the Darkside ransomware group. The Darkside Group claimed responsibility for the attack on their website and offered a statement of remorse.
Colonial Pipeline is the largest oil product pipeline operator in the United States, and the attack forced shutdown of all their operations. To avoid greater impact, the company has proactively cut off business system networks to prevent spread of the malware to operational industrial control systems (ICS). Colonial then suspended all pipeline operations until they are sure that no ICS networks are compromised. Operations will slowly be brought back online with hope of full operations by the end of the week.
According to BBC news, the criminal group planted malware on the target system in order to demand a ransom, hijacked nearly 100GB of the company's data, and threatened that if the payment is not made, the data will be leaked to the Internet.
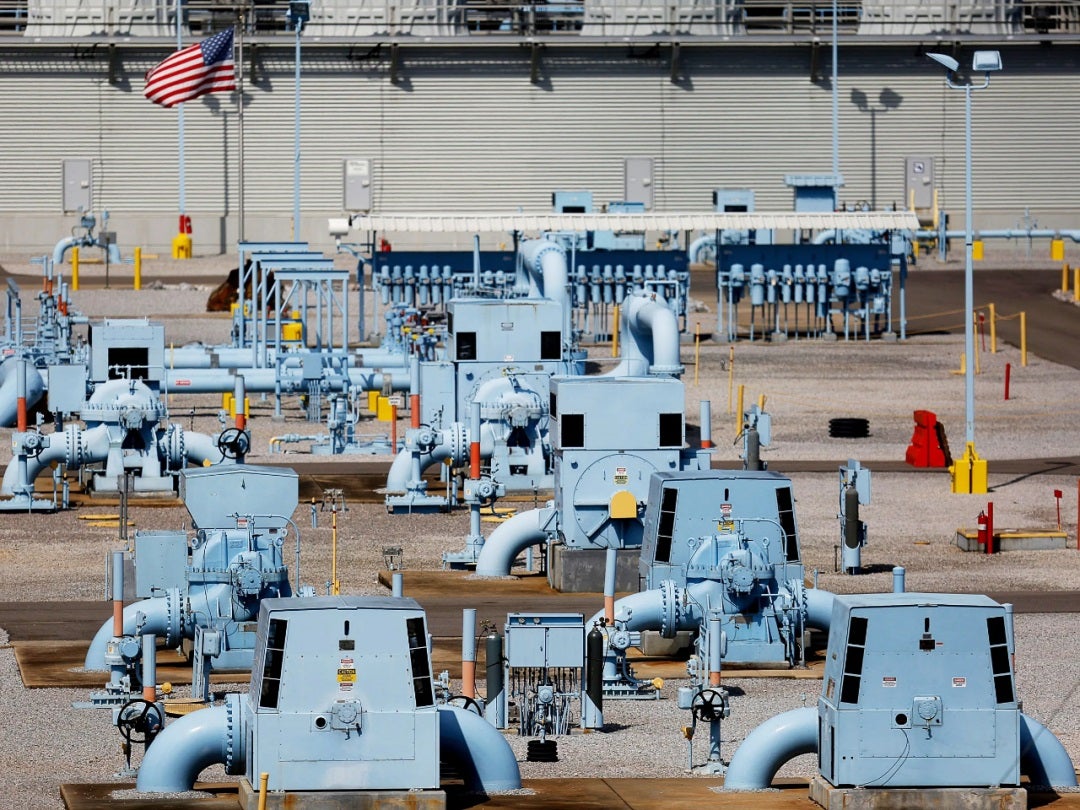
Image Source Wired: https://www.wired.com/story/colonial-pipeline-ransomware-attack/
What is Darkside Ransomware?
Sangfor reported on the DarkSide ransomware group as early as September 2020. The DarkSide group is one of the leading providers of ransomware as a service (RaaS). In recent years, the criminal activities of the ransomware group have grown rapidly, and the victims are often unwilling to take the risk of not paying the high ransom. This actually helped the DarkSide group to become a more professional and customer service-oriented organization. They even provide a help desk with a call-in phone number for victims. DarkSide’s website has a section called “DarkSide Leaks” where the hackers have posted the private data of over 40 victims that they have stolen from. And although the ransomware group is developing a professional demeanor, they still carry out “double extortion,” where the hackers infiltrate and install backdoors to systems, encrypt and lock up the victim’s data, and then steal the data and threaten to make it public if the ransom is not paid. Typical ransom demands range from $200,000 to $20 million.
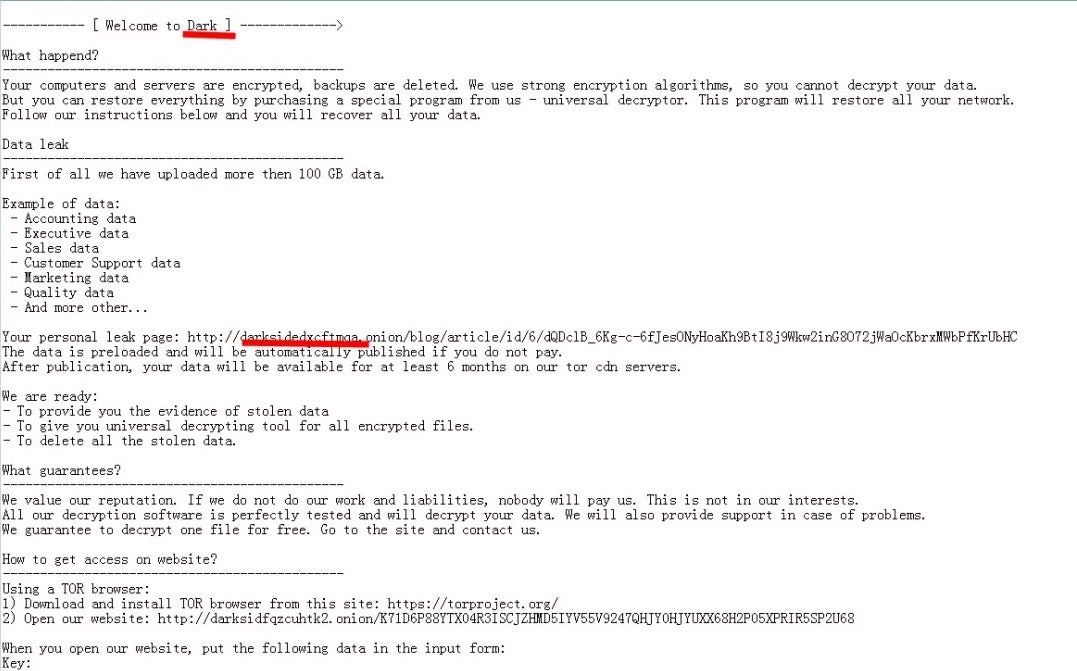
DarkSide Ransomware Information TXT
Different from "bulk" or scattershot ransomware attacks, the DarkSide ransomware group is very targeted. They perform reconnaissance and technical analysis of the target for several weeks or even months, and even conduct a financial analysis on the target; detailed intelligence gathered on their victims includes the size and scope of the company and key decision-makers. Darkside publicly claims to have an ethical code of conduct that states they prohibit attacks against non-profit organizations such as hospitals and schools, and even donate a portion of their gains to charities. Their target of choice are companies on the United States NASDAQ tech-based stock exchange.
DarkSide posted a statement of remorse on their website saying they are not political and only want to make money without greatly impacting society.
We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for our motives. Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.
Oil Pipeline Hack: Technical Analysis
The DarkSide ransomware is different from other ransomware in that its encrypted suffix is not fixed, but instead is usually 8-bit random characters, and the encrypted file types include the following suffixes:
386, adv, ani, bat, bin, cab, cmd, com, cpl, cur, deskthemepack, diagcab, diagcfg, diagpkg, dll, drv, exe, hlp, icl, icns, ico, ics, idx, ldf, lnk, mod, mpa, msc, msp, msstyles, msu, nls, nomedia, ocx, prf, ps1, rom, rtp, scr, shs, spl, sys, theme, themepack, wpx, lock, key, hta, msi, pdb
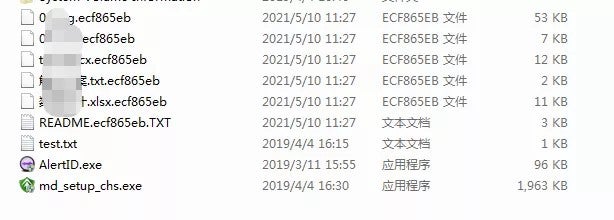
Encrypted file suffix
Oil Pipeline Attack Shines Light on Critical Infrastructure Needs
Colonial Pipeline was not the first infrastructure target this year. There have already been cyberattacks against infrastructure targets globally including power grids & nuclear power plants, water treatment facilities, telecommunications, and transportation. Critical infrastructure is related to a national economy and should be a top priority of network security. As economies and societies increasingly rely on the Internet, the security protection of critical infrastructure becomes more urgent. Yet, critical information infrastructure is already one of the primary targets of cyber-attacks.
In the face of so many infrastructure attacks, many using ransomware, more attention and priority is needed to improving infrastructure security worldwide. Yet, little is being done globally or even regionally to secure aging and obsolete infrastructure cybersecurity.
Sangfor Protects Infrastructure from Ransomware
Sangfor protects critical information infrastructure around the world, providing real-time comprehensive security monitoring and protection of critical information infrastructure.
Sangfor Solution for Ransomware based on both Sangfor’s award winning Endpoint Secure protection and award winning NGAF next-generation firewall, is proven to break every step of the ransomware attack chain, providing comprehensive prevention, protection, detection, and response.
Prevention:
Identify vulnerabilities in systems before an attack through security baseline inspection, vulnerability detection and repair, and blocking the entry point of ransomware attacks.
Protection:
Deploying protection against brute-force RDP & login attacks, fileless APT attacks, as well as technologies such as ransomware honeypots and network-wide one-click kill of malware.
Detection and response:
Real-time AI-based malware/APT detection, network-wide threat visualization, hybrid network/cloud integration allows the NGAF to work with Endpoint Secure to stop command & control (C&C) communications and enact micro-isolation of endpoints to stop the lateral spread of ransomware throughout the environment.
Sangfor VDI provides secure virtual desktop environments that facilitate secure ICS and infrastructure operations while preventing both APT/ransomware from attacking and sensitive data from being exfiltrated.
In addition, Sangfor's MSS security operation service suites provide users with preventative, monitoring, and incident response services for ransomware prevention and response.
Sangfor reminds users that the best protection against ransomware is prevention. Most files encrypted by ransomware cannot be decrypted so regular preventive measures should include:
- Upgrade/patch systems and applications to mitigate high-risk vulnerabilities.
- Perform regular remote offline multi-media backup of important data files.
- Do not click on email attachments from unknown sources, and do not download software from unknown websites.
- Remove unnecessary file sharing permissions across all systems.
- Change account passwords using strong passwords and avoid using the same password on multiple systems.
- Disable RDP and do not map RDP services to external network unless absolutely necessary.
- Use endpoint protection with proven ransomware defense and response capabilities such as ransomware honeypots to stop encryption processes
This week's oil pipeline attack and ransomware demand is just the latest in a long series of serious ransomware and malware attacks, and we can’t help but envision a world in the not-too-distant future where ransomware attacks affect all our daily lives more often. The ransomware industry is booming. Attacks are successful daily, and those companies who can’t pay the ransom for their encrypted data employ cyber-attack insurance agencies, ready to make the payment for their client. In short, it’s a great time to be a cyber-criminal. We predict many more ransomware attacks which bring countries and perhaps the world, to its knees.
Be prepared.
Sangfor Technologies is an APAC-based, global leading vendor of IT infrastructure solutions specializing in Network Security and Cloud Computing. Visit us at www.sangfor.com to learn more about Sangfor’s Security solutions and ransomware protection, and let Sangfor make your IT simpler, more secure and valuable.
Contact Us for Business Inquiry
FAQs on Colonial Gas Pipeline Hack
There has been so much movement on the Colonial Oil Pipeline attack on the East Coast of the USA, one off the biggest and most significant attacks in ransomware history. One of the most surprising moves lately is an apology from the DarkSide hackers, saying, “We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives,” the group said in broken English. “Our goal is to make money, and not creating problems for society.” What else has been going on, and what are the questions on the front of everyone’s mind.
How did the pipeline get hacked?
While Colonial is keeping silent on how the attack actually gained entry into the system, security experts say that most attacks of this type start with a phishing email to an employee. It could also potentially be a vulnerability in third party software or the network of a third party vendor. Hackers aren’t picky about how they get in – a successful attack is a successful attack, no matter how dirty their hands get.
Who hacked into Colonial Gas Pipeline?
US News and Reuters report that DarkSide is responsible for hacking the Colonial oil pipeline. DarkSide is a highly organized group of experienced cyber criminals with a mailing list, press centre, and even a victim hotline, suspected to be based in Russia. DarkSide website claims responsibility for an array of highly destructive attacks. Because the software they are using is new, they’ve obviously taken issue with being underestimated, with their website saying of the new software, "that does not mean that we have no experience and we came from nowhere."
Why was the oil pipeline shut down?
As Colonial runs a highly digitized system, all their modern pipelines are controlled by computer, and rarely directly managed by human beings. Because the pipeline was connected to Colonials internal network, the ransomware attack on Colonial’s network could have easily spread to the pipeline itself, necessitating the shutdown out of an overabundance of caution.
Was the gas pipeline hacked?
The attack began at 7PM on Friday night, on a pipeline that runs from New Jersey to Houston Texas. When Colonial discovered the intrusion, they shut down all systems which could be potentially affected, the major gas pipeline being one of them. While it was not hacked as far as the world knows, the attack on the network was enough to shut down the pipeline itself.
What states are affected by the pipeline cyber-attack?
State of Emergency Declarations are currently in place for Alabama, Arkansas, District of Columbia, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas, and Virginia. North Carolina has been hit particularly hard, with pumps empty or shut down, and police and first responders taking what’s left of the gas to maintain public safety.
How much is the ransom for Colonial Pipeline?
It is unknown how much DarkSide asked in ransom from Colonial Pipeline, although DarkSide typically asks for ransom between $200,000 and $2 million USD. In an interview with a former CIA hacker Dr. Eric Cole, CBS News learned that Colonial will likely pay the ransom requested. Cole said, “They have to decide, do we pay a million dollars or $40 million. And unfortunately, because that’s such a big range, most companies from a business standpoint, unfortunately, say it’s more economical to pay the ransom than to suffer the consequences,” he said.
What is ransomware?
Ransomware is a malicious software designed to encrypt data and block access to computer networks or systems, until a ransom is paid for the encryption key.
What is cyber-attack?
A cyber-attack is when an attacker attempts to gain access to a network, computer, or computing system, in an attempt to steal, cause damage, or hold data for ransom. Cyber-attacks are designed to destroy, disable, disrupt and control infiltrated enterprise computer systems, followed by damage or theft of any data within the systems. Sometimes data is held for ransom, sometimes destroyed, and often sold to the highest bidder on the dark web. Cyber-attacks are becoming an every-day occurrence inn 2021, with the Colonial Pipeline hack the biggest and most disruptive to date.





