Ransomware is a growing issue in the modern world. Ransomware attacks threaten businesses, individuals, and global corporations. Ransomware is constantly evolving and becoming harder to detect and mitigate. The latest of these ransomware threats goes by the name Akira Ransomware and has forced the Indian government to send out an official warning to the public.
Indian Government Cautions Against Akira Ransomware
The Indian Computer Emergency Response Team (CERT-In) recently issued an advisory reporting the emergence of the new internet ransomware virus. The Akira ransomware is said to primarily target systems running on Windows and Linux.
According to the advisory released by the government, the Akira ransomware steals personal data, encrypts it, and later extorts money from the victims. If users refuse to pay the ransom, their data is then leaked onto the dark web.
The advisory continued to say that the ransomware group is "known to access victim environments via VPN (virtual private network) services, particularly where users have not enabled multi-factor authentication."
What Is Akira Ransomware?
The Akira ransomware is a new ransomware family that emerged in March of this year. The ransomware is designed to encrypt data on infected computers and manipulate filenames by appending the ".akira" extension.
The ransomware group claims to have hit at least 63 organizations since its launch – mostly in the US. “Akira” is the name of a popular 1988 cyberpunk anime film and the group seems to have maintained the retro '80s theme for its data leak site as well.
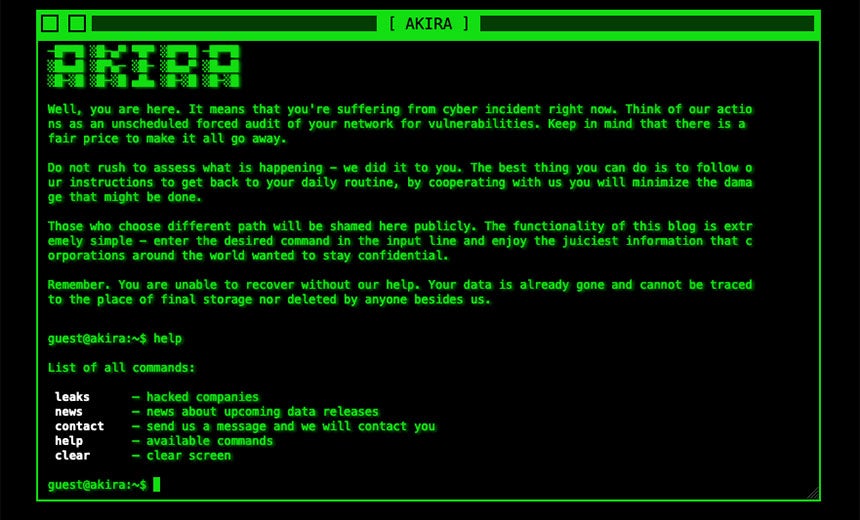
Akira data leak site. Sourced from Info Risk Today
Yelisey Bohuslavskiy shared in a post that the Akira ransomware features code that overlaps with the Ryuk ransomware. The security studies expert claims that whoever built Akira appears to have based the malware on the original version of the Ryuk crypto-locking malware code.
Akira also makes use of tools such as AnyDesk, WinRAR, and PCHunter during intrusions. These tools are usually already in the victim's environment and their misuse typically goes unnoticed.
The ransomware can enter networks through malware in email attachments, pirated software websites, peer-to-peer (P2P) networks, free file hosting sites, fake software updates, Trojans, or third-party downloaders.
How Does the Akira Ransomware Work?
The advisory released by CERT-In details how the Akira ransomware works. Upon execution, Akira deletes the Windows ‘Shadow Volume Copies' on the targeted device. The ransomware then encrypts files with a predefined set of extensions. The “.akira” extension is added to each encrypted file's name during this encryption process.
The advisory states that the ransomware terminates active Windows services using the Windows Restart Manager APL. This step prevents any interference with the encryption process.
The ransomware encrypts files found in various hard drive folders, excluding the ProgramData, Recycle Bin, Boot, System Volume Information, and Windows folders. To maintain system stability, it refrains from modifying Windows system files.
Every computer folder then contains a ransom note named “akira_readme.txt”. The note tells the user what happened to their files and links to the Akira data leak and negotiation site. The note threatens that the data stolen will be published or sold if an agreement – or price - isn’t reached.

Akira Ransomware Note. Sourced from Bleeping Computer
Each victim has a unique negotiation password that can be used to access the Akira site. Unlike other ransomware sites, the Akira site includes a chat feature that can be used to negotiate with the group.
How to Protect against Akira Ransomware?
With the growing threat of Akira ransomware, more companies, organizations, and governments are urging the public to take steps to prevent these attacks from happening. There are guidelines issued by Sangfor team as well on how to protect against ransomware.
The CERT-In advised internet users to use basic cyber hygiene practices and protection protocols to keep safe from ransomware attacks.
A few steps that the public can take to ensure their safety online include:
- Updating software regularly.
- Avoiding suspicious email links and websites.
- Ensuring that downloaded files are in the correct format and have the right extensions.
- Installing proactive antivirus protection and Endpoint Security.
- Backing up important files and data.
- Avoiding pop-up ads.
- Not paying any ransom amounts to the criminals.
- Maintaining the best cybersecurity measures available.
Sangfor Technologies is a world-class cybersecurity and cloud computing company that offers intensive and advanced Anti-Ransomware prevention and state-of-the-art IT infrastructure.
Protect your data and network from ransomware attacks using the Sangfor Next-Generation Firewall (NGFW) integrated with Endpoint Security to identify malicious files at both the network level and endpoints and so much more.
For more information on Sangfor’s cyber security and cloud computing solutions, please visit www.sangfor.com.





