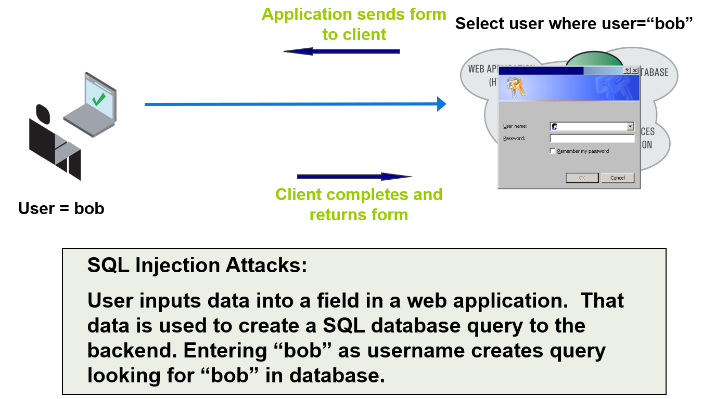
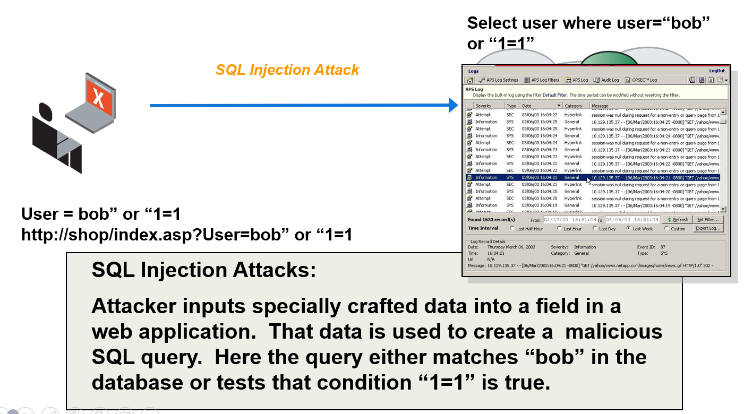
SQL is the most widely use database protocol in the world for accessing, changing, and storing data. It is essentially the method our computers use for when we are navigating a database. But its common use has made it easy prey for SQL injection attacks and other malicious activities.
There are many web security solutions out there, but not all are created equal. Let’s explore the basics of SQL injection attacks, how to defend against them, and how Sangfor NGAF with Next Generation WAF are your best and most powerful protection option in 2021.
What is an SQL Injection Attack?
Most web applications are connected to a database. You access a database when you search for something and order it online, or when you access online banking to pay bills. SQL is the query language used to easily manage, access, and modify that data. An SQL injection attack, also known as SQLi, is the process of inserting or “injecting” malicious strings into the data fields of a web application and those strings are turned into a malicious SQL query from the application to the databases. A successful attack will allow the attacker to read and steal sensitive data, modify, or delete the contents of entire databases, or execute administrative privileges. It will even allow the attacker to recover files and enter commands into the company operating system.
Methods of SQLi Attack
Because SQL queries are relied on for so many functions, they are the focus of many types of attacks. Attackers use it to perform several types of attacks, including:
- Discovering user credentials within a database and using these credentials to impersonate users and gain administrative access.
- Selecting and outputting data from a database server.
- Altering databases, and removing or adding data.
- Deleting records or information to databases and even database backups.
- Accessing user operating systems, and using this access to get into the internal network and work behind the network firewall.
Below is a simple example of how an attacker can use SQL injection attacks to circumnavigate application security and gain administrative privileges.
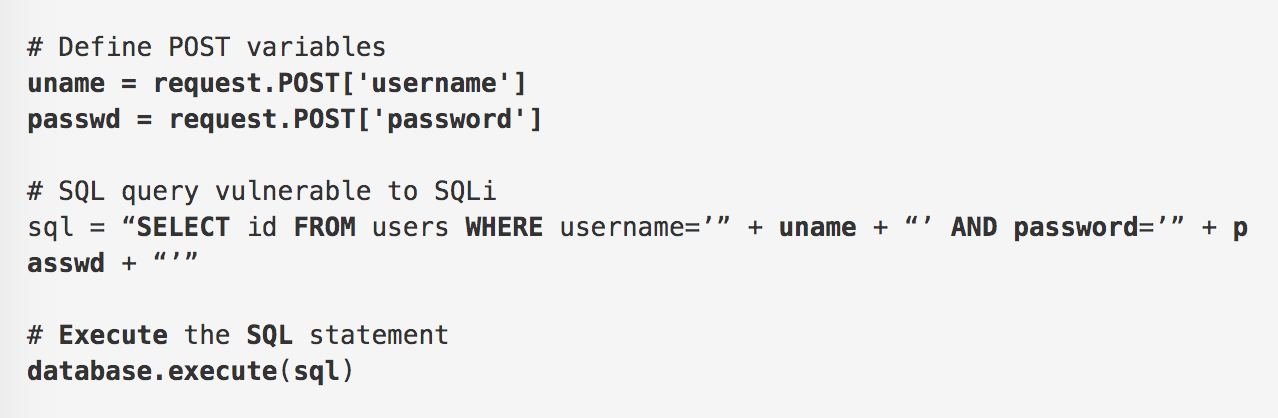
SQLi Threat Modelling
SQLi attack methods let attackers fake database requests to adjust or change data like balances, transactions, or to steal all information from a system. This type of attack also damages or destroys data, making it useless or unavailable. Worst of all, SQLi attacks do not require skilled attackers or hackers, as there are many free or paid SQLi tools available on the internet. But as you can see from above, attackers can write their own scripts with practice.
Defense Against SQL Injection Attacks
According to the OWASP SQL Injection Prevention Cheat Sheet, the best ways to defend against injection in SQL are as follows:
- Use of Prepared Statements allows the network security solutions to distinguish between code and data easily, regardless of user input.
- Use of Stored Procedures differs from prepared statements, in that the SQL code is stored within the database and validates data sent by applications.
- Allow-list Input Validation means input comes from code, not from user parameters, like dropdown lists. Parameter values should be carefully managed, to ensure invalid user input is rejected.
- Escaping All User Supplied Input should only be used when all else fails, and requires a great deal of work to implement. Use the OWASP ESAPI, an open source, web application security control library that helps developers create low-risk applications.
- Enforcing Least Privilege to limit the privileges of every user in your network, lessening the risk of attacks through SQL injection .
- Performing Allow-list Input Validation allows you to detect unauthorized input before it is inserted into the SQL query.
Enterprises are increasingly relying on web application firewalls, or WAFs, to block SQLi and other web-based cyber threats. It’s important to work with a WAF and firewall provider with access to a constantly updated list of threat signatures, and who also employs AI and machine learning to discover new attack vectors and stop them. When a WAF detects a potential attack, it first verifies the IP address before blocking. If the IP address shows up as potentially malicious, the connection is rejected. Cloud-based WAF uses a mass of other security capabilities, and can be incorporated with other, powerful SQLi attacks prevention capabilities.
Sangfor Next Generation WAF & NGAF
Sangfor, cooperating with Sangfor’s Next Generation Application Firewall (NGAF), were perfectly designed to protect users and enterprises from advanced web-based attacks like SQLi attacks, web shell, Struts2 injection and deserialization flaws. Sangfor's NGAF uses machine learning and AI to analyse attack patterns and behavior, enhancing detection rates and decreasing false positives. A threat model is created to easily manage application system threats.Sangfor’s Next Generation Application Firewall (NGAF), were perfectly designed to protect users and enterprises from advanced web-based attacks like SQLi attacks, web shell, Struts2 injection and deserialization flaws. Sangfor’s Cyber Command is an advance Network Detection and Response platform which also helps to identify any network vulnerabilities including SQL Injection Attacks. Sangfor's NGAF uses machine learning and AI to analyse attack patterns and behavior, enhancing detection rates and decreasing false positives. A threat model is created to easily manage application system threats.
Sangfor NGAF is a best-in-class hardware firewall, built to detect and prevent a variety of network attack types, including SQLi. NGAF monitors all traffic and access logs and uses traceability to provide better visibility and control for your IT security team. Sangfor’s NGAF deals effectively with vulnerability scanning, injection attack in SQL, website defacement, brute force attacks and even weak passwords, quickly identifying and interpreting high-risk user behavior.
WAF tools and Next Generation Firewall are relied upon to stop application-layer attacks, a long-time standard for many enterprises dealing with a complex threat landscape. Sangfor’s NGAF threat detection engine has integrated AI modules for deep analysis of threats. These AI models are self-teaching, self-developing and easily adaptable, providing the most effective defence, compared to traditional methods.
For more information on how Sangfor Cyber Command, WAF and NGAF can help defend against, injection attacSQL contact Sangfor today!