A sophisticated phishing campaign is currently targeting WooCommerce administrators, aiming to exploit their trust by distributing fake security patches that, once installed, compromise the integrity of WordPress sites. This article aims to help you understand the mechanics of this attack, signs of compromise, and steps to safeguard your online store.

Understanding the Fake Security Patch Campaign
The Phishing Attack Unveiled
The attack begins with phishing emails that mimic official WooCommerce communications. Sent from the spoofed address 'help@security-woocommerce.com,' these emails alert administrators to a fabricated "unauthenticated administrative access" vulnerability. The message urges recipients to download a "critical patch" to protect their online stores. The urgency and official-looking branding are designed to deceive administrators into taking immediate action without scrutiny.
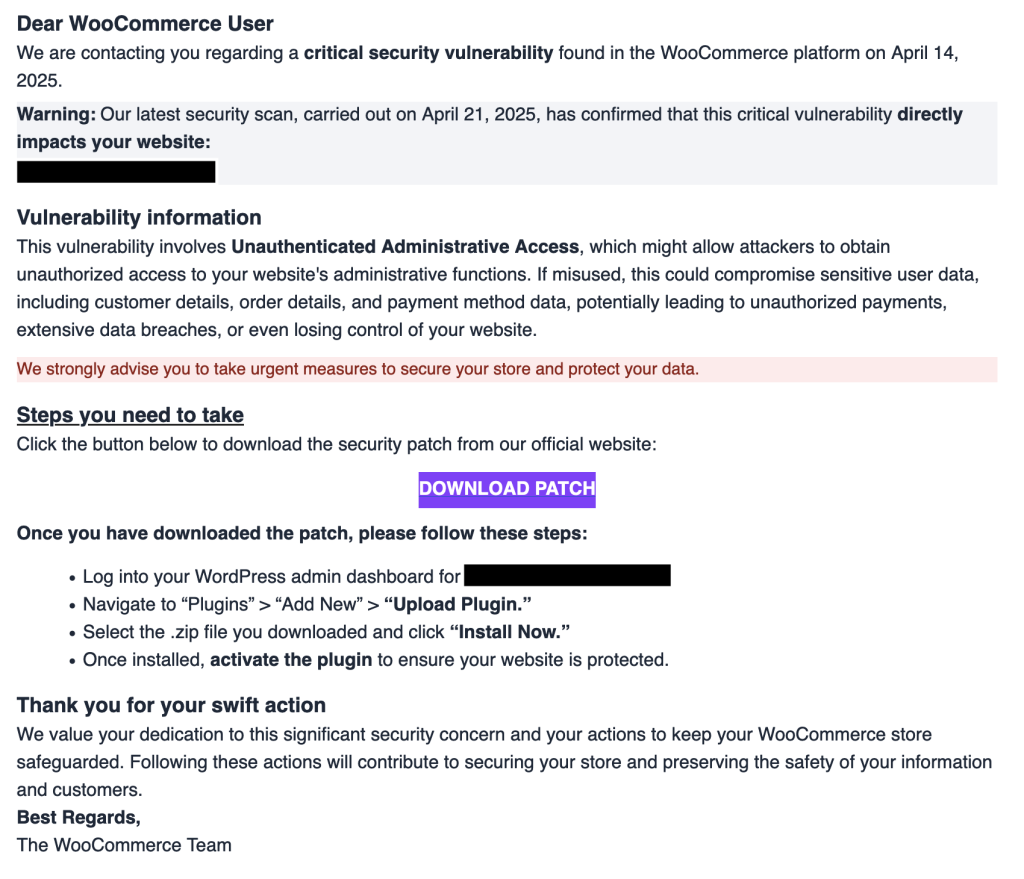
Source: Patchstack
Source: WooCommerce
The Malicious Payload
Upon downloading, administrators unknowingly install a malicious plugin named 'authbypass-update-31297-id.zip.' This plugin initiates a series of actions: it creates a cron job that runs every minute to generate a hidden admin-level user, connects to external domains to retrieve second-stage payloads, and deploys multiple PHP-based web shells under the 'wp-content/uploads/' directory. These web shells provide attackers with full control over the infected site.
Technical Analysis of the Hijack Mechanism of Phishing
Creation of Hidden Admin Accounts
The malicious plugin creates unauthorized admin accounts with random eight-character usernames. These accounts are concealed from legitimate administrators by removing them from the WordPress admin panel and hiding associated cron jobs. This stealth approach ensures persistent access for attackers.
Deployment of Web Shells
The installed web shells, such as P.A.S.-Form, p0wny, and WSO, allow attackers to execute arbitrary commands, inject malicious content, steal sensitive data, redirect visitors to malicious sites, and potentially enlist the server in DDoS botnets. The presence of these web shells significantly compromises site security and can lead to severe reputational and financial damage.
Indicators of Compromise (IoCs)
Identifying Suspicious Activities
Administrators should be vigilant for the following signs:
- Unknown admin accounts with random eight-character usernames.
- Unusual cron jobs running at high frequencies.
- Presence of a folder named 'authbypass-update' in the 'wp-content/uploads/' directory.
Monitoring Outbound Connections Monitor for outgoing requests to suspicious domains such as 'woocommerce-services.com,' 'woocommerce-api.com,' or 'woocommerce-help.com.' Unusual traffic to these domains may indicate ongoing malicious activities.
Mitigation and Prevention Strategies
Immediate Actions Post-Infection If a WooCommerce site is compromised:
- Immediately disable the malicious plugin and remove it from the system.
- Change all administrator passwords and enforce strong password policies, including the use of unique and complex passwords for each admin.
- Review and remove any unauthorized admin accounts that may have been created during the attack.
- Restore the site from a clean backup taken before the infection occurred. Ensure that the backup does not contain any of the malicious files.
- Conduct a thorough security audit to identify and rectify any other vulnerabilities that may be exploited in the future.
Long-Term Security Measures
To prevent future attacks, administrators should implement the following best practices:
- Regularly update WooCommerce and all associated plugins to their latest versions, ensuring that the site benefits from the most recent security patches.
- Enable auto-updates for security patches where possible, ensuring that vulnerabilities are fixed automatically without delays.
- Implement two-factor authentication (2FA) for all administrator accounts. This will provide an extra layer of protection even if login credentials are compromised.
- Only install plugins from trusted sources, such as the official WordPress plugin repository or reputable third-party developers with a track record of secure code.
- Regularly back up the site and store backups in secure, remote locations. Automated backups ensure that you can quickly recover from a security breach without significant downtime.
- Perform regular security audits and vulnerability assessments. This will help identify potential weaknesses before they are exploited by attackers.
Conclusion
The phishing campaign targeting WooCommerce administrators highlights the importance of proactive security practices. By understanding the tactics used by cybercriminals and implementing strong security measures, you can significantly reduce the risk of your online store being compromised. Ensuring that your WooCommerce site is properly secured requires vigilance, regular updates, and the adoption of best practices. Administrators should also remain informed about emerging threats to protect their sites from attacks like the fake security patch campaign discussed in this article. If you suspect your site has been compromised, acting quickly can minimize damage and restore security. Stay alert, stay secure, and always verify the authenticity of any security updates you receive.
Frequently Asked Questions
Fake security patches are malicious plugins or updates disguised as official WooCommerce security updates. These patches are distributed through phishing emails or malicious websites and, when installed, allow attackers to take control of your website by creating hidden admin accounts and deploying backdoors like web shells.
Signs that your site may have been compromised include:
- Unusual admin accounts with random, unfamiliar usernames.
- Increased server activity, such as cron jobs running frequently.
- Suspicious files or folders, such as "authbypass-update" in the 'wp-content/uploads/' directory.
- Unusual outbound connections to suspicious domains.
If you suspect that your site has been compromised, take the following steps:
- Disable and remove the malicious plugin.
- Change all admin passwords and enforce strong password policies.
- Check for any unauthorized admin accounts and remove them.
- Restore your site from a clean backup.
- Perform a full security audit to identify any other vulnerabilities.
Yes, fake security patches can have severe consequences. Once installed, they can steal sensitive customer data, redirect visitors to malicious sites, inject malware, or even enroll your server in a DDoS botnet. These activities can lead to reputational damage, loss of revenue, and potential legal issues if customer data is compromised.
To prevent such attacks, follow these best practices:
- Always verify the authenticity of any security update or plugin before installing it.
- Install plugins only from trusted sources, such as the official WordPress repository.
- Keep all plugins and WordPress core up-to-date with the latest security patches.
- Enable two-factor authentication for admin accounts.
- Regularly back up your site and conduct security audits.
Yes, there are various security tools available, such as:
- Wordfence Security, which offers real-time threat defense and malware scanning.
- Sucuri Security, which provides malware removal, security hardening, and monitoring.
- iThemes Security, which helps protect against brute force attacks, file changes, and malware.
Yes, you can enable automatic updates for WooCommerce and WordPress core in your site’s settings. However, it's also crucial to monitor updates and verify their authenticity to avoid installing any malicious updates unintentionally.





