1. Summary
| Vulnerability Name | Apache HTTP Server Path Traversal Vulnerability (CVE-2021-42013) |
|---|---|
| Release Date | October 8, 2021 |
| Component Name | Apache HTTP Server |
| Affected Versions | Apache HTTP Server 2.4.49 Apache HTTP Server 2.4.50 |
| Vulnerability Type | Path Traversal |
| Severity | CVSS v3 Base Score 9.8 (Critical) |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: None User Interaction: None |
| Impact | Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2021-42013
2.1 Introduction
Apache HTTP Server is an open-source web server, developed by the Apache Foundation. Because of its cross-platform functions and security, it has become one of the most popular web servers in use today. It is fast, reliable and can be extended through a simple API to compile Perl/Python, and other interpreters into the server.
2.2 Summary
On October 8, 2021, Sangfor FarSight Labs received a notice about the Apache HTTP Server path traversal vulnerability (CVE-2021-42013), classified as critical with a CVSS Score of 9.8.
It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. If files outside of these directories are not protected by the usual default configuration "require all denied", these requests can succeed. If CGI scripts are also enabled for these aliased paths, this could allow for remote code execution.
CVE-2021-42013 was added to CISA’s Known Exploited Vulnerabilities Catalog on November 3, 2021.
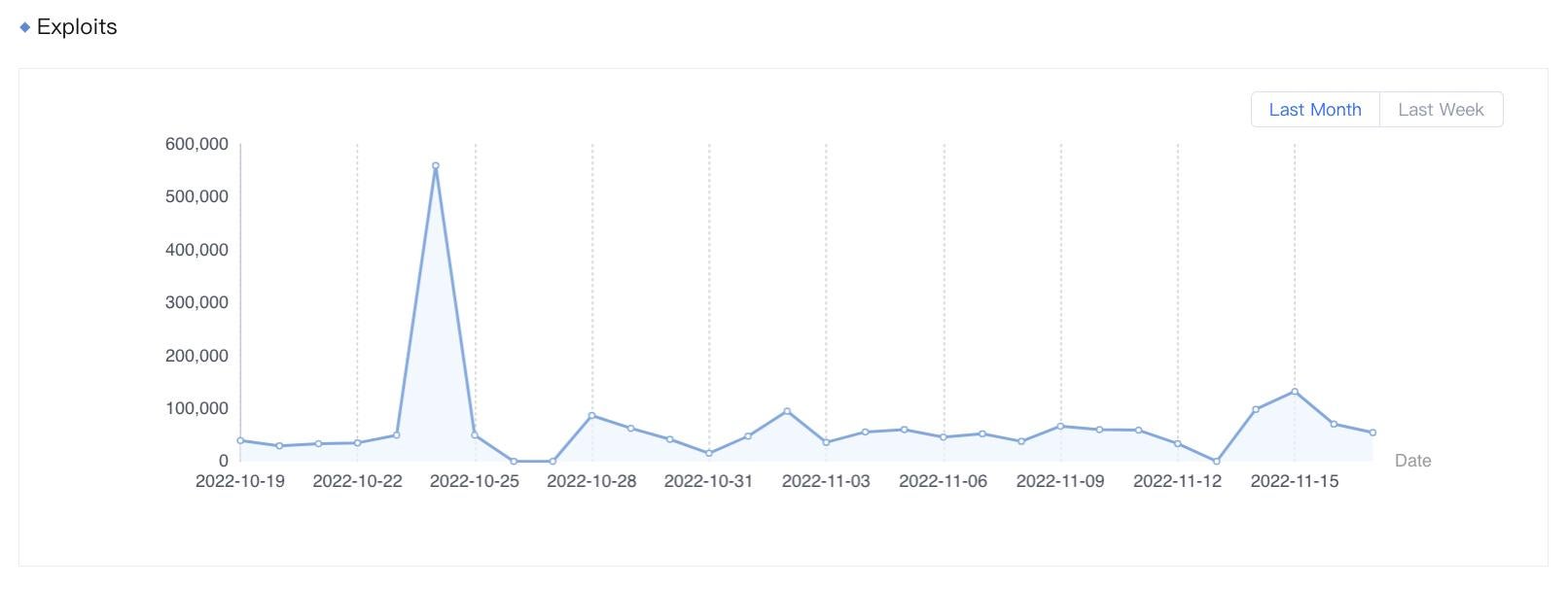
Figure 1. Exploits of CVE-2021-42013 detected by Sangfor from October 19 to November 17, 2022.
For the most up-to-day exploit statistics, please visit the following page (registration required).
3. Affected Versions
Apache HTTP Server 2.4.49
Apache HTTP Server 2.4.50
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
Enter command httpd -v in the server backend to view the current version.
4.1.2 Solution from Apache
Apache has released a new version to fix the vulnerability. Affected users can download from the following link: https://httpd.apache.org/download.cgi
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Apache HTTP Server path traversal vulnerability (CVE-2021-42013):
- Sangfor Cyber Guardian (Managed Detection and Response)
- Sangfor Cyber Command (Network Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Apache HTTP Server path traversal vulnerability (CVE-2021-42013):
5. Timeline
On October 8, 2021, Sangfor FarSight Labs received a notice about the Apache HTTP Server path traversal vulnerability (CVE-2021-42013).
On October 8, 2021, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://httpd.apache.org/security/vulnerabilities_24.html
https://nvd.nist.gov/vuln/detail/CVE-2021-42013
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





