1. Summary
| Vulnerability Name | Apache Log4j2 DoS Vulnerability (CVE-2021-45105) |
|---|---|
| Component Name | Apache Log4j2 |
| Affected Versions | 2.0-alpha1 ≤ Apache Log4j2 ≤ 2.16.0 (excluding 2.12.3 and 2.3.1) |
| Vulnerability Type | Denial-of-Service |
| Severity | CVSS v3 Base Score 5.9 (Medium) |
| Exploitability | Attack Vector: Network Attack Complexity: High Privileges Required: None User Interaction: None |
| Impact | Confidentiality Impact: None Integrity Impact: None Availability Impact: High |
2. About CVE-2021-45105
2.1 Introduction
Apache Log4j2 is a Java logging framework and an upgraded version of Log4j. It can control the output format of each log. By defining each logging level, the log generation process can be controlled in more detail. Because of its ease of use, it is widely integrated into various servers and components.
2.2 Summary
This vulnerability is caused when Apache Log4j2 uses a non-default Pattern Layout with either a Context Lookup (for example, $${ctx:loginId}) or a Thread Context Map pattern (%X, %mdc, or %MDC). Attackers can exploit this vulnerability by constructing malicious data that includes a lookup variable that will cause an infinite recursive lookup leading to Stack-Overflow in Context Lookups causing a denial-of-service attack without authorization.
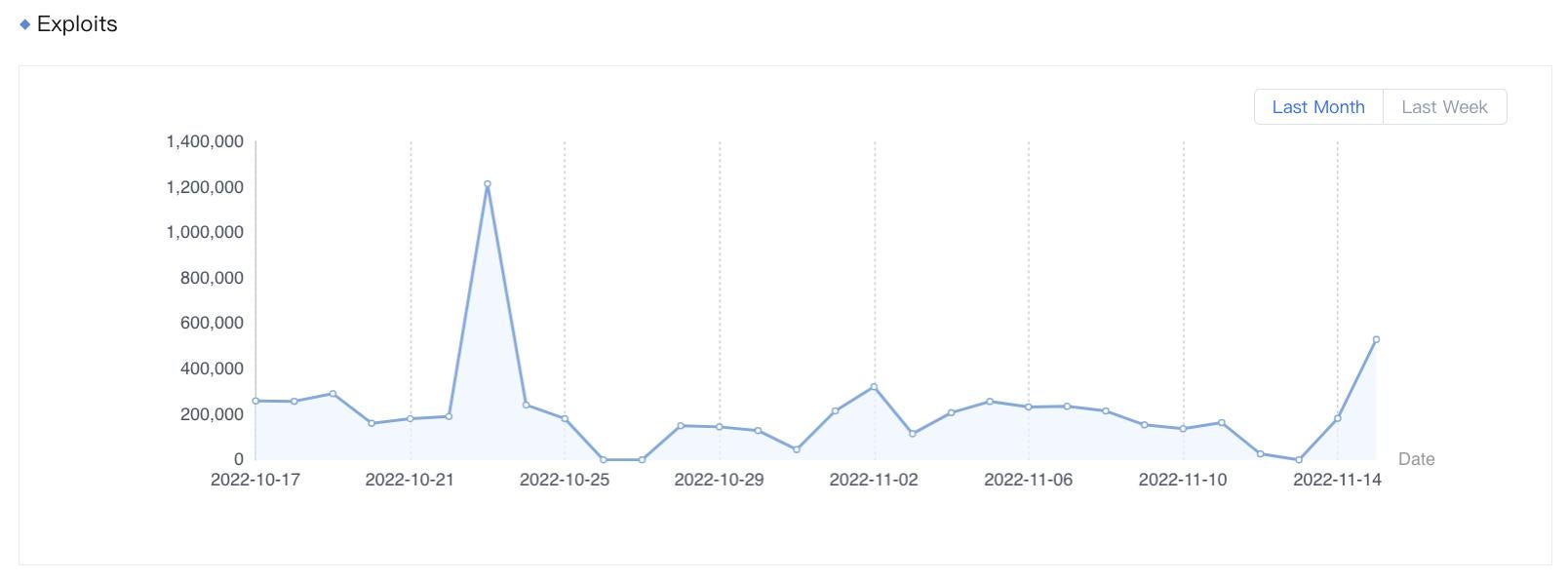
Figure 1. Exploits of CVE-2021-45105 detected by Sangfor from October 16 to November 15, 2022
3. Affected Versions
2.0-alpha1 ≤ Apache Log4j2 ≤ 2.16.0
(excluding 2.12.3 and 2.3.1)
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
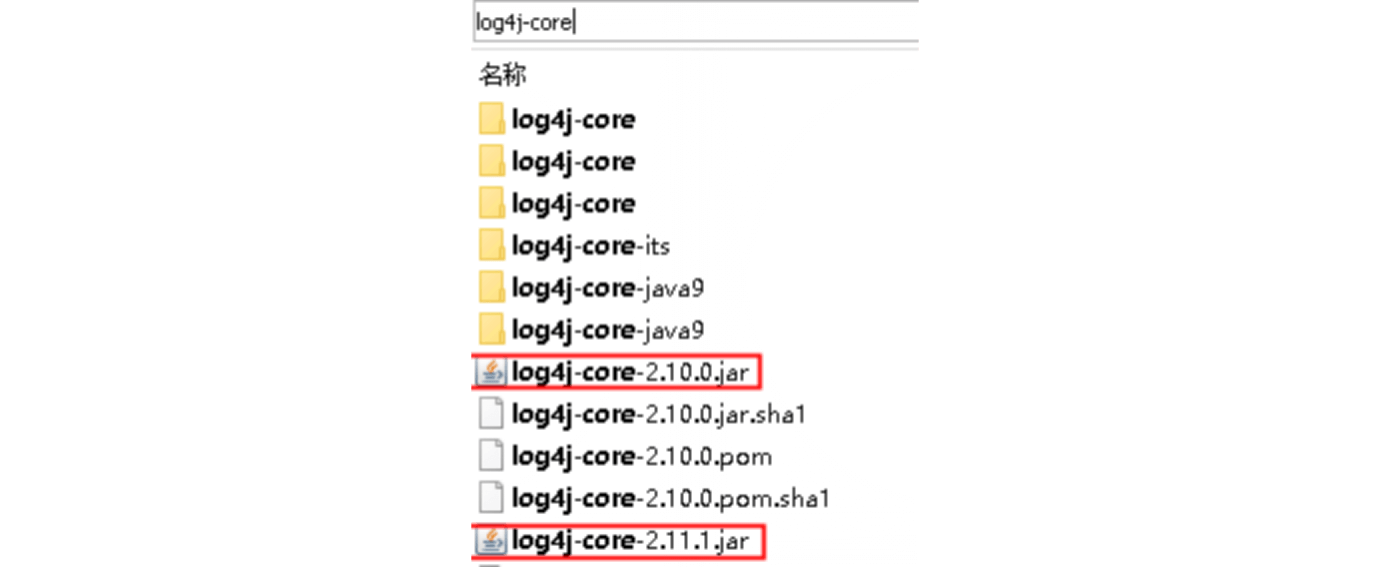
Option 1
Do a global search for log4j-core. If log4j-core-{version}.jar exists, and the version is within the affected range, then users may be affected by this vulnerability.
Option 2
If the project is compiled using Maven, there will be pom.xml file in the root directory of the project.
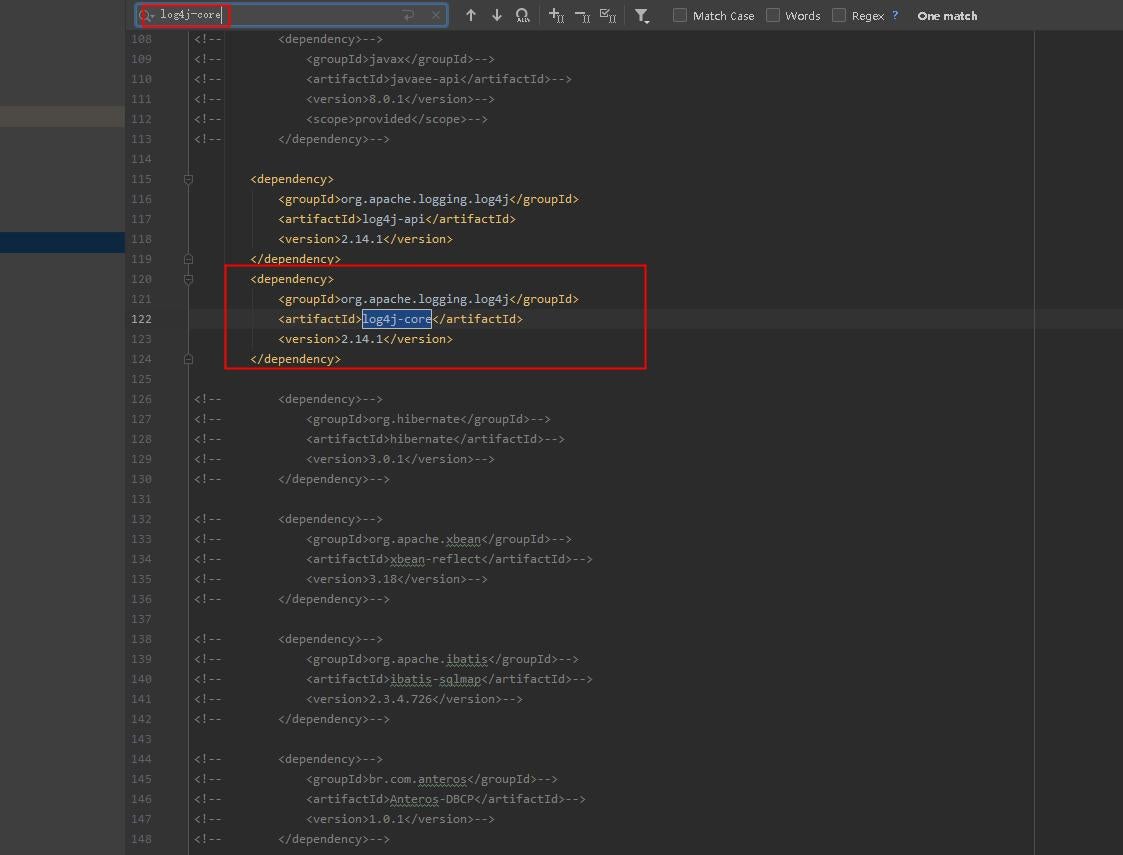
Open the pom.xml file, as shown below:

Search for log4j-core in this file. If it is found, and the string inside the <version> tag is within the affected range, then users may be affected by this vulnerability. The version of log4j-core in the figure is 2.14.1, which may be affected by this vulnerability.
If no results are found in the above search, it does not mean that there are no Log4j components. If the server uses the middleware listed below, log4j components are nested inside the middleware. Sangfor advises the user to contact the developer or vendor of the business system to determine whether log4j components are used.
The middleware that are affected by the vulnerability includes but is not limited to:
- Apache Struts2
- Apache Solr
- Apache Flink
- Apache Druid
- ElasticSearch
- Dubbo
- Apereo CAS
4.1.2 Apache Solution
Apache has released an updated version that fixes the vulnerability. Affected users can download it from the following link: https://github.com/apache/logging-log4j2/tags
Note: Java 8 users need to upgrade to Apache Log4j version 2.17.0.
4.1.3 Workaround
This temporary solution does not fix the issue completely. Users can decide whether to adopt this solution based on their business needs.
Users need to check whether Apache Log4j is configured using a non-default Pattern Layout with Context Lookup (for example: ${ctx:loginId} or $${ctx:loginId}). If a similar configuration exists, you need to delete the configuration or replace it with Thread Context Map mode (e.g.: %X, %mdc or %MDC).
Note: Currently only log4j-core JAR files are affected by this vulnerability. Applications that use log4j-api JAR files instead of log4j-core JAR files are not affected by this vulnerability.
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Apache Log4j DoS vulnerability (CVE-2021-45105):
- Sangfor Cyber Guardian (Managed Detection and Response)
- Sangfor Cyber Command (Network Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Apache Log4j DoS Vulnerability (CVE-2021-45105):
5. Reference
https://nvd.nist.gov/vuln/detail/cve-2021-45105
https://github.com/apache/logging-log4j2/tags
6. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





