1. Summary
| Vulnerability Name | F5 BIG-IP iControl REST Authentication Bypass Vulnerability (CVE-2022-1388) |
|---|---|
| Release Date | May 6, 2022 |
| Component Name | F5 BIG-IP |
| Affected Versions | 11.6.1 ≤ F5 BIG-IP ≤ 11.6.5 12.1.0 ≤ F5 BIG-IP ≤ 12.1.6 13.1.0 ≤ F5 BIG-IP < 13.1.5 14.1.0 ≤ F5 BIG-IP < 14.1.4.6 15.1.0 ≤ F5 BIG-IP < 15.1.5.1 16.1.0 ≤ F5 BIG-IP < 16.1.2.2 |
| Vulnerability Type | Authentication Bypass |
| Severity | CVSS v3 Base Score 9.8 (Critical) |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: None User Interaction: None |
| Impact | Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-1388
2.1 Introduction
F5 BIG-IP is a family of software and hardware products that provide application availability, access control, and security solutions.
2.2 Summary
On May 6, 2022, Sangfor FarSight Labs received a notice about a F5 BIG-IP iControl REST Authentication Bypass Vulnerability (CVE-2022-1388), classified as critical with a CVSS score of 9.8.
Undisclosed requests may bypass iControl REST authentication, which could allow a threat actor with network access to the BIG-IP system management port and/or self IP addresses to execute arbitrary system commands, create or delete files, and disable services on BIG-IP.
CVE-2022-1388 was added to CISA’s Known Exploited Vulnerabilities Catalog on May 10, 2022.
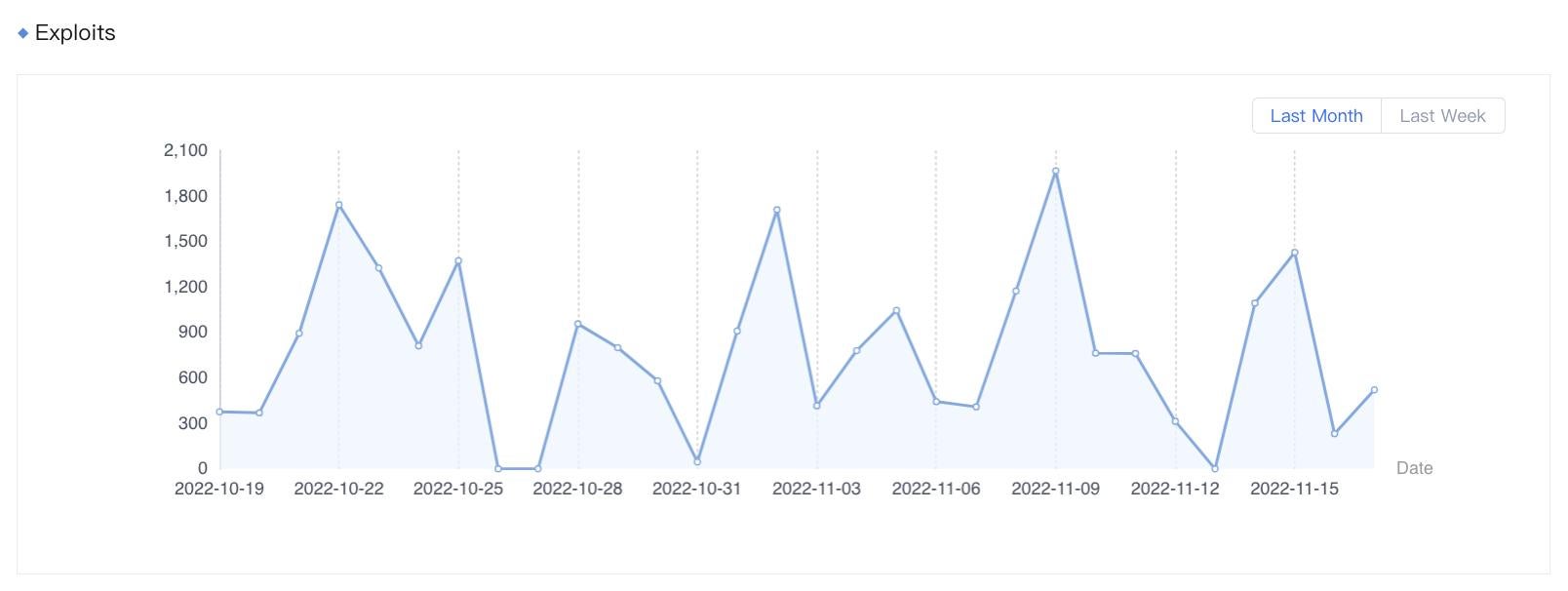
Figure 1. Exploits of CVE-2022-1388 detected by Sangfor from October 19 to November 17, 2022
3. Affected Versions
11.6.1 ≤ F5 BIG-IP ≤ 11.6.5
12.1.0 ≤ F5 BIG-IP ≤ 12.1.6
13.1.0 ≤ F5 BIG-IP < 13.1.5
14.1.0 ≤ F5 BIG-IP < 14.1.4.6
15.1.0 ≤ F5 BIG-IP < 15.1.5.1
16.1.0 ≤ F5 BIG-IP < 16.1.2.2
4. Solutions
4.1 Remediation Solution
4.1.1 F5 Solution
Affected users can update to the latest version to fix the vulnerability. Link: https://downloads.f5.com
4.1.2 Workarounds
These temporary mitigations restrict access to iControl REST to only trusted networks or devices, thereby limiting the attack surface, but do not completely fix the issue. Users can decide whether to adopt the solutions based on their business needs.
- Block iControl REST access through the self IP address
- Block iControl REST access through the management interface
- Modify the BIG-IP httpd configuration
For details, please refer to the official documentation: https://support.f5.com/csp/article/K23605346
4.2 Sangfor Solutions
4.2.1. Active Detection
The following Sangfor products and services actively detect assets affected by the F5 BIG-IP iControl REST authentication bypass vulnerability (CVE-2022-1388):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
4.2.2. Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the F5 BIG-IP iControl REST authentication bypass vulnerability (CVE-2022-1388):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
4.2.3. Security Protection
The following Sangfor products and services provide protection against the F5 BIG-IP iControl REST authentication bypass vulnerability (CVE-2022-1388):
5. Timeline
On May 6, 2022, Sangfor FarSight Labs received a notice about the F5 BIG-IP iControl REST authentication bypass vulnerability information.
On May 6, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://support.f5.com/csp/article/K23605346
https://nvd.nist.gov/vuln/detail/CVE-2022-1388
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





