1. Summary of CVE-2022-30190
| Vulnerability Name | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability (CVE-2022-30190) |
|---|---|
| Release Time | May 31, 2022 |
| Component Name | Microsoft Support Diagnostic Tool (MSDT) |
| Affected Versions | See Section 3 |
| Vulnerability Type | Remote Code Execution (RCE) Vulnerability |
| Severity | CVSS v3 Base Score: 7.8 (High) |
| Exploitability | Attack Vector: Local Attack Complexity: Low Privileges Required: None User Interaction: Required |
| Impact | Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-30190 (Follina)
On May 30, 2022, Sangfor FarSight Labs received a notice about a remote code execution vulnerability (CVE-2022-30190) in the Microsoft Support Diagnostic Tool (MSDT). The zero-day vulnerability has been dubbed Follina and is classified as a high-severity vulnerability with a CVSS v3 score of 7.8.
Microsoft Support Diagnostic Tool (MSDT) is a service in Microsoft Windows and Windows Server. MSDT collects information to send to Microsoft Support. Microsoft Support will then analyze this information and use it to determine the resolution to any problems that you may be experiencing on your computer.
The vulnerability was first observed by the cyber security research team "nao sec". A Twitter post on My 27, 2022, notes that a malicious Word document submitted from Belarus used Word's external link to load the HTML and then uses the "ms-msdt" scheme to execute PowerShell commands.
The remote code execution (RCE) vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. A threat actor who successfully exploits the Follina vulnerability can execute code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the rights of users.
CVE-2022-30190 was added to CISA’s Known Exploited Vulnerabilities Catalog on June 14, 2022.
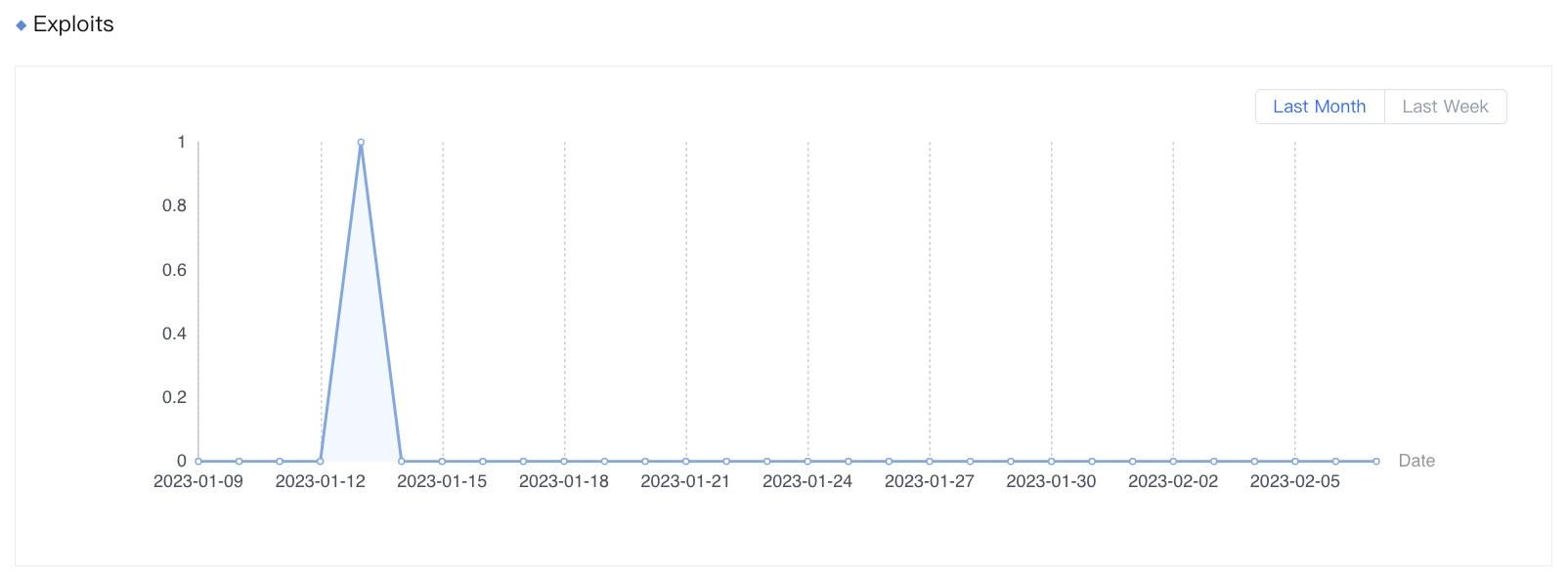
Figure 1. Exploits of the Follina flaw detected by Sangfor from January 9 to February 7, 2023.
For the most up-to-day statistics, please visit the following page (registration required).
3. Windows Versions Affected by CVE-2022-30190
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for 32-bit/x64-based Systems Service Pack 2
Windows RT 8.1
Windows 8.1 for 32-bit/x64-based Systems
Windows 7 for 32-bit/x64-based Systems Service Pack 1
Windows Server 2016
Windows 10 Version 1607 for 32-bit/x64-based Systems
Windows 10 for 32-bit/x64-based Systems
Windows 10 Version 21H2 for 32-bit/ARM64-based/x64-based Systems
Windows 11 for x64-based/ARM64-based Systems
Windows 10 Version 20H2 for x64-based/32-bit/ARM64-based Systems
Windows Server 2022 Azure Edition Core Hotpatch
Windows Server 2022
Windows 10 Version 21H1 for x64-based/ARM64-based/32-bit Systems
Windows Server 2019
Windows 10 Version 1809 for 32-bit/x64-based/ARM64-based Systems
4. Solutions for CVE-2022-30190
4.1 Microsoft Solution
4.1.1
On Tuesday June 14, 2022, Microsoft issued Windows updates to address this vulnerability. Affected users can install the security updates using Windows Update.
4.1.2 Workarounds
To disable the MSDT URL Protocol
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command "reg export HKEY_CLASSES_ROOT\ms-msdt filename"
- Execute the command "reg delete HKEY_CLASSES_ROOT\ms-msdt /f".
To undo the workaround
- Run Command Prompt as Administrator.
- To restore the registry key, execute the command "reg import filename"
Users can view the details at https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Windows MSDT remote code execution vulnerability (CVE-2022-30190):
- Sangfor Cyber Guardian (Managed Detection and Response Service)
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Endpoint Secure (Endpoint Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Windows MSDT remote code execution vulnerability (CVE-2022-30190):
- Sangfor NGAF (Next Generation Firewall)
- Sangfor Cyber Guardian (Managed Detection and Response Service)
- Sangfor Endpoint Secure (Endpoint Detection and Response)
5. Timeline
On May 30, 2022, Sangfor FarSight Labs received a notice about the Microsoft Windows MSDT remote code execution vulnerability (CVE-2022-30190).
On May 31, 2021, Sangfor FarSight Labs released a vulnerability alert.
6. References
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190
https://nvd.nist.gov/vuln/detail/cve-2022-30190
7. About Sangfor FarSight Labs
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





