1. Summary
| Vulnerability Name | Microsoft Exchange Server Server-Side Request Forgery Vulnerability (CVE-2022-41040) |
|---|---|
| Release Date | September 30, 2022 |
| Component Name | Microsoft Exchange Server |
| Affected Versions | Microsoft Exchange Server 2013 Cumulative Update 23 Microsoft Exchange Server 2016 Cumulative Update 22 Microsoft Exchange Server 2016 Cumulative Update 23 Microsoft Exchange Server 2019 Cumulative Update 11 Microsoft Exchange Server 2019 Cumulative Update 12 |
| Vulnerability Type | Elevation of Privilege Vulnerability |
| Severity | CVSS v3 Base Score 8.8 (High) |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: Low User Interaction: None |
| Impact | Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-41040
2.1 Introduction
Microsoft Exchange Server is a mail server and calendaring server developed by Microsoft. It runs exclusively on Windows Server operating systems.
2.2 Summary
On September 30, 2022, Sangfor FarSight Labs received a notice about a zero-day server-side request forgery (SSRF) vulnerability in Microsoft Exchange Server (CVE-2022-41040), classified as high severity with a CVSS Score of 8.8.
This vulnerability allows an authenticated attacker with standard user access to remotely trigger a second Exchange Server vulnerability, CVE-2022–41082, which in turn allows the attacker to run PowerShell on the server for remote code execution. The two vulnerabilities have been named ProxyNotShell vulnerabilities after the ProxyShell vulnerabilities affecting Exchange Server.
CVE-2022-41040 was added to CISA’s Known Exploited Vulnerabilities Catalog on September 30, 2022.
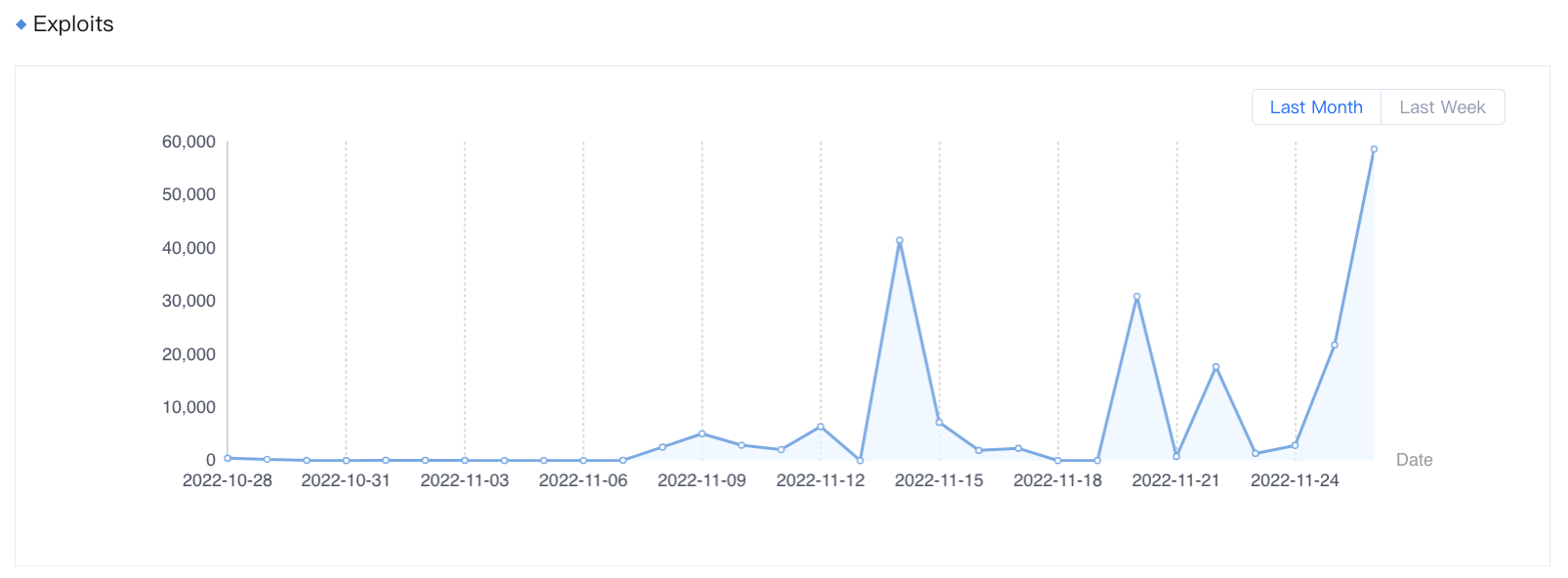
Figure 1. Exploits of CVE-2022-41040 detected by Sangfor from October 28 to November 26, 2022
For the most up-to-day exploit statistics, please visit the following page (registration required).
3. Affected Versions
Microsoft Exchange Server 2013 Cumulative Update 23
Microsoft Exchange Server 2016 Cumulative Update 22
Microsoft Exchange Server 2016 Cumulative Update 23
Microsoft Exchange Server 2019 Cumulative Update 11
Microsoft Exchange Server 2019 Cumulative Update 12
4.Solutions
4.1 Remediation Solutions
4.1.1 Microsoft Solution
Microsoft has released a patch for affected OS versions to fix this vulnerability on November 8, 2022. Please download the patch corresponding to the affected OS from the following link: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41040
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Microsoft Exchange server server-side request forgery vulnerability (CVE-2022-41040):
- Sangfor Cyber Guardian (Managed Detection and Response)
- Sangfor Cyber Command (Network Detection and Response)
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Microsoft Exchange server server-side request forgery vulnerability (CVE-2022-41040):
5. Timeline
On September 30, 2022, Sangfor FarSight Labs received a notice about the Microsoft Exchange server server-side request forgery vulnerability (CVE-2022-41040).
On September 30, 2022, Sangfor FarSight Labs released a vulnerability alert.
On November 15, 2022, Sangfor FarSight Labs updated the vulnerability alert with remediation solutions.
6. Reference
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41040
https://nvd.nist.gov/vuln/detail/CVE-2022-41040
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





