About the Vulnerability
Introduction
Apache Tomcat software is an open-source implementation of the Jakarta Servlet, Jakarta Server Pages, Jakarta Expression Language, Jakarta WebSocket, Jakarta Annotations, and Jakarta Authentication specifications. These specifications are part of the Jakarta EE platform.
Summary
On August 22, 2024, Sangfor FarSight Labs received notification that an Apache-Tomcat component contains information of data exposure vulnerability(CVE-2024-21733), classified as medium in threat level.
There exists a security vulnerability in Apache Tomcat stemming from improper exception handling in the Coyote connector component when processing POST requests. Attackers could trigger an erroneous response by sending incomplete POST requests, which may lead to the potential retrieval of previously requested data from other users.
Affected Versions
8.5.7 ≤ Apache Tomcat < 8.5.63
9.0.0-M11 ≤ Apache Tomcat < 9.0.43
Solutions
Remediation Solutions
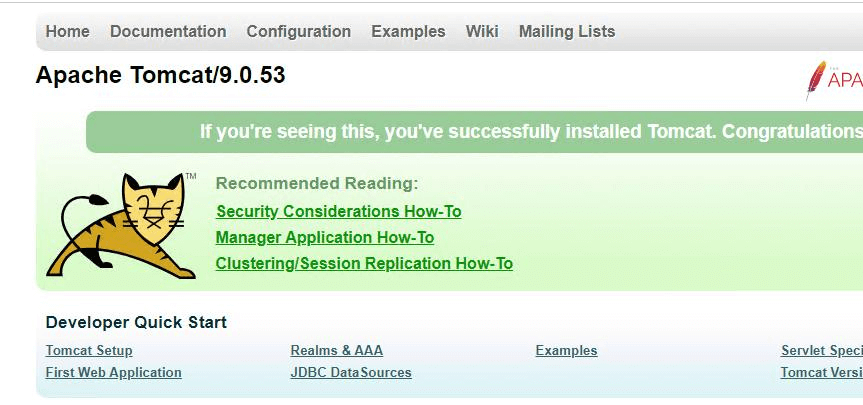
Check the System Version
The current service version information is usually displayed on Tomcat web pages.
Official Solution
Affected users are strongly advised to update the version of Tomcat.
Download link: https://tomcat.apache.org/
Sangfor Solutions
Risky Assets Detection
Support is provided for proactive detection of Apache-Tomcat; and it is capable of batch identifying the affected asset conditions of this event in business scenarios. Related products are as follows:
[Sangfor CWPP] has released an asset detection scheme, with Fingerprint ID: 0006642.
[Sangfor Host Security] has also released an asset detection scheme, with Fingerprint ID: 0006642.
Vulnerability Proactive Detection
Support is provided for proactive detection of the Apache Tomcat sensitive data exposure vulnerability (CVE-2024-21733); and it is capable of quickly batch identifying whether there are vulnerability risks in business scenarios. Related products are as follows:
[Sangfor Host Security] has released a detection scheme, with Rule ID: SF-0005-19939.
[Sangfor Cyber Guardian MDR/Nova MDR] has released a detection scheme, with Rule ID: SF-0005-17109.
[Sangfor Omni-Command/Nova XDR] has released a detection scheme (requiring Host Security component capabilities), with Rule ID: SF-0005-19939.
Vulnerability Security Detection
Support is provided for monitoring the Apache OFBiz code execution vulnerability (CVE-2024-21733); and it is capable of monitoring the affected asset conditions in business scenarios in real-time based on traffic collection, and quickly checking the scope of impact. Related products and services are as follows:
[Sangfor Cyber Command/NovaCommand] has released a monitoring scheme, with Rule ID: 11028865.
[Sangfor Cyber Guardian MDR/Nova MDR] has released a monitoring scheme (requiring Cyber Command/NovaCommand component capabilities), with Rule ID: 11028865.
[Sangfor Omni-Command/Nova XDR] has released a monitoring scheme, with Rule ID: 11028865.
Safety Protection
Support is provided for defense against the Apache Tomcat sensitive data exposure vulnerability (CVE-2024-21733); and it is capable of blocking attackers' intrusion targeting this event. Related products and services are as follows:
[Sangfor Network Secure] has released a protection scheme, with Rule ID: 11028865.
[Sangfor WAF] has released a protection scheme, with Rule ID: 11028865.
[Sangfor Cyber Guardian/Nova MDR] has released a protection scheme (requiring AF component capabilities), with Rule ID: 11028865.
[Sangfor Omni-Command/Nova XDR] has released a protection scheme (requiring AF component capabilities), with Rule ID: 11028865.
Timeline
On August 13, 2024, Sangfor FarSight Labs received notification of the Apache Tomcat sensitive data exposure vulnerability.
On August 22, 2024, Sangfor FarSight Labs released a vulnerability alert.
References
http://www.openwall.com/lists/oss-security/2024/01/19/2
https://lists.apache.org/thread/h9bjqdd0odj6lhs2o96qgowcc6hb0cfz
https://security.netapp.com/advisory/ntap-20240216-0005/





