About the Vulnerability
Introduction
Apache Kafka UI is a graphical user interface that allows users to visualize and manage topics, producers, consumers, and other resources in an Apache Kafka cluster.
Summary
On June 25, 2024, Sangfor FarSight Labs received notification of the remote code execution vulnerability (CVE-2024-32030) in Apache Kafka UI, classified as high (CVSS Score 8.1) by NVD.
This vulnerability is caused by the JMX ports connected via the RMI protocol. Attackers can exploit this vulnerability for deserialization and execute arbitrary code, causing server compromise.
Affected Versions
Apache Kafka UI ≤ 0.7.1
Solutions
Remediation Solutions
Check the Component Version
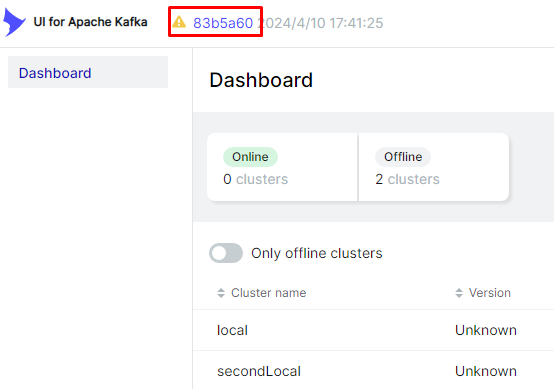
View the version number in the top-left corner of the homepage in the Apache Kafka UI console.
Official Solution
Apache has released the latest version to fix the vulnerability. Affected users are strongly advised to update to Apache Kafka UI 0.7.2 and later.
Download link: https://github.com/provectus/kafka-ui
Timeline
On June 25, 2024, Sangfor FarSight Labs received notification of the Apache Kafka UI remote code execution vulnerability (CVE-2024-32030).
On June 25, 2024, Sangfor FarSight Labs released a vulnerability alert.
References
https://github.com/provectus/kafka-ui/pull/4427
https://securitylab.github.com/advisories/GHSL-2023-229_GHSL-2023-230_kafka-ui/





