About the Vulnerability
Introduction
The Auxiliary Function Driver is a service in Microsoft Windows responsible for operating BSD sockets.
Summary
On August 14, 2024, Sangfor FarSight Labs received notification that a Windows TCP/IP component contains information of remote execution code vulnerability(CVE-2024-38063), classified as high in threat level.
Attackers can exploit this vulnerability to craft malicious data and execute remote code attacks when the victim has IPv6 enabled, ultimately executing code on the system.
Affected Versions
Windows 11 Version 24H2 for x64-based Systems
Windows 11 Version 24H2 for ARM64-based Systems
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows Server 2022, 23H2 Edition (Server Core installation)
Windows 11 Version 23H2 for x64-based Systems
Windows 11 Version 23H2 for ARM64-based Systems
Windows 10 Version 22H2 for 32-bit Systems
Windows 10 Version 22H2 for ARM64-based Systems
Windows 10 Version 22H2 for x64-based Systems
Windows 11 Version 22H2 for x64-based Systems
Windows 11 Version 22H2 for ARM64-based Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 11 version 21H2 for ARM64-based Systems
Windows 11 version 21H2 for x64-based Systems
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Solutions
Remediation Solutions
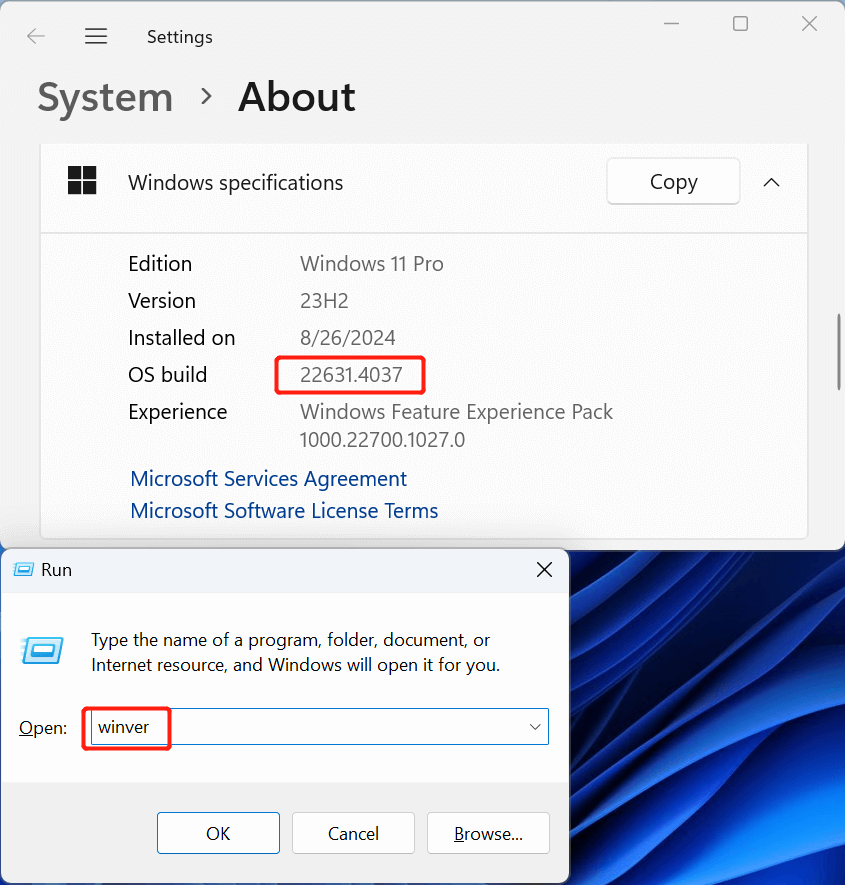
Check the System Version
Press the combination key “Win-R”, and type “winver” in the dialog of the pop-up window “Run”, then click “OK”
Official Solution
Affected users are strongly advised to update the version to fix the vulnerability.
Download link: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38063
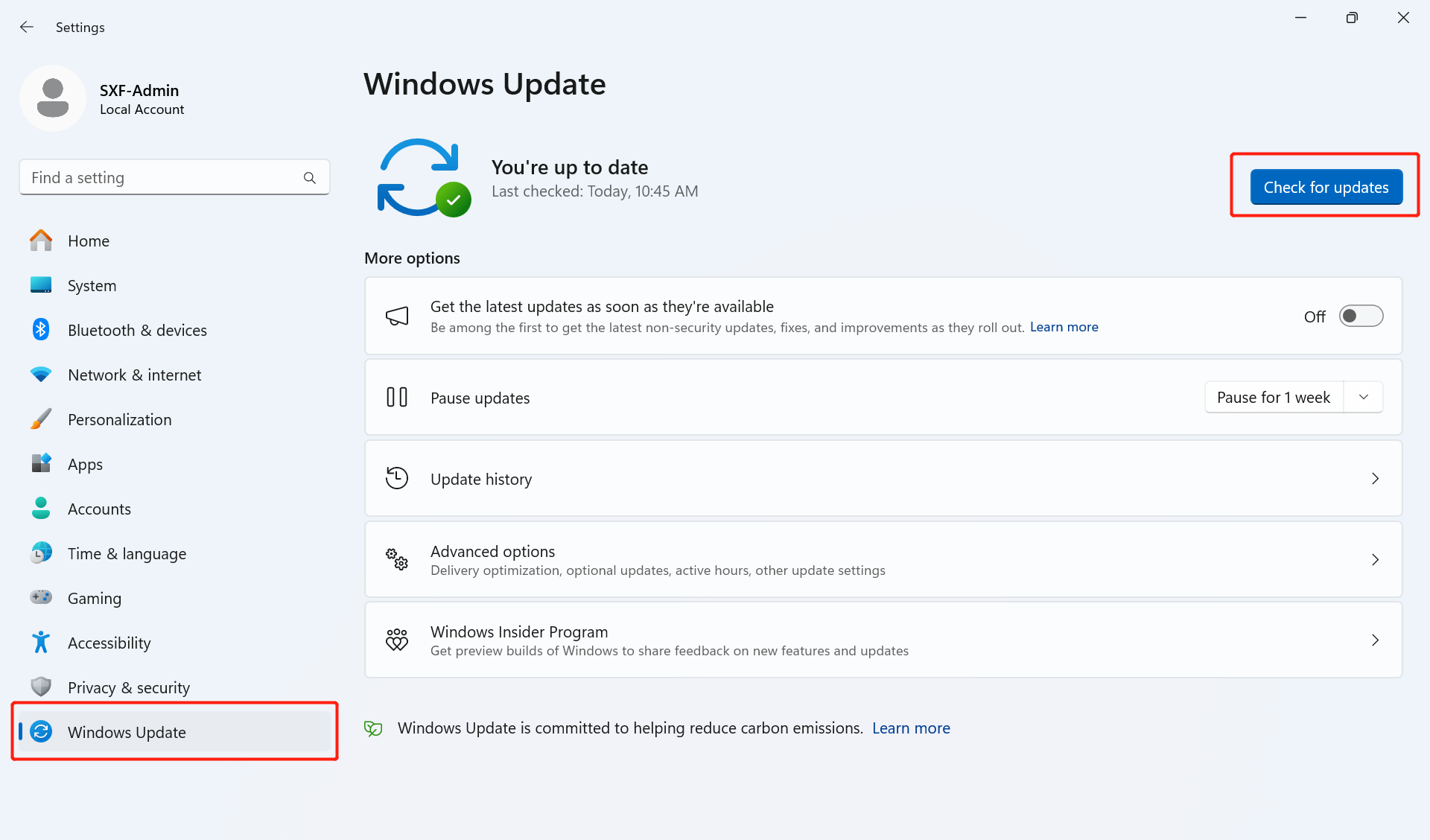
Method of putting patches/updating:
Click “Settings” - “Windows Update” - “Check for updates”.
Timeline
On August 14, 2024, Sangfor FarSight Labs received notification that the security patches has been officially released by Microsoft.
On August 15, 2024, Sangfor FarSight Labs released a vulnerability alert.
References
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38063





