1. Apple Patches New Zero-Day Vulnerabilities Exploited in Operation Triangulation
Apple released a new security update on July 24, 2023, to address one of the zero-day vulnerabilities exploited in attacks targeting iPhone, Mac, and iPad. The vulnerability, identified as CVE-2023-38606, is part of a zero-click exploit chain used to deploy Triangulation spyware on iPhones via iMessage exploits, according to Boris Larin, a lead security researcher in the Global Research & Analysis Team (GReAT) at Kaspersky. This vulnerability impacted a wide range of devices, spanning numerous iPhone and iPad models, as well as Mac devices running on macOS Big Sur, Monterey, and Ventura.
The APT campaign dubbed "Operation Triangulation" can be traced back to 2019. In a recent report dated June 1, 2023, Kaspersky stated that the iPhones of several members of their top and middle management were compromised as part of the APT campaign. The latest attack exploited a zero-click vulnerability that requires no user interaction. After receiving an infected iMessage, a device will be infected, and an APT toolkit will be loaded on the infected device.
Since the beginning of 2023, Apple has addressed a total of 11 zero-day vulnerabilities across various systems, including iOS, macOS, and iPadOS. The previously fixed vulnerabilities are as follows:
- July 10: CVE-2023-37450
- June: CVE-2023-32434, CVE-2023-32435, CVE-2023-32439
- May: CVE-2023-32409, CVE-2023-28204, CVE-2023-32373
- April: CVE-2023-28206, CVE-2023-28205
- February: CVE-2023-23529
We strongly recommend that users update their Apple products as soon as possible to keep their devices secure.

2. BlackByte 2.0 Ransomware Completes Intrusion, Encryption, and Extortion in Five Days
Ransomware attacks are a major threat to organizations worldwide and continue to grow in severity. Microsoft's Incident Response team recently investigated the BlackByte 2.0 ransomware attacks. The team found that the threat actor progressed through the entire attack chain in just five days, from gaining initial access to causing significant impact by compromising additional systems, encrypting critical data, and demanding a ransom.
According to the investigation's findings, the threat actor exploited unpatched Microsoft Exchange server vulnerabilities known as ProxyShell, allowing them to gain initial access to target networks and carry out malicious activities. Subsequently, the BlackByte 2.0 ransomware was deployed to encrypt data using an 8-digit key number.
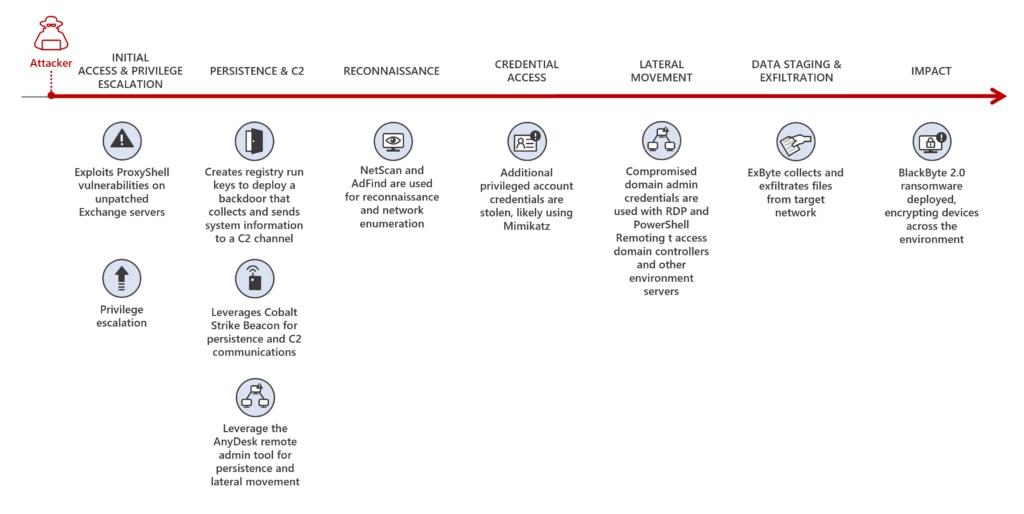
BlackByte 2.0 ransomware attack chain (source: Microsoft)
To ensure successful data encryption, the ransomware employed process hollowing and antivirus bypass techniques for defense evasion. Web shells were also implanted to gain remote access and persistence on affected servers.
3. Sangfor FarSight Labs Releases Report on Recent Attacks by South Asia APT Groups
Over the past three months, Sangfor FarSight Labs detected numerous attacks suspected of being conducted by APT groups from South Asia, particularly India. The groups include CNC, Bitter, Patchwork, Confucius, SideWinder, and DoNot. Among them, CNC, Bitter, and Patchwork have shown significant activity, launching multiple attacks against various industries in China since 2022. Notably, these three groups share many similarities, including similar infrastructure, attack techniques, and samples. There is a possibility that the groups are associated to some extent.
Sangfor FarSight Labs also found that APT groups from India recently attacked government agencies and educational, aerospace, scientific research, and military institutes, with each group exhibiting slight variations in their target preferences.
In terms of attack techniques, Sangfor FarSight Labs noticed that the APT groups employed advanced and highly tailored spear-phishing attacks for initial access. Through dark web channels, the groups acquired the leaked credentials for internal email addresses of agencies or institutes. They used these to hijack email communications and crafted custom emails to users based on their roles. They even interacted with users to gain their trust. The groups have continuously enhanced their attack tools for lateral movement and persistence, employing various masquerading, obfuscation, and hiding techniques to evade detection. For instance, Patchwork uses signature spoofing, updates encryption algorithms, and evades API monitoring to bypass detection by security products. Similarly, CNC forges certificates from security vendors and those of popular translation tools to evade detection.
Sangfor FarSight Labs studied the trend of recent attacks by highly active South Asian APT groups and predicts that they will continue to rely heavily on spear-phishing emails characterized by heightened levels of deception. Our analysis also indicates that the groups will continue to utilize tools modified from open-source software as their primary means of attack. The APT groups have demonstrated great proficiency in rapidly developing and improving open-source software, particularly in techniques such as anti-debugging, anti-analysis, and target identification. These constantly evolving adversarial techniques pose a great challenge for security vendors in terms of defense, investigation, and attribution.





