1. About the Vulnerabilities
1.1 Introduction
WebLogic is an application server and middleware developed by Oracle based on the Java EE architecture. WebLogic is a Java application server designed for developing, integrating, deploying, and managing large-scale distributed web apps, network apps, and database apps.
The Java dynamic function and the Java Enterprise standards of safety were introduced in the development, integration, deployment, and management of large-scale web apps. WebLogic is one of the main Java (J2EE) application server software in the commercial market. It is also the world's first successfully commercialized J2EE application server, with the advantages of scalability, rapid development, flexibility, and reliability.
1.2 Summary
On April 17, 2024, Sangfor FarSight Labs received notification of four vulnerabilities in Oracle WebLogic, ranging from medium to high severity. The following table describes these vulnerabilities.
| No. | Vulnerability Name | Affected Versions | Severity Level |
|---|---|---|---|
| 1 | Information Disclosure Vulnerability (CVE-2024-21006) | Oracle WebLogic Server 12.2.1.4.0 Oracle WebLogic Server 14.1.1.0.0 | High (CVSS Score 7.5) |
| 2 | Information Disclosure Vulnerability (CVE-2024-21007) | Oracle WebLogic Server 12.2.1.4.0 Oracle WebLogic Server 14.1.1.0.0 | High (CVSS Score 7.5) |
| 3 | XSS Vulnerability (CVE-2024-23635) | Oracle WebLogic Server 12.2.1.4.0 Oracle WebLogic Server 14.1.1.0.0 | Medium (CVSS Score 6.1) |
| 4 | Denial of Service Vulnerability (CVE-2024-26308) | Oracle WebLogic Server 12.2.1.4.0 Oracle WebLogic Server 14.1.1.0.0 | Medium (CVSS Score 5.5) |
1.3 Description of High-Severity Vulnerabilities
1. Information Disclosure Vulnerability (CVE-2024-21006)
An information disclosure vulnerability was found in Oracle WebLogic Server. Unauthenticated attackers can exploit this vulnerability to steal sensitive information.
2. Information Disclosure Vulnerability (CVE-2024-21007)
An information disclosure vulnerability was found in Oracle WebLogic Server. Unauthenticated attackers can exploit this vulnerability to steal sensitive information.
2. Affected Versions
WebLogic is a Java application server designed for developing, integrating, deploying, and managing large-scale distributed web apps, network apps, and database apps. Assets that may be affected by the vulnerabilities are widely distributed around the world. The affected assets in Guangdong, Beijing, Shanghai, and other provinces and cities account for approximately 70% of the affected assets in China. The vulnerabilities exposed in the current year involve a large number of users, making the vulnerability very serious.
3. Solutions
3.1 Remediation Solutions
3.1.1 Check the Component Version
(1) Check the version of WebLogic Server
Log in to the WebLogic Server console to view its version number.
(2) Check the ID of the patch for WebLogic Server
Go to the OPatch directory under the WebLogic Server home directory and run the .\opatch lspatches command, as shown in the figure below.
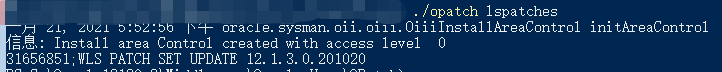
In this example, the patch ID is 31656851.
3.1.2 Install the Patch
For WebLogic Server 12.2.1.3 Step 1 Check the version of OPatch
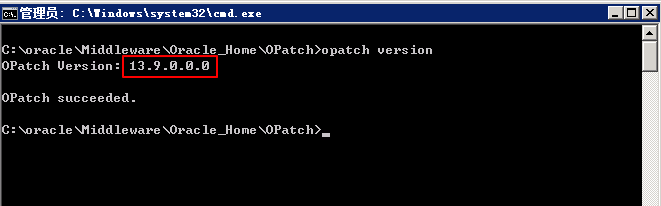
Go to C:\oracle\Middleware\Oracle_Home\OPatch and run the following command:
C:\oracle\Middleware\Oracle_Home\OPatch > opatch version
If the version is 13.9.4.0.0 or later, perform Step 2. Otherwise, upgrade OPatch.
Perform the following steps to upgrade OPatch:
Delete OPatch of an earlier version.
Go to the C:\oracle\Middleware\Oracle_Home directory and rename the following directories: OPatch, oracle_common, oui, and inventory.
Download and decompress the patch installation package.
Click the following URL to download the installation patch package: https://updates.oracle.com/Orion/Services/download/p28186730_139400_Generic.zip?aru=22731294&patch_file=p28186730_139400_Generic.zip
WebLogic Server is updated on a regular basis. We recommend that you download the latest patches from the official website (https://support.oracle.com). For information about how to download the latest patches, visit http://blog.itpub.net/31394774/viewspace-2699573
- Install OPatch
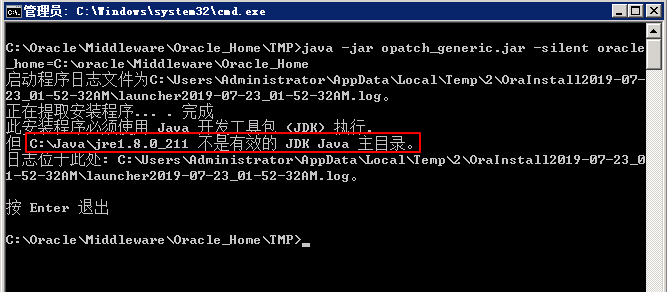
Run the following command:
java -jar opatch_generic.jar -silent oracle_home=C:\oracle\Middleware\Oracle_Home
If the following error occurs, install OPatch to the bin directory in the JDK installation directory.
- Check the installation result
New OPatch, oracle_common, oui, and inventory directories are generated.
Run the following command: C:\oracle\Middleware\Oracle_Home\OPatch > opatch version
If the upgrade is successful, the OPatch version is changed to 13.9.4.
Step 2 Download and decompress the patch installation package
Click the following URL to download the patch installation package:
WebLogic Server is updated on a regular basis. We recommend that you download the latest patches from the official website (https://support.oracle.com). For information about how to download the latest patches, visit http://blog.itpub.net/31394774/viewspace-2699573
Decompress the package to any directory.
Step 3 (Recommended) Read the README file before performing the succeeding steps
Step 4 Stop WebLogic Server
Step 5 Install the patch
Go to the directory in which the decompressed patch installation package is stored and run the following command:
C:\oracle\Middleware\Oracle_Home\OPatch\opatch apply
Step 6 Restart WebLogic Server
Restart WebLogic Server and verify whether services are running properly.
Note: If service exceptions occur, run the following command to roll back the patch:
C:\oracle\Middleware\Oracle_Home\OPatch\opatch rollback -id <patch ID>
For WebLogic Server of earlier versions
Upgrade WebLogic Server to 12.2.1.3 and later. For information about how to upgrade WebLogic Server, please contact Oracle technical support.
3.1.3 Workaround
Note: This temporary mitigation does not completely fix the issue. Users can decide whether to adopt the solution based on their business needs.
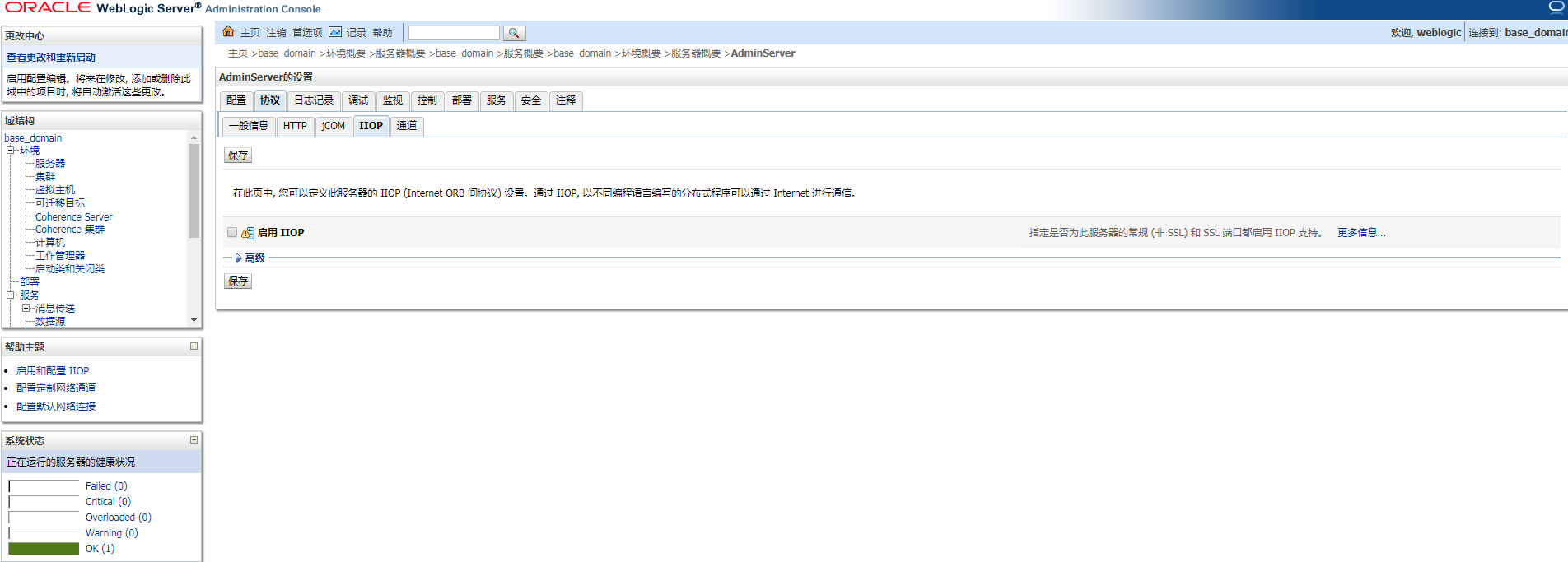
- This vulnerability can be mitigated by closing the IIOP protocol. Perform the following operations:
Log in to the WebLogic Server console, select Services > Settings for AdminServer > Protocols, deselect Enable IIOP, and restart WebLogic Server.
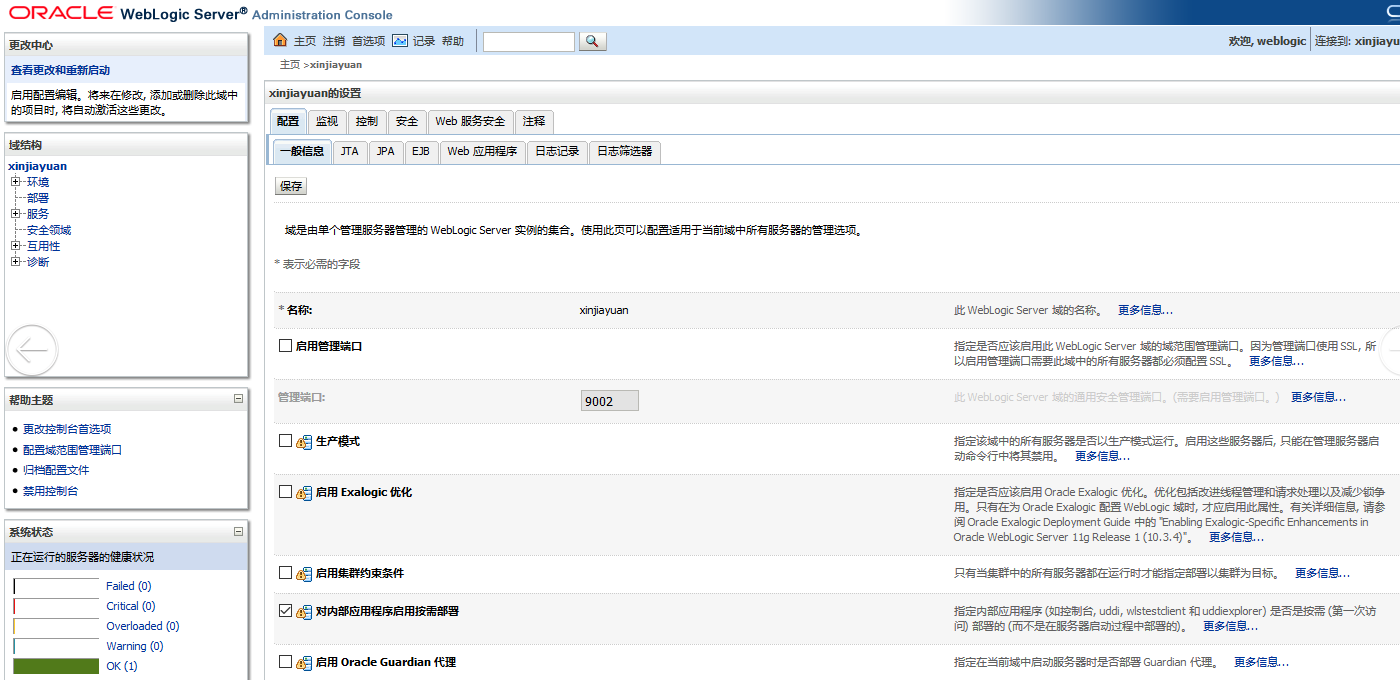
Log in to the WebLogic Server console. In the Domain Structure panel on the left side of the page, click the domain name. On the settings page of the domain name, select Security > Filter. In the text box of Connection Filter, enter security.net.ConnectionFilterImpl.
In the text box of Connection Filter Rules, enter 127.0.0.1 * * allow t3 t3s,0.0.0.0/0 * * deny t3 t3s.
Save the settings and restart the server.
- Official Solution
Oracle has released patches for affected versions to fix these vulnerabilities, and affected users are recommended to download the corresponding patches from the following link:
https://www.oracle.com/security-alerts/cpuapr2024.html
5. Timeline
On April 17, 2024, Sangfor FarSight Labs received notification of four vulnerabilities in Oracle WebLogic.
On April 18, 2024, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.





