Summary
On January 15, 2025, Microsoft released its January 2025 Security Updates, which included patches for a total of 161 CVEs, an increase of 89 compared to the previous month.
In terms of vulnerability severity, there were 11 vulnerabilities marked as "Critical," and 150 vulnerabilities were marked as "Important/High" level vulnerabilities. Regarding the types of vulnerabilities, there were primarily 58 remote code execution vulnerabilities, 38 privilege escalation vulnerabilities, and 25 information disclosure vulnerabilities.
Statistics
Vulnerability Trend
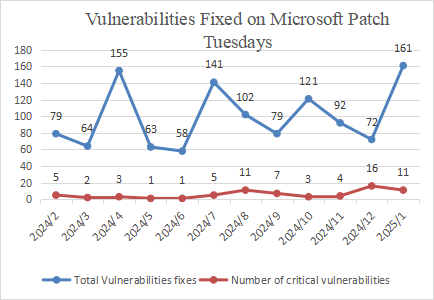
Figure 1 Vulnerabilities Patched by Microsoft in the Last 12 Months
On the whole, Microsoft released 161 patches in January 2025, including patches for 11 critical vulnerability patches.
Based on Microsoft's historical vulnerability disclosures and the specific circumstances of this year, Sangfor FarSight Labs estimates that Microsoft will announce more vulnerabilities in the coming February in comparison to January. We expect a figure of approximately 80 vulnerabilities.
Comparison of Vulnerability Trends
The following figure shows the number of patches released by Microsoft in the month of January from 2022 to 2025.
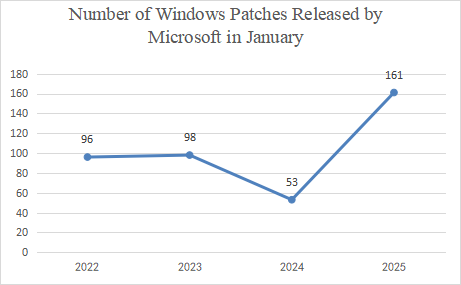
Figure 2 Number of Windows Patches Released by Microsoft in January from 2022 to 2025
The following figure shows the trend and number of vulnerabilities at different severity levels addressed by Microsoft in January from 2022 to 2025.

Figure 3 Number of Vulnerabilities by Severity Level Addressed by Microsoft in January from 2022 to 2025
The following figure shows the number of vulnerabilities by type addressed by Microsoft in January from 2022 to 2025.

Figure 4 Number of Vulnerabilities by Type Addressed by Microsoft in January from 2022 to 2025
Data source: Microsoft security updates
Compared to last year, there has been an increase in terms of the number of vulnerabilities of this year. The number of vulnerabilities addressed by Microsoft in January 2025 has increased. A total of 161 vulnerability patches, including 11 critical ones, have been reported this month.
Compared to last year, the number of vulnerabilities at the Critical level addressed by Microsoft has increased, and that of vulnerabilities at the Important/High level has also increased. 150 vulnerabilities at the Important/High level have been addressed, an increase of about 194%, and 16 vulnerabilities at the Critical level have been addressed, an increase of about 450%.
In terms of Vulnerability Type, the number of RCE and EoP vulnerabilities has increased, and that of DoS vulnerabilities has also increased. However, we should remain highly vigilant because, when combined with social engineering techniques, attackers can exploit RCE vulnerabilities to take over an entire LAN and launch attacks.
Details of Key Vulnerabilities
Analysis
Windows Hyper-V NT Kernel Integration VSP Elevation of Privilege Vulnerabilities
(CVE-2025-21333) (CVE-2025-21334) (CVE-2025-21335)
Hyper-V, codenamed Viridian and formerly known as Windows Server Virtualization, is Microsoft's native hypervisor. It allows for the creation of virtual machines on Windows systems running x86-64 architecture.
A privilege escalation vulnerability exists within it, which attackers can exploit to gain higher privileges on the target system. This vulnerability is known to be exploited in the wild, and after assessment, it is considered critical in threat level. We recommend that users promptly update the Microsoft security patches.
Windows NTLM V1 Elevation of Privilege Vulnerability(CVE-2025-21311)
In Windows networks, NTLM (NT LAN Manager) is a suite of Microsoft security protocols designed to provide authentication, integrity, and confidentiality to users.
A privilege escalation vulnerability exists within it, which attackers can exploit to gain higher privileges on the target system. After assessment, it is considered critical in threat level. We recommend that users promptly update the Microsoft security patches.
Affected Versions
| Vulnerability Name | Affected Versions |
|---|---|
Windows Hyper-V NT Kernel Integration VSP Elevation of Privilege Vulnerabilities (CVE-2025-21333) (CVE-2025-21334) (CVE-2025-21335) | Windows Server 2025 Windows Server 2025 (Server Core installation) Windows Server 2022, 23H2 Edition (Server Core installation) Windows 11 Version 24H2 for x64-based Systems Windows 11 Version 24H2 for ARM64-based Systems Windows 11 Version 23H2 for x64-based Systems Windows 11 Version 23H2 for ARM64-based Systems Windows 11 Version 22H2 for x64-based Systems Windows 11 Version 22H2 for ARM64-based Systems Windows 10 Version 22H2 for x64-based Systems Windows 10 Version 21H2 for x64-based Systems |
Windows NTLM V1 Elevation of Privilege Vulnerability (CVE-2025-21311) | Windows Server 2025 Windows Server 2025 (Server Core installation) Windows Server 2022, 23H2 Edition (Server Core installation) Windows 11 Version 24H2 for x64-based Systems Windows 11 Version 24H2 for ARM64-based Systems |
Solutions
Official Solution
Microsoft has released patches for affected applications. Affected users can install the corresponding security updates according to the system versions:
Download Links:
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21333
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21334
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21335
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21311
Reference
https://msrc.microsoft.com/update-guide/releaseNote/2025-Jan
Timeline
On January 15, 2025, Microsoft released a security bullet.
On January 15, 2025, Sangfor FarSight Labs released a vulnerability alert.





