Summary
On September 11, 2024, Microsoft released its September 2024 Security Updates, which included patches for a total of 79 CVEs, a decrease of 23 compared to the previous month.
In terms of vulnerability severity, there were 7 vulnerabilities marked as "Critical," and 71 vulnerabilities were marked as "Important/High" level vulnerabilities. Regarding the types of vulnerabilities, there were primarily 23 remote code execution vulnerabilities, 30 privilege escalation vulnerabilities, and 11 information disclosure vulnerabilities.
Statistics
Vulnerability Trend
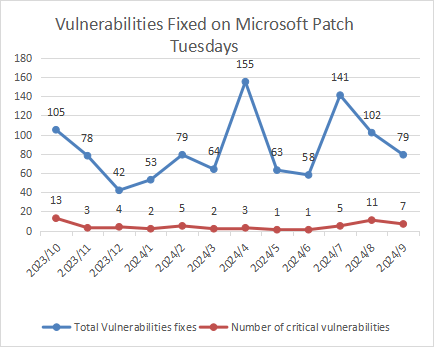
Figure 1 Vulnerabilities Patched by Microsoft in the Last 12 Months
Microsoft released 79 patches in September 2024, including patches for seven critical vulnerabilities.
Based on Microsoft's historical vulnerability disclosures and the specific circumstances of this year, Sangfor FarSight Labs estimates that Microsoft will announce more vulnerabilities in the coming October in comparison to September. We expect a figure of approximately 90 vulnerabilities.
Comparison of Vulnerability Trends
The following figure shows the number of patches released by Microsoft in the month of September from 2021 to 2024.
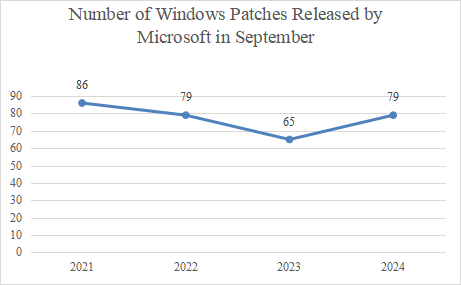
Figure 2 Number of Windows Patches Released by Microsoft in September from 2021 to 2024
The following figure shows the trend and number of vulnerabilities at different severity levels addressed by Microsoft in September from 2021 to 2024.
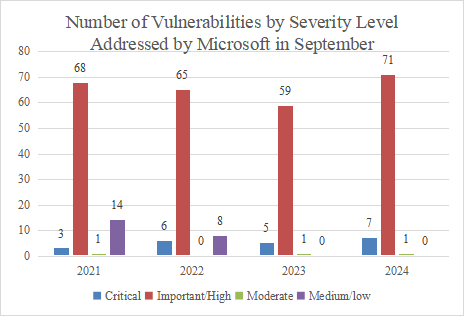
Figure 3 Number of Vulnerabilities by Severity Level Addressed by Microsoft in September from 2021 to 2024
The following figure shows the number of vulnerabilities by type addressed by Microsoft in September from 2021 to 2024.
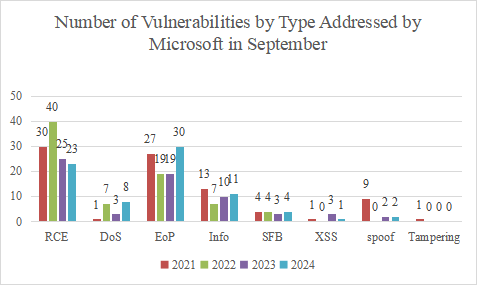
Figure 4 Number of Vulnerabilities by Type Addressed by Microsoft in September from 2021 to 2024
Data source: Microsoft security updates
Compared to last year, there has been an increase in terms of the number of vulnerabilities of this year while the number of vulnerabilities addressed by Microsoft in September 2024 has decreased. A total of 79 vulnerabilities, including seven critical ones, have been reported this month.
Compared to last year, the number of vulnerabilities at the Critical level addressed by Microsoft has decreased, and that of vulnerabilities at the Important/High level has increased. 7 vulnerabilities at the Important/High level have been addressed, an increase of about 40%, and 71 vulnerabilities at the Critical level have been addressed, a increase of about 20%.
In terms of Vulnerability Type, the number of RCE vulnerabilities has increased, and that of DoS and EoP vulnerabilities has decreased. However, we should remain highly vigilant because, when combined with social engineering techniques, attackers can exploit RCE vulnerabilities to take over an entire LAN and launch attacks.
Details of Key Vulnerabilities
Analysis
Microsoft Windows Update Remote Code Execution Vulnerability (CVE-2024-43491)
Windows Update is a Microsoft service designed for the Windows series of operating systems, allowing automatic downloading and installation of Microsoft Windows software updates from the internet. This service provides updates for Windows software and various Microsoft antivirus software, including Windows Defender and Microsoft Security Essentials.
A remote code execution vulnerability exists within it, which attackers can exploit to execute arbitrary code on the target system. This vulnerability is known to be exploited in the wild, and after assessment, it poses a significant risk. We recommend that users promptly update the Microsoft security patches.
Windows Web Query Tagging Security Feature Bypass Vulnerability (CVE-2024-38217)
Web Query Tagging (MoTW) is a feature used by Microsoft Windows to mark files downloaded from the internet as potentially unsafe. A security feature bypass vulnerability exists within it, which attackers can exploit to circumvent security features on the target system, leading to unauthorized actions. This vulnerability has been exploited in the wild and is considered highly dangerous. We recommend that users promptly update Microsoft security patches to protect their systems.
Microsoft Publisher Security Feature Bypass Vulnerability (CVE-2024-38226)
Microsoft Publisher is a desktop publishing application released by Microsoft. Unlike Microsoft Word, which focuses on text composition and proofreading, Publisher emphasizes page layout and graphic design.
A security feature bypass vulnerability exists within it, which attackers can exploit to circumvent security features on the target system, leading to unauthorized actions. This vulnerability has been exploited in the wild and is considered highly dangerous. We recommend that users promptly update Microsoft security patches to protect their systems.
Windows Installer Privilege Escalation Vulnerability (CVE-2024-38014)
Windows Installer is a programming interface used by Microsoft Windows for the installation, maintenance, and removal of software.
A privilege escalation vulnerability exists within it, which attackers can exploit to gain higher privileges on the target system. This vulnerability has been exploited in the wild and is considered highly dangerous after assessment. We recommend that users promptly update Microsoft security patches to protect their systems.
Affected Versions
| Vulnerability Name | Affected Versions |
|---|---|
| Microsoft Windows Update Remote Code Execution Vulnerability (CVE-2024-43491) |
Windows 10 for x64-based Systems Windows 10 for 32-bit Systems |
| Windows Web Query Tagging Security Feature Bypass Vulnerability (CVE-2024-38217) |
Windows Server 2012 R2 Windows Server 2012 R2 (Server Core installation) Windows Server 2012 (Server Core installation) Windows Server 2012 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2016 (Server Core installation) Windows Server 2016 Windows 10 Version 1607 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems Windows 10 for x64-based Systems Windows 10 for 32-bit Systems Windows 11 Version 24H2 for x64-based Systems Windows 11 Version 24H2 for ARM64-based Systems Windows Server 2022, 23H2 Edition (Server Core installation) Windows 11 Version 23H2 for x64-based Systems Windows 11 Version 23H2 for ARM64-based Systems Windows 10 Version 22H2 for 32-bit Systems Windows 10 Version 22H2 for ARM64-based Systems Windows 10 Version 22H2 for x64-based Systems Windows 11 Version 22H2 for x64-based Systems Windows 11 Version 22H2 for ARM64-based Systems Windows 10 Version 21H2 for x64-based Systems Windows 10 Version 21H2 for ARM64-based Systems Windows 10 Version 21H2 for 32-bit Systems Windows 11 version 21H2 for ARM64-based Systems Windows 11 version 21H2 for x64-based Systems Windows Server 2022 (Server Core installation) Windows Server 2022 (Server Core installation) Windows Server 2022 Windows Server 2022 Windows Server 2019 (Server Core installation) Windows Server 2019 Windows 10 Version 1809 for ARM64-based Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for 32-bit Systems |
| Microsoft Publisher Security Feature Bypass Vulnerability (CVE-2024-38226) |
Microsoft Publisher 2016 (64-bit edition) Microsoft Publisher 2016 (32-bit edition) Microsoft Office LTSC 2021 for 32-bit editions Microsoft Office LTSC 2021 for 64-bit editions Microsoft Office 2019 for 64-bit editions Microsoft Office 2019 for 32-bit editions |
| Windows Installer Privilege Escalation Vulnerability (CVE-2024-38014) |
Windows Server 2012 R2 (Server Core installation) Windows Server 2012 R2 Windows Server 2012 (Server Core installation) Windows Server 2012 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2016 (Server Core installation) Windows Server 2016 Windows 10 Version 1607 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems Windows 10 for x64-based Systems Windows 10 for 32-bit Systems Windows 11 Version 24H2 for x64-based Systems Windows 11 Version 24H2 for ARM64-based Systems Windows Server 2022, 23H2 Edition (Server Core installation) Windows 11 Version 23H2 for x64-based Systems Windows 11 Version 23H2 for ARM64-based Systems Windows 10 Version 22H2 for 32-bit Systems Windows 10 Version 22H2 for ARM64-based Systems Windows 10 Version 22H2 for x64-based Systems Windows 11 Version 22H2 for x64-based Systems Windows 11 Version 22H2 for ARM64-based Systems Windows 10 Version 21H2 for x64-based Systems Windows 10 Version 21H2 for ARM64-based Systems Windows 10 Version 21H2 for 32-bit Systems Windows 11 version 21H2 for ARM64-based Systems Windows 11 version 21H2 for x64-based Systems Windows Server 2022 (Server Core installation) Windows Server 2022 (Server Core installation) Windows Server 2022 Windows Server 2022 Windows Server 2019 (Server Core installation) Windows Server 2019 Windows 10 Version 1809 for ARM64-based Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for 32-bit Systems |
Solutions
Official Solution
Microsoft has released patches for affected OS versions to fix the latest vulnerabilities. Please install the latest Windows security updates to install the patches or download the patch for individual vulnerabilities from Microsoft's security updates page:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43491
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38217
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38226
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38014
References
https://msrc.microsoft.com/update-guide/releaseNote/2024-Sep
Timeline
On September 11, 2024, Microsoft released a security bullet.
On September 1, 2024, Sangfor FarSight Labs released a vulnerability alert.





