Analysis of Silver Fox Loader
1.1 Introduction
Sangfor FarSight Labs has been monitoring the Silver Fox cybercriminal group and has recently detected and captured In-The-Wild (ITW) attacks from a new variant of their loader. The sample of the new variant has evolved capabilities to fight against security software.
1.2 Behavior Analysis
Evolution of historical variants In most cases, succeeding generations of the Silver Fox loader variants can better disguise themselves as normal files compared with their predecessors. They inject unobtrusive malicious code into normal code or files to avoid being detected by a heuristic engine and trick the engine into generating more false positives. Silver Fox loaders frequently use two methods to avoid detection. First, they insert malicious binary code into the execution stream of a normal file by using binary hijack techniques. The following figure shows a type of slide code as an example.
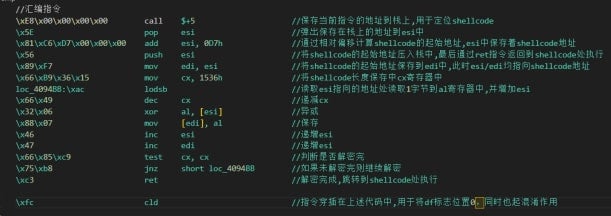
Second, they insert loader code into normal Microsoft Foundation Class (MFC) projects. Based on the class names used by the collected samples, specific MFC projects are downloaded from the Internet.
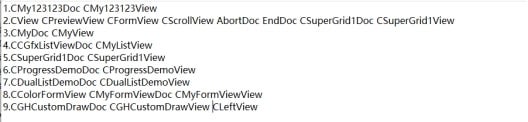
For example, the CCGfxListViewDoc and CMyListView classes, as shown in the following figure.
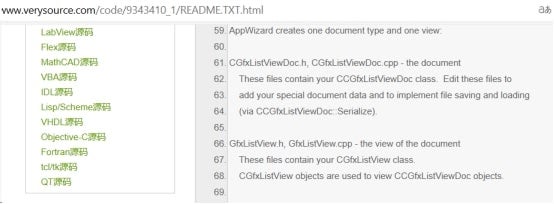
In addition, the amount of inserted code is increasing. Earlier loader samples simply downloaded next-stage payloads from the Internet and then executed the payloads. The latest samples copy specific functions of the next-stage payloads into the loader.
General execution process
In most cases, the execution of a loader hiding in an MFC project follows a specific procedure. Initially, the loader sends a character string to the command-and-control (C2) server to report a successful landing. Then, the loader downloads the next-stage payloads and allocates executable memory to execute the payloads.
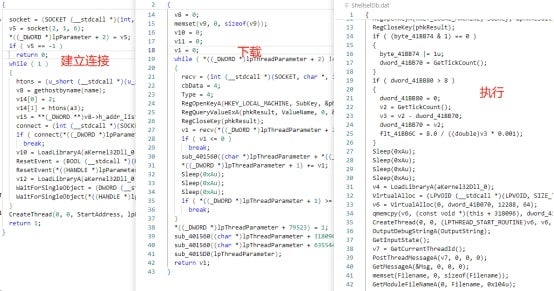
Specific loaders are transferred to the downloader code by using the exception handling mechanism.
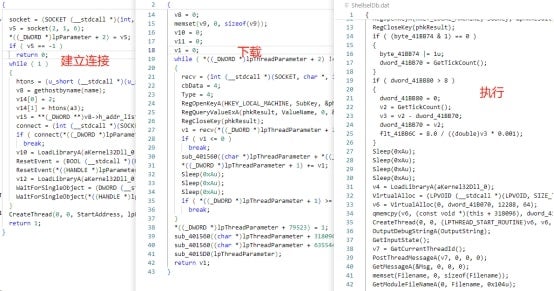
About the new variant
The new variant captured this time is able to detect and disable security software. Before downloading next-stage payloads, the variant checks process names to detect the presence of security software in the system and then tries to disable the security software by modifying privileges in process tokens.
The new variant calls the LookupPrivilegeValueA and AdjustTokenPrivileges functions to enable the following privileges.
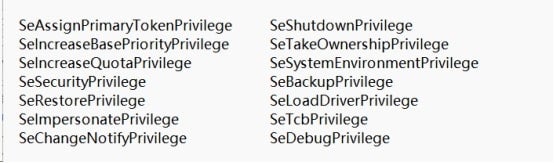
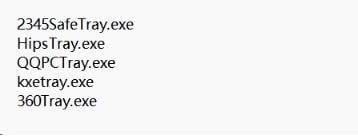
Then, the variant calls the SetTokenInformation function to adjust the integrity levels of security software processes and tries to call the PostThreadMessageA function to send a quit message and the TerminateProcess function to terminate the processes of security software. The new variant is able to detect the presence of the following five processes.
1.3 Indicators of Compromise (IOCs)
URL
43.136.235.18
Hash
717F9C2EB6FFD9244F747297B1F904B7
24182A6C8EFCBD16A829BEC483AD5F84
2 Solutions
2.1 Ransomware Prevention Strategies
Do not open suspicious or unexpected emails, especially the links and attachments in them. Use antivirus software to scan an unknown file before opening it (if you have to do so). Install antivirus software, perform regular system scans, remove detected threats, and regularly install updates and patches. Download products via official and verified channels, and activate and update products using tools or functions provided by the official developer. Illegal activation tools and third-party downloaders are not recommended, as they are often used to distribute malicious content.





