1. Summary
| Vulnerability Name |
Windows OLE Remote Code Execution Vulnerability (CVE-2023-29325) |
|---|---|
| Release Date |
May 11, 2023 |
| Component Name |
Windows Object Linking and Embedding (OLE) |
| Affected Versions |
Windows 11, 10 Windows Server 2022, 2019, 2016, 2012, 2008 See Section 3 Affected Versions for details |
| Vulnerability Type |
Remote Code Execution Vulnerability |
| Severity |
CVSS v3 Base Score: 7.5 (High) |
| Exploitability |
Attack Vector: Network Attack Complexity: High Privileges Required: None User Interaction: Required |
| Impact |
Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About the Vulnerability CVE-2023-29325
2.1 Introduction
OLE (Object Linking and Embedding) is a technology developed by Microsoft that allows different applications to work together and share data. It provides a way for one application to use objects from another application or embed them within its own documents.
2.2 Summary
On May 11, 2023, Sangfor FarSight Labs received a notice about a remote code execution vulnerability (CVE-2023-29325) in the Windows OLE component, classified as high severity with a CVSS score of 7.5 (NVD)/8.1 (Microsoft).
The vulnerability is caused by memory corruption in the Windows OLE component.
In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted email to the victim. Exploitation of the vulnerability might involve either a victim opening a specially crafted email with an affected version of Microsoft Outlook software, or a victim's Outlook application displaying a preview of a specially crafted email. This could result in the attacker executing remote code on the victim's machine.
3. Affected Versions
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows 11 version 21H2 for x64-based Systems
Windows 11 version 21H2 for ARM64-based Systems
Windows 11 Version 22H2 for x64-based Systems
Windows 11 Version 22H2 for ARM64-based Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows 10 Version 22H2 for x64-based Systems
Windows 10 Version 22H2 for ARM64-based Systems
Windows 10 Version 22H2 for 32-bit Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
4. Vulnerability Validation
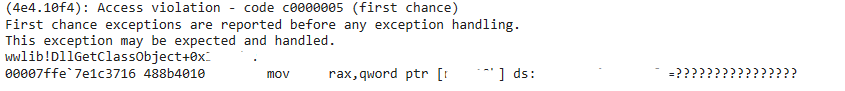
Sangfor FarSight Labs created a Windows 10.0.19045.2846 version environment to reproduce the vulnerability in Outlook, causing Outlook crash, as shown in the following figure.
5. Solutions
5.1 Remediation Solutions
5.1.1 Check the Component Version
Use cmd.exe to execute the winver command to obtain the internal version number of the Windows OS.
5.1.2 Microsoft Solution
Microsoft has released a patch for affected OS versions to fix this vulnerability. Please download the patch corresponding to the affected OS from the following link: https://msrc.microsoft.com/update-guide/en-us/vulnerability/CVE-2023-29325
Patching Method:
Click the above link to download the patch package corresponding to the current OS version for installation.
5.1.3 Workaround
Note: This temporary mitigation does not completely fix the issue. Users can decide whether to adopt the solution based on their business needs.
To implement this workaround, modify the Microsoft Outlook settings to view all emails in plain text to reduce the risk of opening RTF files from unknown or untrusted sources. For details, refer to https://support.microsoft.com/en-us/office/read-email-messages-in-plain-text-16dfe54a-fadc-4261-b2ce-19ad072ed7e3.
Impact of workaround: An email viewed in plain text format will not contain pictures, specialized fonts, animations, or other rich content. In addition:
- The changes are applied to the preview pane and open messages.
- Pictures are converted into attachments to avoid loss.
- Because the message is still stored in RTF or HTML format, the object model (custom code solutions) may behave unexpectedly.
5.2 Sangfor Solution
5.2.1 Security Protection
The following Sangfor products and services provide protection against the Windows OLE remote code execution vulnerability (CVE-2023-29325)
- Sangfor Endpoint Secure (Endpoint Detection and Response) *Please update to the latest vulnerability rule base
6. Timeline
On May 9, 2023, Microsoft disclosed the Windows OLE remote code execution vulnerability (CVE-2023-29325).
On May 11, 2023, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
7. Reference
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-29325
https://nvd.nist.gov/vuln/detail/CVE-2023-29325
8. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





