Analysis of XZ Utils Supply Chain Compromise
Introduction
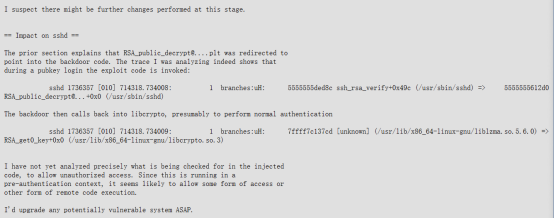
On March 29, 2024, Andres Freund, a PostgreSQL developer at Microsoft, discovered a backdoor in the XZ Utils package while troubleshooting SSH performance issues. He reported the backdoor to Open Source Security (oss-security), revealing a supply chain compromise involving obfuscated malicious code in the XZ Utils package.
This backdoor affects XZ Utils/liblzma 5.6.0 and 5.6.1 and the following software:
Alpine Edge
Arch
Cygwin
Exherbo
Gentoo
Homebrew
KaOS
MacPorts
Manjaro Testing
nixos-unstable/nixpkgs-unstable
OpenIndiana
OpenMamba
OpenMandriva Rolling
Parabola
PCLinuxOS
Pisi Linux
pkgsrc-current
Ravenports
Slackware-current
Solus
Termux
Wikidata
The impact of the backdoor is confined as software versions with the backdoor have not been merged into the stable repository of the mainstream Linux distributions (Red Hat/CentOS/Debian/Ubuntu) used by enterprises.
Timeline
In 2021, a user named Jia Tan (JiaT75) registered on GitHub. JiaT75 then started contributing to the XZ Utils project and gained commit access.
A few months ago, JiaT75 committed bad-3-corrupt_lzma2.xz and good-large_compressed.lzma, two binary test files containing malicious code. Under certain conditions, the compilation script will read the malicious code from these two files and modify the compilation results, causing inconsistencies between the compilation results and the public source code.
On March 29, 2024, Andres Freund discovered the backdoor while troubleshooting SSH performance issues and reported it to oss-security, revealing the supply chain compromise.
Solutions
Remediation Strategies
Run the xz --version command to check the version of XZ Utils. If the output is 5.6.0 or 5.6.1, your system may have been embedded with the backdoor. Then, execute the following script to check whether the backdoor exists:
Then, execute the following script to check whether the backdoor exists:
#! /bin/bash
set -eu
# find path to liblzma used by sshd
path="$(ldd $(which sshd) | grep liblzma | grep -o '/[^ ]*')"
# does it even exist?
if [ "$path" == "" ]
Then
echo probably not vulnerable
Exit
fi
# check for function signature
if hexdump -ve '1/1 "%.2x"' "$path" | grep -q f30f1efa554889f54c89ce5389fb81e7000000804883ec28488954241848894c2410
Then
echo probably vulnerableelseecho probably not vulnerable
fi
If the backdoor exists, run the following command to downgrade XZ Utils to 5.4.6 or upgrade it to 5.6.4:
sudo apt install xz-utils={Target version}





